2023-12-5 23:46:44 Author: flashpoint.io(查看原文) 阅读量:21 收藏
Redefining vulnerability standards
Flashpoint’s VulnDB, our premier vulnerability intelligence database, has achieved a critical milestone by documenting over 100,000 vulnerabilities missed by the CVE & NVD databases.
This achievement goes beyond mere numbers, revealing a stark reality: there are significant gaps in CVE-dependent vulnerability management programs. In this article we highlight Flashpoint’s collection of non-CVE vulnerabilities, which affect key players like Google and Microsoft, as well as numerous third-party libraries—in addition to zero-day and in-the-wild exploits that are being used by threat actors.
This data is especially crucial for industries like manufacturing, and those in the blockchain sectors, underscoring the importance of comprehensive vulnerability intelligence in today’s cyber threat landscape.
VulnDB’s non-CVE vulnerabilities: A new perspective of cyber threat
Flashpoint’s VulnDB now complements the existing landscape of over 339,000 known disclosed vulnerabilities with a groundbreaking addition of over 101,000 non-CVE vulnerabilities. What does this mean for the security of your organization? Let’s examine what this extensive, yet often overlooked, vulnerability data means for you and your organization’s security posture.
What does missing vulnerability data mean for your organization:
- Facing the unseen danger: Vulnerability management programs that heavily rely on CVE data are likely operating on less than 70 percent of known vulnerability risk.
- The hidden threats in plain sight: VulnDB’s non-CVE ID collection includes zero-days and discovered-in-the-wild vulnerabilities. There are known instances of threat actors using them in recent cyberattacks.
- A wake-up call for major vendors: Non-CVE vulnerabilities also affect major vendors such as Google, Microsoft, Adobe, Apple, and more. They also affect well-known third-party libraries—a market historically underserved by MITRE, which administers the CVE Program.
- Specialized industries, specialized risks: For organizations in highly specialized industries like manufacturing, medical, and blockchain technology, VulnDB’s non-CVE collection is particularly beneficial.
- Using VulnDB, triaging and prioritizing non-CVE vulnerabilities is made easier. Every vulnerability entry (whether non-CVE or CVE) is standardized, containing up to 60 distinct classifications based on the disclosure. It also captures public citation, exploit details, CVSSv2, and CVSSv3 scores.
The importance of having the full intelligence picture
Flashpoint is the only vulnerability intelligence provider with the most detailed, largest, and broadest collection of publicly disclosed vulnerabilities. We proactively monitor thousands of websites and developer resources. VulnDB includes everything in CVE and more, fully mapping to CVE / NVD, in addition to resources like the CISA KEV.
Each year, CVE has missed 28 to 33 percent of known disclosed vulnerabilities. On average, our VulnDB team adds 23 new vulnerabilities daily that CVE fails to report. Additionally, VulnDB publishes vulnerabilities two weeks faster than CVE, on average, and in some cases months faster.
Without the full intelligence picture, vulnerability risk models are likely only 70-percent effective at best. Most organizations lack the resources to monitor thousands of vulnerability disclosure sources and triage every issue. Therefore, using a comprehensive and timely source like VulnDB is invaluable for security teams as they can better prioritize the threats that impact them. Having such broad coverage that also includes exploit availability, attack vector, and remediation information allows for the quick targeting of ‘easy wins’ in patching.
Taking a deeper look: VulnDB’s 100K non-CVE vulnerabilities
Let’s examine the entire vulnerability disclosure landscape with over 330,000 unique vulnerabilities that have been disclosed:
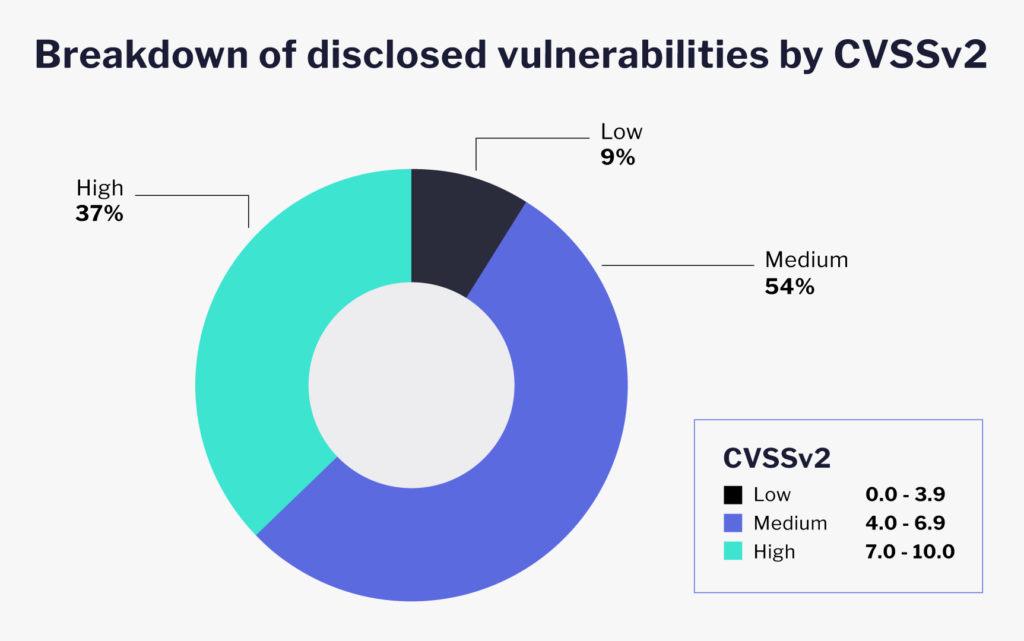
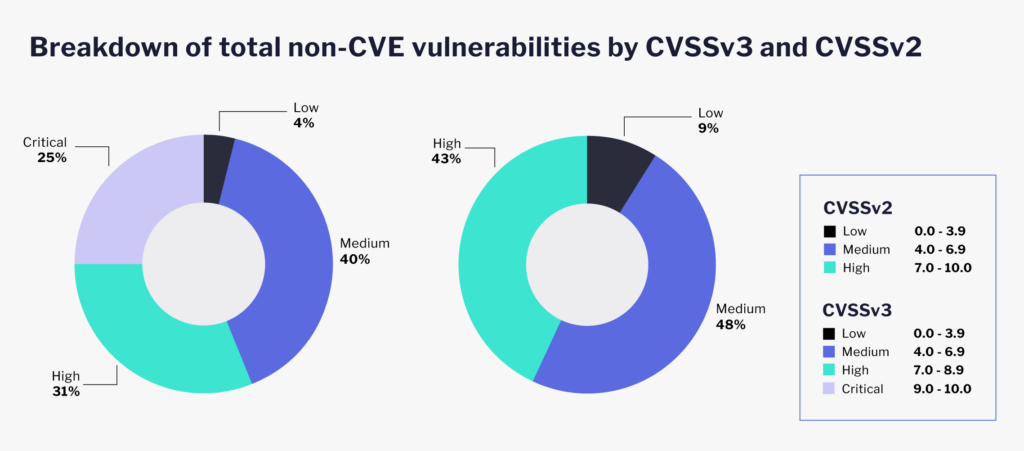
There are many ways to prioritize vulnerabilities, and some organizations do have their own vulnerability management frameworks. However, CVSS, regardless of its many shortcomings, has been consistently used by organizations around the world.
The standard vulnerability management framework dictates that if a given vulnerability is scored between 7.0 to 9.0 (high), or 9.1 to 10.0 (critical), it poses a great risk to the organization. Therefore, high to critical issues should be put to the top of the queue. As we can see, out of the total number of disclosed vulnerabilities, 37 percent of them are high to critical in severity. Compared to this, how does VulnDB’s non-CVE collection fit?
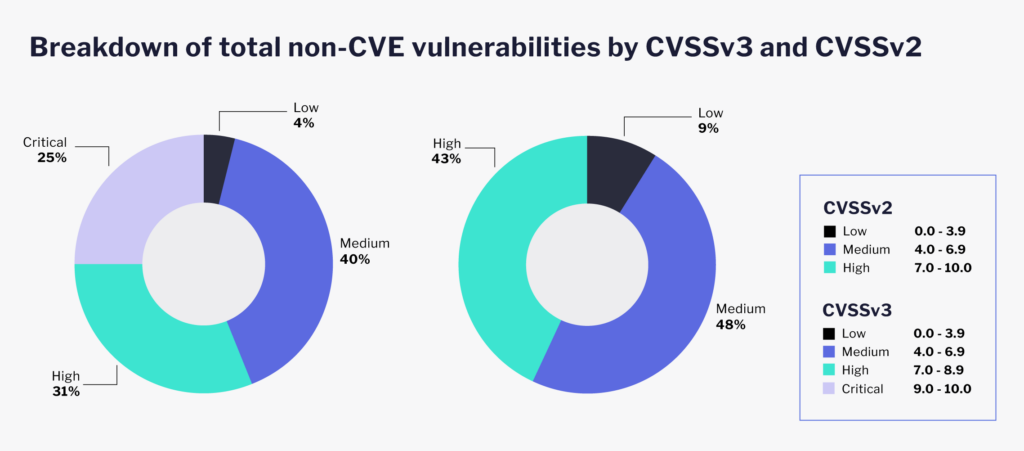
Using CVSSv3, more than half of them are scored between high to critical. This is just one example of how shifting from CVSSv2 to v3 can impact your organization’s triage process. Aside from severity, let’s examine exploitability, which is arguably a better way to enhance potential risk. Out of the over 100,000 missing non-CVE vulnerabilities, 60.4 percent of them are remotely exploitable in some fashion.
“VulnDB is the gold standard for vulnerability intelligence.”
Vulnerability Manager, Fortune 500 Telecom Company
Non-CVE vulnerabilities introduces more possible attack vectors
Flashpoint has also tracked several instances of non-CVE vulnerabilities being exploited by threat actors. Vulnerabilities without CVE IDs affecting major vendors and products also fall within this subset.
As of December 2023, our analysts have cataloged over 300 vulnerabilities that were discovered being exploited in the wild, that still do not have a CVE ID. These include vulnerabilities in:
- Adobe Reader
- Apple iOS
- Apple macOS
- Google Android
- Microsoft SQL Server
- MOVEit Transfer (DMZ)
- SIemens SIMATIC
- Solarwinds Orion Platform
As of December 2023, the following have been exploited in some form of malware, yet do not have a CVE ID:
- Apache Hadoop
- Google Authenticator for Android
- PHP
Timing is everything
Organizations need to remember that vulnerabilities discovered in the wild are sometimes first disclosed without a CVE ID. Zero-day vulnerabilities and other high-profile issues, such as the MOVEit vulnerability, also tend to follow this trend. Even though CVE usually will assign IDs to prolific vulnerability events, this process is not always timely. In the case of some zero days, it could take days, weeks, or even up to a whole month for an ID to be assigned and for NVD to do their analysis. Therefore, it is critical for security teams to get access to newly disclosed vulnerabilities as soon as details are known, whether they have a CVE ID at disclosure or not.
Non-CVE vulnerabilities provide value to everyone, especially niche industries
Many of these overlooked issues affect vendors such as Microsoft, Google, and Siemens, software that are used by most large companies. These vulnerabilities often have high to critical severity scores.

Although a portion of non-CVE vulnerabilities will likely affect vendors or software that most Fortune 500 companies might not use, that doesn’t diminish their importance. We have to remember that the entire commercial market does not rely on the same systems. Every industry has its own nuances, technology needs, and budgetary constraints. We have been told first-hand by customers that they use relatively obscure software or plugins not commonly used. Therefore, security teams will need every bit of data available to them.
For example, seasoned IT teams within niche industries know that their vulnerability needs are often underserved by CVE. For these organizations, older and more obscure technologies often underpin key business operations. Vendor disclosures and updates are infrequent, and if there are vulnerabilities being reported, CVE is unlikely to become aware of them. However, this does not mean that vulnerabilities affecting those systems do not exist.
Take the manufacturing industry for example. There is a surplus of SCADA-related issues that fall through the cracks. According to CVE, there are a reported 4,859 SCADA vulnerabilities. However, VulnDB captures an additional 1,283 known SCADA vulnerabilities, which is over 25 percent of what CVE is able to report.
There are even more underserved industries that will benefit from VulnDB’s collection of non-CVE vulnerabilities. Organizations within the medical devices space and the blockchain industries will also find a sizable amount of non-CVE issues that might be specifically pertinent for them.
Integrating non-CVE vulnerabilities with VulnDB for improved workflows
Incorporating non-CVE vulnerabilities into vulnerability management programs enhances awareness and coverage, which leads to more effective prioritization. More than 60 percent of VulnDB’s non-CVE vulnerabilities have immediate solutions, and all entries are standardized and scrutinized, containing over 60 distinct classifications. VulnDB can also be integrated into your existing tools or workflow—being able to be leveraged in existing GRC, ITIL, CMDB, and many SIEM products.
What Flashpoint’s 100,000+ milestone means is that better data matters. Our team goes above and beyond to provide our customers with the most comprehensive, actionable, and timely source of vulnerability intelligence. This includes our team adding over 90 new vulnerabilities on average daily, while also updating roughly many hundreds of existing records. Request a demo to see how VulnDB’s rich collection of vulnerability data can make a difference for your security teams.
Further reading:
如有侵权请联系:admin#unsafe.sh