Author:
Kaustubh Jagtap, Product Marketing Director, SafeBreach
On February 15th, the Cybersecurity and Infrastructure Security Agency (CISA) and the Multi-State Information Sharing & Analysis Center (MS-ISAC) issued an advisory highlighting the results of their incident response investigation into a state government organization’s network whose sensitive data including host/user details and other pertinent metadata were posted to the dark web. Detailed information about this investigation and the associated tactics, techniques, and procedures (TTPs) are listed in Threat Actor Leverages Compromised Account of Former Employee to Access State Government Organization.
Technical Details
The advisory reveals that the state government organization was notified that several documents containing sensitive network and user data were available for purchase on a dark web brokerage website. CISA and MS-ISAC revealed that unknown threat actors were able to access these sensitive documents by leveraging the stolen credentials and intended to sell this data on the dark web for a profit. The thorough investigation (conducted on the organizational on-prem environment and their Azure deployment), revealed that these stolen credentials belonged to a former employee who may not have been properly removed from the organizational Active Directory (AD). Investigation revealed the following details:
- Based on the log data, threat actors were able to first connect from an unknown virtual machine (VM) to the victim’s on-prem network by leveraging IP addresses belonging to the internal virtual private network (VPN). Their primary objective of doing so was to blend in with legitimate traffic and stay undetected.
- Threat actors were able to gain access by leveraging the credentials of a former employee who had admin-level access. These credentials were likely stolen in a separate data breach. This former employee had access to two virtual servers including the organizational SharePoint and another on their previous workstation. The workstation was virtualized from a physical workstation using the Veeam Physical to Virtual (P2V) function within the backup software.
- Threat actors were then able to obtain the credentials of another employee from the virtual SharePoint server. These new credentials had global domain administrator access which enabled the threat actors to access the organizational on-premises AD as well as the Azure AD.
- Through a connection from the VM, the threat actor conducted LDAP queries of the AD, likely using the open-source tool “AdFind.exe” to collect user, host, and trust relationship information. These LDAP queries were also used to generate the text file containing the stolen data that was offered for sale on the dark web.
- Threat actors also used both sets of stolen credentials to perform further network and service discovery by connecting to a multitude of services on the organizational network.
- There were no indications the threat actor further compromised the organization by moving laterally from the on-premises environment to the Azure environment.
Important Note for SafeBreach Customers – Coverage for AA24-046A (State Government Attack)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks in the Hacker’s Playbook to this US-CERT immediately. It is important to note that existing SafeBreach customers already had FULL coverage against all of the TTPs identified in the advisory. Please run/ re-run the attacks listed below to ensure your environments are protected against these TTPs.
Existing Behavioral Attacks Related to CERT Alert
- #7211 – Collect Azure credentials (Windows)
- #7005 – Create role assignment (Azure)
- #6800 – Domain Controller discovery using user credentials
- #6799 – Domain Controller discovery using interactive session token
- #6581 – Discover domain computers using LDAP method
- #6578 – Discover domain users using LDAP method
- #6550 – Agentless lateral movement via SMB and RCE, using Impersonated user
- #6513 – Agentless lateral movement via SMB and RCE, using Mimikatz
- #6483 – Agentless lateral movement via SMB and RCE, using Token duplication
- #5671 – Agentless lateral movement via Windows Remote Management
- #2306 – Domain Trust Discovery
- #1339 – Remote command execution by PSExec
What You Should Do Now
SafeBreach customers can now validate their security controls against these TTPs in multiple ways.
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA24_046A (State Government Attack) scenario from the list of available scenarios.
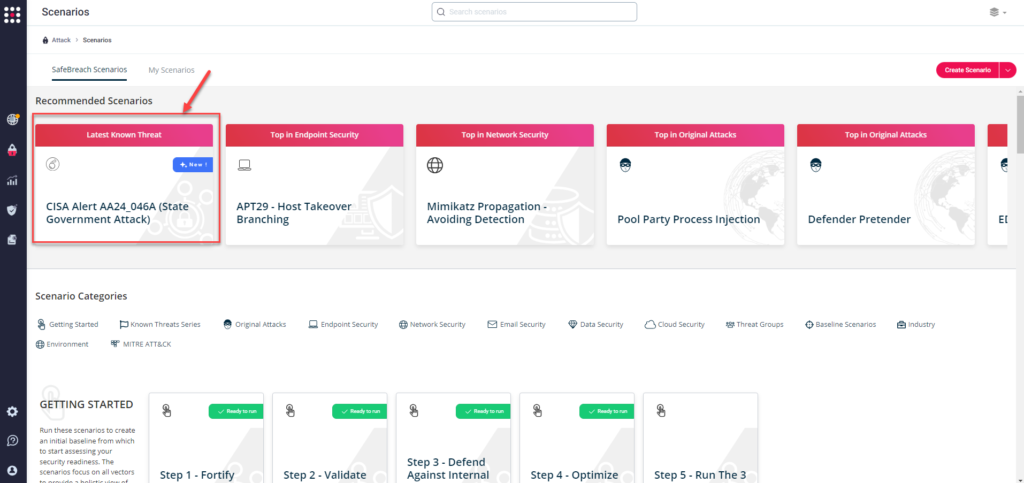
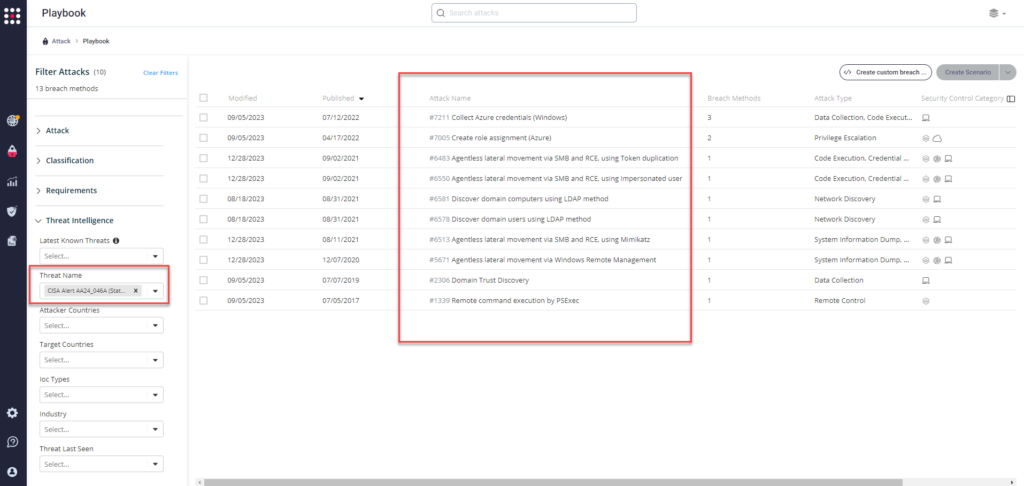
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA24_046A (State Government Attack). Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
Method 3 – From the Known Attack Series report, select the AA24_046A (State Government Attack) report and select Run Simulations which will run all attack methods.
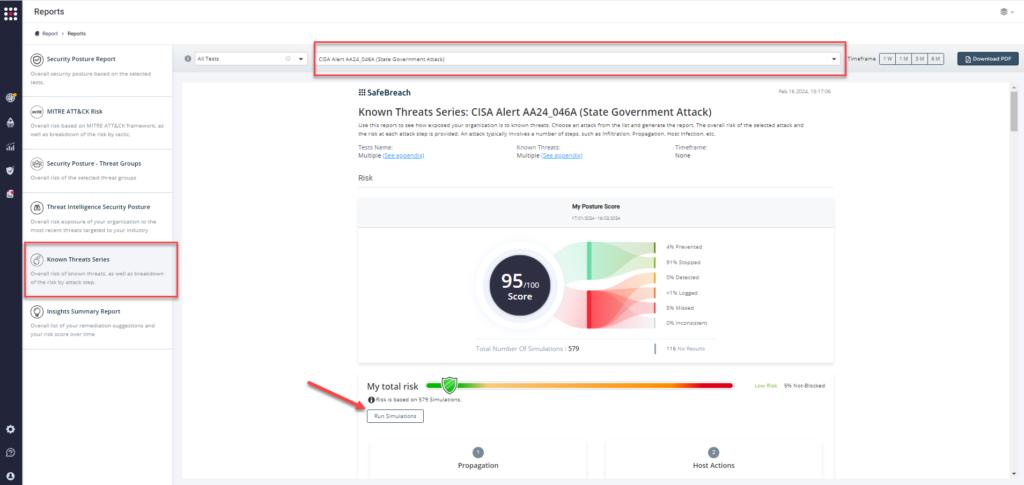
NOTE – CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against growing threat of advanced cyber threats. Additional recommendations include:
- Review current administrator accounts to determine their necessity and only maintain administrator accounts that are essential for network management.
- Restrict the use of multiple administrator accounts for one user.
- Create separate administrator accounts for on-premises and Azure environments to segment access.
- Use phishing-resistant multifactor authentication (MFA).
- Establish policy and procedure for the prompt removal of unnecessary accounts and groups from the enterprise, especially privileged accounts.
- Evaluate Tenant Settings.
- Assess the Security Configuration of Azure Environment.
- Evaluate Conditional Access Policies.
- For detailed information about mitigations and incident response, please refer to the full advisory.
You Might Also Be Interested In
Get the latest
research and news
The post State Government Organization Network Breach: SafeBreach Coverage for US-CERT Alert (AA24-046A) appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by Kaustubh Jagtap. Read the original post at: https://www.safebreach.com/blog/state-government-network-breach-safebreach-coverage-for-us-cert-alert-aa24-046a/
