2024-2-20 15:31:36 Author: cyble.com(查看原文) 阅读量:24 收藏
On February 2, 2024, Cyble Research & Intelligence Labs (CRIL) identified a Malware-as-a-services (MaaS) dubbed ‘AsukaStealer’ advertised on a Russian-language cybercrime forum, for which the version 0.9.7 of the web panel was offered for USD 80 per month. The AsukaStealer was originally advertised on another popular Russian forum on January 24, 2024, using an alternate persona.
The malware is written in C++ with flexible settings and a web-based panel and is designed to collect information from browsers, extensions, Discord tokens, FileZilla sessions, Telegram sessions, crypto wallets and extensions, screenshots from Desktop, and maFiles from the Steam Desktop Authenticator application. A few screenshots from the command-and-control (C&C) panel were shared to demonstrate the AsukaStealer Malware-as-Service (MaaS).
Detailed research also revealed that the malware is likely a revamped version of the ObserverStealer.

Figure 1: Advertisement of AsukaStealer on the forum
Observations & Analysis
The promoters of AsukaStealer boasted several features and shared multiple screenshots captured from the C&C panel to demonstrate the capabilities of the stealer malware. The notable features of the stealer included:
- Functional features:
- The native styler is written in C++ language and is 280 kb in size.
- Collects browser data (Cookies, Passwords, AccountsSync, Extensions) on Chromium (Edge, Google, OperaGX) and Gecko (Firefox, Waterfox) engines.
- Collects Discord tokens.
- Collects FileZilla sessions (FileGrabber|Standard config).
- Collects Telegram sessions (ProcessGrabber|FileGrabber|Standard config).
- Builds Steam (Standard config).
- There is functionality for uploading a file after collecting the log (Loader).
- Ability to install custom proxies.
- Ability to send logs to telegram.
- Collects a screenshot from the desktop.
- Collecting maFiles from the Steam Desktop Authenticator application (ProcessGrabber|Standard config).
- An anti-duplicate system.
- Configuration setup:
- Customizable list of browsers [Chromium, Gecko].
- Customizable FileGrabber/crypto wallet files.
- Customizable list of extensions.
- Customizable ProcessGrabber.
- Customizable Loader.
- Customizable Discord clients.
The screenshots of the AsukaStealer C&C panel are as follows:

Figure 2: Login page of the AsukaStealer dashboard

Figure 3: Customized browser configuration settings

Figure 4: Dashboard demonstrating the total information collected by the malware

Figure 5: Logs collected by the stealer

Figure 6: Information collected from Discord token.

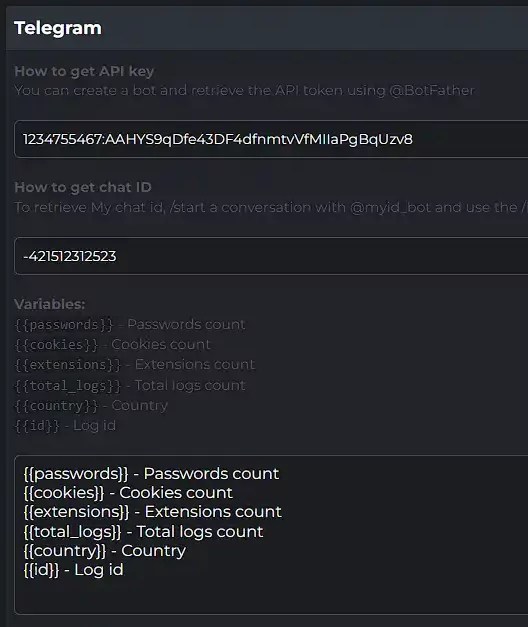
Figure 7: Telegram session information

Figure 8: Screenshot of the collected logs.
During our research, we discovered the following indicators associated with the C&C panel of AsukaStealer:
- hxxp[:]//5.42.66.25/
- IP address geolocated in Russia.
- Hosts the AsukaStealer C&C panel.
- Open ports – 80, 3000
- Also hosts simplyavailable.com and freemsk.org domains.
The domains simplyavailable.com, freemsk.org were possibly the other remote servers for AsukaStealer.
According to VirusTotal, we observed the following files with the IP address, reported between January 29, 2024 – February 13, 2024:
- VL_SkinChanger.exe
- 24bb4fc117aa57fd170e878263973a392d094c94d3a5f651fad7528d5d73b58a.exe
- Setup.exe
- 5f2016f22935cea6fa5eafe1e185d6a9b4c14c4b2aa8619ec15a539358cac928.exe
- brave_exe
- Launcher-AI.exe
- 9ac629ed8e07b6c99b05edd46b86e1795e5f96908ab1fe85a06282b0a982cd1b.exe
- file_1.zip
- c534f184b8ea3887161eC&Cb364de15e61ee9a4053f8902450383d3f4165fc818.exe
- CCiVUlD20s4qygxJucEODm800LQYrBtW.exe
Some of the aforementioned files were detected as AsukaStealer based on the YARA signatures.
AsukaStealer – a Revamped Version of ObserverStealer
During our research in July 2023, we observed that the promoters of AsukaStealer MaaS also announced the closure of MaaS operations for the ObserverStealer, indicating the involvement of the same threat actors behind the development and administration of both stealer malware.

Figure 9: ObserverStealer on offer and announcement of its closure
Furthermore, while investigating the indicators for AsukaStealer, we found multiple files that were interacting with IP address ‘5.42.66.25’, that have been flagged and detected as ObserverStealer, by VirusTotal. Interestingly, the C&C panel of AsukaStealer and ObserverStealer have strikingly similar features.

Figure 10: GET Request
We also observed the same mutex ‘IESQMMUTEX_0_208’ in the files associated with both the malware, indicating their inception from the same malware family.
Conclusion
It is evident from our research that the malware developers or authors leveraged the same C&C infrastructure for hosting ObserverStealer and AsukaStealer. Overall, our research led us to assess that the AsukaStealer is an enhanced version of the ObserverStealer. Although there is limited information on the source of infection, we have observed one of the files using phishing as a method to deliver the malware.
Threat actors who are proficient in malware development and capable of hosting a sizeable C&C infrastructure, continue to seize opportunities to offer malware-as-a-service (MaaS) to cater to underground communities and make profits within a short period of time. The stealer malware, such as Redline, Raccoon, and Azorult, has already become a popular resource development service for threat actors to gain initial access to the targeted organizations and execute cyberattacks. The release of AsukaStealer is another instance of information-stealing malware being offered as malware-as-a-service (MaaS) on Russian cybercrime forums this year.
Tactics, Techniques & Procedures (TTPs)
The tactics, techniques, and procedures (TTPs) identified during our analysis based on the MITRE ATT&CK framework follows:
| Tactics | Techniques & Sub-Techniques | MITRE ATT&CK® ID |
| Credential Access | TA0006 | |
| OS Credential Dumping Input Capture Credentials from Web Browsers Steal Application Access Token Steal Web Session Cookie | T1003 T1056 T1555.003 T1528 T1539 | |
| Discovery | T0007 | |
| Remote System Discovery File and Directory Discovery System Information Discovery Security Software Discovery | T1018 T1083 T1082 T1518.001 | |
| Collection | TA0009 | |
| Data from Local System Input Capture Automated Collection | T1005 T1056 Indicators of Compromise (IoCs) T1119 |
Indicators of Compromise (IoCs)
| IOCs | Type | Description |
| http://5.42.66.25/ | URL | C&C panel of AsukaStealer |
| 5.42.66.25 | IP | Malicious IP |
| http://www.simplyavailable.com | Domain | Login panel of AsukaStealer |
| freemsk.org | Domain | Login panel of AsukaStealer |
| 2d2b66d90495c1236f2e557172bf0f1c a06d203ae9cbe26a3c2e389f1c361ac49ef54c08 24bb4fc117aa57fd170e878263973a392d094c94d3a5f651fad7528d5d73b58a | MD5 SHA-1 SHA-256 | 24bb4fc1.exe communicating with the IP 5.42.66.25 |
| 7ce0bd101d349bc88b668e380093e1a9 45fc72df60f39ebe77d4012f34a10e73eb2fd485 00cc1ef3d307750d5cdbe537da606101e90091b6020c71f696e454aee11c9a98 | MD5 SHA-1 SHA-256 | VL_SkinChanger.exe communicating with the IP 5.42.66.25 |
| e9dda8ccde5385e8d0a7f0bdc361e51d 863734caf0cb94dce610fe49eeebe438a7096dfb 5b2b8a4d5b8375a3ac2ce68b93cdbfdc8fd13d1cf4ea1a6a61bd784aa495dbfb | MD5 SHA-1 SHA-256 | Setup.exe communicating with the IP 5.42.66.25 |
| 28b7d6b0a793d772c953f529742ca91f fc33fe3deb280d9ed94e3add58134660433bdb18 5f2016f22935cea6fa5eafe1e185d6a9b4c14c4b2aa8619ec15a539358cac928 | MD5 SHA-1 SHA-256 | File communicating with the IP 5.42.66.25 |
| 9ce2a046a0698212c2963f2df91ff2e1 69a2d82f13246761e6d5159efb78b8fa91856380 6b0e95d68da6d029a4af645a408c0608218e853f11c8ba70a14b06ec2a005424 | MD5 SHA-1 SHA-256 | brave.exe file communicating with the IP 5.42.66.25 |
| 20017810fba85ef8ac6e4230d0e67a07 d7b6530a4c7d685e9ee6765231bab14fecdadeba 9ac629ed8e07b6c99b05edd46b86e1795e5f96908ab1fe85a06282b0a982cd1b | MD5 SHA-1 SHA-256 | File communicating with the IP 5.42.66.25 |
| 371e14f7e146ff22cb9ebe2f78cbfb7f 2fde663b31a46e83f3034464674ad3f3a85f6972 bb17d47f10fefcee4c883f93f2989e753b969298dd70262ae00696dd482dc9b4 | MD5 SHA-1 SHA-256 | File communicating with the IP 5.42.66.25 |
| 1494c8bc32576cb008c33d6f0fd1e842 4b3cdfbeaa9f8dc3554a0f9a54fc0d16334a46ed c534f184b8ea3887161ec2b364de15e61ee9a4053f8902450383d3f4165fc818 | MD5 SHA-1 SHA-256 | File communicating with the IP 5.42.66.25 |
| 75c79796fa147bf3f4d569b544ee0547 5c6a4cd4b9271410cc45ccda00a2531631f35136 dc723d302340d27529b8c3c880b4cf53534a02e2a71a68f39eec30f239c2c988 | MD5 SHA-1 SHA-256 | File communicating with the IP 5.42.66.25 |
| 2de37ffcae86c673de3cd2ee5e2ad3b1 09f2187f0228eed3df41c76c69d94da789c0f2f1 e6430183aa7bbaffa89ffbef7bfac3aa54481e904556ab71ea20ccf55dfce53f | MD5 SHA-1 SHA-256 | File communicating with the IP 5.42.66.25 |
References
Yara rules submitted for AsukaStealer in open-source repository: https://github.com/RussianPanda95/Yara-Rules
Related
如有侵权请联系:admin#unsafe.sh