2023-12-1 07:23:29 Author: securityboulevard.com(查看原文) 阅读量:4 收藏

Quick Response codes – aka QR Codes – were first used in 1994 by a Japanese company called Denso Wave to primarily track parts in the automotive manufacturing process. The QR code’s design allowed it to store more information than the traditional barcodes that were used and could be quickly scanned, hence the name “Quick Response.” Over time, QR codes have found applications beyond their original intended use, becoming widely used for many other purposes, including marketing, mobile payments, and information sharing. Their popularity surged with the widespread adoption of smartphones and phone cameras.
Thirty years later, QR codes are still on the rise. In 2022, according to Statista, about “89 million smartphone users in the United States scanned a QR code on their mobile devices.” Usage of mobile QR code scanners is projected to reach over 100 million users in the U.S. by 2025. And according to a 2021 survey of U.S. shoppers cited by Statista, almost half of the respondents reported using a QR code to access marketing or promotional offers.
With success comes cybercrime, and this year threat actors have picked up on QR codes and turned them into malicious quishing (QR code phishing) attacks. The threats of quishing and QRLJacking (QR link jacking) are exploiting user trust and convenience and are bypassing security filters. Cybercriminals are manipulating QR codes to redirect users to malicious sites to steal login credentials, financial information, and more. These malicious QR codes can contain malware to gain access to the user’s mobile device and steal personal and financial information.
Last month, SlashNext Threat Labs published a “malicious usage of QR codes” blog post detailing how threat actors leverage QR codes for various attacks and breach attempts. It defines quishing, a blend of QR code and phishing techniques, and details how quishing manipulates QR codes for nefarious purposes used in phishing emails, digital ads, social media, or even posters in common areas. In the blog, QRLJacking is explained as a social engineering method that exploits the “login with QR code” feature available on many legitimate apps and websites, which is then used by bad actors to gain full control of victims’ accounts.
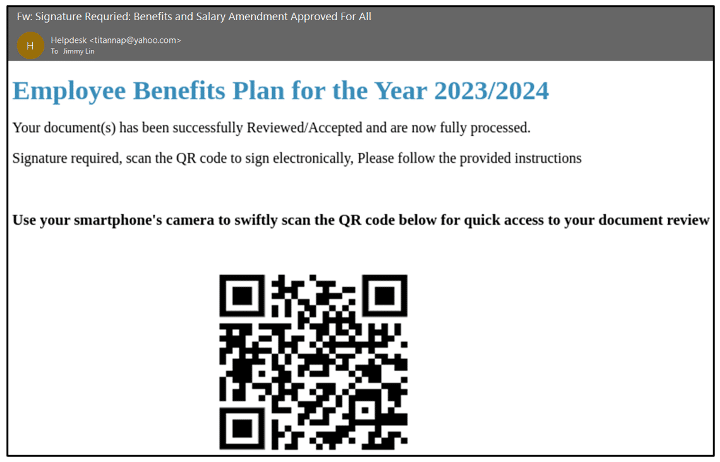
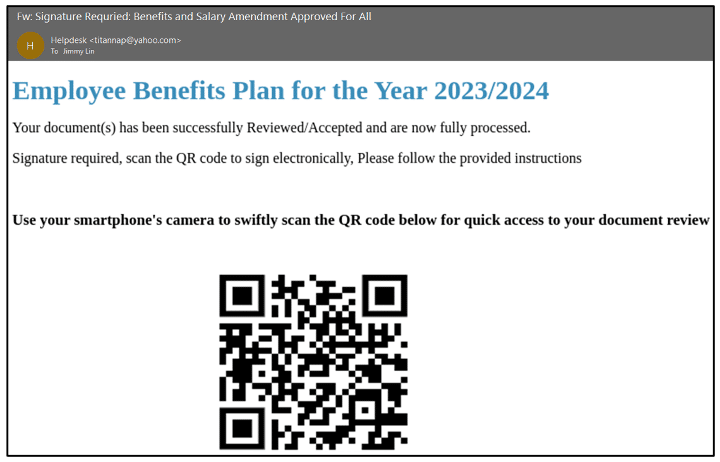
The following image illustrates how an email that includes a QR code incites an employee into scanning the code using a mobile device. The QR code then takes the targeted user, via their mobile phone, to a phishing website.
Security experts have noted a recent 50% spike in QR code-based phishing attacks as cybercriminals leverage this tactic to exploit user trust and convenience. Given the growing dependence on QR codes across various sectors and the ease of manipulating them, it is highly likely that quishing attacks will continue to increase in popularity among cybercriminals. With a 50% spike in these types of attacks this quarter alone, security vendors and organizations need technology now that can identify malicious QR codes in email, and all messaging channels including personal email and mobile apps to stop these threats before they experience a costly breach.
In a 2022 FBI ICE report, it was noted that the FBI started receiving a significant number of victims reporting QR code scams that, in some instances, included large amounts of money loss. The report mentioned fraudulent crypto transactions. Today, QR code cybercrime has evolved to many types, including gift cards – instead of receiving a free $100 gift card, the QR code takes you to a malicious website. Quishing also uses business compromise and link/file phishing themes including these listed in a 2023 HHS white paper:
- Fraudulent invoices
- Request for personal information
- Late payment references with links
- Fake discounts on products or services
- False government refunds
Other reasons why quishing is on the rise include:
- Easy way to bypass Microsoft’s advance threat protection (ATP) services Safe Links and Safe Attachments
- Exploits users familiarity and “trust” using QR codes
- Lag in user awareness training
- No protection on mobile devices
Types of Quishing Protection
The FBI has given a list of ways to protect users from malicious QR code exploits, including the following:
- Do not scan randomly found QR codes
- Be suspicious if the QR code scan takes you to a site that asks for a password or login information.
- Don’t scan QR codes found in emails or text messages unless you know they’re legitimate and call the sender to confirm.
- If the QR code looks like it has been physically tampered with (for example, in a poster), don’t use it.
SlashNext QR Code Phishing Protection – An Industry First
We’ve been working on QR code phishing for some time and we’re now delivering the “industry’s first multi-channel quishing protection to block malicious QR codes in all business and personal messaging channels with 99% accuracy.”
SlashNext’s QR Code Phishing Protection leverages patent-pending computer vision and a new natural language processing (NLP) classifier to block the delivery of messages containing malicious QR codes and block malicious QR code URLs scanned by users’ mobile phones. Its ability to detect malicious intent in both the QR code itself as well as the accompanying message makes it the most comprehensive and accurate protection against QR-code based attacks.
The QR code phishing protection stops quishing, QRLJacking and other scams distributed via malicious QR codes. It’s the first security solution to offer multi-channel quishing protection that blocks malicious QR codes in email, mobile, web and messaging channels such as Slack, iMessage, Microsoft Teams, and more.
You can find more information in the press release.
Contact SlashNext for a demo or read more on our website about QR Code Phishing Protection capabilities.
The post Malicious Use of QR Codes on the Rise Through Quishing Attacks first appeared on SlashNext.
*** This is a Security Bloggers Network syndicated blog from SlashNext authored by Barry Strauss. Read the original post at: https://slashnext.com/blog/malicious-use-of-qr-codes-on-the-rise-through-quishing-attacks/
如有侵权请联系:admin#unsafe.sh