2024-2-2 06:51:58 Author: blog.sucuri.net(查看原文) 阅读量:22 收藏
Emerging in 2022, a phishing tool known as Greatness has caught the attention of our research team due to its coordinated efforts to breach Microsoft 365 accounts and presence on compromised websites. More disturbingly, it has shown effectiveness against multi-factor authentication (MFA), elevating the potential threat level. Identified as a Phishing as a Service (PhaaS) platform, Greatness is equipped to aid its operators in executing sophisticated phishing attacks.
In this post we’ll examine the risks that the platform poses, document features, and outline steps you can take to mitigate phishing threats like this one.
The “Greatness” phishing kit: a PhaaS offering
In the past year our team has found components of the “Greatness” phish kit on a number of hacked websites. Greatness operates as a Phishing as a Service (PhaaS) platform, providing a number of features and components for bad actors to conduct their phishing attacks against Microsoft 365 accounts. URLScan results show thousands of affected pages related to this kit.
Once bad actors acquire a license and make the payment, they are provided with the software used to launch these attacks. The software can be hosted anywhere but we have seen a number of infections on compromised websites, hidden deep within the website structure.
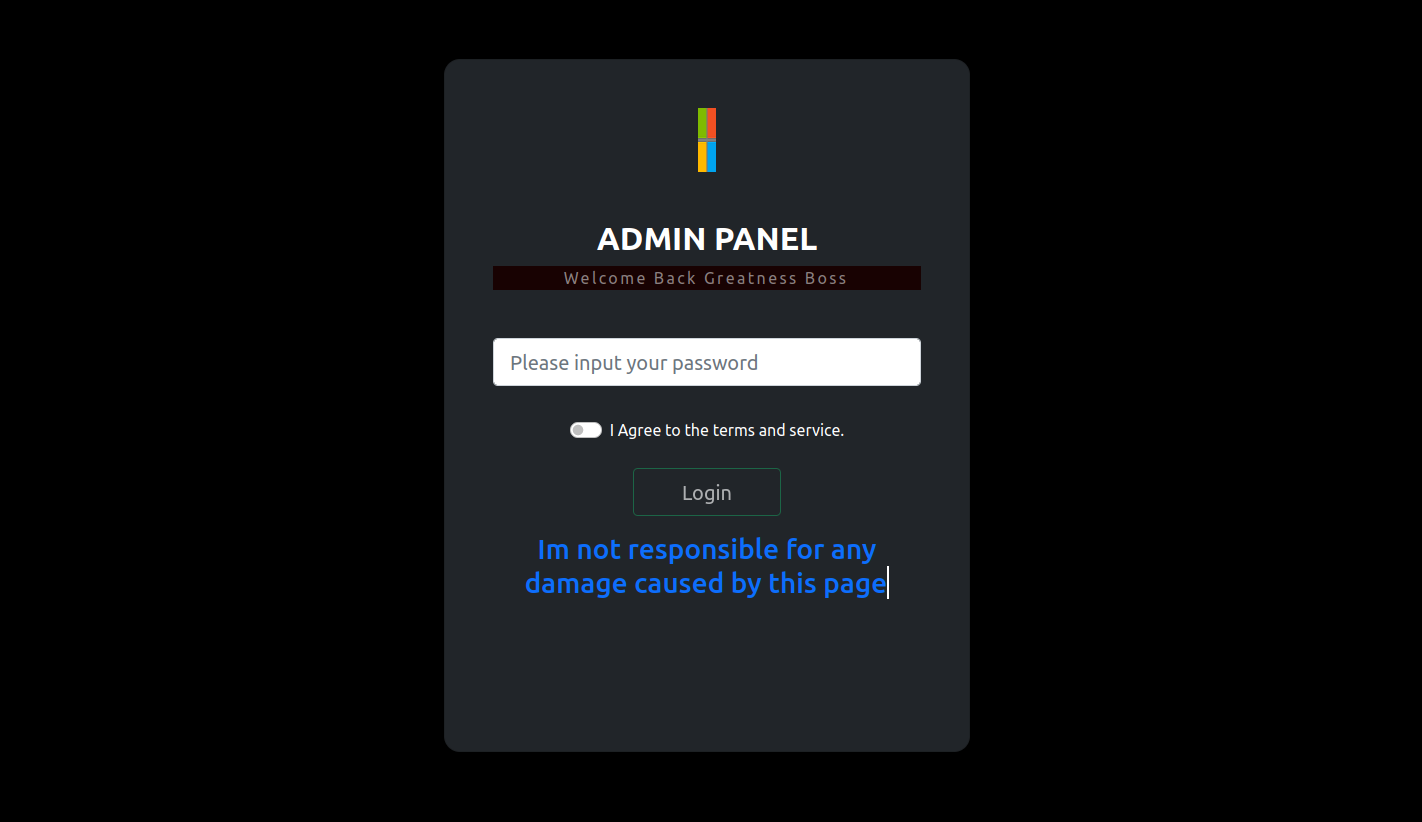
The “Greatness” platform serves as command control for attackers, offering configuration options for personalized phishing attempts. These alarming capabilities demonstrate the potential for harm that the Greatness tool holds, emphasizing the need for awareness and protective measures to counter phishing malware.
Results dashboard
The Results dashboard acts as the command center, providing a detailed view of captured credentials. This feature allows attackers to assess the effectiveness of their phishing efforts.
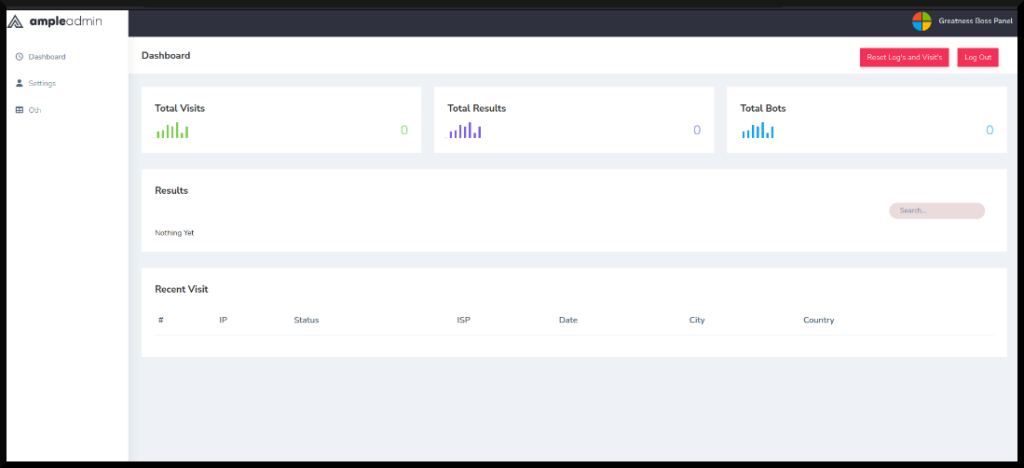
Campaign builder ‘Office Page’
The ‘Office Page’ functions as a campaign builder, enabling phishers to craft detailed phishing campaigns, create convincing emails equipped with deceptive links, or create attachments embedded with malware. The platform facilitates easy creation of attack templates and offers customization for tailoring the phishing attack, such as modifying backgrounds to mimic various file types and an ‘autograb’ function, streamlining the phishing process by setting the target account in advance.
Authentication and session cookie retrieval
Greatness uses a sophisticated authentication procedure. After a victim enters their password, the tool verifies if multi-factor authentication (MFA) is enabled. If MFA is active, the tool prompts victims for additional information. Utilizing Microsoft’s API, the tool can then procure a valid session cookie.
Configuration and settings
Configuration options include checking server status, uploading new configuration files, and IP access restrictions. Interestingly, the tool allows threat actors to specify alternate methods for receiving the stolen credentials, such as via a bot on Telegram or through an additional email account, providing insights into the advanced methods being employed in phishing campaigns.
Security and evasive techniques
To prevent theft, Greatness relies on several sophisticated security techniques. For starters, the source code is heavily obfuscated, making it more difficult for unauthorized users to understand the code and copy the tool.
Furthermore, the generated HTML phishing files communicate with a central server to validate the API key, ensuring the authenticity of the client. Any mismatch results in the server rendering a denial page instead of the phishing content.
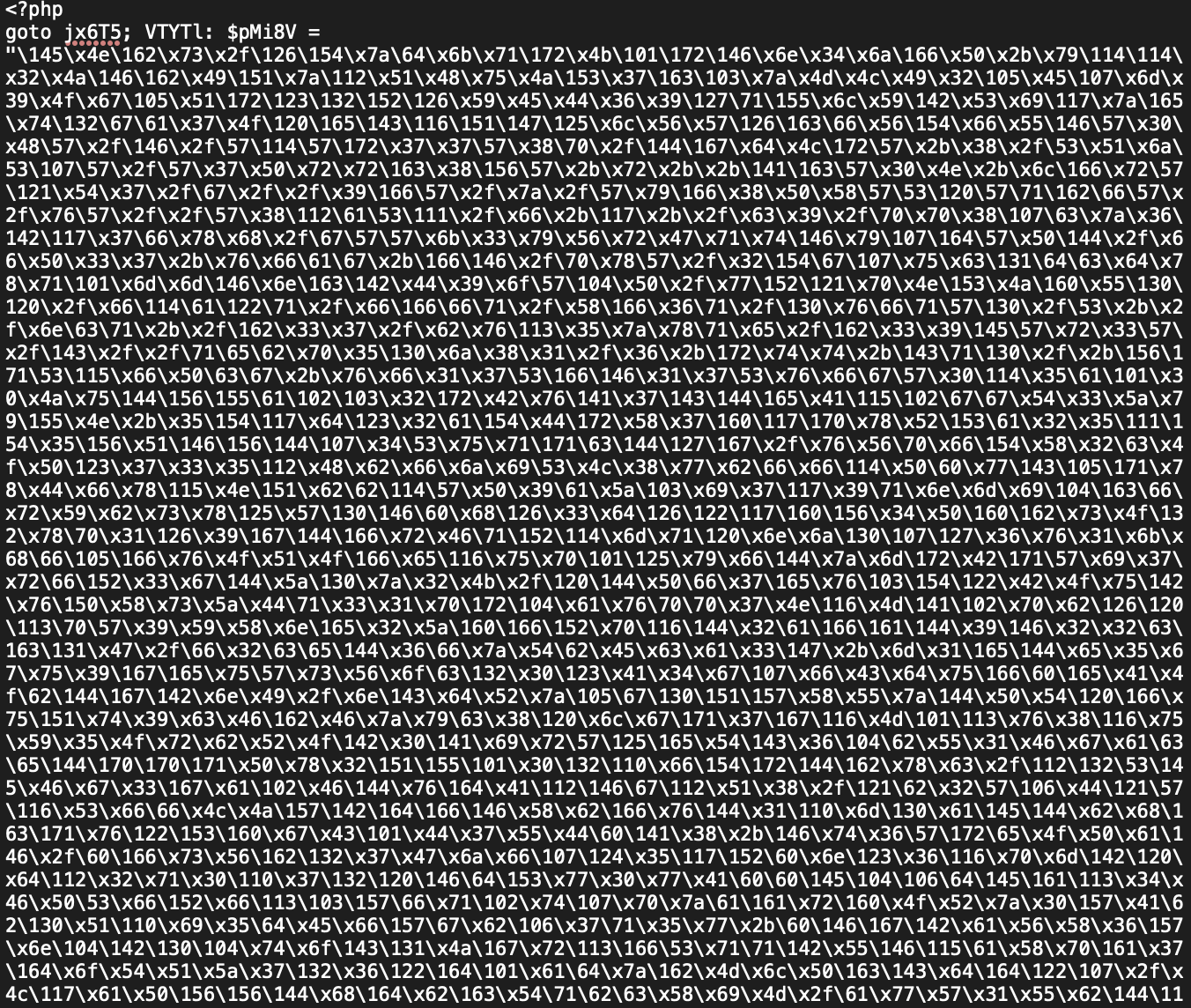
The location of the central server, crucial for verification, is concealed in the encoded configuration file, making it elusive and subject to change across installations and over time.
Encoded configuration file httpd.grt used by the toolkit to find the central server:
API
The API is the backbone of the service. Each affiliate or user must possess a valid API key to use the kit. Without a valid key, the phishing page refuses to load, and an “invalid API key” message is displayed. Configuration options in the panel enable phishers to insert their unique API key.
The service API integrates various functions like verifying the affiliate’s key, blocking specific, unwanted IP addresses from viewing the phishing content, and crucially, facilitates covert communication with the real Microsoft 365 login page on behalf of the victim.
In essence, the phishing kit and API work in unison, executing a “man-in-the-middle” attack. It tricks the target victim into disclosing their information to the API, which is then submitted in real-time to the legitimate login page. This enables phishers to steal usernames, passwords, and authenticated session cookies in cases of MFA-enabled victims.
Since authenticated sessions usually time out after some time, quick data extraction becomes vital. A Telegram bot is used to quickly alert the attacker about valid cookies, enabling them to act before session timeouts if the target is of significant interest.
Indicators of compromise
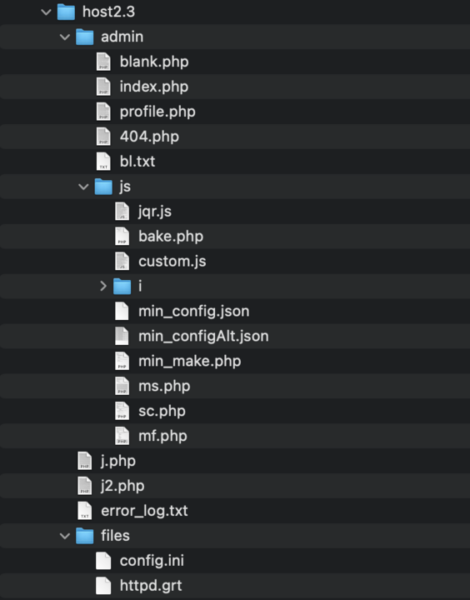
During our investigation we’ve found this malware hidden in various different directories. Webmasters can search for some of the files as they appear to have static names that don’t change, including but not limited to:
- host[N]/admin/js/mf.php
- host[N]/admin/js/ms.php
- host[N]/admin/js/sc.php
- host[N]/files/config.ini
- host[N]/files/httpd.grt
- host[N]/j.php
- host[N]/j2.php
- …etc…
The file httpd.grt is the configuration file the tool kit uses to communicate with the central server, while admin/js/mf.php is used to access the admin panel for the toolkit.
You can search for these file names or scan with our website security platform if you believe your website has been compromised. I have included a screenshot with the file structure below for reference:
Potential risks and threats
With this toolkit, even novices with little technical knowledge can launch damaging phishing attacks. This accessibility amplifies the potential for harm, as it lowers the threshold for individuals to participate in and profit from cybercrime.
Perhaps the most concerning aspect is this phishing kit’s capability to outmaneuver multi-factor authentication. MFA is currently one of the most effective security measures employed by companies to protect login credentials. Prioritizing the development of advanced security measures effective against such attacks is becoming increasingly vital.
Concluding remarks: the evolving face of phishing attacks
Cybersecurity is an ongoing chess match between defenders and attackers. Tools like “Greatness” are indicative of how threat actors are enhancing their methods to outsmart existing security measures.
In this particular instance, phishers are exploiting hacked websites to upload their phishing kits and use the website resources to target Microsoft 365 users. By understanding and recognizing these threats, you can stay one step ahead to protect your website against malicious phishing kits.
Tips for mitigating phishing
Here are seven steps you can take to prevent phishing from exploiting your website and server resources.
1 – Run a malware scan on your site.
You can opt to check for website malware yourself, or leverage a reputable security company like Sucuri to scan your website for malware.
Regardless of how you check for infection, the scan should be deep and comprehensive, covering all aspects of your website: files, databases, posts, and the web server itself.
For example, we often find PHP mailer scripts and other malicious code lurking on the server level that are used for spamming, so don’t skip this step. You can also check your mail server logs to identify any anomalies in outbound emails, which may imply they’re being used for phishing or spam campaigns.
2 – Remove any suspicious files or scripts as soon as possible.
If a malware scan uncovers any suspicious files or scripts on your website, remove these ASAP. Be sure to make a backup of your website before making any changes. Files can either be replaced with fresh copies, or you can revert to a recent uninfected website backup.
Check out our how to clean a hacked website guide for step-by-step instructions.
3 – Change your account passwords.
This includes CMS, FTPs, databases, and SSH. Make sure you have unique and strong passwords for each of your accounts. Don’t overlook dormant or rarely used accounts, as hackers often exploit these to gain unauthorized access.
4 – Update your website software and patch whenever a new version is available.
You’ll need to patch all themes, plugins, core CMS, and any other website software to their latest versions on a regular basis to help mitigate risk from known vulnerabilities and bugs.
5 – Monitor for blocklisting by Google and other search authorities.
Your site may be blocked by Google and other blocklisting authorities due to phishing or other malicious activities. If you’re getting site warnings from search authorities, you’ll want to conduct an online status check and request a site review after your site is completely clean.
6 – Set up file integrity monitoring
Implementing a file integrity monitoring system can help you detect unauthorized changes to your website’s files, which may indicate the presence of phishing or other website malware.
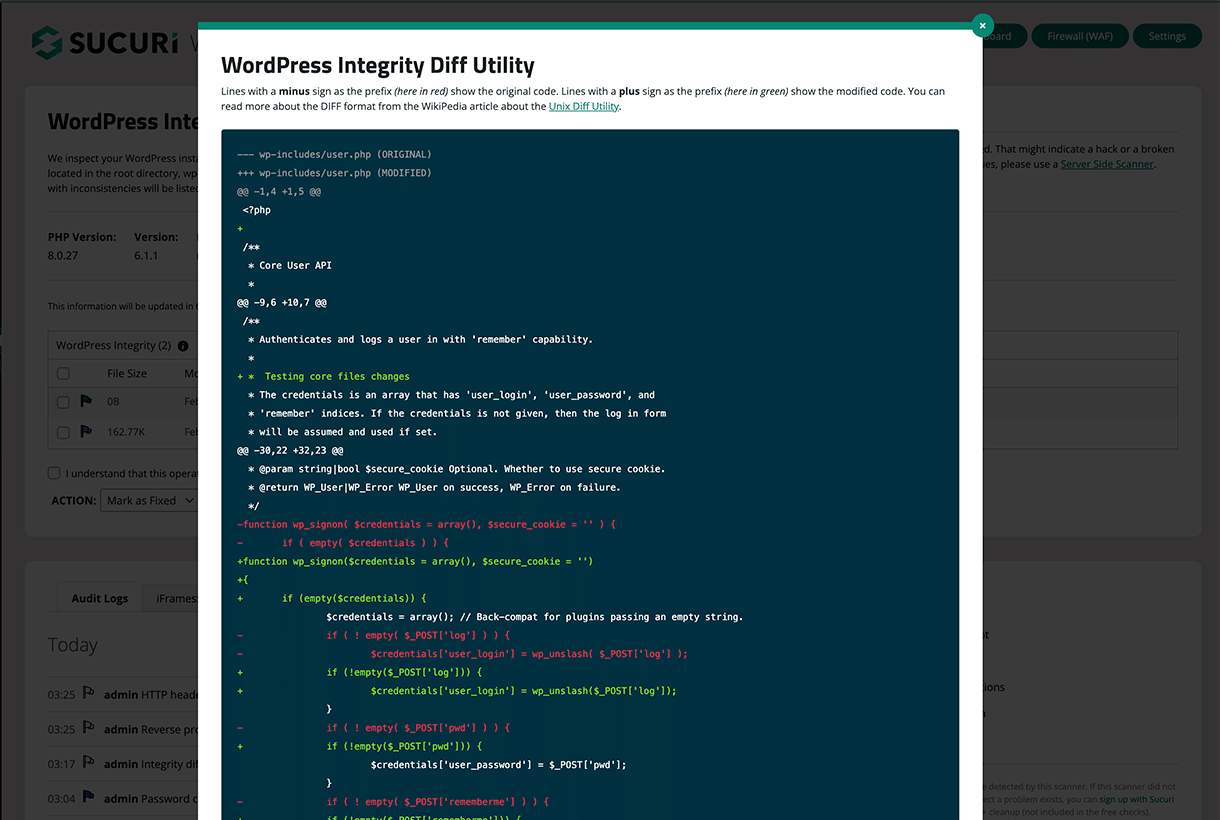
WordPress users can install the Sucuri Security WordPress plugin to check the integrity of your core WordPress files, including PHP, JavaScript, and CSS.
7 – Put your website behind a firewall.
A web application firewall can help harden your site against attack, stop bad bots and brute force attacks, and virtually patch known vulnerabilities to prevent infection from occuring in the first place. We offer a 30 day trial so you can check out the features.
If you suspect that your website has been involved in phishing or may have a kit installed somewhere and you need a hand, our skilled analysts are available 24/7 to help clean up malware!
如有侵权请联系:admin#unsafe.sh
