【逆向分析】BUUCTF 逆向题目 [ACTF新生赛2020]easyre
BUUCTF 逆向题目 [ACTF新生赛2020]easyre题目地址:https://buuoj.cn/challenges#[ACTF%E6%96%B0%E7%94%9F%E8%B5%9B2020 2023-12-8 16:36:58 Author: 利刃信安攻防实验室(查看原文) 阅读量:49 收藏
BUUCTF 逆向题目 [ACTF新生赛2020]easyre题目地址:https://buuoj.cn/challenges#[ACTF%E6%96%B0%E7%94%9F%E8%B5%9B2020 2023-12-8 16:36:58 Author: 利刃信安攻防实验室(查看原文) 阅读量:49 收藏
BUUCTF 逆向题目 [ACTF新生赛2020]easyre
题目地址:
https://buuoj.cn/challenges#[ACTF%E6%96%B0%E7%94%9F%E8%B5%9B2020]easyrehttps://files.buuoj.cn/files/ee7f29503c7140ae31d8aafc1a7ba03f/attachment.tar首先,查壳
信息:文件名: H:/第七届“强网杯”全国网络安全挑战赛/BUUCTF/[ACTF新生赛2020]easyre/easyre.exe大小: 21467(20.96 KiB)操作系统: Windows(95)架构: I386模式: 32 位类型: 控制台字节序: LE
打包工具: UPX(3.95)[NRV,best]
脱壳
再次查壳
使用IDA32打开文件
mov byte ptr [esp+12h], 2Ah ; '*'mov byte ptr [esp+13h], 46h ; 'F'mov byte ptr [esp+14h], 27h ; '''mov byte ptr [esp+15h], 22h ; '"'mov byte ptr [esp+16h], 4Eh ; 'N'mov byte ptr [esp+17h], 2Ch ; ','mov byte ptr [esp+18h], 22h ; '"'mov byte ptr [esp+19h], 28h ; '('mov byte ptr [esp+1Ah], 49h ; 'I'mov byte ptr [esp+1Bh], 3Fh ; '?'mov byte ptr [esp+1Ch], 2Bh ; '+'mov byte ptr [esp+1Dh], 40h ; '@'
int __cdecl main(int argc, const char **argv, const char **envp){_BYTE v4[12]; // [esp+12h] [ebp-2Eh] BYREF_DWORD v5[3]; // [esp+1Eh] [ebp-22h]_BYTE v6[5]; // [esp+2Ah] [ebp-16h] BYREFint v7; // [esp+2Fh] [ebp-11h]int v8; // [esp+33h] [ebp-Dh]int v9; // [esp+37h] [ebp-9h]char v10; // [esp+3Bh] [ebp-5h]int i; // [esp+3Ch] [ebp-4h]__main();qmemcpy(v4, "*F'\"N,\"(I?+@", sizeof(v4));printf("Please input:");scanf("%s", v6);if ( v6[0] != 'A' || v6[1] != 'C' || v6[2] != 'T' || v6[3] != 'F' || v6[4] != '{' || v10 != '}' )return 0;v5[0] = v7;v5[1] = v8;v5[2] = v9;for ( i = 0; i <= 11; ++i ){if ( v4[i] != _data_start__[*(v5 + i) - 1] )return 0;}printf("You are correct!");return 0;}
根据上面代码,v4数组对应的字符串
*F'"N,"(I?+@__data_start__对应的字符串
~}|{zyxwvutsrqponmlkjihgfedcba`_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$# !"要求 v4[i] = _data_start__[*(v5 + i) - 1] )
编写代码
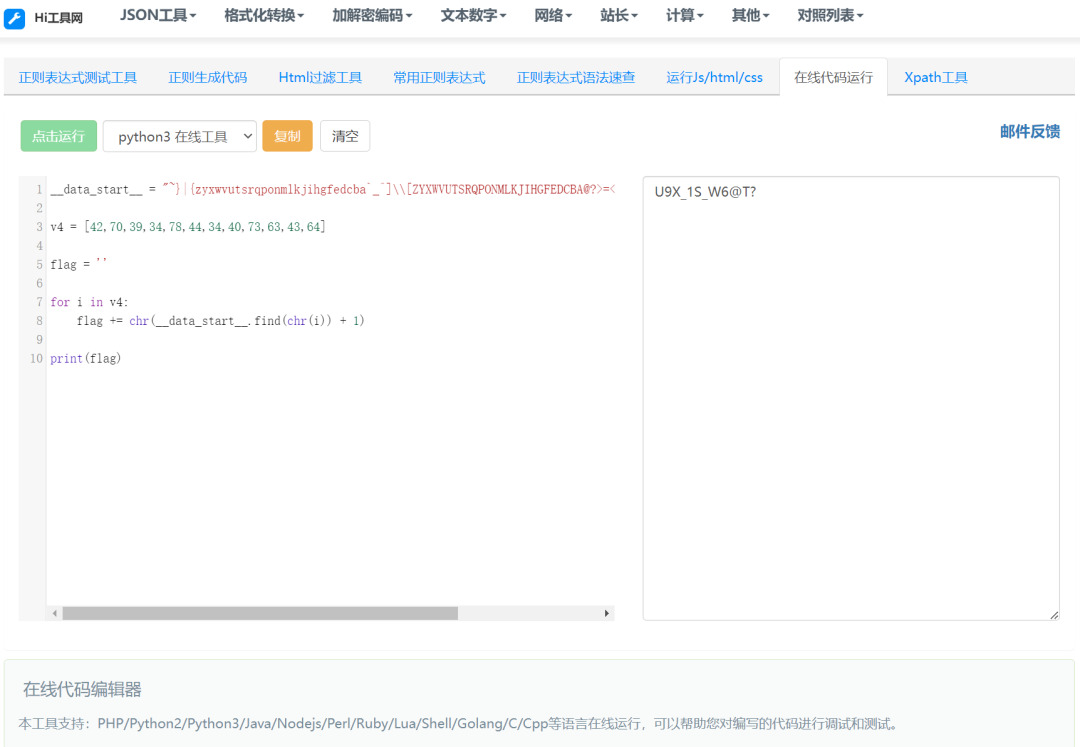
__data_start__ = "~}|{zyxwvutsrqponmlkjihgfedcba`_^]\\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$# !\""v4 = [42,70,39,34,78,44,34,40,73,63,43,64]flag = ''for i in v4:flag += chr(__data_start__.find(chr(i)) + 1)print(flag)
flag{U9X_1S_W6@T?}
文章来源: http://mp.weixin.qq.com/s?__biz=MzU1Mjk3MDY1OA==&mid=2247508561&idx=1&sn=a1fab148693ba35be7aeaa84c8872f63&chksm=fbfb129ccc8c9b8ad112c70f8b975ebfb1859f1f79c64dfc5b8ac78dac6b700b9f59c4bb5306&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh