
2023-11-12 06:8:57 Author: blog.sucuri.net(查看原文) 阅读量:6 收藏
Attackers are always on the hunt for vulnerable websites. Whether you have a WordPress, Magento, or Joomla website — you’ll want to take steps to secure your site and server from attacks and malware.
In today’s post, we’ll be outlining the top twelve steps you can take to harden your website and enhance the security of your environment.
What is website security?
Website security is all about adding layers of protection to reduce the risk of an attack. This is a process referred to as “defense in depth.” It’s essentially a catch-all term used to describe the techniques, settings, and configurations that help enhance the security of your website.
Why should I secure my website?
If you care about your website and visitors, you’ll want to take steps to secure your website against attacks. Website hardening techniques can help reduce risk from automated attacks, known vulnerabilities, and strengthen any weak access points.
How to secure a website
Let’s dive in. Here are our top 12 recommendations to secure a website:
- Keep website software patched and updated
- Reduce the attack surface
- Remove unnecessary plugins and themes
- Practice the principle of least privilege
- Restrict access to the admin panel
- Use multi-factor authentication
- Use strong, unique passwords
- Access over HTTPS
- Reduce exposure of information
- Monitor the website and keep up with its log activity
- Check for input sanitization techniques
- Use a web application firewall
1 – Keep website software patched and updated
Every single piece of software running on your website needs to be kept up to date with the latest patches and security updates. Website vulnerabilities come in all shapes and sizes, so it is important to update your CMS along with any third party components like plugins, themes, and extensions.
And don’t neglect your server, Apache, or PHP updates either. These important components need to be patched to the latest version to mitigate risk, too.
By keeping everything up-to-date with the latest security releases, you’ll reduce the possibility of attackers targeting your site due to known vulnerabilities.
2 – Reduce the attack surface
There are a few ways you can reduce the attack surface of your website.
- Only allow public access to public areas of your application.
- Deny everything else by default.
- Search for and harden all of your website access points.
These can be accomplished with server configuration rules, setting file and folder permissions, and by using features found in modern web application firewalls.
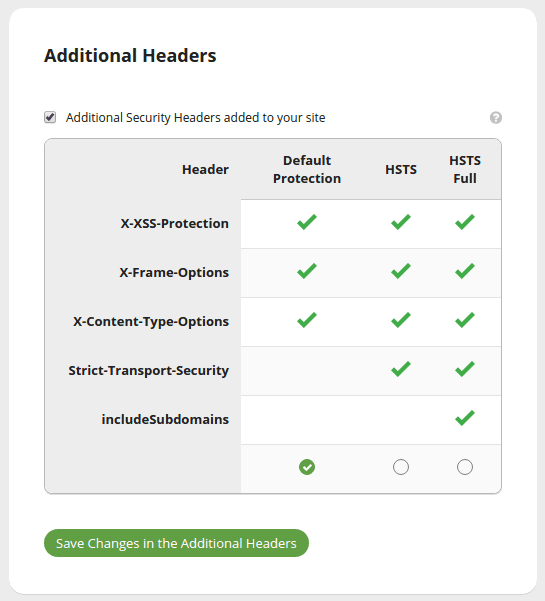
3 – Remove unnecessary plugins and themes
We all love features and functionality that improve engagement and website experience. But the more software (or third-party components) you have, the greater the risk of an attack. Each additional piece of code on your website is a potential gateway for attack.
So if you’re not using a plugin, theme, or third party component — uninstall it. Especially if you’re not keeping up with updates on your site. Keep only what you’re actively using on your website. And remember: disabling a plugin or theme is not the same as removing it.
4 – Practice the principle of least privilege
Restrict what each member of your team can do and make sure they don’t have more privileges than necessary. This can be accomplished by practicing the principle of least privilege.
Granting every user administrative access is a security hazard. You can mitigate risk by using appropriate permissions. So, make use of CMS roles and define access control for your site.
For example: If you have an author or editor contributing to your website, they shouldn’t need administrator privileges.
Grant someone the exact amount of access needed to do their job. And be sure to remove users and revoke access when they no longer need it.
5 – Restrict access to the admin panel
Administrator panel compromises are among some of the most common attacks WordPress users face.
By default, WordPress admin panel login screens are accessible to the public. This renders them vulnerable to brute force attacks. But regardless of the CMS you use, restricting access to your admin or login panel can significantly enhance the security of your website.

Here are some ways that you can enhance the security of your admin panel:
- Restrict access to specific IP addresses
- Require CAPTCHA
- Limit login attempts
- Use a non-standard URL
Applying these techniques to your admin pages can deter brute force and password guessing attempts, as well as limit access for bad actors.
6 – Use multi-factor authentication
Multi-factor authentication requests multiple methods of authentication from different categories of credentials to verify the identity of a user. It essentially combines two or more independent forms of authentication.
For example:
- What the user knows (a password)
- What the user has (a security token)
- What the user is (biometrics)
Combining two or more of these forms of authentication creates a layered defense that makes it significantly harder for an unauthorized attacker to breach.
WordPress users can leverage a variety of plugins to help accomplish this on your site. Choose one that has solid reviews — and make sure it’s regularly maintained and patched by the development team.
Sucuri Firewall users can employ two factor authentication on their website with Google authenticator.
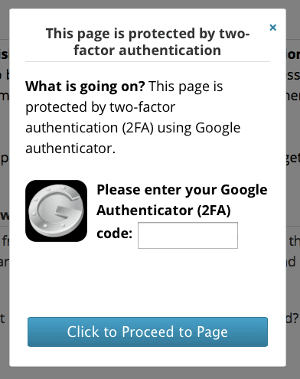
7 – Use strong, unique passwords
Passwords are the standard for logging in to accounts. That includes your server, database, FTP, and admin panels.
By using strong and unique passwords for all of your accounts, you are hardening your website as well. So enforce the use of secure passwords for your website.
Take a quick look at this quick demo of how brute force attacks work:
As you can see, automated attacks make it much easier for hackers to gain unauthorized access to your website. So be sure to use secure passwords for all of your accounts.
If creating and maintaining strong, unique passwords is a challenging task for you, use a password manager to store, encrypt and manage them for your site.
8 – Access over HTTPS
All websites should be accessed over HTTPS — this ensures all data is securely encrypted during transit from point A to point B.
HTTPS and SSL certificates are the status quo when it comes to securing data in transit on your website. They’re especially important for sites collecting any form of data — including credit card information, login credentials, names, addresses, or any other form of Personally Identifiable Information (PII).
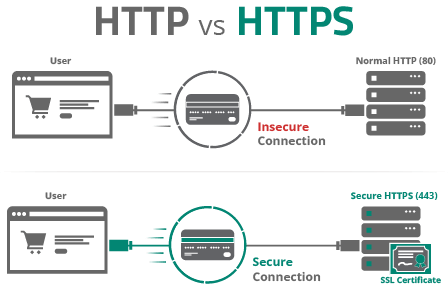
You’ll also want to prevent direct access from public hotspots by allowing access to restricted areas only when using a secure channel such as a VPN or proxy. And make sure all administrators are accessing from safe devices!
9 – Reduce exposure of information
Instead of “Your password is incorrect”, change failed password attempt messages to something like “Login credentials invalid.”
Why? In the first example, you’re explicitly telling the attacker that the username is correct, but the password isn’t. But in the second example, the attacker won’t know for sure if they have the wrong username, password — or both.
This kind of reduced verbosity can diminish the chance of a successful brute force attack.
Furthermore, make sure sensitive website data isn’t written to any website or server logs — and that logs cannot be publicly accessible. Using an internal error code can reduce the amount of information displayed while still allowing for easy debugging.
10 – Monitor the website and keep up with its log activity
Logs are exceptionally valuable for website monitoring. They’re also very helpful when you need to troubleshoot technical issues or ensure user accountability.
Furthermore, if you have an ecommerce website, logs are mandatory for PCI DSS compliance. And storing logs for future analysis is also a critical piece for GDPR, CIPA, and other regulations.
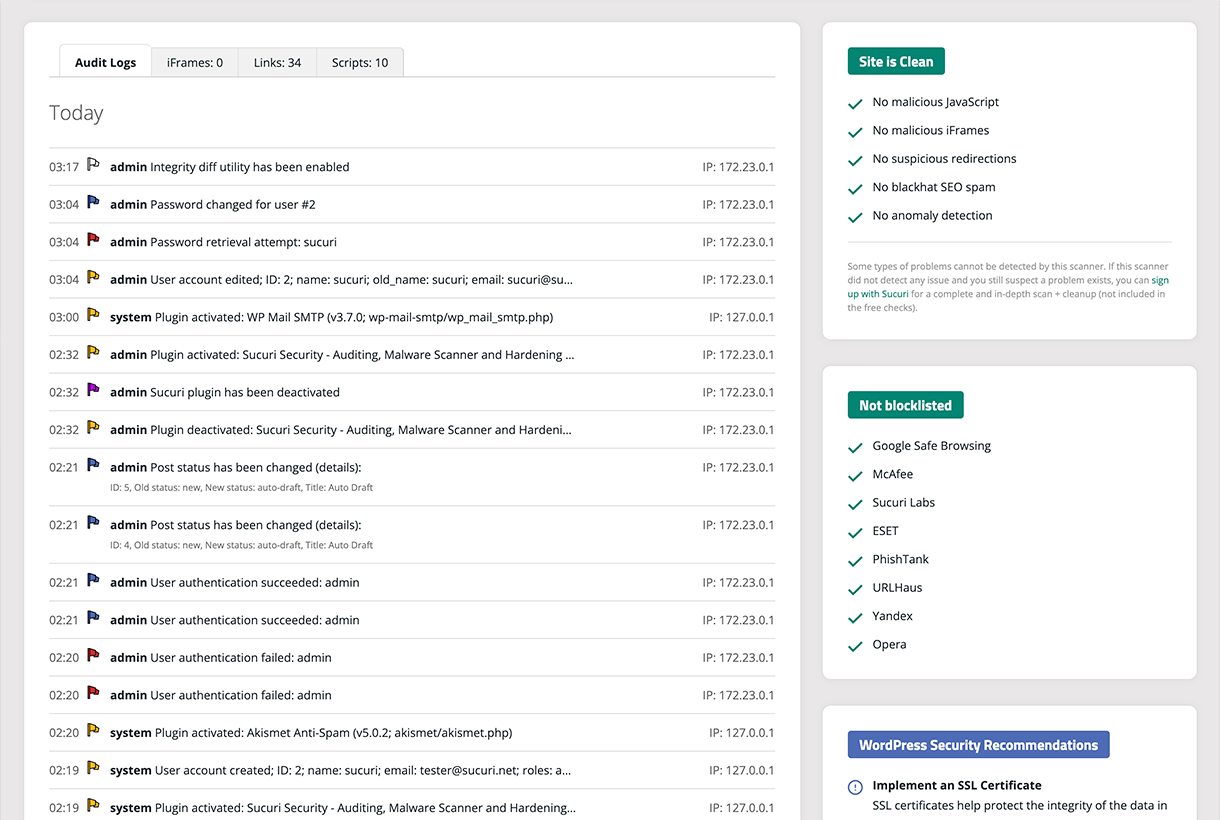
So be sure to check for anomalies in your website logs to detect important information concerning misconfigurations, malfunctions, attack attempts, and other important status information.
11 – Check for input sanitization techniques
Input sanitization is used to check data that’s entered on your website. It then “sanitizes” or removes anything that might be potentially dangerous.
One excellent example of input sanitization can be found for website forms that sanitize inputs to prevent SQL injection attacks.
When employing input sanitization techniques, you’ll need to specify exactly what kind of data you expect from the user:
- Should you accept special characters?
- What is the maximum length or size?
- Should you allow only numbers, or letters as well?
Any visitor to your website could be an attacker. So it’s important to exercise caution — and never trust information inputted into website fields.
So, be sure to accurately filter what is sent to your website or application. This will help enhance your security, prevent SQL injections, and harden your website. And remember: accidental damage can be just as harmful as intentional damage.
12 – Use a web application firewall
Sucuri offers a web application firewall that can help harden your website against attacks. Virtual patching allows the Sucuri team to harden your website against known vulnerabilities until you have time to patch.
Activating the firewall will help enhance the security of your website and server, defend against brute force and bad bots, and protect against DDoS attacks. However, you’ll still need to practice good security habits like passwords and privileges.
Interested in giving the firewall a try? Sign up for our free 30 day firewall trial and get an enterprise-grade WAF for your website!
如有侵权请联系:admin#unsafe.sh
