This post is also available i 2024-1-23 19:0:11 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:66 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers have been tracking the BianLian ransomware group, which has been in the top 10 of the most active groups based on leak site data we’ve gathered. From that leak site data, we’ve primarily observed activity affecting the healthcare and manufacturing sectors and industries, and impacting organizations mainly in the United States (US) and Europe (EU).
We also observed that the BianLian group shares a small, customized tool in common with the Makop ransomware group. This shared tool indicates a possible connection between the two groups, which we will explore further.
BianLian has also recently moved from a double extortion scheme to one of extortion without encryption. Rather than encrypting their victims’ assets before stealing data and threatening to publish it if they do not pay the ransom, they’re now moving straight to stealing data to motivate victims to pay.
The Unit 42 Incident Response team has responded to several BianLian ransomware incidents since September 2022.
Palo Alto Networks customers are better protected against ransomware used by the BianLian ransomware group through Cortex XDR, as well as by Cloud-Delivered Security Services for the Next-Generation Firewall such as WildFire and Advanced URL Filtering.
In particular, the Cortex XDR anti-ransomware module included out-of-the-box protections that prevented adverse behavior from the ransomware samples we tested without the need for specific detection logic or signatures.
The Prisma Cloud Defender should be deployed on cloud-based Windows virtual machines to ensure they are protected. Cortex Xpanse is able to provide visibility that can prove valuable for proactive protection.
The Unit 42 Incident Response team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
| Related Unit 42 Topics | Ransomware, Cybercrime |
Table of Contents
BianLian Threat Overview
Possible Connection to Makop Ransomware
Technical Analysis
Attack Lifecycle
Initial Access
Credential Dumping
Persistence
Reconnaissance
Encryptor and Backdoor
Conclusion
Protections and Mitigations
Indicators of Compromise
Examples of the BianLian Encryptor
Examples of the BianLian Backdoor
Advanced Port Scanner
.NET Tool
BianLian Command and Control Servers
Additional Resources
BianLian Threat Overview
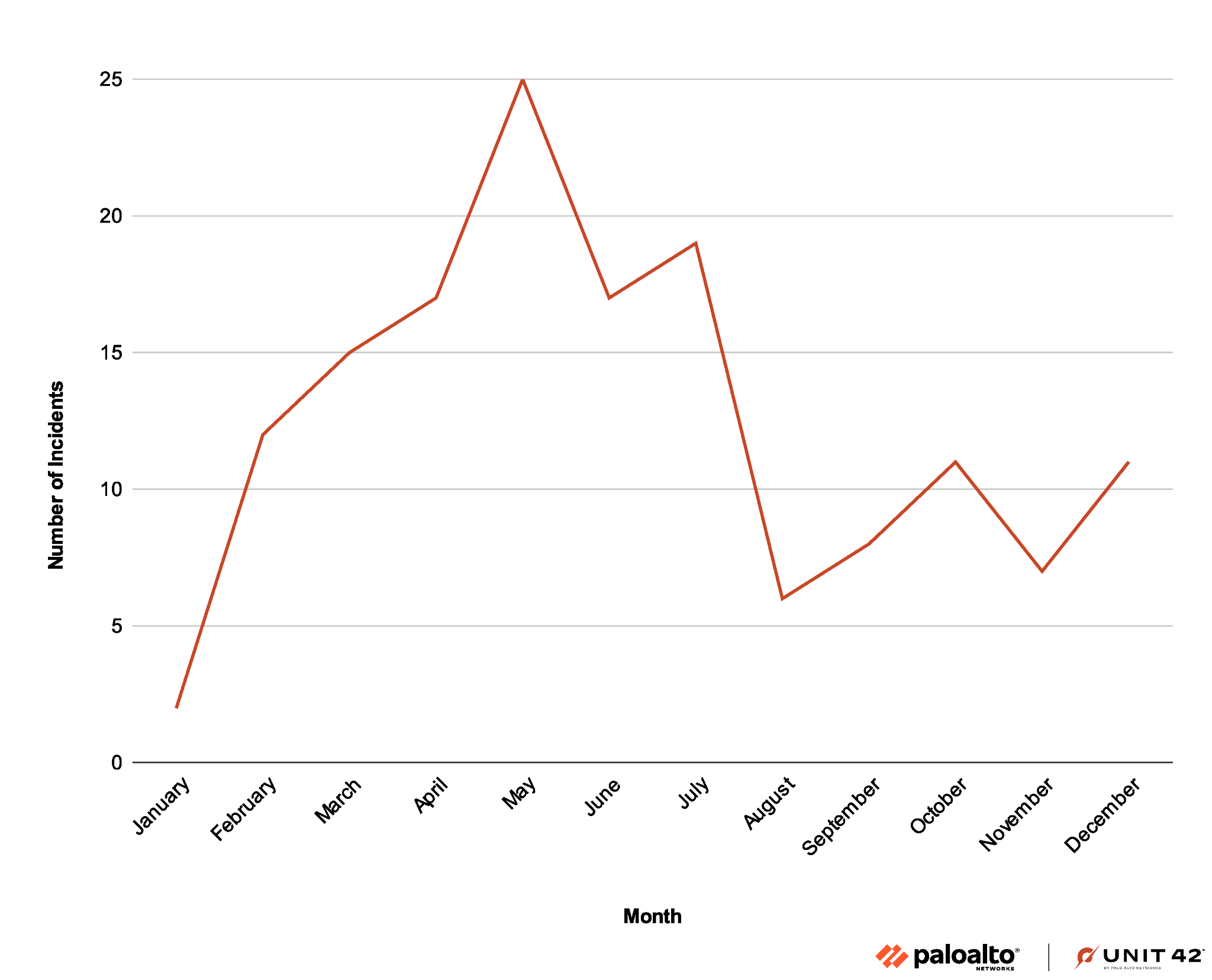
The BianLian group has been extremely active ever since it emerged in 2022, with new organizations compromised by the group being reported on their leak site almost on a weekly basis. Figure 1 below details their activity throughout 2023, as illustrated by their leak site data.
This group impacts mainly the healthcare, manufacturing, professional and legal services sectors. Their attacks have primarily taken place in North America, but they were also seen in the EU and India.
BianLian shares a small custom .NET tool with the Makop ransomware group, which indicates a possible connection between the two groups.
BianLian has moved from a double extortion scheme of encrypting their victims’ assets, stealing data, and threatening to publish it if they do not pay the ransom to a main focus of extortion without encryption.
The group’s leak site indicates that BianLian might be expanding by hiring new developers and affiliates, as noted in the “Work with us” section from the group's homepage shown below in Figure 2.
![Image 2 is a screenshot of the BianLian leak site homepage as of December 2023. BianLian. Categories are Home, Companies, Tags, Contacts. Work with us: targets’ providers, software engineers, pentesters, journalists. Tox: [redacted]. Email: [redacted onion email]. Most of the following text is also redacted.](https://unit42.paloaltonetworks.com/wp-content/uploads/2024/01/word-image-132125-2.png)
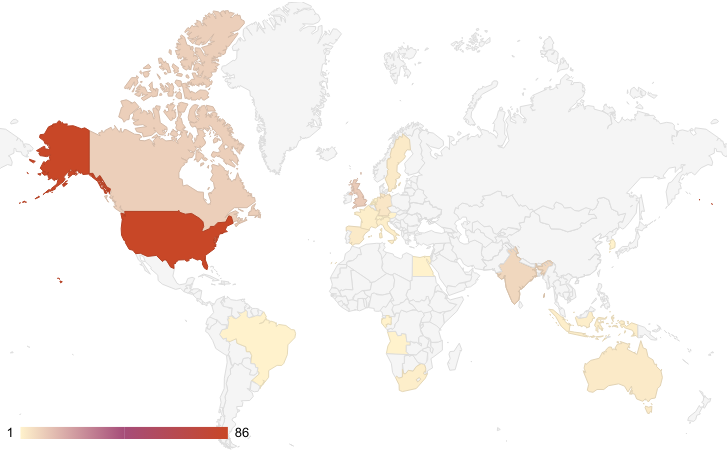
The BianLian group regularly updates the list of compromised targets on their leak site. Figure 3 details the most affected countries. While BianLian has impacted organizations all over the world, the US is clearly the most affected country as of 2023.
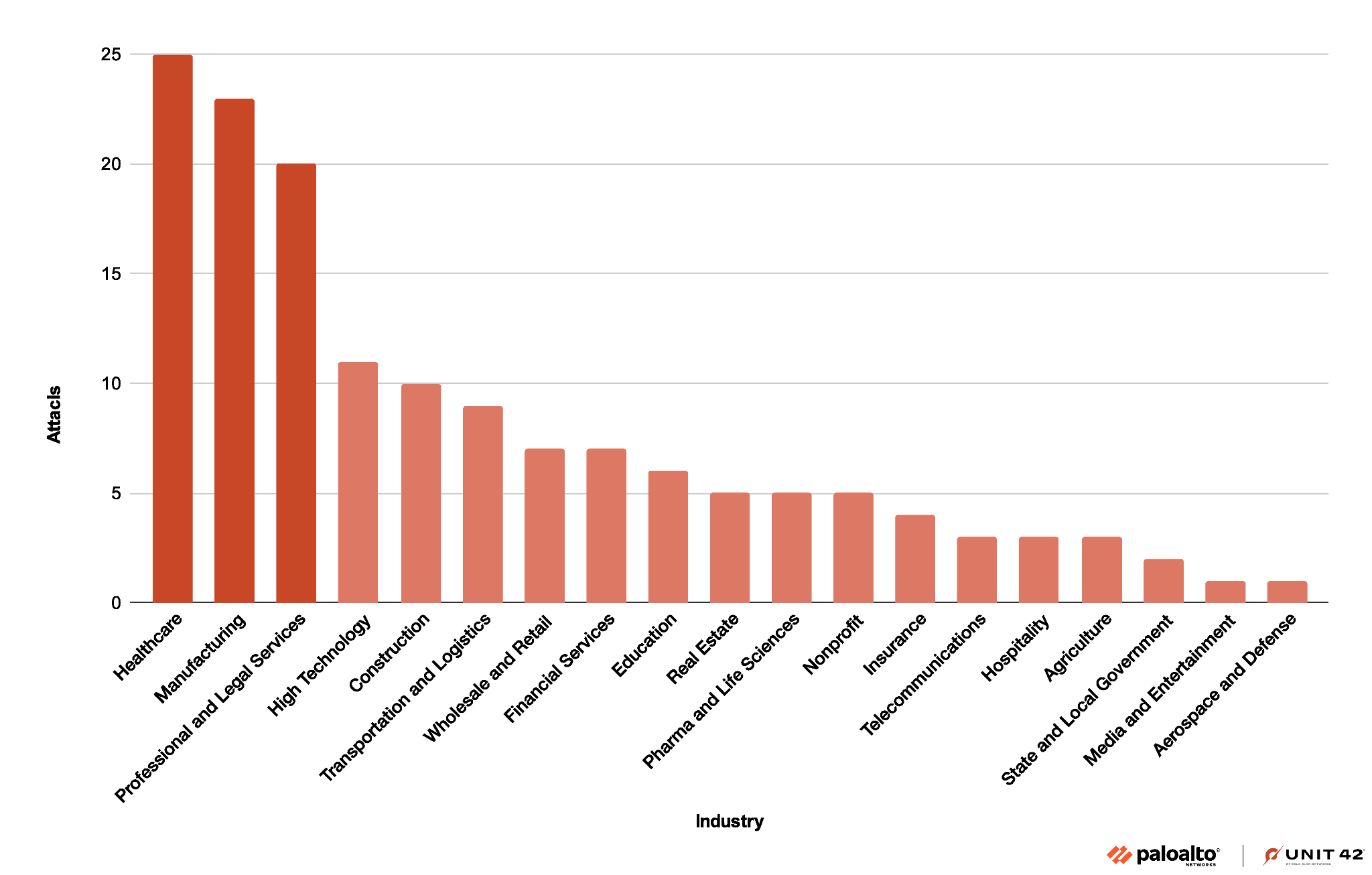
As detailed in Figure 4 below, healthcare is the sector most affected by the BianLian group, with manufacturing a close second. In January 2023, the group claimed to have exfiltrated 1.7 TB of data, including personal data of patients and employees, from a California-based hospital. Attacks on healthcare organizations are especially concerning because they disrupt hospitals’ day-to-day operations and potentially endanger patients' lives.
Possible Connection to Makop Ransomware
During our analysis, we noticed a small .NET custom executable was shared between the BianLian and Makop ransomware groups. Both groups also used the same hash of the publicly available Advanced Port Scanner tool.
This .NET tool is responsible for retrieving file enumeration, registry and clipboard data. This tool contains some words in the Russian language, such as the numbers one to four. The use of such a tool indicates that the two groups might have shared a tool set or used the services of the same developers in the past.
A possible – yet not confirmed – explanation for this overlap is that BianLian could be sharing a codebase with the Makop group, or using the services of the same third-party developers. This phenomenon is well-known and documented among certain underground cybercrime groups.
Another noteworthy fact is that the Makop ransomware was documented excluding certain file extensions when encrypting an infected endpoint, including known extensions that are used by other ransomware strains. This is yet another indicator of possible existing relationships among these threat actors, or at least a “not stepping on someone’s toes” approach when it involves other ransomware groups.
Technical Analysis
Attack Lifecycle
We have mapped the attack stages that are common with the BianLian group to the MITRE ATT&CK framework, which is summarized below.
Initial Access
To infiltrate corporate networks, BianLian operators often perform the following activities:
- Use stolen Remote Desktop Protocol (RDP) credentials
- Exploit the ProxyShell vulnerability
- Target virtual private network (VPN) providers
- Use other previously reported techniques such as deploying web shells
During the last year, BianLian’s methods of infiltration and lateral movement did not change much. Nevertheless, we were able to retrieve interesting forensic data from our telemetry that provides additional behavioral indicators of compromise (IoCs).
After successfully infiltrating an organization’s network, our telemetry indicates the BianLian group uses various public tools to move laterally, dump credentials and remotely execute a backdoor payload.
Credential Dumping
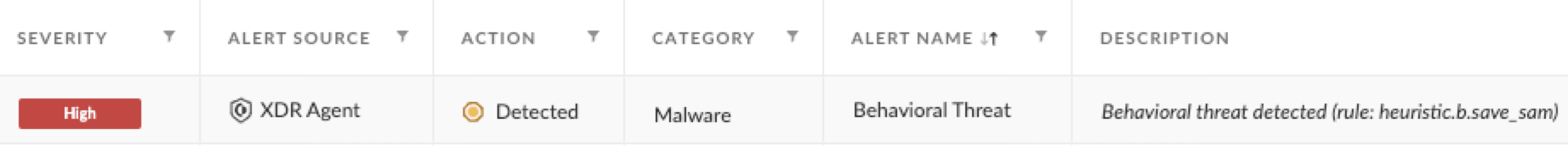
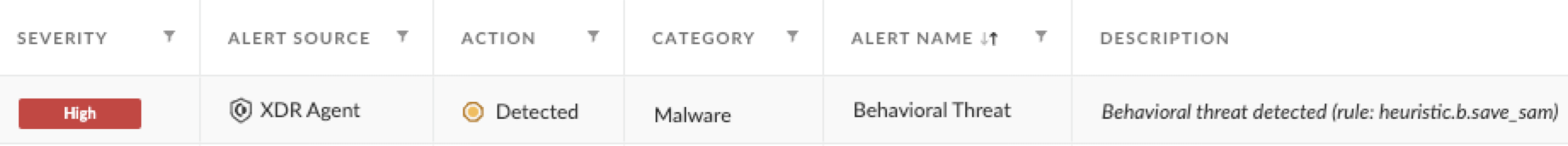
In our telemetry, we have witnessed dumping of the Security Accounts Manager (SAM) registry hive into a file at %windir%\Temp. This is a common technique used by attackers.
The SAM stores hashed passwords from accounts used on the attacked machine, and it can be recovered when processing SYSTEM privileges. The corresponding Cortex XDR alert is shown in Figure 5.
Persistence
During the analysis of our telemetry, we saw the attackers drop the BianLian backdoor DLL component under the following path:
- c:\\programdata\\vmware\\[filename].dll.
To execute the backdoor, they used the impacket tool to create the following scheduled task:
cmd.exe /C rundll32.exe c:\\programdata\\vmware\\[filename].dll,Entry > C:\\Windows\\Temp\\[filename].tmp 2>&1. |
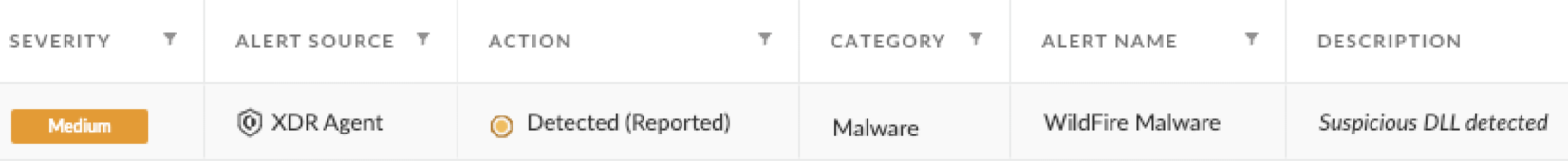
The creation of the task was detected by Cortex XDR, and the corresponding alert is shown in Figure 6 below.

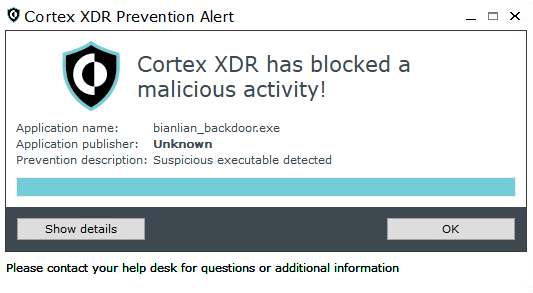
This task’s role is to periodically execute the backdoor DLL with its export function named Entry, using rundll32. The execution of the backdoor DLL was detected and prevented by Cortex XDR. The alert and prevention pop-up are shown in Figures 7 and 8, respectively.
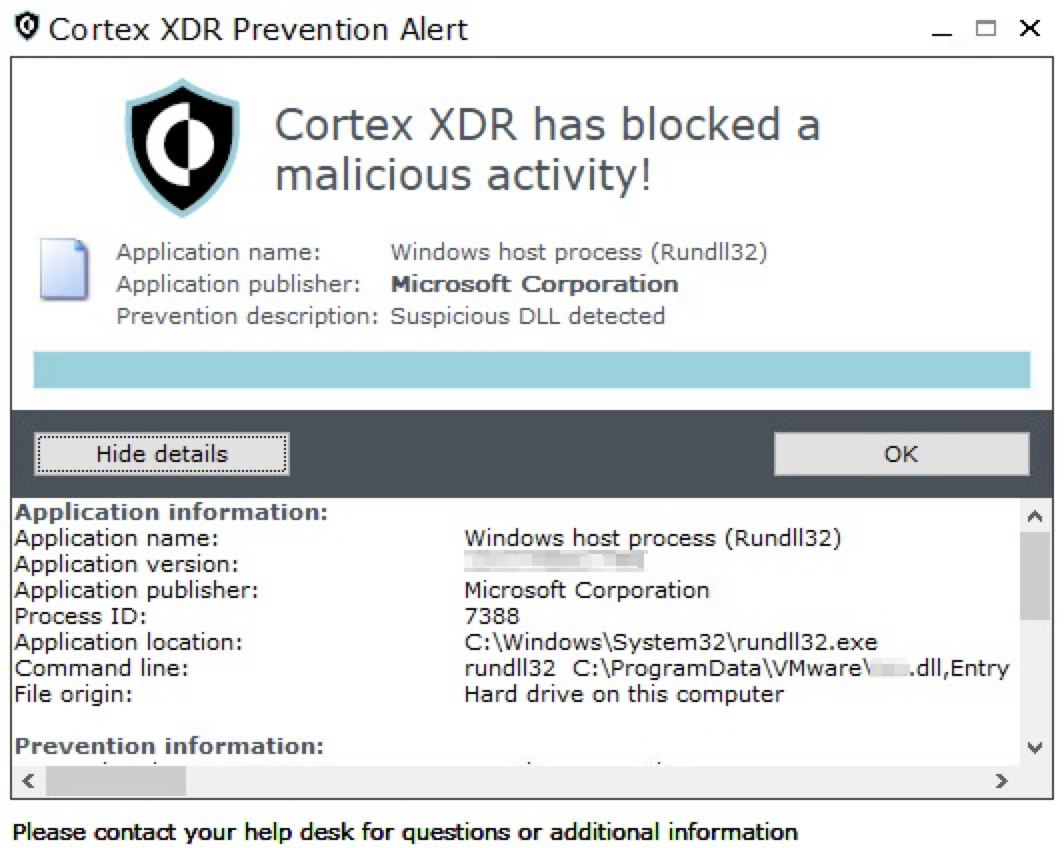
The backdoors themselves have different names and paths in each incident, thus making it difficult to implement naming-based behavioral detection.
Reconnaissance
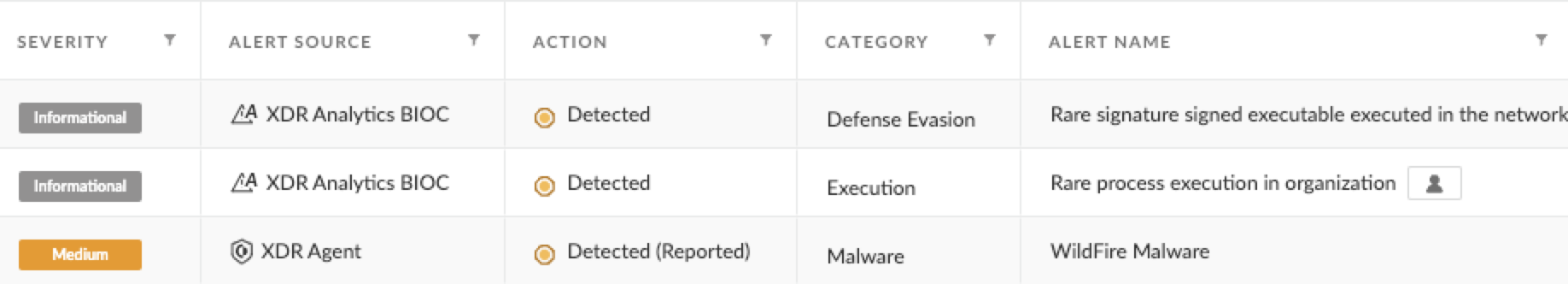
To get a better picture of an already infected network’s open ports that attackers can later use for lateral movement, the tool Advanced Port Scanner by Famatech was used from the following path:
- C:\\Users\\%username%\\AppData\\Local\\Temp\\31\\Advanced_Port_Scanner_2.5.3869.exe
This is the same Advanced Port Scanner file that Makop ransomware was previously documented using. The alerts raised by its execution are shown in Figure 9.
Encryptor and Backdoor
Since the beginning of their activity, BianLian used two main components for their final payloads: an encryptor and a backdoor. Figure 10 below shows the encryptor’s ransom note.
![Image 10 is a screenshot of a BianLian ransomware note. Title: Look at this instruction.txt. Your network systems were attacked and encrypted. Contact us in order to restore your date. Don’t make any changes in your file structure: touch no files, don’t try to recover by yourself, that may lead to its complete loss. To contact us you have to download “tox” messenger. Add user with the following ID to get your instructions [redacted]. Alternative way [redacted email]. Your ID: [redacted]. You should know that we have been downloading data rom your network for a significant time before the attack: financial, client, business, post, technical and personal files. In 10 days it will be posted at our site. [redacted] with links. Send to your clients, partners, competitors and news agencies, that will lead to a negative impact on your company: potential financial, business and reputational loses.](https://unit42.paloaltonetworks.com/wp-content/uploads/2024/01/word-image-132125-10.png)
In early 2023, Avast released a decryptor for BianLian's encryptor, which ultimately caused the group to cease most of its encryption activity. The threat actors then shifted their operation into a steal-and-extort scheme, mainly relying on their custom backdoor.
BianLian's backdoor, similar to the encryptor, is written in Go. Its core functionality is more of a loader than a classic backdoor, with its main functionality being downloading and executing additional payloads. The backdoor contains a hard-coded C2 IP address and port to communicate with.
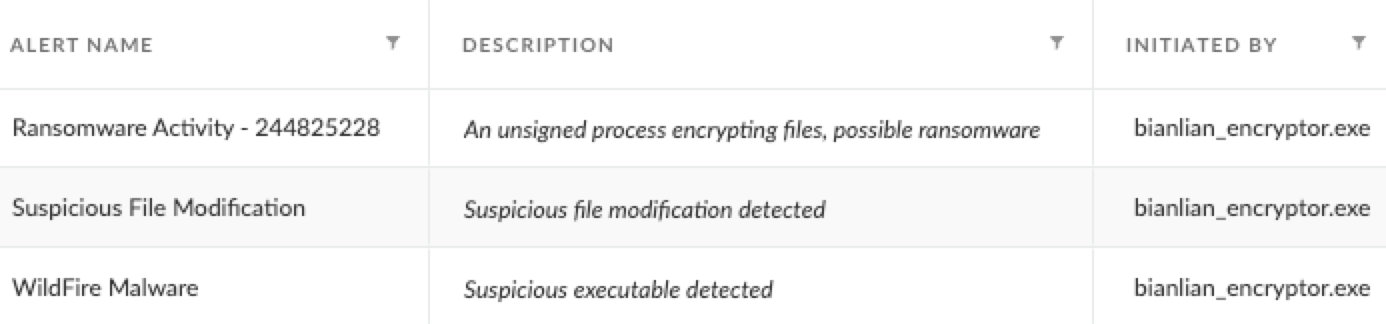
As shown in Figures 11 and 12, Cortex XDR successfully detected the execution of the encryptor, using its anti-ransomware module and other behavioral and static detection signatures.
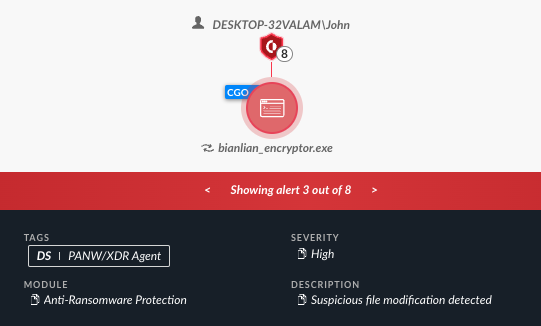
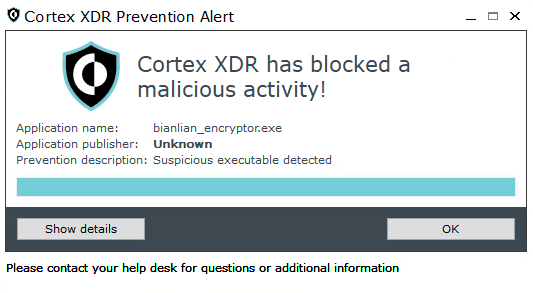
As shown in Figure 13, when operating in prevent mode, the BianLian encryptor is prevented by Cortex XDR.
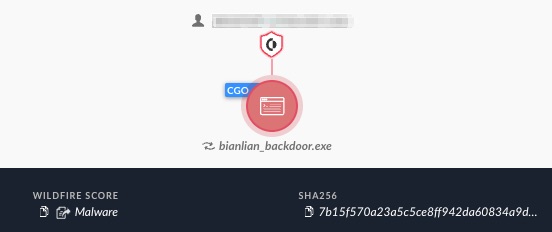
Figures 14 and 15 below demonstrate how Cortex XDR also detected the BianLian custom backdoor in detect mode and prevented it in prevent mode.
Conclusion
Following its discovery in 2022, the BianLian group has been one of the most active and prevalent extortion groups in the cyberthreat landscape. Out of the leak site data tracked by Unit 42 between January and mid-December of 2023, BianLian was in the top 10 of the most active groups. There is a growing list of alleged victims that they update on their leak site.
Maintaining their tactics, techniques and procedures (TTPs) of infiltrating corporate networks, the BianLian group has shown adaptiveness to the ransomware market demands. They have shifted from double-extortion into being focused solely on extortion efforts, pressuring their victims into paying the ransom without encrypting their files. A possible connection to the Makop ransomware group was also found, due to their mutual use of a custom tool.
Protections and Mitigations
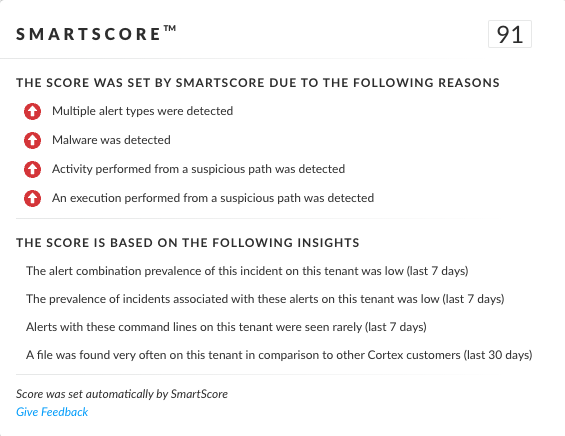
SmartScore, a unique ML-driven scoring engine that translates security investigation methods and their associated data into a hybrid scoring system, scored an incident involving BianLian backdoor at 91 out of 100, as shown in Figure 16. This type of scoring helps analysts determine which incidents are more urgent and provides context about the reason for the assessment, assisting with prioritization.
Palo Alto Networks customers are better protected from the BianLian encryptor and backdoor components.
The Cortex XDR and XSIAM platforms detect and prevent the execution flow described in the screenshots included in the previous section.
The Cortex XDR agent included out of the box protections that prevented adverse behavior from the samples we tested from this group, without the need for specific detection logic or signatures.
Cortex XDR and XSIAM detect user- and credential-based threats by analyzing user activity from multiple data sources including the following:
- Endpoints
- Network firewalls
- Active Directory
- Identity and access management solutions
- Cloud workloads
Cortex XDR and XSIAM build behavioral profiles of user activity over time with machine learning. By comparing new activity to past activity, peer activity and the expected behavior of the entity, Cortex XDR and XSIAM detect anomalous activity indicative of credential-based attacks.
They also offer the following protections related to the attacks discussed in this post:
- Prevent the execution of known malicious malware
- Prevent execution of unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module
- Protect against credential-gathering tools and techniques using the Credential Gathering Protection, available from Cortex XDR 3.4
- Protect against exploitation of different vulnerabilities including ProxyShell using the Anti-Exploitation modules as well as Behavioral Threat Protection
Cortex XDR Pro detects post-exploitation activity, including credential-based attacks, with behavioral analytics.
The Prisma Cloud Defender as well as Cortex XDR for cloud agents should be deployed on cloud-based Windows virtual machines to ensure they are protected from these known malicious binaries. WildFire signatures can be used by both Palo Alto Networks cloud services to ensure cloud-based Windows virtual machine runtime operations are being analyzed and those resources are protected.
Cloud-Delivered Security Services for the Next-Generation Firewall such as WildFire and Advanced URL Filtering include protections based on the IoCs shared in this article.
Cortex Xpanse is also able to detect exposed RDP and many other remote access interfaces which are often brute forced or exploited with compromised credentials. This visibility can prove valuable through proactive prevention.
If you think you might have been impacted or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Examples of the BianLian Encryptor
- af46356eb70f0fbb0799f8a8d5c0f7513d2f6ade4f16d4869f2690029b511d4f
- 1fd42d07b4be99e0e503c0ed5af2274312be1b03e01b54a6d89c0eef04257d6e
- 3a2f6e614ff030804aa18cb03fcc3bc357f6226786efb4a734cbe2a3a1984b6f
- 46d340eaf6b78207e24b6011422f1a5b4a566e493d72365c6a1cace11c36b28b
- 1fd07b8d1728e416f897bef4f1471126f9b18ef108eb952f4b75050da22e8e43
- eaf5e26c5e73f3db82cd07ea45e4d244ccb3ec3397ab5263a1a74add7bbcb6e2
Examples of the BianLian Backdoor
- c775e6d87a3bcc5e94cd055fee859bdb6350af033114fe8588d2d4d4f6d2a3ae
- c57ca631b069745027d0b4f4d717821ca9bd095e28de2eafe4723eeaf4b062cf
- c592194cea0acf3d3e181d2ba3108f0f86d74bcd8e49457981423f5f902d054b
- df51b7b031ecc7c7fa899e17cce98b005576a20a199be670569d5e408d21048c
- 2ed448721f4e92c7970972f029290ee6269689c840a922982ac2f39c9a6a838f
- 264af7e7aa17422eb4299df640c1aa199b4778509697b6b296efa5ae7e957b40
- 73d095abf2f31358c8b1fb0d5a0dc9807e88d44282c896b5033c1b270d44111f
- 8b65c9437445e9bcb8164d8557ecb9e3585c8bebf37099a3ec1437884efbdd24
- 4ca84be5b6ab91694a0f81350cefe8379efcad692872a383671ce4209295edc7
- 93fb7f0c2cf10fb5885e03c737ee8508816c1102e9e3d358160b78e91fa1ebdb
- afb7f11da27439a2e223e6b651f96eb16a7e35b34918e501886d25439015bf78
- 53095e2ad802072e97dbb8a7ccea03a36d1536fce921c80a7a2f160c83366999
- 16cbfd155fb44c6fd0f9375376f62a90ac09f8b7689c1afb5b9b4d3e76e28bdf
- 60b1394f3afee27701e2008f46d766ef466caa7711c45ddfd443a71efc39a407
- ba3c4bc99b67038b42b75a206d7ef04f6d8abaf87a76c373d4dec85e73859ce2
- e7e097723d00f58eab785baf30365c1495e99aa6ead6fe1b86109558838d294e
- 96e02ea8b1c508f1ee3c1535547f9b89396f557011e61478644ae5876cdaaca5
- ac1d42360c45e0e908d07e784ceb15faf8987e4ba1744d56313de6524d2687f7
- 1cba58f73221b5bb7930bfeab0106ae5415e70f49a595727022dcf6fda1126e9
- 487f0d748a13570a46b20b6687eb7b7fc70a1a55e676fb5ff2599096a1ca888c
- f84edc07b23423f2c2cad47c0600133cab3cf2bd6072ad45649d6faf3b70ec30
- 93953eef3fe8405d563560dc332135bfe5874ddeb373d714862f72ee62bef518
- f3f3c692f728b9c8fd2e1c090b60223ac6c6e88bf186c98ed9842408b78b9f3c
- f6669de3baa1bca649afa55a14e30279026e59a033522877b70b74bfc000e276
- 228ef7e0a080de70652e3e0d1eab44f92f6280494c6ba98455111053701d3759
- 0e4246409cdad59e57c159c7cc4d75319edf7d197bc010174c76fe1257c3a68e
- 90f50d723bf38a267f5196e22ba22584a1c84d719b501237f43d10117d972843
- 4c008ac5c07d1573a98eb87bffe64e9c9e946de63b40df3f686881cf0698eef7
- d3574cc69a5974a32a041d1dc460861fe1cef3c1f063171c5fc890ca0e8403c4
- 99fc3e13f3b4d8debf1f2328f56f3810480ee2eed9271ebf413c0015c0a54c23
- 4f4a2adc7ecc41f12defe864c78ad6bbf708355affac4115dcd5065b38198109
- 188e95d6ed0810c216ab0043ecc2f54f514e624ca31ed1eec58cfc18cc9ac75e
- 16b0f643670d1f94663179815bfac493f5f30a61d15c18c8b305b1016eece7ef
- c5fa6a7a3b48a2a4bbcbbbb1ca50c730f3545e3fbb03fa17fb814ad7a400a21f
- d3fc56b98af9748f7b6dd44e389d343781ff47db9ed3d92ae8fadc837f25f6ed
- 23295c518f194dee7815728de15bafe07bf53b52d987c7ad2b2050f833f770f7
- 06f10c935fae531e070c55bde15ee3b48b6bb289af237e96eec82124c19d1049
- 7ba40902dc495d8da28d0c0788bcfb1449818342df89f005af8ce09f2ee01798
- 3106e313f6df73b84acd8d848b467ac42c469ffabbad19e4fdcc963639cfff8c
- 56e63edb832fdf08d19ecfe2de1c7c6c6581cedd431215ded0c8e44ac9aed925
- 195c11ee41f5a80d8e1b1881245545d6529671b926eb67bd3186e3ffecefe362
- ac14946fd31ca586368c774f3a3eed1620bf0f0b4f54544f5d25e87facf18d82
- 29a14cb63a1900fe185fad1c1b2f2efb85a058ac3c185948b758f3ce4107e11e
- 91ffe0ee445b82bd3360156feeecf8112d27c9333f9796caffcfda986fd7e9b4
- 5162fd73cbe8f313d2b0e4180bab4cbe47185f73a3ffc3d1dcccc36bc2865142
- 7dabe5d40c13c7c342b7182eaf7c63fbb5e326300316f6f6518b527d57e79ac8
- 4e92b73a17e0646876fb9be09c4ee6f015f00273932d2422b69339e22b78b385
- 9413ba4a33ea77326b837ba538f92348e1909d5263ca67a86aa327daa8fbba30
- bd41ac2686beadc1cb008433960317b648caae37c93d8c0d61ad40fe27b5b67e
- bd57af28c94c3b7f156511c48f4b62cd1b4c29a1a693f4dc831e0a928691cc56
Advanced Port Scanner
- d0c1662ce239e4d288048c0e3324ec52962f6ddda77da0cb7af9c1d9c2f1e2eb
.NET Tool
- 40126ae71b857dd22db39611c25d3d5dd0e60316b72830e930fba9baf23973ce
BianLian Command and Control Servers
- 208.123.119[.]123
- 13.215.228[.]73
- 54.193.91[.]232
- 172.96.137[.]159
- 204.152.203[.]90
- 144.208.127[.]119
- 192.161.48[.]43
- 146.70.87[.]197
- 45.86.230[.]64
- 45.56.165[.]17
- 23.163.0[.]168
- 172.96.137[.]249
- 173.254.204[.]78
- 185.56.137[.]117
- 52.87.206[.]242
- 45.66.249[.]118
- 96.44.157[.]203
- 103.20.235[.]122
- 44.212.9[.]14
- 149.154.158[.]154
- 146.59.102[.]74
- 96.44.135[.]76
- 85.239.52[.]96
- 66.85.156[.]83
- 198.252.98[.]186
- 3.236.161[.]7
- 13.59.168[.]154
- 172.245.128[.]35
- 216.146.25[.]60
- 172.86.122[.]183
- 185.99.133[.]112
- 149.154.158[.]214
- 104.200.72[.]6
- 23.163.0[.]228
Additional Resources
- BianLian ransomware gang holds Save the Children hostage – Computer Weekly, by TechTarget
- #StopRansomware: BianLian Ransomware Group – U.S. Cybersecurity and Infrastructure Security Agency (CISA)
- BianLian Ransomware Gang Gives It a Go! – Redacted
- BianLian Ransomware Gang Continues to Evolve – Redacted
- Makop: The Toolkit of a Criminal Gang – L M, Medium
- Makop Ransomware Whitepaper – LIFARS by SecurityScorecard
- BianLian Ransomware Lists St Rose Hospital as Victim – The Cyber Express
- Decrypted: BianLian Ransomware – Avast Threat Labs
- OS Credential Dumping: Security Account Manager, Sub-technique T1003.002 - Enterprise – MITRE ATT&CK
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh