
2024-1-8 20:1:57 Author: www.bitdefender.com(查看原文) 阅读量:12 收藏
Bitdefender launched in May 2023, an industry-first technology called App Anomaly Detection that gave the security solutions feature in our mobile security solution for Android the power to analyze app behavior and identify threats based on what applications do after installation. We took a closer at what this new technology found in the wild over the course of a few months.
The new technology provides us with data on current threats and a better understanding of worldwide trends. And, if we can take away one lesson right now from all of the data we've collected in only a few months, it’s that there is a considerable amount of applications impersonating top-ranking apps for, well, everything.
Key findings:
- Attackers mimic the names and versions of popular apps to trick people into downloading these “evil twin” applications. These are generally available through third-party stores and websites.
- Most of the malware is identified as riskware. While this riskware is in many cases all about showing ads to victims, it's also about exfiltrating as much data as permissions allow.
- Trojan bankers and stalkerware are widespread and usually have complex features that offer attackers access deep into infected devices.
- Many of these applications have already been identified as malware during the installation process, but their behavior continues to get flagged by the App Anomaly Detection technology as well.
They know what you want
Attackers know what people search for and what interests them; that's the main reason why we see these package names raising alerts. Applications such as Truecaller, with more than 1 billion downloads, will definitely be a target, not to mention games such as Roblox.
But the list of apps triggering the App Anomaly Detection includes apps in the official store, such as FamiSafe Jr - App for kids (com.wondershare.famisafe.kids) that claims to provide parental control features. While the app can be installed on devices, the security solution will warn users, marking the software as a possible PUA (Potentially Unwanted Application).
Some of the more popular apps criminals try to copy by using the same package name to trick users include Roblox, WhatsApp, Spotify, Instagram, and others. Also, Cerberus is one of the more insidious apps that triggers the security solution, although this particular dangerous app is detected both during installation and by App Anomaly.
For the most part, criminals want to make money, so they heavily focus on malware that's supposed to serve annoying ads and generate money.
Riskware
We used the term riskware when defining the type of malware we see in our insights, but it's actually an umbrella term for a variety of threats.
While a type of malware might be used to display ads, it can also extract a lot of data. The more dangerous types of riskware can control the camera and microphone, make phone calls, and more.
Android.Riskware.Agent.JEP:
These malicious apps don't have a user interface and they hide from the launcher, making their removal more difficult. The malware can read and write on external storage and access the device's location.
It also tries to collect the SIM provider's country code, mobile country code, mobile network and country code. All the collected data is eventually sent to a C&C server over a secured channel. Also, these samples may use WebView to load phishing pages or fake alerts.
Android.Riskware.Agent.KCR :
These samples can access contacts data, read and write on external storage, access the device's location, initiate or answer phone calls, record audio or access the camera.
They request notification permission and spy on user's text messages. They hide by not appearing in the launcher and can install other apps. Also, information related to the mobile network and country code, mobile country code and SIM provider's country code can be collected and sent to a remote server.
Android.Riskware.HiddenAds.LL:
We covered this kind of malware when we discovered a world of fake apps hosted in third-party websites just waiting for victims to download them. The introduction of App Anomaly Detection helped us find more than 558.000 unique samples in this malware category alone.
Android.Riskware.Agent.KHZ:
These samples can access contacts data, calendar data, sensor data, send and receive SMS, read and write on external storage, access the device location, read or write call logs or even redirect the call to a different number, initiate or answer a phone call, record audio, recognize physical activity and to access the camera device.
- They usually request access to Accessibility permissions and try to load side components (other malicious apps within its payload).
- They hide themselves from the launcher, making removal difficult for users. Of course, like most malware, they will try to collect mobile country code, SIM provider's country code, Mobile Network and Country Code, Unique device ID, Mobile Subscriber Identity (IMSI), International Mobile Equipment Identity (IMEI), Serial number of the SIM. Everything is sent to a remote server.
- They could also ask for overlay permission, access to read notifications, permission to install other apps, and even for system setting permission.
Android.Riskware.TaJawaBar.A:
These samples can spy on calls, MMS, SMS, contacts and the user's location and send data to a C&C over a secure channel. These samples ask for overlay permission, accessibility and device admin. They're hidden from view and start sending SMS when active.
Android.Riskware.SpinOk.A:
These apps can access contacts data, calendar data, sensor data, send and receive SMS, read and write on external storage, access the device location, read or write call logs or even redirect the call to a different number, initiate or answer phone calls, record audio, recognize physical activity, access the camera device.
They were eventually removed from Google Play, but they're still likely available to download from other sources. Here's an example of such an app disguised as a movie streaming service.
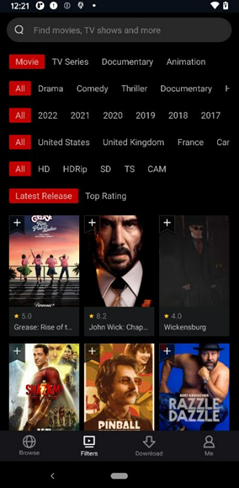
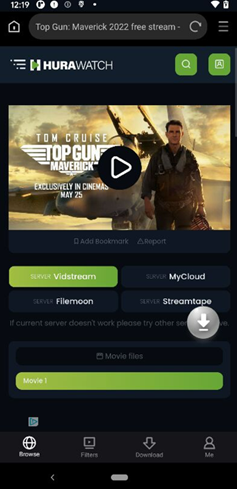
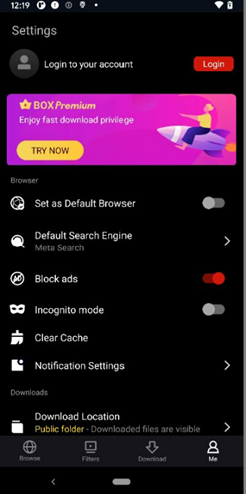
And here are the ads they show.


Trojans are scary
One of the reasons trojans are among the most dangerous is because of the level of access they have to Android devices. Some of the more popular kinds of Trojans that get a lot of coverage in the media are bankers.
Android.Trojan.Marcher.AV:
This is one of the more widespread variants, but they are more active. For the most part, they share roughly the same functionality. The malware can take a variety of actions on the device, including accessing contacts data, sending and receiving SMSs, reading and writing on external storage, accessing the device location, reading or writing call logs or even redirecting the call to a different number, initiating or answering a phone call, recording audio, accessing the camera device.
These samples request device admin and accessibility permissions and use persistent tactics to prevent users from uninstalling it. The applications try to collect mobile country codes, phone numbers, international mobile equipment identity (IMEI), and unique device IDs. They also try to access blacklisted domains.
Android.Trojan.Banker.ZK
The malware can access contacts data, send and receive SMS, read and write on external storage, access the device location, read or write call logs or even redirect the call to a different number, initiate or answer a phone call, record audio, and access the camera.
It also supports remote data transfer and will ask for accessibility access. It will also make sure that people can't easily find it and delete it.
Android.Trojan.Banker.XJ
Like the previous one, this malware can take a variety of actions on the device, including accessing contacts data, sending and receiving SMS, reading and writing on external storage, seeing the device location, reading or writing call logs or even redirecting the call to a different number, initiating or answering a phone call, recording audio, and accessing the camera device.
It comes with some extra functionality, like SMS spying. It uses dynamic code loading as an evasion technique to obfuscate its code, making it difficult to detect. Also, it tries to gain admin and accessibility access.
The malware also collects private information such as the country code, phone number, unique device ID, and International Mobile Equipment Identity (IMEI). All this information is sent to a C&C.
Android.Trojan.Banker.XO
This is another good example of an app with the Google Play Store label and icon. On start, it guides the user to get accessibility permissions and to show persistent notifications specifying that the app needs accessibility to be used.
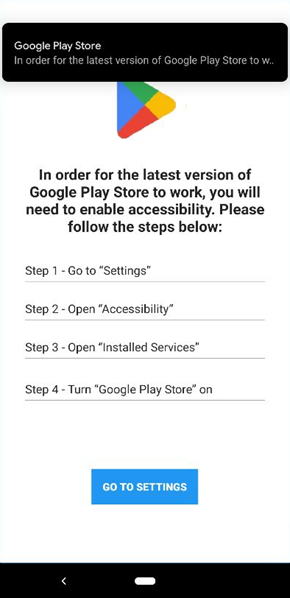
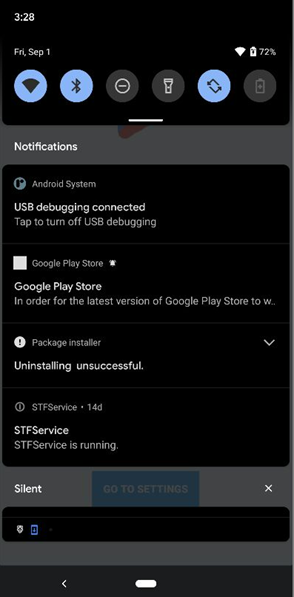
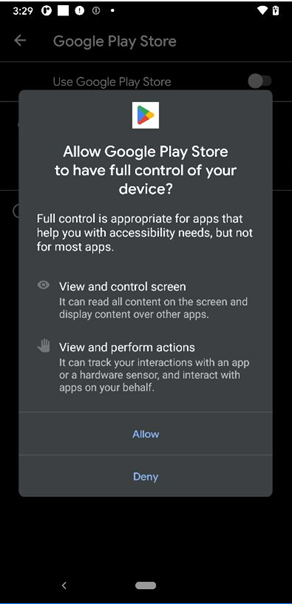
After the user enables accessibility, the app grants itself permission to access notifications, contacts data, send and receive SMSs, read and write on external storage, and initiate or answer phone calls.
Monitors or stalkerware
Not all attackers deploy apps that try to steal money or data. There's a particular type of Android application designed to track people, listen to their conversions, get their locations, read private messages and emails and so much more. Some of these apps are well known, such as Cerberus, but others are disguised as parental control.
Cerberus works as a hidden app on the victim's phone. It initially requests device admin rights, accessibility permission, notification permission, overlay, and system settings permission. It can read SMS and contacts and has spy functionality by getting the user's location and sending the data to a C&C over a secured channel.
We were already detecting Cerberus at installation, but now the App Anomaly technology will also catch its anomalous behavior.
Hoverwatch (com.Android.core.mntac):
The Hoverwatch app is detected as Android.Monitor.Refog.D and it's explicitly used to monitor child activity, employee activity, and the user's private devices. It requires basic permissions (access to storage, phone settings, call logs, contacts), Accessibility and overlay permission. It also turns off app notifications and battery optimization.
The application monitored user's activity on the following apps: Messages by Google, Google (direct search queries from the default Google interface), WhatsApp, Facebook, Samsung Android InCallUI, Google Chrome, Netflix, Gallery, Email Blue Mail – Calendar, Google Play Store, Settings, and Samsung Wallet.
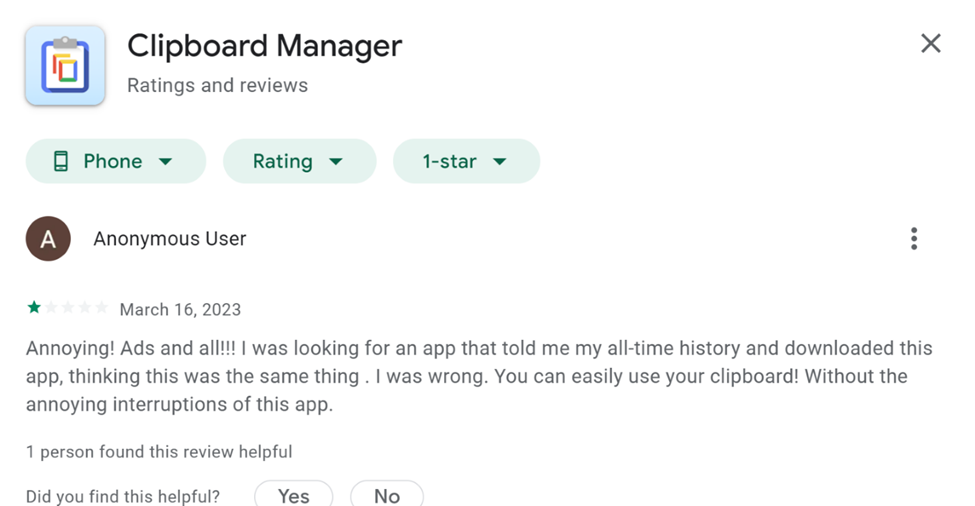
Clipboard Manager
Here's another example of an app that can save the history of copied text and asks to run in the background. It also asks for permission to display over other apps and asks for Accessibility permission, likely intending to show full-screen ads. More worryingly, it's available on Google Play, and users complain they’re bombarded with annoying ads.
Conclusion
The introduction of App Anomaly Detection as an extra technology available for free in Bitdefender Mobile Security for Android has helped unveil an entire ecosystem of apps, malware and other types of malicious applications that managed to stay hidden by employing various tactics.
By analyzing the behavior of apps, the security solution can now identify whether any of them changes behavior following an update or for any other reason. For example, some malicious apps remain dormant for weeks after compromising a device.
The new technology is meant to help Bitdefender Mobile Security users stay one step ahead of attackers, allowing them to remain safe online and reassuring them that the security solution will continue to monitor apps and their behaviors long after installation.
如有侵权请联系:admin#unsafe.sh