23 November 2023
KELA Cyber Intelligence Center
The cybercrime landscape is constantly evolving with sophisticated threats and risks, but the heart of the cybercrime ecosystem is built on threat actors. Being the brains behind each cyber incident, they are responsible for ransomware attacks, data breaches, building new malware, and aiming to compromise corporate networks. Threat actors are a wide range of players, from nation-state actors to script kiddies.
This blog delves into KELA’s new module – Threat Actors and details how CTI analysts can leverage it for their everyday tasks.
The module allows security teams to monitor, identify, and track threat actors in the cybercrime landscape, understand their TTPs and connections with other actors. It further delivers actionable intelligence on their motivations, aliases, tools, contact details, and activity in cybercrime forums.
Dashboards Featuring Threat Actor Profiles with Filter Options
The module offers extensive and enriched profiles of threat actors within a unified platform. This empowers threat intelligence analysts to research and investigate adversaries based on their specific interests, such as targeted sectors, geographies, actors’ motivations, and their activities in cybercrime forums. All this information is conveniently accessible in a single, consolidated dashboard.
The actor’s profile includes valuable information, such as:
- Origin
- Motivation
- Handles
- Cybercrime communities the actor is active on
- Targeted sectors
- Targeted geographies
- A summary description of the activity of the actor
The Actors Hub gives an overview of all initial access brokers (IABs), who specialize in compromising corporate networks and offering network access for sale. After applying a filter based on a particular motivation, the analyst will exclusively view profiles associated with a specific cybercrime activity: ransomware, network access, data leaks, malware, etc. For example, an analyst can filter by IABs who target specific geography and get results of around 100 initial access brokers that target the UK.
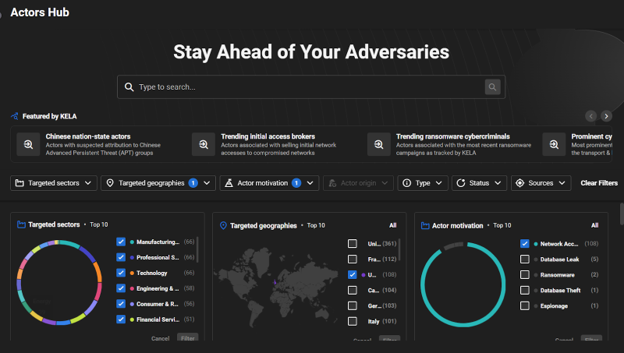
Search by Location: UK and the Motivation of an actor: Network Access
Specific Threat Actor Search
The module allows cyber threat intelligence teams to delve into comprehensive research on specific threat actors, pivoting to this phase after monitoring cybercrime trends and campaigns. Analysts can easily retrieve detailed information about an actor by entering their moniker and have a look into their contact details such as email addresses, instant messaging services (Telegram, Jabber, TOX) and more.
After conducting research using KELA’s Investigate module and gaining insights into current cyber trends, CTI teams will find value in exploring the specific threat actors. This extended exploration can provide a deeper understanding, especially when focusing on those initial access brokers.
As an illustration, while reviewing the Intelligence Feed, an analyst may highlight an incident involving network access to Volkswagen Argentina, posted by Rqrelty. Subsequently, the analyst can navigate to the actor’s profile on the Actor Hub to access more comprehensive details about the actor, including credibility, activity on cybercrime forums, and contact information. This process helps in understanding if the actor’s cybercrime activities are primarily centered around the automotive sector and whether they possess expertise as an Initial Access Broker (IAB), providing valuable insights for subsequent investigations.
Searching for the actor “Rqrelty” reveals details about the profile of the actor providing an extensive overview of their activities. The actor’s card includes a visual graph of their activity over time and by sources. As the card indicates, the actor has been active on different cybercrime forums including Exploit and XSS, operating under different handles like Rqrelty, Sqlety, Totemchikkkk. The analyst can then review the actor’s prior activities tracked by KELA’s research team across all forums and under each handle. The card also provides contact details retrieved by KELA research team enabling actions such as blocking communication through specific email addresses and social media channels, or conducting further interaction with the actor.
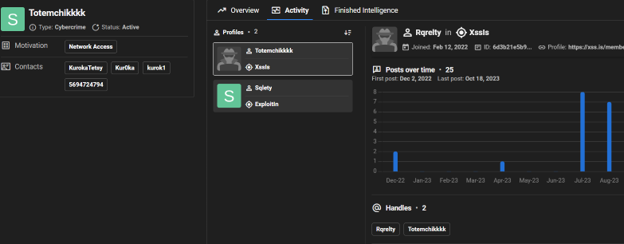
Rqrelty: an experienced IAB that has been active on different cybercrime forums under different handles
Investigation with One Click
Actors Hub enables investigations even with just a single parameter received by the CTI team. For instance, if a user becomes a target of a ransomware attack and receives a ransom note, a search on TOX can unveil the actor responsible. For example, inputting the TOX ID 3488458145EB62D7D3947E3811234F4663D9B5AEEF6584AB08A2099A7F946664BBA2B0D30BFC leads to Alphv (BlackCat) ransomware gang. The associated card offers a comprehensive overview of Alphv’s members, enriched with finished intelligence, including various aliases on cybercrime forums and additional contact details.
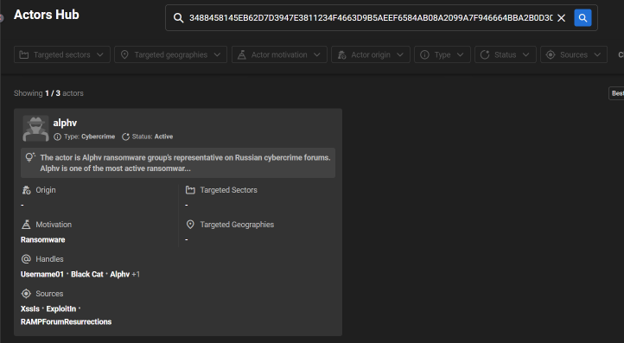
Tox ID reveals the involvement of the Alphv ransomware group
Here is another illustration: a CTI team might be interested in exploring new malware and tools, such as the Whitesnake infostealer. Searching for the keyword “whitesnake” on Actors Hub returns results for six different actors operating under the same handle “Whitesnake”, some of whom have the same profile picture associated with Whitesnake infostealer. Interestingly, Whitesnake’s account on XSS forum has been banned, which may imply that the actor’s credibility and reliability on cybercrime forums is low. This can provide analysts with indicators for further investigation. Clicking on the Whitesnake card reveals more details:the actor initiated operations on XSS forum in January 2023 and remained active untill August 2023, whereas on BDF, the actor Whitesnake appears to still be active.
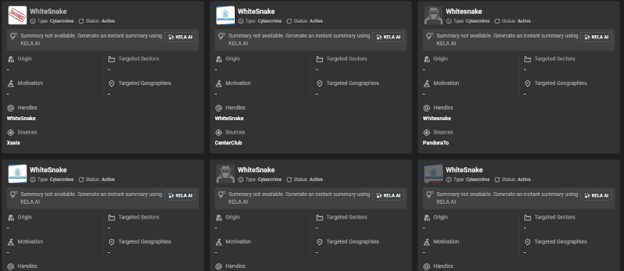
Whitesnake actor appears to have been banned from XSS forum
Valuable Insights Based on Metadata
As mentioned above, the platform provides real actionable intelligence not solely based on posts and content on cybercrime forums, but rather on metadata as well. This may include information about registration dates on cybercrime forums, author ID, profile picture, and more.
For instance, the threat actor ‘adrastea’ has been active on several cybercrime forums since July 2022, offering government databases for sale. A search for their handle shows that they use the same profile picture across all forums. The search results display five profile pictures of adrastea on various forums and a quick examination of the pictures suggests that this is the same threat actor.
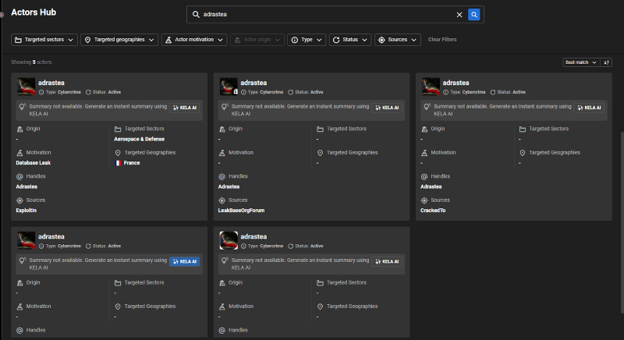
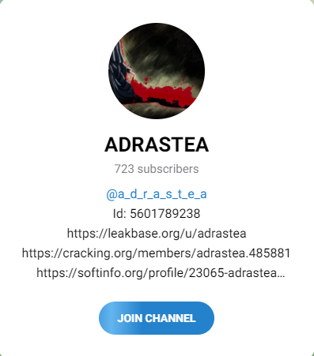
The actor adrastea uses the same profile picture on different cybercrime platforms
Threat actors often include additional user details in their signatures on cybercrime forums, such as contact information, handles, affiliations, and more. This valuable information can be enticing and helpful for further investigation. KELA’s Threat Actors module extracts this data and incorporates it into the threat actor’s profile.
For example, when examining the signature of the threat actor ‘Drumrlu’, one can notice that they use “Turkish Hacker” , which may provide a hint about their origin.
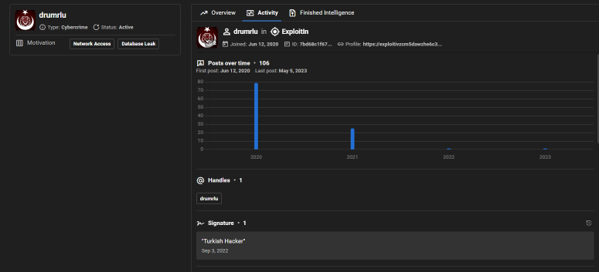
Threat actor Drumrlu, an IAB, allegedly based in Turkey
LockBitSupp, a member of LockBit ransomware group, includes information in the signature that can be useful. The actor details how they can be contacted: “When you write to me in a personal message, do not check the box “Encrypt correspondence (AES256+SHA256)”, if you are afraid that someone else will read your personal messages, then write through a secure PRIVATE NOTE and you can send a picture or file through a secure FILE SHARE”.
Moreover, signatures often reveal information about the actor’s motivation and area of operation. The threat actor Bl00d included the following note in his signature: “Looking for botnet/stealer operation partner. DM me Join my public hacking channel on Telegram”.
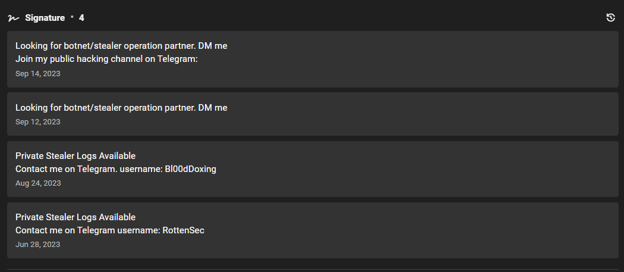
The actor states in their signature that they are seeking partners for a stealer operation
The Value of KELA’s Threat Actors Module
KELA’s Threat Actors module streamlines investigations by consolidating extensive information on threat actors from various web sources. With a user-friendly interface and linked profiles, it provides quick access to comprehensive insights, making it an invaluable tool for routine data analysis. The module’s visual graphs offer immediate insights into threat actors’ historical activity, channel status, and real identities, enhancing intelligence gathering.
