2024-2-13 15:0:3 Author: securityboulevard.com(查看原文) 阅读量:12 收藏
The “Security Spotlight” blog series provides insight into emerging cyberthreats and shares tips for how you can leverage LogRhythm’s security tools, services, and out-of-the-box content to defend against attacks.
Last week, the Cybersecurity and Infrastructure Security Agency (CISA) released a security advisory regarding People’s Republic of China (PRC) state-sponsored cyber actors seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure. The associated group, Volt Typhoon, have since received attention press coverage, and the attention of our customer CISOs.
We’ve been at work ensuring that our customers are equipped and able to detect any potential compromises by said threat actor using the LogRhythm SIEM. In this Security Spotlight, we’ll share the information available, and how to to quickly setup detection in LogRhythm SIEM and some interesting observations during threat hunting phase.
Who is Volt Typhoon?
Also known as BRONZE SILHOUETTE, Volt Typhoon is a People’s Republic of China (PRC) state-sponsored actor active since mid-2021. The group rarely uses any malware; instead, their primary TTPs (technique, tactics and procedures) is Living of the Land (LOTL), which uses built-in legitimate tools and processes in the Operating Systems to carry out their objectives. Volt Typoon’s TTP allows them evade detection by blending in normal network activities, making it difficult for tools such as EDR or application whitelisting to detect, as no new 3rd party files are installed on the target system. As a result, a Security Information and Event Management (SIEM) platform, is best suited to detect such stealthy and sophisticated attacks.
Overview of Volt Typhoon’s Attack
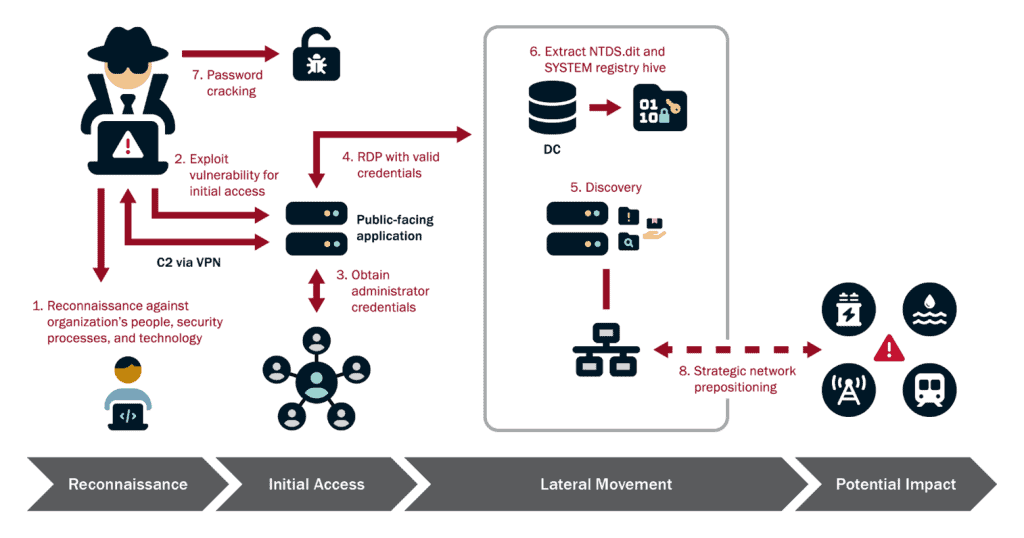
While Volt Typhoon actors tailor their TTPs to the victim environment, the U.S. authoring agencies have observed the actors typically following the same pattern of behavior across identified intrusions:
- Conduct extensive pre-compromise reconnaissance to learn about the target organization’s network architecture and operational protocols.
- Gain initial access to the IT network by exploiting known or zero-day vulnerabilities in public-facing network appliances (e.g., routers, virtual private networks (VPNs), and firewalls) and connect to the victim’s network via VPN for follow-on activities.
- Obtain administrator credentials within the network, often by exploiting privilege escalation vulnerabilities in the operating system or network services.
- Use valid administrator credentials to move laterally to the domain controller (DC) and other devices via remote access services such as Remote Desktop Protocol (RDP).
- Conduct discovery in the victim’s network, leveraging LOTL binaries for stealth.
- Achieve full domain compromise by extracting the Active Directory database from the DC.
- Uses offline password cracking techniques to decipher these hashes.
- Uses elevated credentials for strategic network infiltration and additional discovery, often focusing on gaining capabilities to access OT assets.
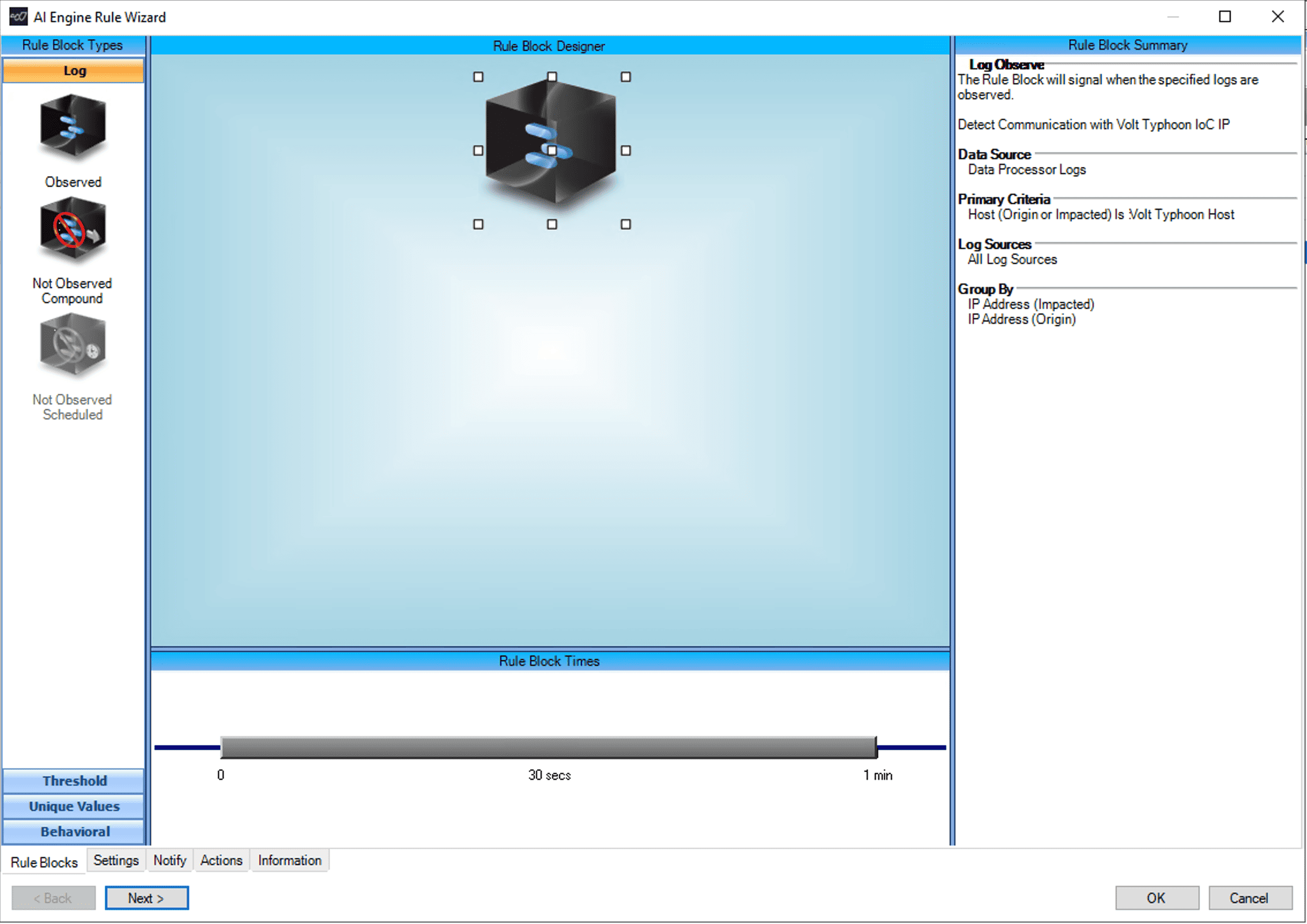
Using LogRhythm to Detect Volt Typhoon Activities
The LogRhythm SIEM can be configured to detect Volt Typhoon activities, along with a custom dashboard for you to view all relevant activities in one screen.
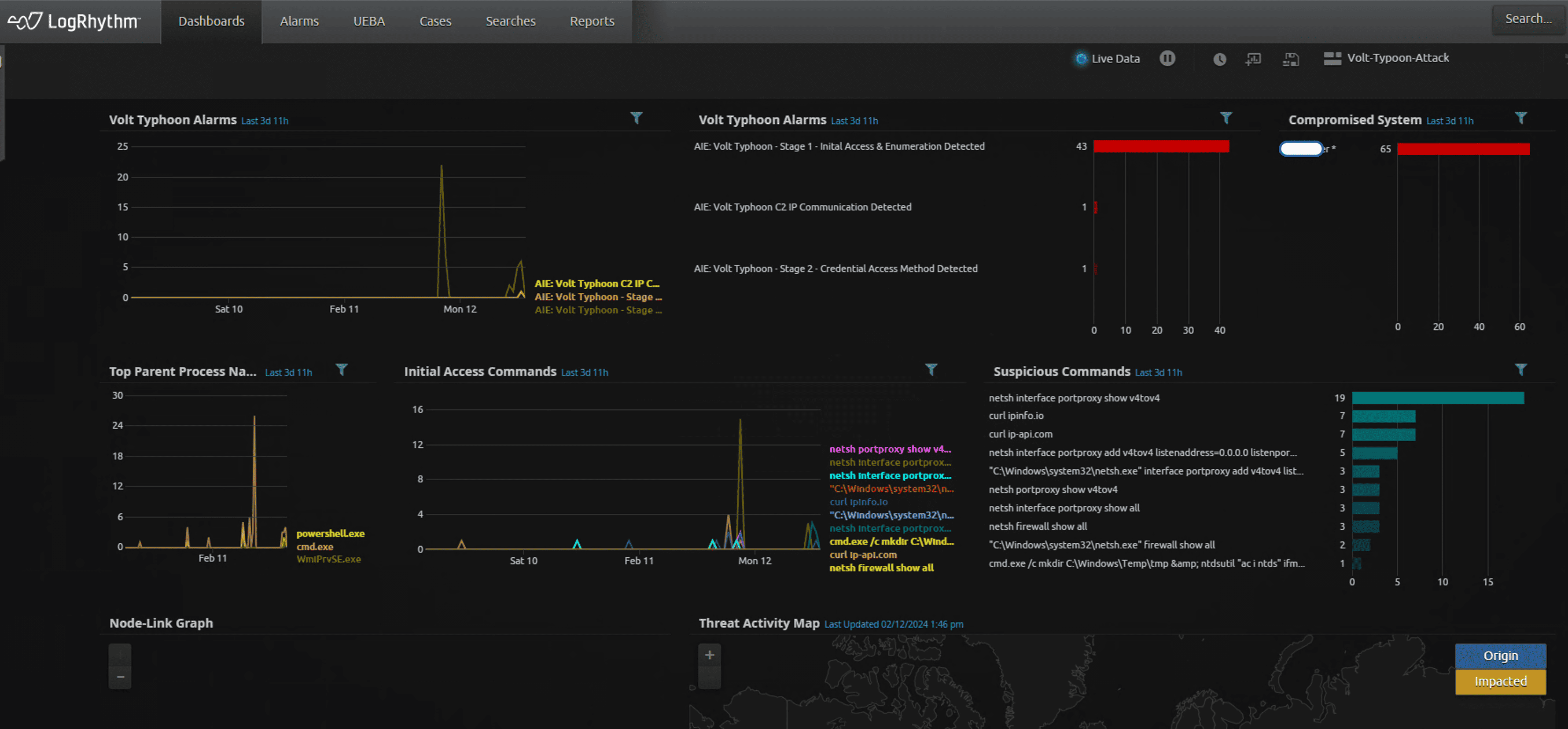
- Ensure proper logging is in place: It is imperative to capture Windows Security Log Event ID 4688 for any meaningful detection. For Volt Typhoon TTPs, you can configure the Global Log Processing Rules (GLPR) to forward only logs with Process Name: PowerShell.exe, pwsh.exe, wmic and cmd.exe
- AI Engine Rules Setup: Since Volt Typhoon uses large number of LOLBins (Living Off the Land Binaries) and commands, the goal is to minimize noise in alarms while detect precise and unique TTPs associate with this threat actor. This can be achieved by creating the following 3 AIE rules:
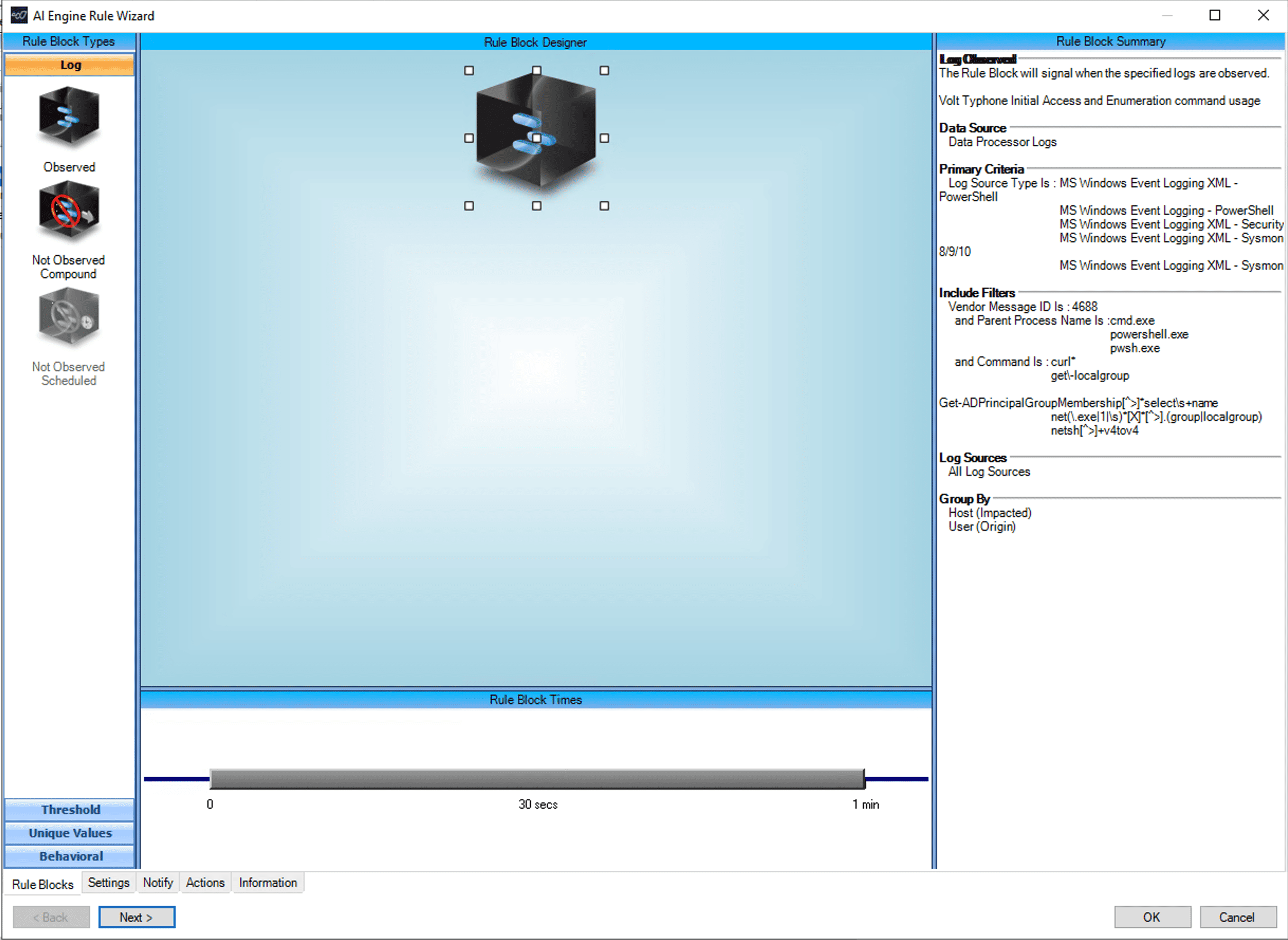
Rule 1: Initial Access and Enumeration Method Detected
In this rule, we are detecting the following TTPs.
curl www.ip-api.com
curl ipinfo.io
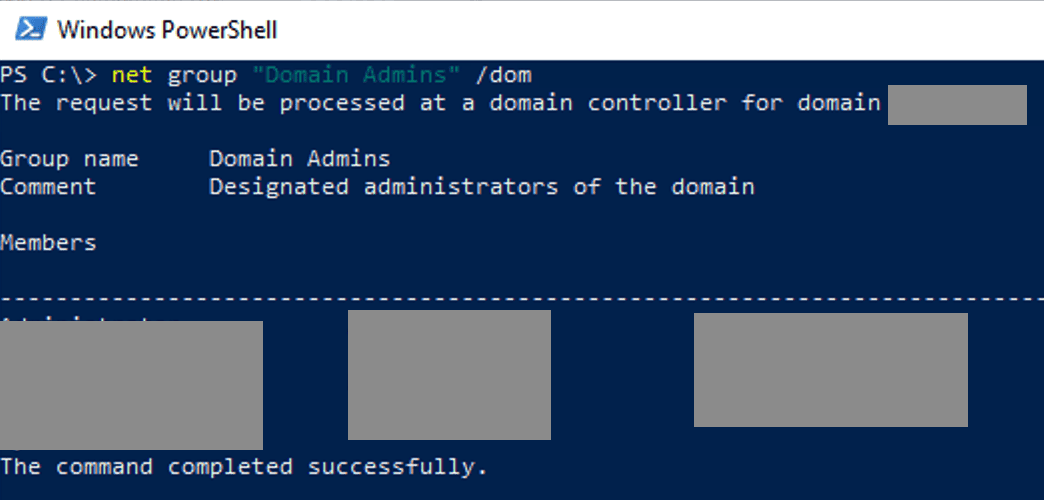
net localgroup administrators
net group /dom
net group “Domain Admins” /dom
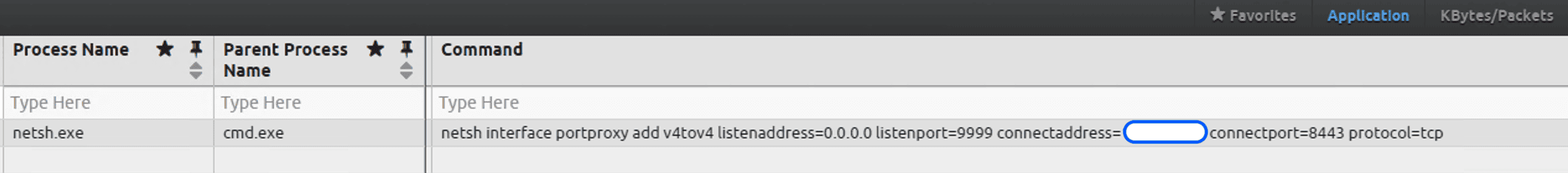
netsh interface portproxy add v4tov4 listenaddress=0.0.0.0 listenport=9999 connectaddress=InternalLANIPAddress connectport=8443 protocol=tcp
netsh interface portproxy show v4tov4
netsh portproxy show v4tov4
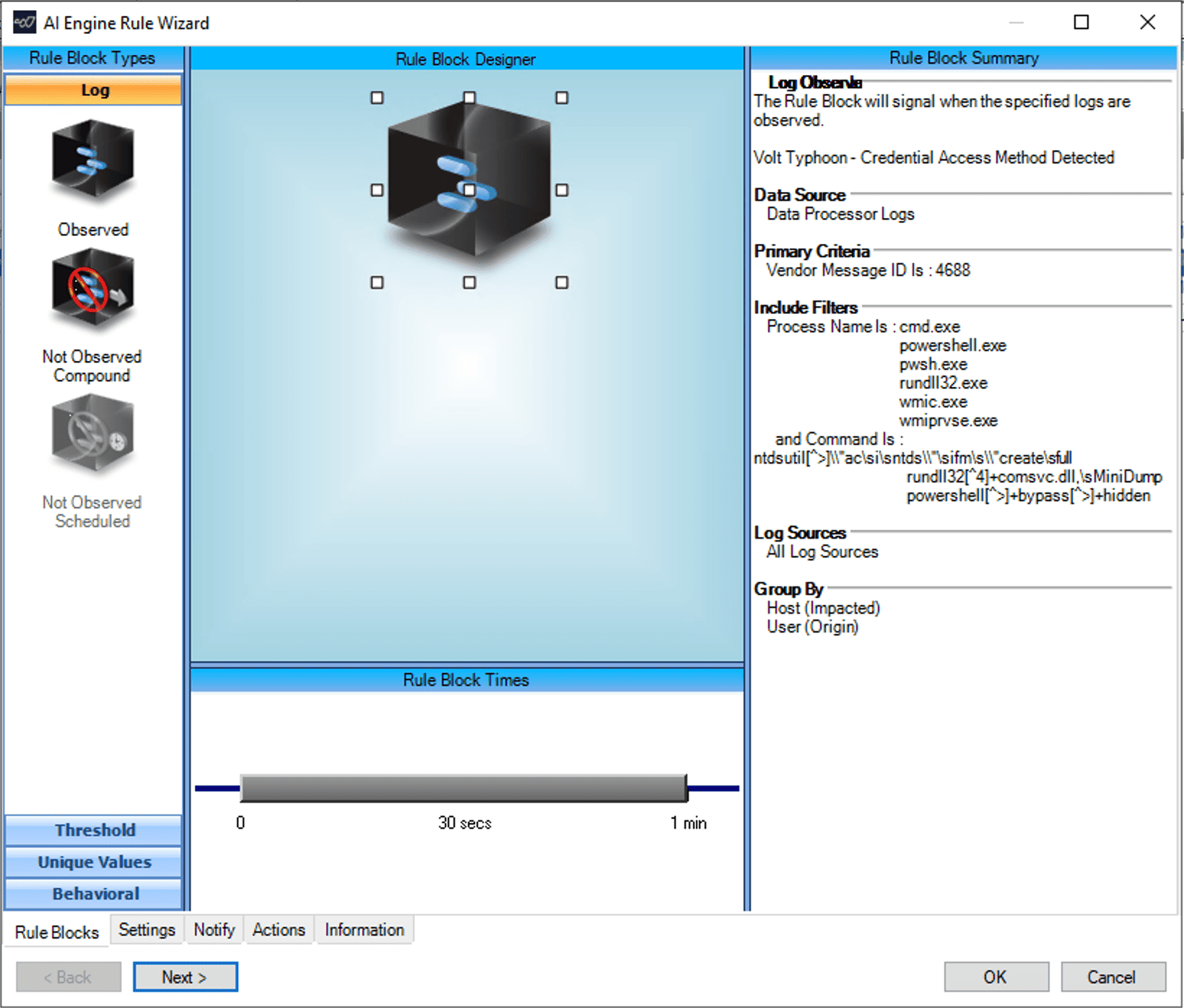
Rule 2: Credential Access Method Detected
In this rule, we are detecting the following TTPs:
Detecting NTDSUTIl use by creating installation media on domain controller:
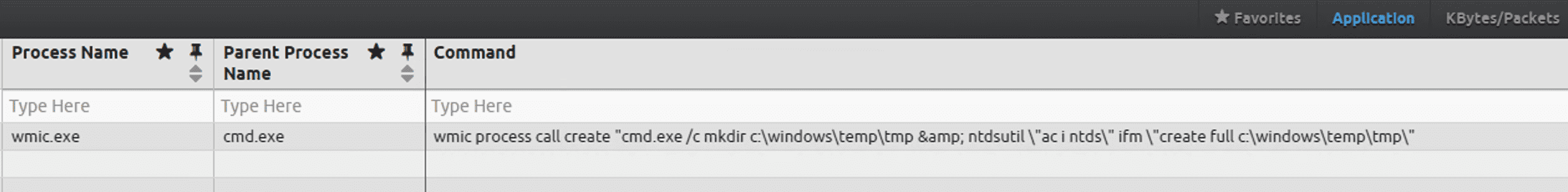
wmic process call create “ntdsutil \”ac i ntds\” ifm \”create full C:\Windows\Temp\pro Done
wmic process call create “cmd.exe /c ntdsutil \”ac i ntds\” ifm \”create full C:\Windows\Temp\Pro” Done
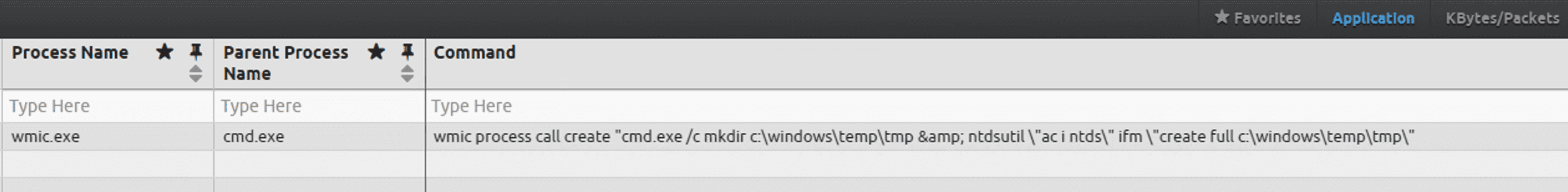
wmic process call create “cmd.exe /c mkdir C:\Windows\Temp\tmp & ntdsutil \”ac i ntds\” ifm \”create full C:\Windows\Temp\tmp\”
cmd.exe” /c wmic process call create “cmd.exe /c mkdir C:\windows\Temp\McAfee_Logs & ntdsutil \”ac i ntds\” ifm \”create full C:\Windows\Temp\McAfee_Logs\” Done
cmd.exe /Q /c wmic process call create “cmd.exe /c mkdir C:\Windows\Temp\tmp & ntdsutil \”ac i ntds\” ifm \”create full C:\Windows\Temp\tmp\” 1> \\127.0.0.1\ADMIN$\ 2>&1
Dumping LSASS memory for credential access:
cmd.exe /c powershell -exec bypass -W hidden -nop -E rundll32.exe C:\Windows\System32\comsvcs.dll, MiniDump 552
Rule 3: C2 IP Comm Detected
Create a list of IoCs (IPs). Black Lotus Labs Research is maintaining Volt Typhoon IoCs here that you can use.
Interesting Findings During our Investigation:
Port Forwarding: Once the attacker had compromised the victim, they did not use any malware to maintain persistence. Instead, they used windows netsh utility to create a proxy tunnel. This was achieved by leveraging windows built-in netsh command to do port forwarding. This is an uncommon and somewhat unique technique. We captured this in our Initial Access AIE Rule.
AD Credential Stealing Method: We usually see the attacker using VSSAdmin to create a shadow copy and then extracting NTDS.dit file from it. However, in this case, the actor created a copy of NTDS database, system, and security registry hives using a single command. This was accomplished by using ifm parameter in NTDSUTIL.exe command which creates an offline installation media to prepare an additional Domain Controller installation. We captured this in our second AIE rule.
No Admin Rights, No Problem: The attacker used non-admin accounts to perform discovery that still provided valuable information to map the environment. One such example is attacker pulling list of Domain Admin accounts.
For more information on how to enable these rules within your LogRhythm deployment, check out our community page to read more, download, and then import the rule into your platform.
The post Detecting Volt Typhoon TTPs – Security Spotlight appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Nicholas Tan. Read the original post at: https://logrhythm.com/blog/detecting-volt-typhoon-security-spotlight/
如有侵权请联系:admin#unsafe.sh