Update: 1768.py Version 0.0.20
This update to 1768.py, my Cobalt Strike beacon analysis tool, adds “runtime configuration” extraction.
Although 1768.py could already search for beacon configurations inside process memory dumps, the dump was just processed as a raw file.
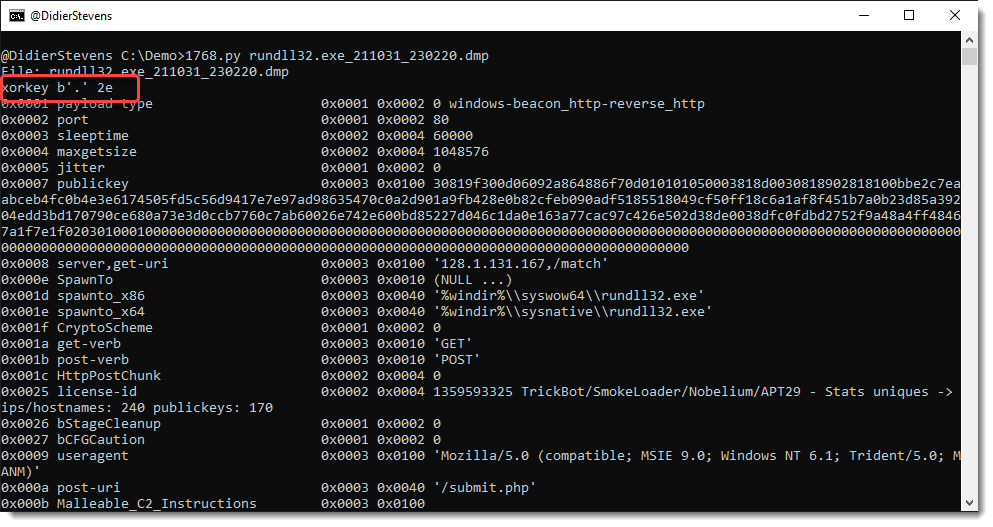
With this update, 1768.py will also search for the runtime configuration inside a process memory dump. The runtime configuration, is a C/C++ array with integers and pointers, that is created in the heap by the beacon’s C/C++ code from the obfuscated configuration (e.g., XOR 0x2E).
Because this requires pointer calculations for the heap, Python module minidump is required. A warning will be displayed if it is not installed and it is needed.
The hexadecimal dump screenshots in this blog post show a runtime configuration.
Example of 1768.py finding a runtime configuration:

This is a 32-bit runtime config.
As the runtime config uses pointers, its structure is different for 32-bit and 64-bit beacons (because pointer size is different).
In this process memory dump, 1768.py only found the runtime config, not the embedded config.
Here is an example where both configs are found:


1768_v0_0_20.zip (http)
MD5: EFEFF856FEAD08DE8F9F27056E729351
SHA256: 2F71EA23F64403C26B64CA32E8FA025CAB1F941790D746E8906AA87401900AAC
No comments yet.
如有侵权请联系:admin#unsafe.sh