
2024-1-23 22:2:30 Author: blog.projectdiscovery.io(查看原文) 阅读量:23 收藏
Security professionals are constantly on guard against cyber threats, especially given the rising number and sophistication of attacks. However, there's a less obvious, yet increasingly alarming "enemy" in cybersecurity: the surge in reported Common Vulnerabilities and Exposures (CVEs). Though CVEs are vital for identifying and discussing vulnerabilities, their rapid increase and sometimes exaggerated severity can be misleading.
This "noise" in the CVE system poses a significant challenge. In security, where professionals must be vigilant at all times against adversaries seeking just one weak point, the distraction caused by an overwhelming number of CVEs can lead to misdirected efforts and overlooked critical vulnerabilities. In essence, while CVEs are intended to enhance security, their current state risks doing the opposite.
Enter ProjectDiscovery
If you're unfamiliar with ProjectDiscovery, allow me to introduce our core ethos. PD Tools are designed for practitioners and security engineers who prioritize genuine security measures over mere compliance checkboxes. These professionals are driven by a strong desire to effectively safeguard their systems. At ProjectDiscovery, this commitment resonates deeply with us, compelling us to offer our support and assistance.
And that’s where today’s brand-new tool comes from: cvemap.
Introducing cvemap
Amidst the rapidly evolving cybersecurity landscape, the year 2023 marked a significant influx of cybersecurity threats, with an astounding 24,804 new CVE (Common Vulnerabilities and Exposures) entries reported by the National Vulnerability Database (NVD). This deluge of data can be overwhelming, but our latest innovation, cvemap, is designed to tackle this challenge head-on. Powered by the cvemap-api, our tool periodically collects CVE data from NVD and other critical sources, consolidating them into a singular, comprehensive repository.
This strategic aggregation transforms the complex and ever-expanding universe of CVEs into a format that is both manageable and user-friendly. cvemap does more than just cut through the dense "jungle" of CVE data; it acts as a reliable guide, providing a clear map and compass for navigating this intricate and constantly shifting cybersecurity terrain. With cvemap, you're not just keeping pace with cybersecurity developments; you're empowered to confidently navigate and stay ahead of them.
Our methodology for prioritizing CVEs adopts a multidimensional perspective, ensuring a thorough analysis beyond just the CVSS (Common Vulnerability Scoring System) score or severity level. This approach includes assessing exploitability, critical due dates, probabilistic assessments, and a comprehensive evaluation of publicly available CVEs, among other factors. This multi-faceted evaluation ensures a more accurate and holistic understanding of each vulnerability.
Here are some of the diverse and high-value sources that cvemap utilizes:
- Known Exploited Vulnerabilities Catalog (KEV): This list from the USA's Cybersecurity & Infrastructure Security Agency (CISA) provides a list of actively exploited vulnerabilities along with crucial due dates, helping prioritize threats that require immediate attention.
- Exploit Prediction Scoring System (EPSS): EPSS is a model that estimates the likelihood of a software vulnerability being exploited in the wild, offering a probability score between 0 and 1. Unlike other industry standards that focus mainly on vulnerability characteristics and severity, EPSS enhances threat assessment by incorporating current threat information from CVEs and real-world exploit data.
- Proofs of Concept (POCs): Includes official PoCs, comprehensive references, and ranked PoCs from GitHub and other platforms, providing insights into practical exploitability.
- HackerOne CVE Discovery: Integrates reports and ranks CVEs reported by skilled bug bounty hunters on the HackerOne platform.
- Exposure on the Internet: Provides data on live/active hosts on the internet for specific products, offering real-time insights into the global exposure of vulnerabilities.
- GitHub and OSS data: Delivers metrics and popularity of open source projects when they are impacted by a CVE.
- Nuclei Templates: Community curated list of templates that can fingerprint the CVEs for the nuclei engine to find security vulnerabilities. Nuclei templates also provide a Reliable set of POCs to easily test / retest vulnerabilities at scale, including in-progress POCs.
By integrating these diverse sources, cvemap provides a comprehensive, multidimensional view of the threat landscape. It skillfully establishes meaningful connections between various data points, combining both crucial historical data and real-time insights. This holistic approach positions cvemap as an indispensable tool for cybersecurity professionals and enthusiasts alike, offering a more in-depth understanding and more effective management of cybersecurity threats.
Getting started
To install cvemap, visit https://github.com/projectdiscovery/cvemap and find the command there to install cvemap:
go install github.com/projectdiscovery/cvemap/cmd/cvemap@latestBefore using cvemap, you’ll need to get a ProjectDiscovery Cloud Platform (PDCP) account and API key so that you can access the cvemap API data.
1. Sign up for PDCP
Navigate to https://cloud.projectdiscovery.io/ and click “Sign Up” (or “Sign In” if you already have a PDCP account).
2. Obtain your PDCP API
Once signed in to ProjectDiscovery Cloud Platform, you can navigate to https://cloud.projectdiscovery.io/?ref=api_key to find your API Key.
Use the copy button to copy your API Key - we’ll use that in the steps below
3. Authorize cvemap with PDCP
To authenticate your install of cvemap, run
cvemap -authAnd when prompted, paste the key you obtained above.
Running cvemap
By default, cvemap displays all known exploited vulnerabilities based on the CVEs and KEVs published by CISA.
To list the top known exploited vulnerabilities, use the following command:
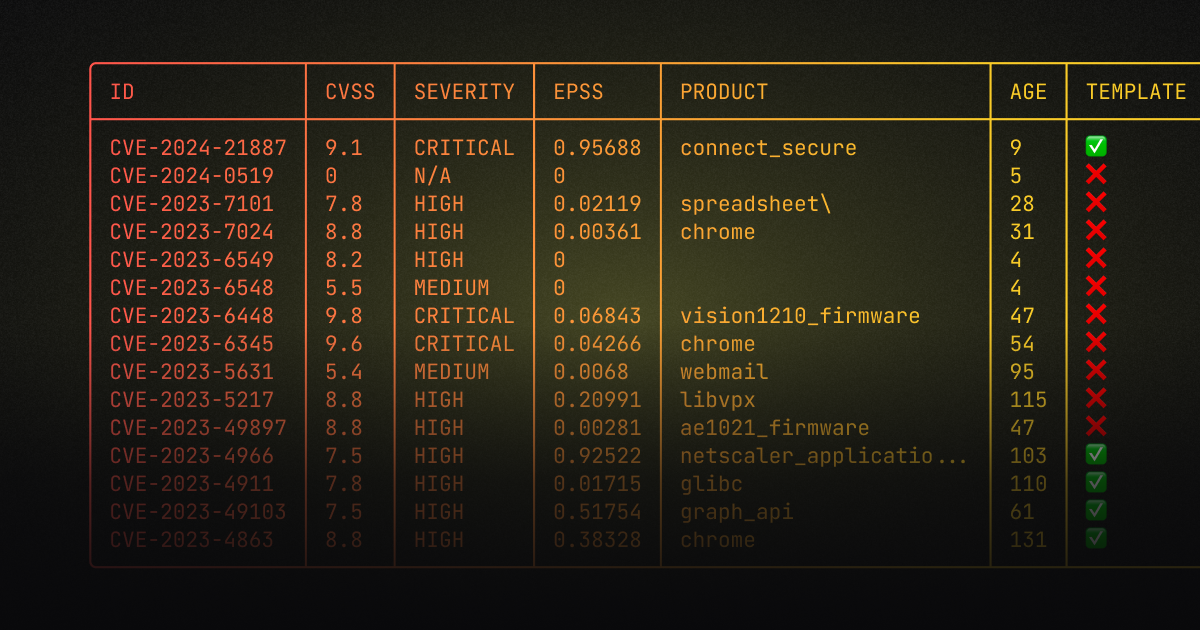
cvemap --limit 10
Filtering Results
You can also filter using a number of options, including:
Product, Vendor, Severity, CPE, Assignee, CVSS-Score, EPSS-Score, Age, …and more!
For example, to find all CVEs for Atlassian Confluence, you could use
cvemap -product confluence -l 5 -silent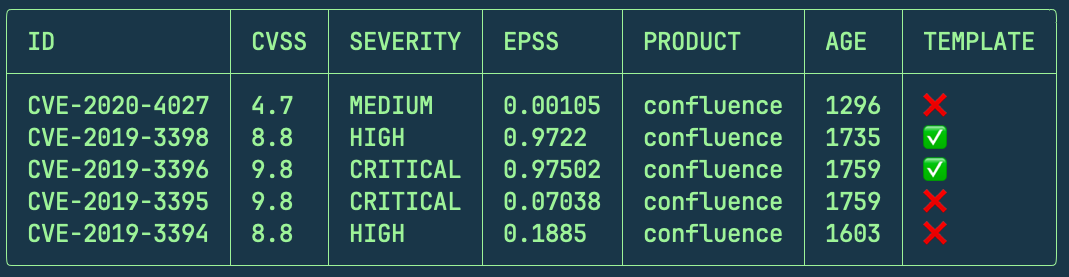
You can also specify what fields are returned with -field, like this:
cvemap -silent -severity critical -field assignee,vstatus,poc -l 5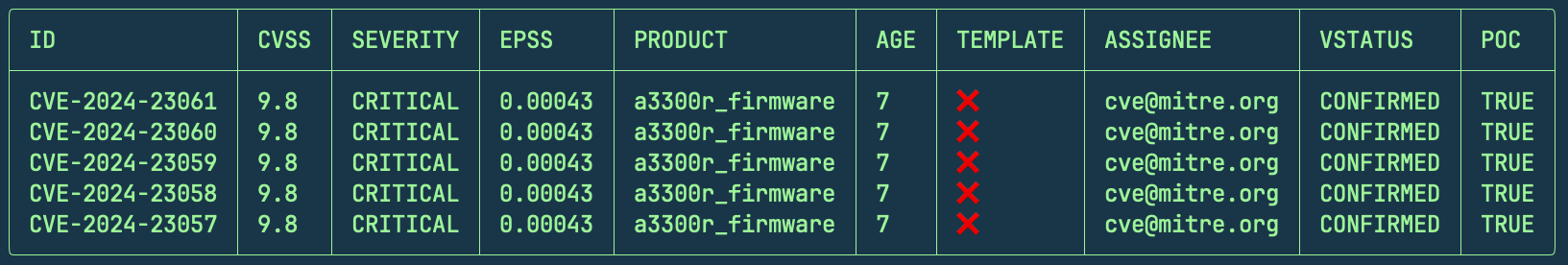
In addition, you can specify ranges of scores with a command like this:
cvemap -silent -cs '> 7' -es '> 0.00053' -l 5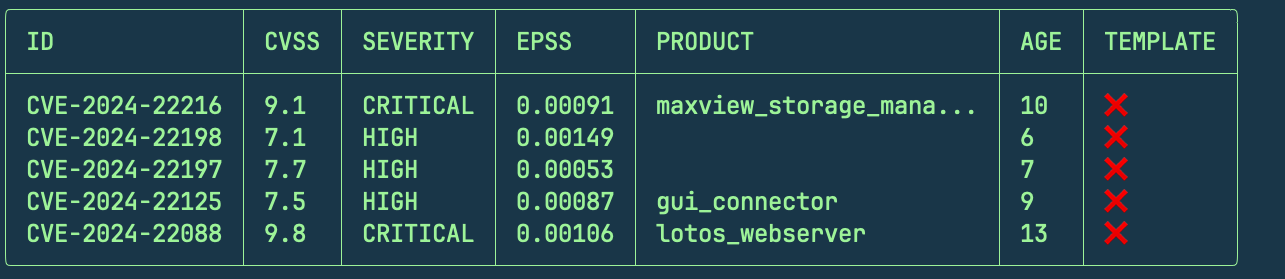
JSON Output
The data from cvemap is also available in JSON format with the -json flag
echo CVE-2024-21887 | cvemap -jsonTo learn more about cvemap, visit the documentation page. You can also join our Discord server to discuss use cases and see success stories of bug bounty hunters and security professionals who are helping to make the internet a safer place by democratizing security, together.
如有侵权请联系:admin#unsafe.sh