By 2024-2-27 00:28:32 Author: checkmarx.com(查看原文) 阅读量:23 收藏
-
 By
Yehuda Gelb
By
Yehuda Gelb
- February 26, 2024

Key Points
- Sophisticated Supply chain attack: The Tornado Cash open source project was compromised with malicious JavaScript code inserted by a developer.
- Impact: Users who conducted transactions using the targeted Tornado Cash project through IPFS gateways were unknowingly impacted for a couple of months.
- Discovery: The compromise, discovered by Security researcher Gas404, marks the second major security issue for Tornado Cash within a year, emphasizing the importance of community vigilance in decentralized finance.
- Ongoing risks in decentralized finance: This incident highlights the persistent challenges in ensuring safety and trust in decentralized platforms.
What is Tornado Cash?
Tornado Cash is a decentralized privacy solution built on the Ethereum blockchain, offering users non-custodial and anonymous transactions. Functioning as a cryptocurrency mixer, it provides a mechanism to obfuscate the origins and destinations of digital asset transfers, enhancing user privacy and security. While Tornado Cash has faced scrutiny for its potential misuse in illicit activities, such as money laundering notably by entities like North Korean hackers, it remains an innovative tool in the realm of decentralized finance.
In 2022, The original Tornado Cash service encountered challenges due to U.S. government sanctions, impacting its usage among certain user demographics. Despite this setback, the project's open-source codebase has fostered the emergence of new independent mixing services.
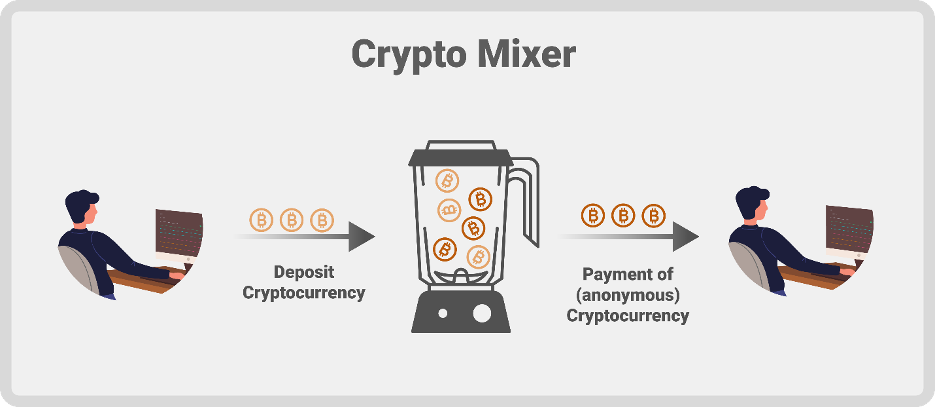
The Compromise of the Open Source Tornado Cash
Tornado Cash recently fell victim to a sophisticated attack. This attack was executed through a deceptive contribution by a developer, who secretly embedded malicious JavaScript code within the project’s user interface. This code was designed to covertly capture and send users' private deposit notes to an unauthorized external server. Deposit notes in Tornado Cash act like private keys, crucial for accessing and managing funds within the service.
This exploit specifically targeted users accessing Tornado Cash through IPFS gateways, like ipfs.io and cf-ipfs.com. These gateways are used to enter the decentralized web where Tornado Cash operates. The malicious code was cleverly concealed within a governance proposal by the developer, making it very challenging for an average user to detect.
The code worked by encoding these private deposit notes and sending them to the exploiter's server under the guise of routine function calls. This meant that whenever a user engaged with certain functions of Tornado Cash, their private information was leaked without their knowledge.
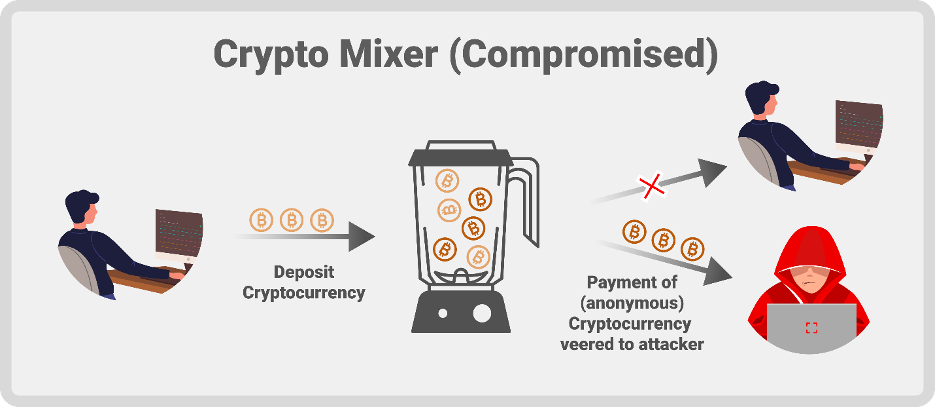
The discovery of this malicious code was credited to a security researcher known as Gas404, and according to their findings, all Tornado Cash servers deployed on the IPFS network since January 1 of this year were believed to be impacted.
In the aftermath of the sanctions imposed on Tornado Cash, the original website of the service was seized. However, the open-source codebase of Tornado Cash continued to exist independently, leading to the emergence of new, shadowy mixing services using the same foundation. This incident of backdoor code implantation marks the second major security breach that Tornado Cash has endured over the past year, with a previous instance in May of the previous year where a hacker briefly seized control of the project's governance.
In terms of the impact, the exact extent of the funds compromised in this latest breach still remains uncertain.
Conclusion
The Tornado Cash open-source project compromise highlights serious concerns about the safety of decentralized finance platforms and the trustworthiness of developers. It serves as a stark reminder that we cannot simply assume open-source projects are immune from malicious activities. The notion that "someone else is checking" can often lead to a false sense of security. Importantly, this incident illustrates how attackers like to leverage supply chain attacks to compromise sensitive applications and networks. It underscores the importance of thorough security audits, vetting of code and contributions, even from seemingly trustworthy sources, and the need to protect against supply chain vulnerabilities. For users, it's a reminder to be vigilant about the platforms they use and to understand the associated risks. Clearly, preserving security and trust in decentralized platforms remains a challenging but vital task.
![]()
Yehuda Gelb
Yehuda is a security researcher at Checkmarx and has a passion for making cyberspace a safer place to live and work. Prior to Checkmarx, he served as an information system security officer for the Lockheed Martin F-35 program, and assisted in developing the Cyber Defense strategy for Israel’s Air Force, the IAF. Yehuda currently holds numerous cyber certifications including CISSP and CCSP. During his free time he also employs his expertise to help people and non-profit organizations share their stories with the world through audio and visuals. Yehuda’s hobbies include creating music, producing films, traveling, and strategy board games.
![]()
Yehuda Gelb
Yehuda is a security researcher at Checkmarx and has a passion for making cyberspace a safer place to live and work. Prior to Checkmarx, he served as an information system security officer for the Lockheed Martin F-35 program, and assisted in developing the Cyber Defense strategy for Israel’s Air Force, the IAF. Yehuda currently holds numerous cyber certifications including CISSP and CCSP. During his free time he also employs his expertise to help people and non-profit organizations share their stories with the world through audio and visuals. Yehuda’s hobbies include creating music, producing films, traveling, and strategy board games.
Never miss an update. Subscribe today!
By submitting my information to Checkmarx, I hereby consent to the terms and conditions found in the Checkmarx Privacy Policy and to
the
processing of my personal data as described therein. By clicking submit below, you consent to allow Checkmarx
to store and process the personal
information submitted above to provide you the content requested.
More Resources to Consider
如有侵权请联系:admin#unsafe.sh