
2024-1-25 06:23:33 Author: securityboulevard.com(查看原文) 阅读量:17 收藏
The online commercial banking industry is experiencing a rising challenge with the subtle yet impactful presence of reverse proxy attacks, particularly in the form of reverse proxy phishing. As financial institutions continue to embrace digital transformation, the threat landscape has expanded, bringing reverse proxy attacks to the forefront of the commercial banking sector.
Read on to discover the formidable cyber threat challenging commercial banking, urging a vigilant defense for financial security. It’s time to explore the elusive world of reverse proxy attacks targeting operations and grasp the crucial need for safeguarding. Understanding the techniques of reverse proxy phishing, a significant risk demanding attention, will arm your business with necessary knowledge to thwart and fortify defenses.

RECOMMENDED RESOURCE
The Economics of Account Takeover Attacks
When Reverse Proxies Attack
At its core, a reverse proxy serves as a mediator between a bank’s internal servers and external clients, facilitating requests on behalf of the server. In contrast to conventional proxies, which forward client requests to the server, reverse proxies operate in the opposite direction by receiving requests from clients and directing them to the relevant server. While this architectural setup provides advantages such as load balancing, improved performance, and enhanced security, it is essential to distinguish this beneficial role from the potential risks associated with reverse proxy attacks, especially in the context of phishing.
Unlike traditional phishing, where attackers create deceptive websites to trick users into providing sensitive information, reverse proxy phishing introduces a more dynamic and elusive approach. In this threat, cybercriminals leverage the reverse proxy mechanics as a way to intercept and manipulate user interactions with legitimate banking websites—all in real-time.
This distinction is significant because, in reverse proxy phishing, the deceptive element operates behind the scenes, making it challenging for users to identify the malicious activities. The reverse proxy acts as an intermediary, allowing attackers to gain immediate access to sensitive information, including login credentials and multi-factor authentication (MFA) codes, without the need for the user to visit a fraudulent site. This level of sophistication and real-time access sets reverse proxy phishing apart from conventional phishing methods.
The Real-World Mechanics of Reverse Proxy Phishing
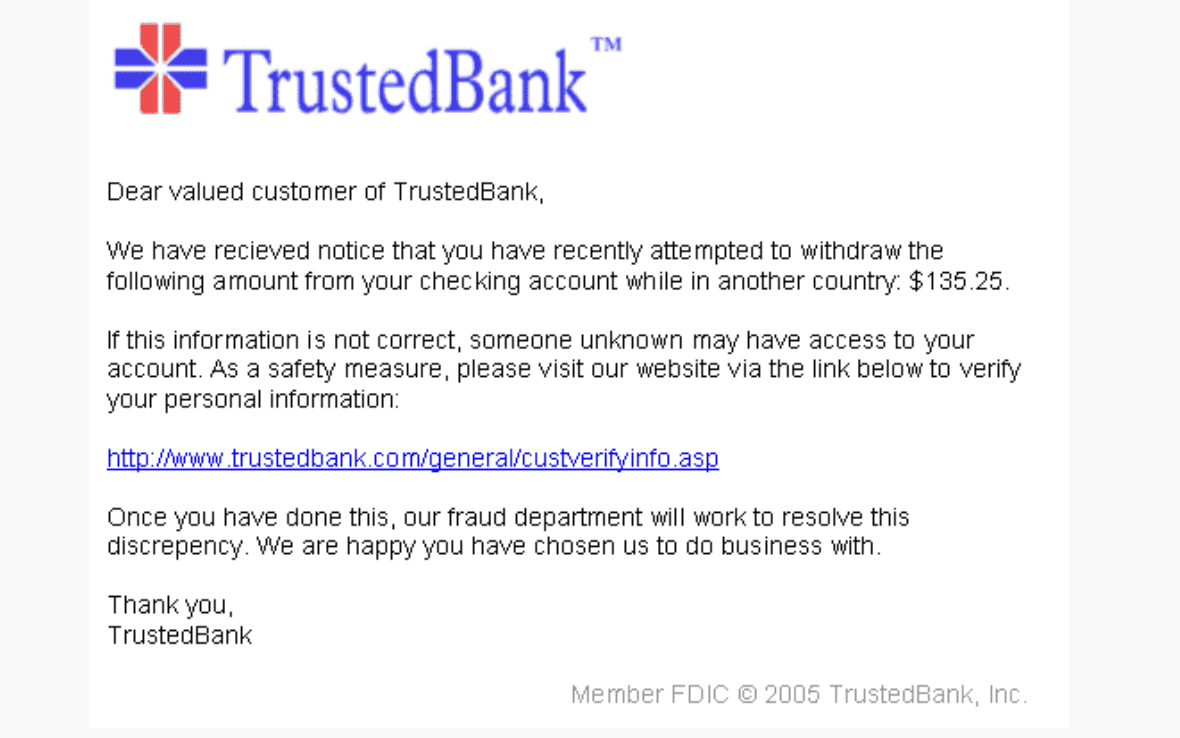
Reverse proxy phishing in the online banking sector involves a straightforward yet sophisticated process, as cybercriminals employ tactics to deceive users and compromise information. Attackers can create deceptive websites that mimic legitimate banking portals, tricking users into entering their credentials.
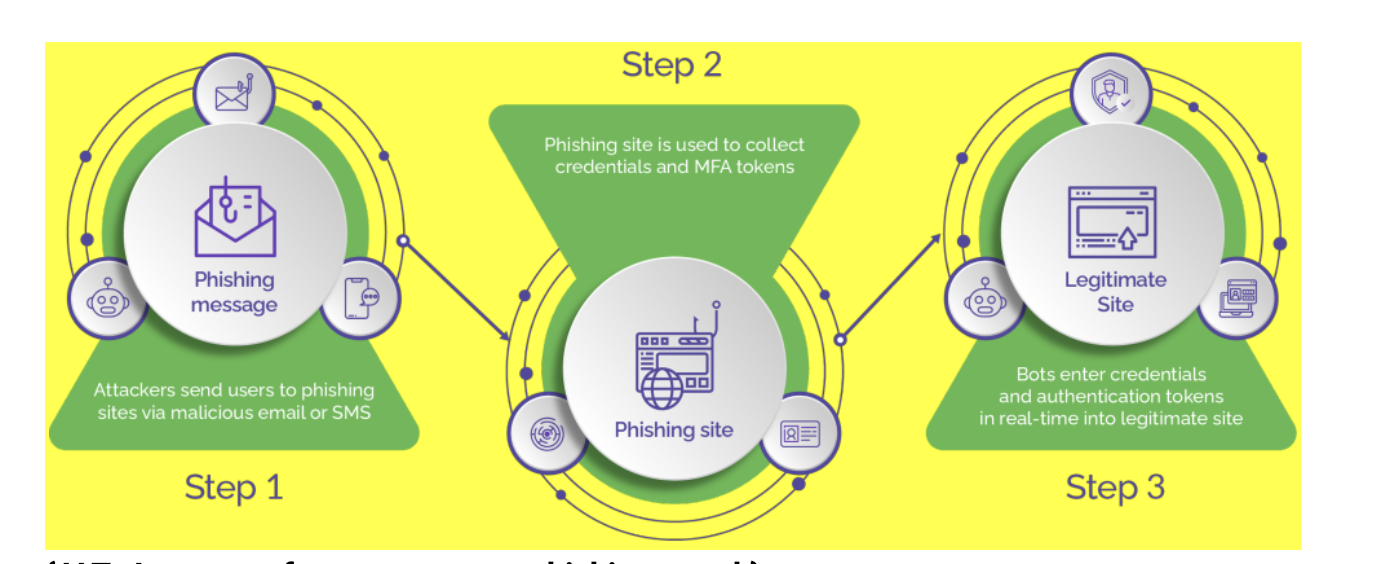
Meticulously personalized using publicly available information, reverse proxy phishing emails convincingly mimic the communication style and branding of legitimate businesses. In fact, 46% of attacks on financial organizations involve some form of phishing.1 As unsuspecting consumers engage with these emails, they may inadvertently divulge sensitive information such as login credentials and personal details.
However, the mechanics extend beyond mere imitation. In a typical scenario, when an unsuspecting user attempts to access their online banking portal, the request is rerouted through a malicious reverse proxy server. This server acts as an intermediary, intercepting the user’s request before directing it to the legitimate banking website. This real-time interception provides threat actors with immediate access to the user’s input, including login credentials and MFA codes.
When Reverse Proxy Phishing Turns Evil
A phishing-as-a-service (PaaS) platform named EvilProxy has emerged on hacking forums, offering a streamlined approach to stealing authentication tokens from various vendors, including Microsoft, Apple, Twitter, Facebook, Google, and more. This phishing kit significantly lowers the entry barrier, simplifying the execution of reverse proxy phishing attacks.
EvilProxy goes beyond by providing instructional videos, a user-friendly graphical interface, and pre-designed templates for cloning phishing pages to pilfer credentials and authentication tokens. With its intuitive interface, threat actors can effortlessly set up and manage phishing campaigns.
EvilProxy poses a significant threat to commercial banks by simplifying phishing attacks and enabling the theft of authentication tokens from major platforms. The platform’s user-friendly interface makes it accessible even to low-skilled threat actors, leading to potential unauthorized access to valuable banking accounts. This heightened risk includes financial fraud, reputation damage, and an expanded pool of cybercriminals targeting the commercial banking sector.
However, convenience comes at a cost, with EvilProxy pricing starting at $150 for 10 days, escalating to $400 for a month. Despite the expense, the potential rewards are substantial, creating opportunities for exploitation or resale to other malicious entities, such as ransomware gangs.
Arkose Phishing Protection Fights Reverse Proxy
Within commercial banking, reverse proxy phishing stands out as a prevalent threat, aiming to compromise user credentials and sensitive data. The effectiveness of phishing attacks is now propelled by sophisticated platforms like cybercrime-as-a-service (CaaS) tools like EvilProxy, challenging traditional detection and mitigation methods.
The Arkose Labs dashboard gives insight to the suspicious domains being used to target end users:

Session Analyzer analyzes all sessions impacted by reverse proxy phishing attacks in real time:
Arkose Phishing Protection caters specifically to the online commercial banking sector, offering:
- Real-time detection of reverse-proxy phishing attacks.
- Proactive blocking of credential theft.
- Prevention of MFA/2FA code interception.
- Customized alerts tailored for user warning.
Key capabilities tailored for the online commercial banking sector include:
- Real-time detection utilizing client- and server-side signatures.
- Managed phishing detection rulesets designed for banking environments.
- Hostname allow and deny lists for enhanced security.
- Immediate end-user warning messages for timely response.
- Support for both active interception and monitor-only modes.
- Seamless integration with no additional integration points required.
- Comprehensive visibility and reporting within the Session Explorer of the Arkose Command Center.
Arkose Phishing Protection, building on the robust bot detection technology of Arkose Bot Manager, is specifically crafted to identify and block reverse-proxy phishing attempts in real time within the online commercial banking sector. The multi-layered detection integrates device, network, and behavioral signals, offering a tailored and comprehensive defense against evolving threats.
- Multi-layered device, IP, and behavioral detection.
- Access to 140+ risk attributes for enriched models relevant to banking.
- ML decisioning based on global and banking-specific attack signatures.
- Continuous 24/7 SOC threat analysis and tuning for heightened security.
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Jenn Jeffers. Read the original post at: https://www.arkoselabs.com/blog/commercial-banking-takes-on-reverse-proxy-phishing/
如有侵权请联系:admin#unsafe.sh