This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our seventh Threat Horizons Report (full version) that we just released (the official blog for #1 report, my unofficial blogs for #2, #3, #4, #5, #6, #7 and #8).
My favorite quotes from the report follow below:
- “Credential abuse resulting in cryptomining remains a persistent issue, with threat actors continuing to exploit weak or nonexistent passwords to gain unauthorized access to cloud instances, while some threat actors are shifting to broader threat objectives.” [A.C. — the new insight here is lack of change!]
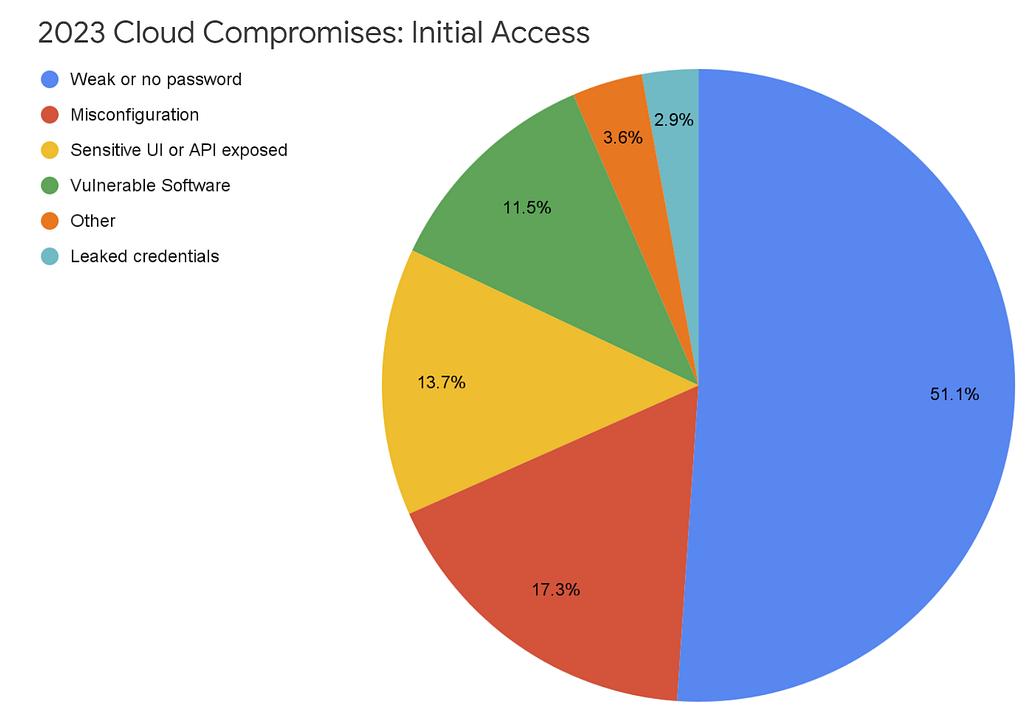
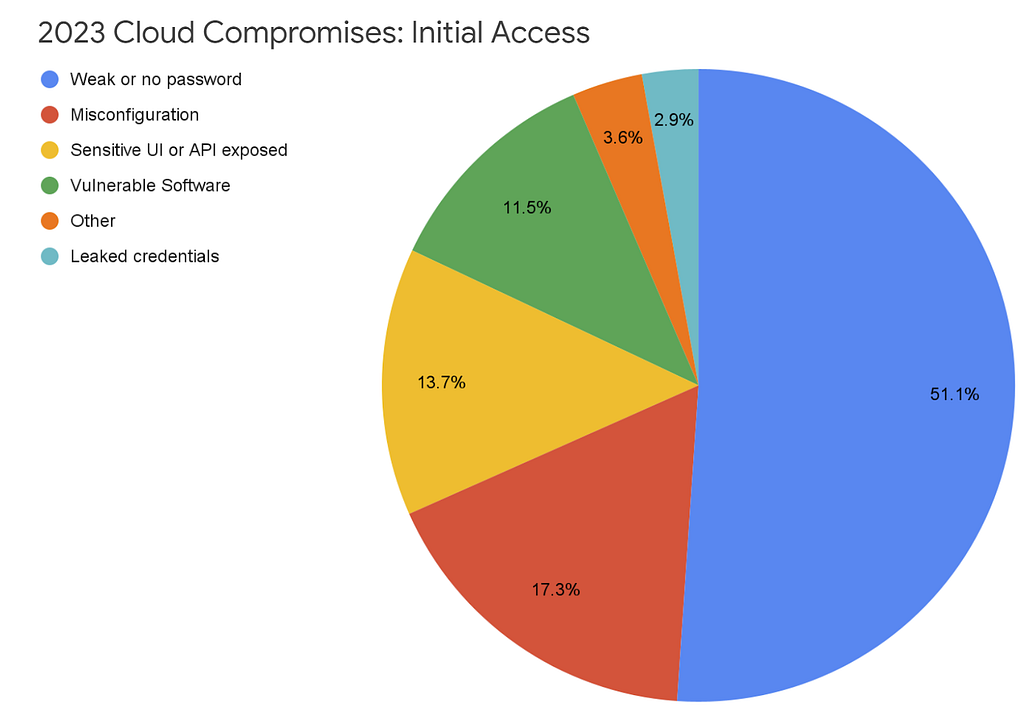
- “Credential issues remain the predominant security oversight observed among Google Cloud customers. Over half of incident data shows that threat actors are compromising Cloud instances with weak or no passwords on common remote access protocols, Secure Shell (SSH) and Remote Desktop Protocol (RDP) to gain unauthorized access to Cloud instances. ” [A.C. — 1980s called, they want their attack back!]
- “Given that harvesting such credentials is low-effort for a threat actor, this trend will likely continue to affect organizations that fail to meet basic standards of security.”
- “Cryptomining remained one of the principal motivations behind threat actors who abused cloud access, accounting for nearly two-thirds of observed activity. This quick and easy money maker serves a clear profit motive for criminal actors, as it allows threat actors to use a victim’s cloud processing power to mine for cryptocurrency in a shorter period of time. ” [A.C. — free money for malefactors, why change? If this keeps being profitable, they will keep doing it, we need to … ImposeCost 🙂]
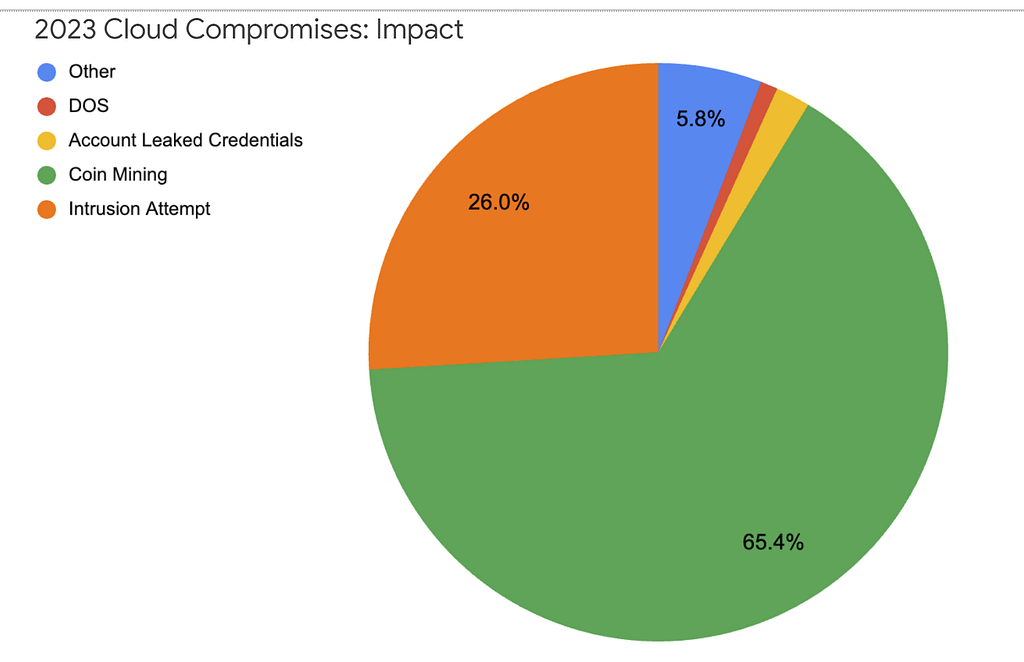
- “Several times throughout 2023, we observed threat actors leverage illicit cloud access in an attempt to infect third parties. This less common tactic, constituting over 25% of observed incidents, has significant security impacts for organizations on both sides of the attack. ” [A.C. — this can be the HVAC access all over again, but worse; your cloud account may be compromised to then compromise somebody else…]
- “Use Essential Contacts to ensure every cloud service used by an organization has point of contact (POC) information updated so cloud providers can reach impacted clients promptly.” [A.C. — this is WAY more important than what it sounds like!]
- “While weak credentials and misconfigurations are often causes for a threat actor’s initial access to cloud environments, other factors, such as weak storage defenses, application vulnerabilities, and third-party issues also led to cloud system compromises, resulting in ransomware and data theft ”
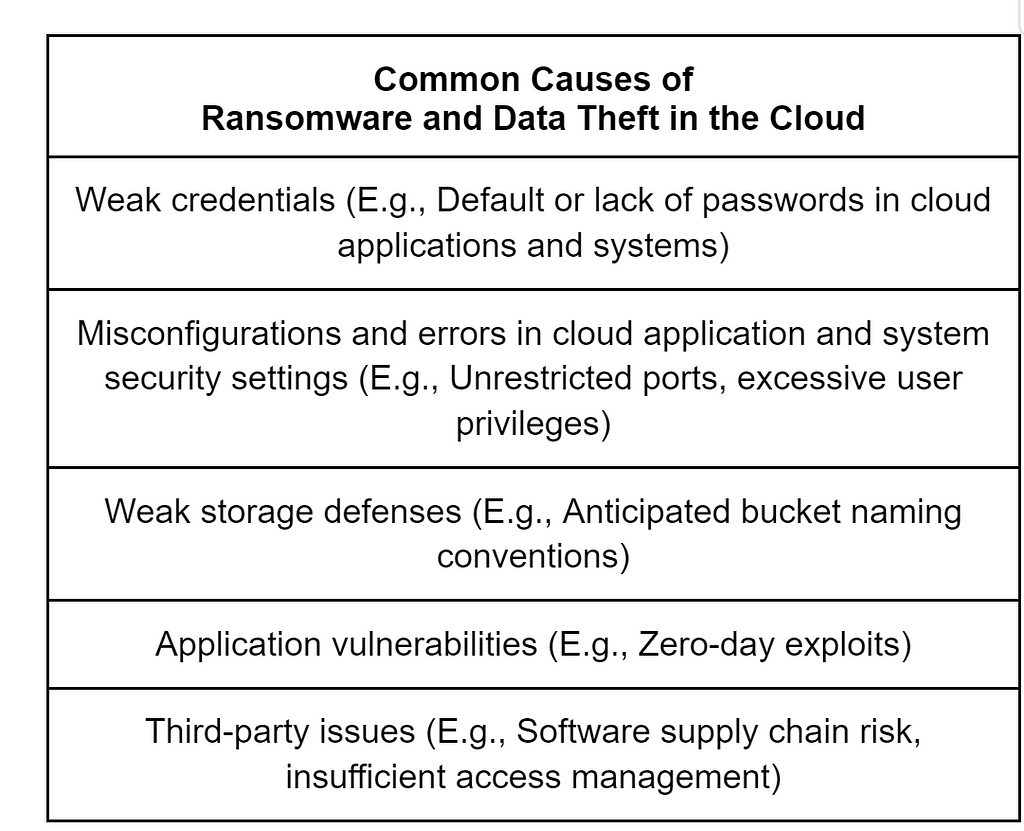
- “Google Cloud Storage (GCS) team observations indicate threat actors are probing weak cloud storage bucket naming conventions to exfiltrate data (Figure 2). Uncategorized threat actors have attempted to use a bucket naming approach that would allow them to anticipate which specific bucket would most likely be used next by a user.” [A.C. — this may not be new, but this matters for new reasons in the cloud]
- “Threat actors targeting cloud environments began prioritizing data exfiltration over data encryption and stolen data advertisements grew in 2023, as threat actors demonstrated an increased focus on publicly releasing exfiltrated data from multiple cloud providers.” [A.C. — ransomware in the cloud is often different from the classics]
Now, go and read the report!
Related posts:
- Google Cybersecurity Action Team Threat Horizons Report #8 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #7 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #6 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #5 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #4 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #3 Is Out!
- Google Cybersecurity Action Team Threat Horizons Report #2 Is Out!
- Illicit coin mining, ransomware, APTs target cloud users in first Google
- Cybersecurity Action Team Threat Horizons report
- All past and future reports are posted at Google Cybersecurity Action Team site.
Google Cybersecurity Action Team Threat Horizons Report #9 Is Out! was originally published in Anton on Security on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from Stories by Anton Chuvakin on Medium authored by Anton Chuvakin. Read the original post at: https://medium.com/anton-on-security/google-cybersecurity-action-team-threat-horizons-report-9-is-out-a1741432bd64?source=rss-11065c9e943e------2