We are excited to announce our new notification rules feature, which helps you get notified about what really matters for you and your business with just a few easy steps.
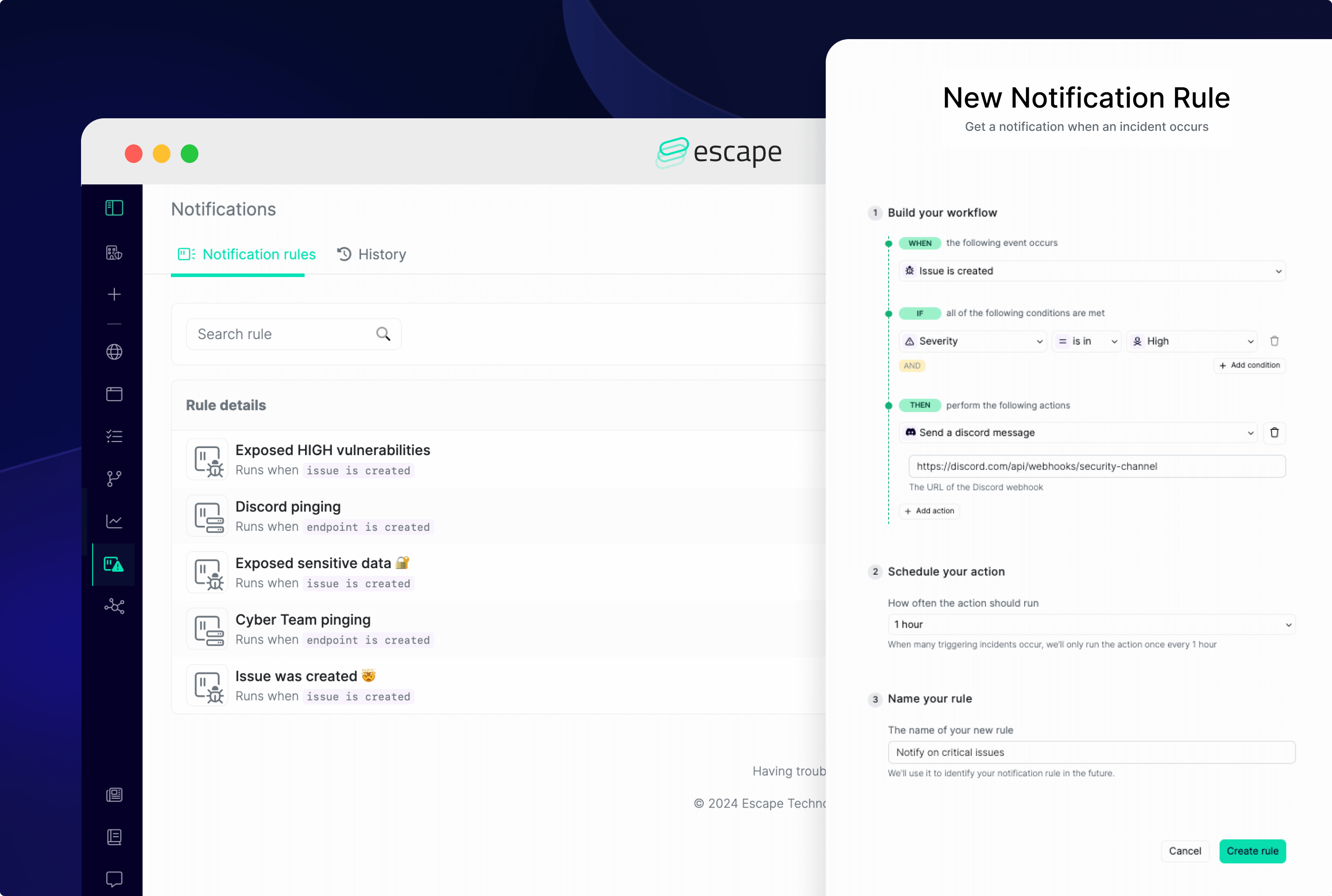
You can choose between 2 triggers:
- Issue is created
- Endpoint is created
Why?
Staying updated on the state of your API security is critically important for application security engineers. Every second counts in identifying and mitigating vulnerabilities that could compromise sensitive data or disrupt operations.
By implementing tailored notification systems, you can inject a sense of urgency into your incident response procedures, ensuring that potential risks are promptly identified and addressed.
But sometimes, you want to stay updated on less critical issues too. Don't worry, we're also here for you.
Here are the key benefits of implementing customized notification workflows:
- Timely Threat Detection: Customized notification workflows enable to detect and respond to the most critical issues quickly, reducing the window of opportunity for attackers to exploit vulnerabilities.
- Proactive Risk Management: By configuring triggers and conditions tailored to your specific security requirements, you can proactively monitor your endpoints
- Efficient Incident Response: With real-time alerts delivered through one or multiple communication channels, your team can quickly mobilize and coordinate your response efforts, minimizing the impact of security incidents and sensitive data breaches.
- Enhanced Collaboration: Customizable notification workflows facilitate seamless communication and collaboration among stakeholders, ensuring that the right information reaches the right individuals or teams promptly, fostering faster decision-making and more effective threat mitigation efforts.
Getting started
Here's how you can quickly set it up:
- In the left-hand sidebar, click Notifications.
- Click
Create new rule - Choose when your workflow should be triggered:
- When a new vulnerability has appeared in your application(s)
- When a new endpoint is created
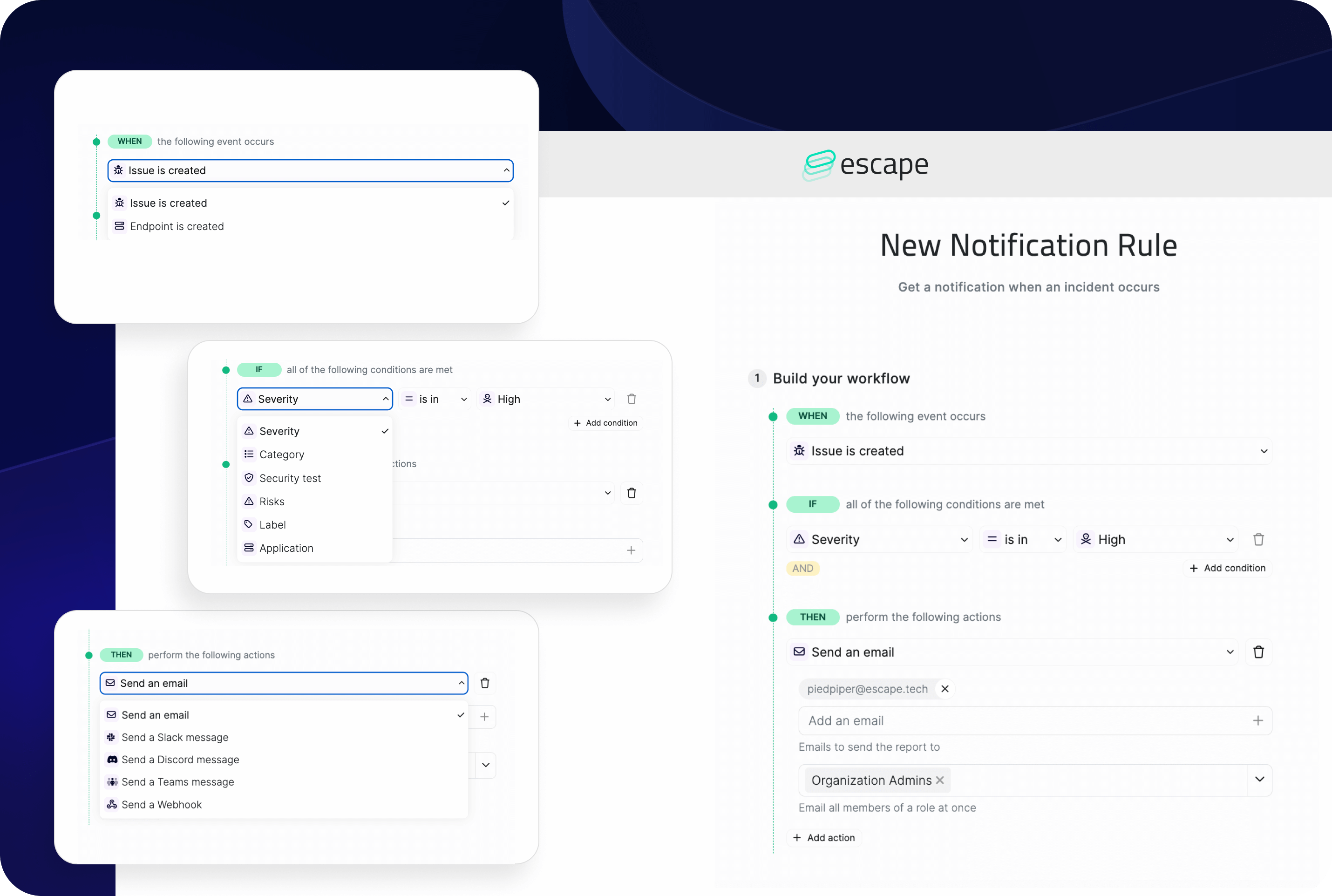
- Set up all the conditions you need for your workflow. Depending on your trigger, Escape's app will propose you different options:
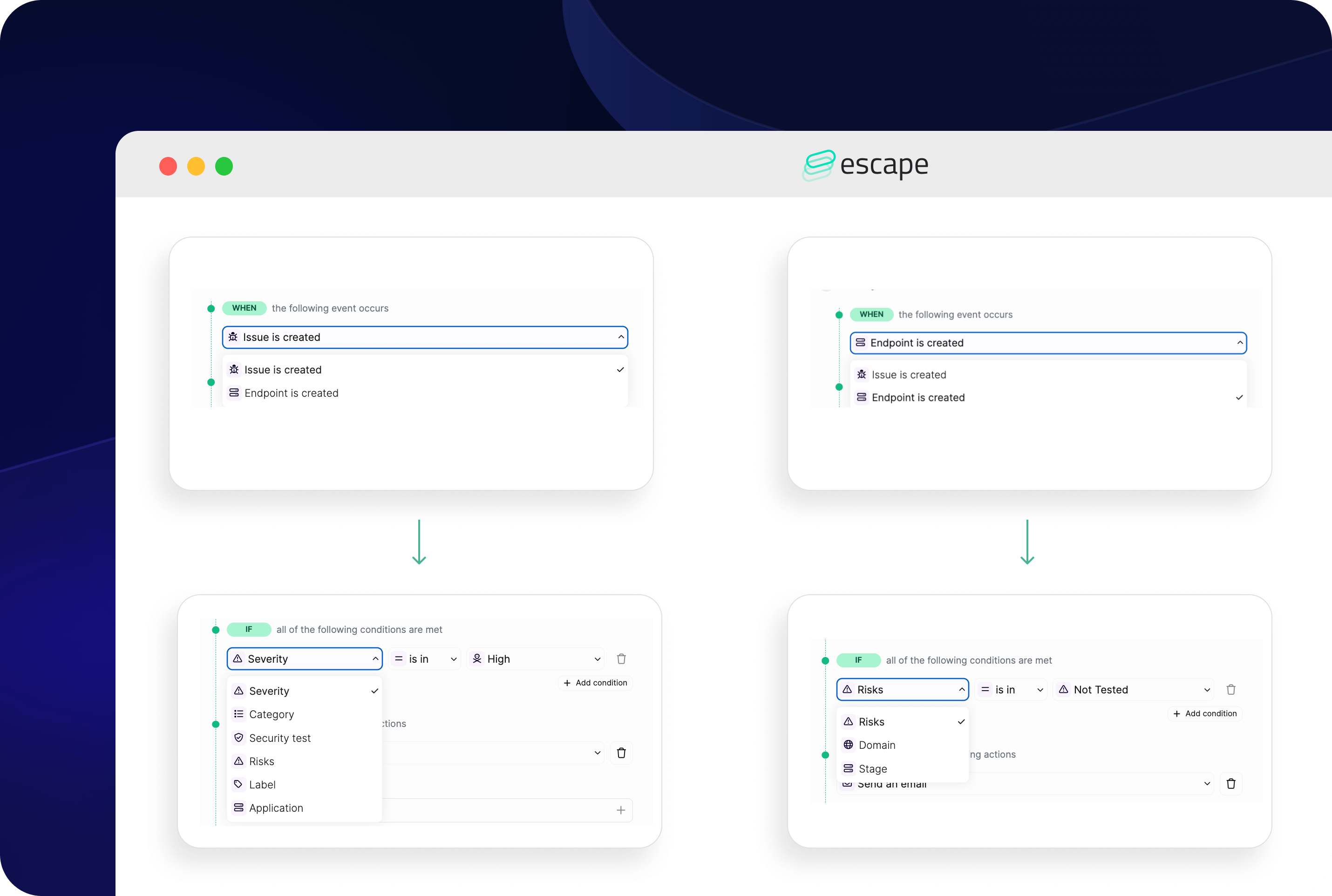
If your trigger is vulnerability-based, you have the possibility to filter by vulnerability severity, its category, security test, associated risks, and your custom label, and don't forget to filter by the application if you want to go even further!
5. Select among five actions that you want your rule to perform:
- Send an email
- Send a Slack message
- Send a Discord message
- Send a Microsoft Teams message
- Send a Webhook
We'll gradually introduce more use cases. If your case isn't among the four ones above, you can create a webhook for most applications.
6. Schedule how often the action should run
7. Name your rule and click on Create rule to save your workflow
And that's it! You can create as many notifications as your organization needs.
With this new feature, we hope you find it simpler than ever to customize your scan alerts to your needs. Try it out for yourself, and let us know what you think in our Discord community!
💡 Check out more product updates below:
- Dynamic authentication token generation feature
- Support for Insomnia collections, WP-JSON schema, Escape's public API, and additional business logic security tests
- What’s new for enterprise
- Compliance matrix product announcement
*** This is a Security Bloggers Network syndicated blog from Escape - The API Security Blog authored by Alexandra Charikova. Read the original post at: https://escape.tech/blog/introducing-notification-rules/
