In the realm of security measures within the digital expanse, we recurrently stumble upon designations, namely, EDR (Endpoint Detection and Response), MDR (Managed Detection and Response), and XDR (Extended Detection and Response). These abbreviations express singular methodologies fashioned to augment online safety provisions across diversified sectors. Let’s unravel these intricate terms and converse on their role in fortifying digital systems.

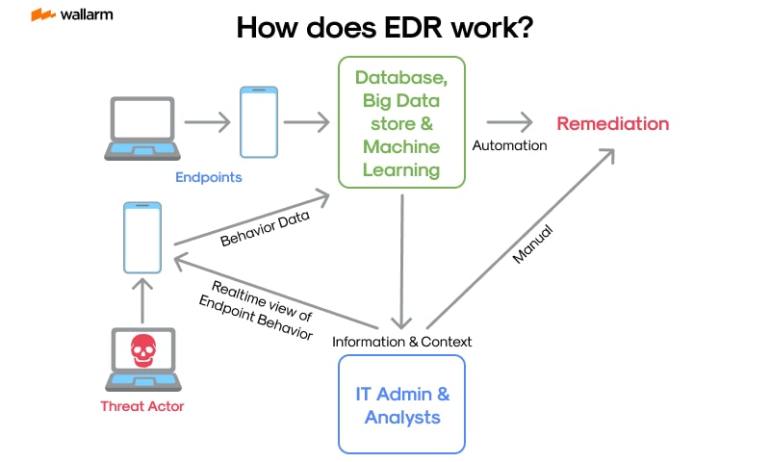
EDR plays a pivotal role in orchestrating protection strategies that detect, scrutinize, and defuse irregular operations on devices connected to networks, typically referred to as ‘endpoints.’ These may encompass network-attached desktops, handy laptops, or petite mobile gadgets, wherein ongoing supervision and data harvesting are vital to foresee looming threats.
<code class="language-python">class EDR:
def __init__(self, endpoints):
self.endpoints = endpoints
def secure(self):
for endpoint in self.endpoints:
endpoint.pull_data()
if endpoint.detect_problem():
endpoint.fix_problem()</code>
The Python code above delineates the operation of EDR – it examines every endpoint, extracts relevant data, identifies possible snags, and implements immediate threat neutralization.

MDR, diverging from EDR, couples specific technology with professional acumen. It arms organizations with the wherewithal to detect anomalies, monitor prospective threats and garner appropriate responses. By alloying EDR with enhanced tech processes, MDR amplifies the virtual defense shield.
<code class="language-python">class MDR:
def __init__(self, edr, tech_safeguard_specialists):
self.edr = edr
self.tech_safeguard_specialists = tech_safeguard_specialists
def monitor_and_counteract(self):
for endpoint in self.edr.endpoints:
endpoint.pull_data()
potential_hazard = endpoint.detect_problem()
if potential_hazard:
for expert in self.tech_safeguard_specialists:
expert.assess_danger(potential_hazard)
expert.respond_to_danger(potential_hazard)</code>
The Python code related to MDR decodes its functionality, demonstrating how it integrates EDR functionalities and cybersecurity experts to manage endpoints, valuate possible dangers, and carry out strategic responses.

XDR typifies a confluence of defense mechanisms which conglomerate control signals, digital safety rules, and critical IT assets into a unified protection envelope. By escalating the proficiencies of EDR and MDR, XDR caters to more data points, thereby expanding the risk perception radar within an enterprise’s IT environment.
<code class="language-python">class XDR:
def __init__(self, mdr, diverse_data_sources):
self.mdr = mdr
self.diverse_data_sources = diverse_data_sources
def monitor_and_counteract(self):
for endpoint in self.mdr.edr.endpoints:
endpoint.pull_data()
potential_threat = endpoint.detect_problem()
if potential_threat:
for specialist in self.mdr.tech_safeguard_specialists:
specialist.assess_danger(potential_threat, self.diverse_data_sources)
specialist.respond_to_danger(potential_threat)</code>
The Python script specified here explicates XDR’s strategy, employing MDR techniques and supplementary data reservoirs to examine endpoints, understand impending threats, and defuse associated perils.
| EDR | MDR | XDR | |
|---|---|---|---|
| Layman Interpretation | Digital Security Foundation | Assisted Protection Services | Full-Spectrum Defense Initiative |
| Prime Focus | Overseeing Endpoints | Detecting & Mitigating Threats | Panoramic Threat Perception and Neutralization |
| Human Interference | Minimal | Considerable | Comprehensive |
| Data Inputs | Primarily Endpoints | Endpoints Supplemented With Additional Data | Diverse Internal Resources |
In summary, EDR, MDR, and XDR offer varying levels of online safeguarding. While EDR concentrates on endpoint defense, MDR necessitates human intervention, and XDR exploits a wide-ranging array of data sources for an exhaustive perspective of possible risks. It’s imperative for businesses to grasp these nuances, especially if they’re contemplating the incorporation of EDR, MDR, or XDR solutions into their networks.
`
`
Navigating the Digital Safety Labyrinth: From EDR to MDR, Culminating at XDR
Major strides have been made in the world of cyber defense, prominently marked by key technologic stepping stones, namely Endpoint Detection and Response (EDR), Managed Detection and Response (MDR), and the recently announced Extended Detection and Response (XDR). Each subsequent stage of development outlines continuous enhancements within the realm of cybersecurity, with every fresh iteration making an endeavor to exceed its predecessor.
Dissecting EDR: Unpacking Endpoint Detection and Response
In the advent of virtual safeguard strategies, huddling around network bastions was the preferred route. However, with steadily amassing digital breaches, these basic safeguards proved to be mostly inadequate, clearing the path for the EDR’s integration.
EDR primarily focused on tracking and logging actions at endpoints and across networks, collecting essential data for subsequent processing, validation, and notification generation.
<code class="language-python">class EDR:
def __init__(self, endpoint, network_events):
self.endpoint = endpoint
self.network_events = network_events
def supervise(self):
# Python code for observing endpoint and network activities
pass
def collate(self):
# Python code for secure data consolidation and retention
pass</code>
Nevertheless, the successful usage of EDR demanded significant analytical prowess for reliable data processing.
The Leap to MDR: Deciphering Managed Detection and Response
MDR was developed to rectify the inadequacies associated with EDR. Contrasting the technically vigorous EDR, MDR introduced elements of threat intelligence, proactive threat mitigation, security administration, incident investigation, and reactive measures, all wrapped in a service-oriented model.
<code class="language-python">class MDR(EDR):
def __init__(self, endpoint, network_events, threat_intelligence, threat_hunting,
security_monitoring, incident_analysis, incident_response):
super().__init__(endpoint, network_events)
self.threat_intelligence = threat_intelligence
self.threat_hunting = threat_hunting
self.security_monitoring = security_monitoring
self.incident_analysis = incident_analysis
self.incident_response = incident_response</code>
MDR addressed EDR’s challenges by providing bespoke resolutions to security breaches. However, the restricted diversity of data sources remained a significant drawback.
Scaling XDR Heights: Unmasking Extended Detection and Response
XDR embarked to overcome the constraints posed by both EDR and MDR. The core of XDR lies in its broad spectrum of security procedures, empowering it to streamline various safety mechanisms into a holistic, incorporated hub, specifically engineered for identifying and handling security infringements.
<code class="language-python">class XDR(MDR):
def __init__(self, endpoint, network_events, threat_intelligence, threat_hunting,
security_monitoring, incident_analysis, incident_response,
integrated_security_products):
super().__init__(endpoint, network_events, threat_intelligence,
threat_hunting, security_monitoring, incident_analysis,
incident_response)
self.integrated_security_products = integrated_security_products</code>
In regard to future digital shielding solutions, XDR leads the race by adopting a potent approach for threat detection and management. Going beyond the limits of its forerunners, XDR has demonstrated its adaptability and tenacity as a tool for online protection.
In a Synoptic View:
| EDR | MDR | XDR | |
|---|---|---|---|
| Key Features | Tracking and Logging of Endpoint and Network Events | Proactive Threat Surveillance, Security Regulation, Incident Forensics, Counteractive Methods | Convergence of Diverse Security Protocols |
| Approach | Technically Dense Paradigm | Service-Centric Model | Comprehensive Blueprint |
| Drawbacks | Need for Advanced Analysis Expertise | Scant Variety of Data Sources | Ongoing Readjustments Necessary |
Tracing the course from EDR to MDR, and ultimately landing at XDR, one can appreciate the tangible advancements in protective tech inventions. Every subsequent generation learns from the past, aiming to outperform it, thereby reinforcing the defense barriers. As the complexity of virtual threats heightens, our preventive mechanisms must keep pace, with XDR signifying the zenith of this sequence to date.
Decoding EDR: Strengths and Weaknesses
Endpoint Detection and Response, symbolically referred to as the keystone of modern security methodologies, emerged as a key player in the digital safeguarding arena capable of fulfilling continuous scrutinizing and intervening obligations against subtle threats. To optimally exploit EDR, one must fathom its boons and plausible shortcomings.
Strengths of EDR:
- Persistent Surveillance and Evaluation: EDR platforms persistently extract data from network endpoints, thereby streamlining the process of detecting potential hazards. Swift and realtime interpretation of threatening patterns and their behavioral inclinations assists in swiftly recognizing abnormalities hinting towards probable security encroachments.
<code class="language-python">class EDR:
def __init__(self):
self.persistent_surveillance = True
self.evaluation = True</code>
- Segregation Capabilities: Intriguing features of EDR allows it to segregate contaminated endpoints, thus halting any further contagion of threats. Additional approaches comprise process annihilation, file obliteration, or modification of registry values to disarm threats.
<code class="language-python">class EDR:
def handle_incident(self, menace):
self.segregate_endpoint(menace)
self.control_menace(menace)</code>
- All-Encompassing Forensic Repository: EDR mechanisms deliver all-inclusive forensic logs on threats, chronicling the birthplace, infected systems, and the conduct of the threat. Such data is paramount for comprehending the threat and averting its reappearance.
<code class="language-python">class EDR:
def forensic_report(self, menace):
return {
'genesis': menace.genesis,
'infected_systems': menace.infected_systems,
'actions': menace.actions,
}</code>
- Harmony with Other Protective Instruments: EDR holds the capacity to blend with other protective mechanisms like Security Information and Event Management (SIEM), supercharging their proficiencies resulting in a fortified security fabric.
<code class="language-python">class EDR:
def sync_with(self, alternate_instrument):
self.boosted_proficiencies = True</code>
Weaknesses of EDR:
-
Influx of Alerts: EDR mechanisms might trigger an overwhelming array of notifications, a substantial portion of which could be baseless alerts. This could pave the way to ‘notification weariness’, where critical alerts are sidestepped owing to a deluge of irrelevant alerts.
-
Dependence on Skilful Analysts: EDR entails competent individuals to meticulously comb through accumulated data and react to menaces, a prerequisite that might distress organizations lacking a proficient security squad.
-
Restricted Insight Beyond the Endpoint: EDR primarily zeroes in on endpoint security, marginally limiting its ability to pinpoint threats emanating from or influencing other network echelons.
-
Intricacy: The deployment and management of EDR pose a formidable challenge. It mandates a profound understanding of the entity’s IT backdrop and security essentials.
In summary, although EDR extends powerful counterattack mechanisms against security infringements, it is not without its share of hitches, such as reliance on qualified specialists and the potential for alert saturation. Despite offering an in-depth view into endpoint security, its vision might be limited in other network partitions. Nonetheless, its place in contemporary security frameworks is critical and its worth cannot be downplayed.
Comparison Table:
| Strengths of EDR | Weaknesses of EDR |
|---|---|
| Persistent Surveillance and Evaluation | Influx of Alerts |
| Segregation Capabilities | Dependence on Skilful Analysts |
| All-Encompassing Forensic Repository | Restricted Insight Beyond the Endpoint |
| Harmony with Other Protective Instruments | Intricacy |
Exploring MDR: The Pros and Cons
Managed Detection and Response (MDR) carves a niche for itself in the realm of cybersecurity, melding processes like threat detection, analysis, and neutralization into a seamless web of protection. Going a step beyond conventional Endpoint Detection and Response (EDR) systems, MDR nonetheless has its own handicaps. Let’s decode MDR laying bare its strength and weaknesses.
MDR: The Strengths
- Superior Threat Identification: MDR platforms employ a trifecta of machine learning, behavior identification, and threat information to find threats that could slip past traditional defenses. This includes newly discovered vulnerabilities, continuous threats, or internal risks.
<code class="language-python">class MDR:
def superior_threat_identification(self):
# Implementation of machine learning, behavior identification, and threat
information
# for identifying superior threats
pass</code>
-
Never-ending Surveillance: MDR services promise an all-time watchful eye on your network and endpoints. This relentless vigil assures immediate detection of any threats, containing possible harm.
-
Swift Countermeasures: Once a threat breaches the defense, MDR swiftly moves into action to confine and eradicate it. The responses could range from isolation of systems, blocking suspicious IP addresses, or engaging with the threat to foil their plans.
-
Assistance in Compliance: MDR facilities ease the burden of meeting compliance standards by providing detailed documentation and proofs of security implementations.
-
Specialized Knowledge: MDR providers come equipped with a group of cybersecurity specialists who offer insights and directions, enabling organizations to heighten their security foundation.
MDR: The Weaknesses
-
Expense: The financial aspect of using MDR services could be formidable, especially for small to medium-sized enterprises. The cost comprises the MDR service as well as any essential enhancements to hardware or software.
-
Dependence on Service Provider: Employing MDR means you’re placing your security in a third party’s custody. Should the provider face operational challenges or interruptions, your security is put at risk.
-
Restricted Customizability: MDR services are usually intended to function with a certain group of technologies. If your organization deploys different tools, the MDR service might not be fully functional.
-
Unintentional Alarms: Despite being designed to minimize false positives, MDR services might accidentally trigger them, leading to unnecessary alarms and resource drainage.
-
Risk of Overdependence: Relying heavily on MDR to maintain your security might lead to the neglect of integral security elements.
In summing up, MDR is undoubtedly a sound security approach that adeptly detects and addresses advanced threats. But one must weigh its limitations like cost, dependence on the provider, and the risk of overdependence before opting for it. As with any security tool, meticulously considering your organization’s needs and resources is crucial before making a choice.
Cementing Cyber Defense Framework with Breakthrough Instrument XDR
Our digital protective barrier is gaining renewed fortification, spurred by the introduction of a pioneering security solution: Extended Detection and Response (XDR). This groundbreaking technology seamlessly integrates numerous defense layers, creating a unified platform for threat spotting and mitigation. It vigilantly monitors prospective vulnerabilities across operational spheres, endowing IT security professionals with a unique skillset that enables them to locate, examine, and eliminate cyber risks.
The advent of XDR represents a significant step-up from traditional security constructs like Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR). XDR capitalizes on the strength of these proven models by extending their effectiveness through a meticulous examination of network activities, tracking user behavior, and enhancing safety measures for cloud-stored data. This approach enables XDR to offer a holistic and flawless view of an organization’s IT security landscape.
To understand how XDR operates, let’s explore this analogy via code snippet:
<code class="language-python">class XDR:
def __init__(self, EDR, MDR, network_traffic_inspection, user_activity_monitoring,
cloud_protection):
self.EDR = EDR
self.MDR = MDR
self.network_traffic_inspection = network_traffic_inspection
self.user_activity_monitoring = user_activity_monitoring
self.cloud_protection = cloud_protection
def identify_and_mitigate_threats(self):
# Gather data from diverse sources
collected_data = self.EDR.data + self.MDR.data + self.network_traffic_inspection
.data + self.user_activity_monitoring.data + self.cloud_protection.data
# Analyze the gathered data to identify potential threats
possible_dangers = self.evaluate_data(collected_data)
return possible_dangers
def evaluate_data(self, collected_data):
# Implement risk detection process here
pass</code>
The provided code demystifies the principle of XDR’ collecting data from varied sources to uncover possible security incidents. Of course, real world deployment demands careful blueprinting that involves complex computational models and predictive analysis.
Running a parallel evaluation of EDR, MDR, and XDR:
| EDR | MDR | XDR | |
|---|---|---|---|
| Coverage | Limited to Endpoint devices | Endpoint devices plus human wisdom | Endpoint devices, network evaluation, user tracking, cloud data vigilance |
| Threat detection | Restricted to observed threats | Discovers visible and hidden threats | Encompasses all threat types |
| Response type | Primarily automated | Fuses manual and automated responses | Entirely automated |
| Integration level | Circumscribed | Narrow | Broad |
Opting for XDR over EDR and MDR proves to be a prudent decision as illustrated in this parallel, given it offers an inclusive and harmonized security mechanism.
Nonetheless, integrating XDR into an existing system isn’t without complications. It necessitates a significant allocation of resources, including manpower, time, and technical expertise. Therefore, organizations need to equip themselves adequately to harness the full potential of XDR.
In conclusion, XDR charts a forward path in security strategies. It amalgamates myriad security elements into one strong, inclusive stage, allowing companies to navigate to a comprehensive understanding of their security challenges. XDR equips businesses to detect, decode, and manage security threats in a savvy, timely manner. Nevertheless, it’s pertinent for organizations to thoroughly examine their specific requirements and competencies before transitioning to XDR.Assessing which type of cybersecurity strategy to implement can seem intimidating. The options might include Endpoint Detection and Response (EDR), Managed Detection and Response (MDR), or Extended Detection and Response (XDR). However, the key lies in understanding the benefits and downsides each strategy brings to the table and how they align with your business environment. Let’s break this down into a few key considerations:
-
Delineating your Defensive Needs
Embark on this journey by enriching your understanding of your company’s distinctive security needs. This encompasses inspecting your current security measures, pinpointing potential loopholes, and setting your risk tolerance boundaries.
If you find that your company doesn’t have the necessary internal skillsets to manage its own security, MDR might be a fitting solution – it’s a turnkey offering managed by experts who are equipped to fulfill your security needs. Conversely, if your operation maintains a robust security team and has the desire to ramp up its threat-spotting capability, EDR could be what you’re looking for.
-
Identifying Funding Boundaries
The depth of your coffers plays an influential part in this decision. EDR tools tend to be more budget-friendly when compared to MDR and XDR, but they require a robust team internally for proper management. On the flip side, MDR comes with a heftier bill but supplies a consolidated defensive solution. XDR solutions, situated at the priciest end of the spectrum, provide the most comprehensive protection.
-
Integration with Pre-existing Systems
Gauge how easily an EDR, MDR, or XDR solution integrates with your current setup. Crafted to marry multiple security tools cohesively, XDR provides a unified view of your security landscape. However, labouring EDR and MDR solutions into your current systems might demand additional efforts.
-
Shaping Business Growth Trajectories
The growth curve of your business leads to a parallel increase in your security demands. Therefore, it’s crucial to select a security solution that can keep pace with your business growth. XDR solutions, with their ability to readily incorporate novel security technologies, may outperform EDR and MDR in terms of scalability.
-
Staying Aligned with Regulatory Mandates
Adhering to compliance protocols or sector-specific regulations assigned to your industry could lean the balance in the favour of some security solutions over others. Certain rules might demand specific monitoring and reactive capabilities, which could cast MDR or XDR systems in a more favourable light.
-
Confidence in Provider
A further consideration lies in the reliability factor of your EDR, MDR, or XDR provider and the quality of their support services. Aim for partners already established in the cybersecurity industry, known for their supportive and reliable track record.
In conclusion, choosing between EDR, MDR, and XDR demands a deep dive into your organization’s exact security needs, available budget, how well the solution integrates with your current systems, predicted business expansion, adherence to any industry-specific regulations, and the trustworthiness of your chosen provider. A plan that strikes a balance across all these considerations can help you find a security approach that’s tailor-made for your organization’s specific needs.Observing the forthcoming landscape of cyber protection, the intensity of attention towards Extended Detection and Response (XDR) is visibly mounting. This intensity is grounded in XDR’s exhaustive methodology for identifying and neutralizing threats, merging various safeguard measures into a harmonized entity. How will this escalating XDR fervor affect Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR)? Let’s explore this predicament.
XDR’s Advent
Various causes inspire the allure of XDR. Primarily, by consolidating data extracted from an array of sources, it crafts a comprehensive panorama of an enterprise’s safeguard position, outlining a full representation of impending security threats. This methodology is a considerable advancement from EDR and MDR, generally focused on individual aspects in the cybersecurity landscape.
Furthermore, XDR utilizes superior analytics and processing power to pinpoint and disarm threats more efficiently, detecting intricate attacks often overlooked by conventional security benchmarks.
Additionally, by uniting several applications onto a single platform, XDR simplifies security management, reducing intricate supervisory tasks, freeing resources for other endeavors.
Implications for EDR and MDR
The broader scope of XDR doesn’t herald the downfall for EDR and MDR. Instead, it portends a metamorphosis of these technologies. It’s likely that EDR and MDR will retain their relevance in the protection sphere, although their functionalities might be incorporated within the wider XDR frameworks.
For instance, EDR’s emphasis on protecting the end-user remains pertinent, even though it may operate within an expansive XDR platform. Likewise, the managed services provided by MDR may persist in delivering valuable expertise and resources, specifically for businesses deficient in in-house security acumen. However, these services could be integrated into XDR frameworks to deliver an all-encompassing protection solution.
Picking the Optimal Option
Just because XDR is gaining momentum doesn’t make it the automatic pick for every business. EDR, MDR, or XDR? This choice depends on parameters like the company’s size, safeguard necessities, and available assets.
For less sizable companies with limited resources, MDR might best fulfill their needs, considering its managed security services that don’t require extensive in-house proficiency. Conversely, larger establishments with intricate protection requirements may benefit from the inclusive safeguard provided by XDR.
`
`
Peering into the Future
As XDR’s prominence continues to increase, a strategy blending diverse protection technologies is forthcoming. This amalgamation is expected to enable more efficient yet stronger threat identification and neutralizing, promoting simplified security procedures.
However, it’s essential to note that no protection design provides a universal solution. Irrespective of the preference – EDR, MDR, or XDR – maintaining a vigorous safeguard position that involves routine updates, user training, and proactive threat surveillance is vital.
In finishing, the growing prominence of XDR signals a thrilling progression in cyber safeguarding. Although it could reshape the roles of EDR and MDR, it concurrently opens opportunities for more adept and pragmatic security procedures. The essence is discerning the approach that best aligns with a company’s unique needs and assets.
The post EDR vs MDR vs XDR appeared first on Wallarm.
*** This is a Security Bloggers Network syndicated blog from Wallarm authored by Ivan Novikov. Read the original post at: https://lab.wallarm.com/what/edr-vs-mdr-vs-xdr/
如有侵权请联系:admin#unsafe.sh
