2024-2-8 22:31:49 Author: flashpoint.io(查看原文) 阅读量:15 收藏
A first look at our latest advancements
Last year, our unwavering commitment to innovation culminated in the launch of Flashpoint Ignite, our all-in-one intelligence platform that combines cyber threat, vulnerability, physical security, and national security data and intelligence into one workspace.
Today, we’re introducing a set of powerful new capabilities and enhancements that are designed to provide a holistic view of risk.
Holistic understanding of the threat landscape
Cyber threat intelligence (CTI) analysts need a holistic view of the threat landscape to make informed decisions and develop effective strategies. By integrating data from across intelligence domains, analysts can begin to understand the correlation and interconnected nature of risks and prioritize effectively.
With this need in mind, we are pleased to introduce Flashpoint Fraud Intelligence and Vulnerability Intelligence to our Ignite platform. These upgrades offer a new range of intelligence possibilities, allowing CTI teams to connect disparate intelligence and eliminate data silos.
Fraud Intelligence
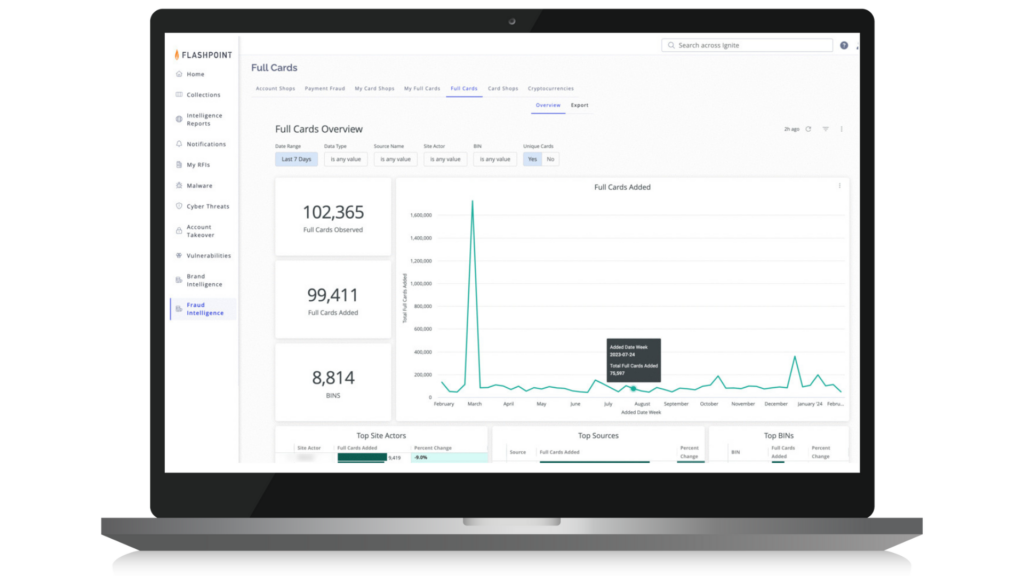
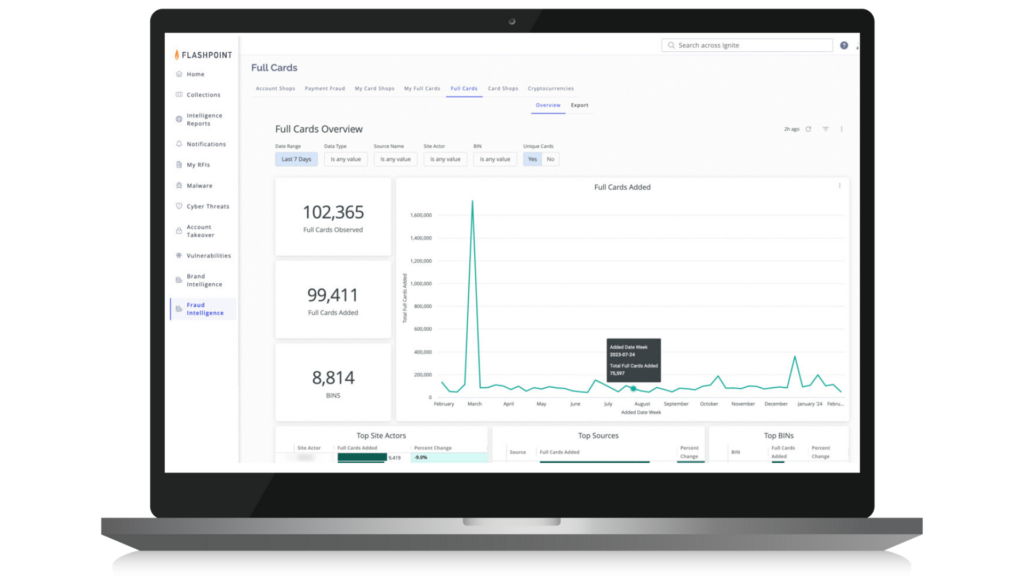
The landscape of financial fraud is evolving towards faster and more discreet methods of cashing out, as digital payment networks become more widely used. Scammers take advantage of these platforms to make speedy and harder-to-trace transactions, posing challenges for traditional transaction monitoring methods that may struggle to keep up with the rapid pace of fraudulent activity.
That’s where Flashpoint Fraud Intelligence comes in: helping CTI teams identify indicators of fraud across the cybercriminal economy and take swift action to prevent financial loss and reputational damage. It offers deep insights into how fraudsters operate, revealing stolen credit cards, payment methods, account credentials for sale, and suspicious cryptocurrency transactions.
Teams can use Fraud Intelligence to:
- Identify and monitor illegal marketplaces where stolen account credentials, including usernames and passwords, are traded;
- Investigate and identify the sale and use of stolen credit card information across card shops, data breaches, and illicit communities;
- Track fraudulent cryptocurrency activities, including money laundering schemes, suspicious wallets, and exchanges;
- Benefit from the flexibility to search for fraud indicators with or without bank or customer identifiers options, effectively identifying and investigating deceptive activities aimed at your organization.
Vulnerability Intelligence
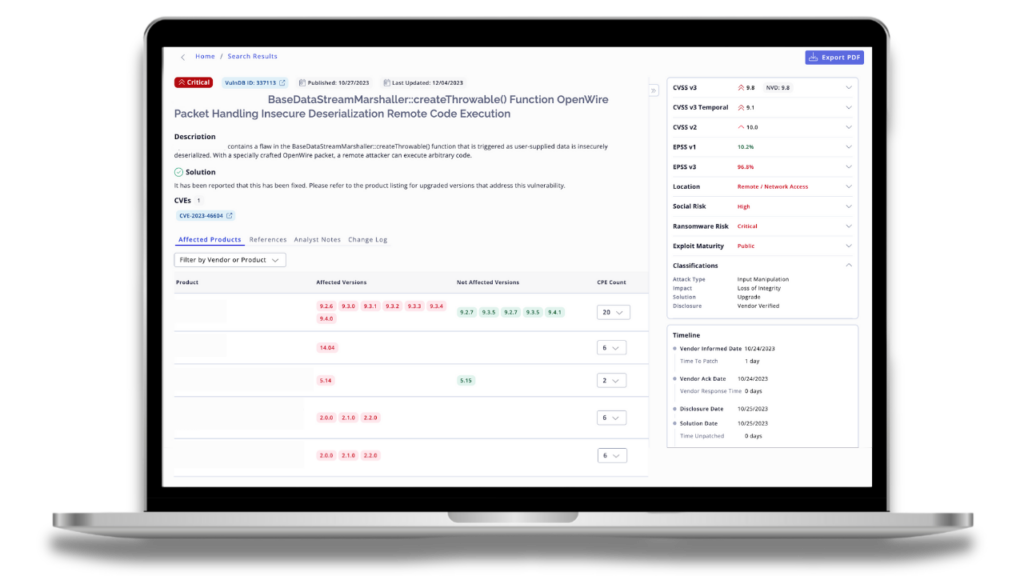
The continual growth of annually disclosed vulnerabilities outpaces the ability of organizations to monitor and remediate them effectively. This creates a daunting task for security teams, forcing them to make difficult decisions around prioritization, often resulting in the deprioritization of certain vulnerabilities due to resource constraints. In fact, a recent Booz Allen Hamilton Retail & Hospitality Information Sharing and Analysis Center (RH-ISAC) survey found that vulnerability identification and remediation is the top initiative that CISOs are prioritizing in 2024.
Flashpoint’s Vulnerability Intelligence provides CTI and cybersecurity teams with unparalleled visibility and context into vulnerabilities– notifying them of vulnerabilities on average two weeks faster than NVD with early coverage of zero-day and emerging vulnerabilities. Compared to CVE and NVD, Flashpoint details an additional 40 percent of documented in-the-wild vulnerabilities. It provides a wide coverage of sources, vendors, and products (endpoints—IT, OT, and IoT).
Teams can use Vulnerability Intelligence to:
- Identify risk faster and significantly reduce time to discovery and mitigation of vulnerabilities, including over 100,000 non-CVE vulnerabilities;
- Leverage custom severity scoring and timely exploit intelligence to better prioritize vulnerabilities and potential impact on their organization;
- Create internal alignment between CTI and Vulnerability Management teams to improve efficiency, simplify workflows and save time and resources.
Enhance your threat analysis
At Flashpoint, we’re constantly innovating to maintain our position as the gold standard in threat intelligence. Frost & Sullivan summed it up perfectly when they recently said “Flashpoint, a transformative leader and catalyst, shapes its corporate culture by harnessing purpose and mission to protect what matters most to fuel innovation.” This dedication to excellence is reflected in our flagship product, Flashpoint Cyber Threat Intelligence (CTI). Now, we have expanded its core offerings to include increased data correlation using generative AI, new visualizations, and more relevant information recommended based on the specific challenges faced by each organization.
The goal of these new enhancements is to make threat intelligence more accessible, actionable, and meaningful to our customers, eliminating the need to spend excessive time and resources searching for it.
Ignite AI
Ignite AI allows customers to ask questions using natural language search and receive answers from Flashpoint Intelligence Reports. Use Ignite AI to streamline search workflows and find more relevant answers, especially those related to timeframes like “recent events”, “this month”, or “in 2024”. Its fast speed and scalability facilitate quicker and more efficient comprehension of diverse topics, including industries, verticals, regions, threat types, actors and groups, as well as trending subjects like technical, cyber, policy, geopolitics, and infrastructure threats.
Threat actor profiles
The task of recognizing, attributing, and describing a threat actor is notoriously challenging and labor-intensive. That’s why our dynamic threat actor profiles are designed to provide you with an automated summary of a threat actor’s pattern of life. This includes their known aliases, the communities they visit, and a heat map of their posting activity over their lifetime. You can quickly gain an overview of actors’ activity using the new “baseball card” view. By hovering over usernames, you can reveal posts, aliases, and easily access the full profiles to understand who is targeting your organization and how they operate.
Configurations
This new central hub provides you with the ability to customize the Ignite platform according to your organization’s specific requirements. You can curate a personalized list of important resources, ranging from applications and brands to BINs, buckets, domains, and IP addresses. Configurations allows you to define your interests, personalize your workflows showing you the most relevant data and insights, making it easier to find what matters and cut through the noise.
Data exposure alerting
Our enhanced Data Exposure Alerting capabilities enable you to scan your code, cloud, and internet infrastructure to detect exposed data, leaks, and threats. This feature includes four main functionalities: Cloud and Internet Infrastructure Monitoring, which tracks S3 buckets and IP addresses; Code Repositories Monitoring, which scans GitHub, Gitlab, and Bitbucket for exposed credentials or leaked code; and Pastebin Takedowns, which allows users to request removal of malicious or unwanted pastes from Pastebin. With targeted queries and timely notifications, you can proactively prevent malicious actors from exploiting exposed data for illicit activities.
Jump-start your intelligence journey
Flashpoint Ignite goes beyond traditional threat intelligence, empowering organizations to proactively detect and address cyberattacks, fraud schemes, brand threats, and vulnerabilities. Make faster, smarter security decisions to protect your valuable data, prevent financial losses, and optimize your security resources.
Book a demo today and discover how Flashpoint Ignite can give you a comprehensive view of your organization’s risk profile.
如有侵权请联系:admin#unsafe.sh