8 November 2023
KELA Cyber Intelligence Center
In late August 2023, in a major operation named Operation Duck Hunt, the FBI, along with international partners such as France, Germany, Latvia, Romania, the Netherlands, and the UK, announced they dismantled the QakBot malware infrastructure.
The operation resulted in the deletion of QakBot from over 700,000 compromised computers worldwide, preventing further harm. Additionally, the U.S. Justice Department seized more than $8.6 million in cryptocurrency in illicit profits linked to QakBot’s activities. The QakBot takedown employed an innovative approach, using an uninstaller file to detach compromised computers from the botnet, thereby preventing further malicious payloads.
The botnet has been known to be used by different ransomware gangs, such as Ryuk, ProLock, Egregor, REvil, MegaCortex, Doppelpaymer and Black Basta for their malware delivery. While most of them are no longer active, some continue to operate — such as Black Basta. As seen by KELA, the botnet takedown could have affected their operations but it seems that two months after the dismantling, the group is back in business, possibly with a new initial infection vector. On the other hand, Black Basta may choose to persist in collaborating with threat actors linked to QakBot, given their ability to continue distributing the Knight ransomware (formerly known as Cyclops) successfully in recent months, even after their botnet was dismantled.
In this blog we provide insights into the collaborative efforts of two operations with QakBot and examine the impact of the takedown on their activities.
Black Basta
Black Basta is one of the most prolific ransomware operations with almost 350 organizations claimed as its victims since its appearance in April 2022. The threat actors behind the Black Basta ransomware operation are known for using double extortion tactics: the actors encrypt and steal victims’ data in the compromised system, and extort victims by threatening to publish the data on the ransom blog operated by Black Basta, unless the victim pays the requested ransom.
Since June 2022, Black Basta ransomware was observed to be deployed via QakBot. QakBot disruption appears to affect the group activity: for the whole month of September, following the takedown, the group did not claim new victims on the blog and no new negotiations appeared to be conducted. However, starting mid-October 2023 the gang is back and has claimed around 20 victims.
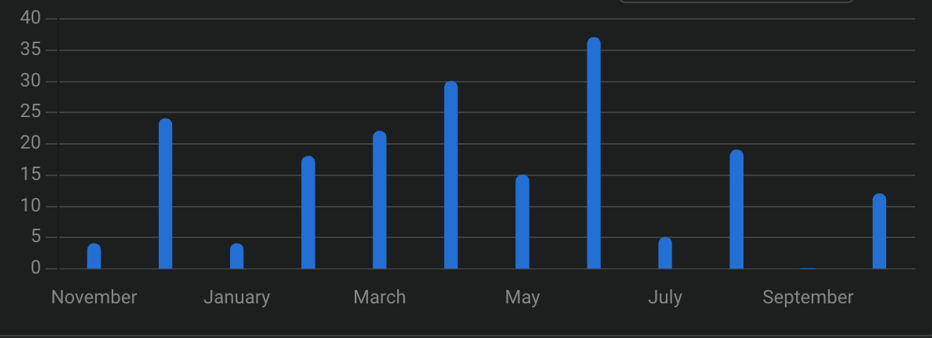
Black Basta victims (publicly claimed or discovered by KELA) over the last year
It’s possible the gang has partnered with other botnet operators to deliver its malware via phishing emails that has been traditionally their preferred method of infection. Alternatively, Black Basta could continue working with threat actors behind QakBot, especially considering they have been successfully distributing Knight (former Cyclops) ransomware in the last months despite the takedown of their botnet.
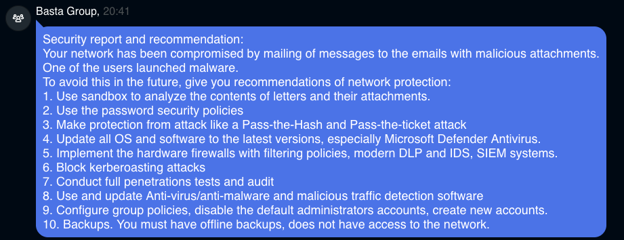
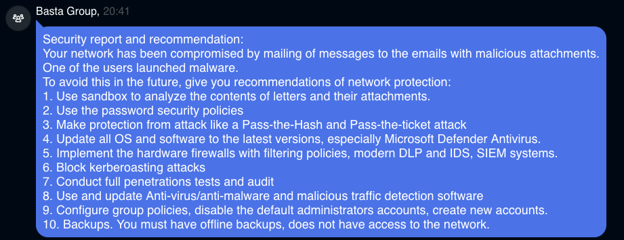
Black Basta disclosing their initial infection vector to one of the victims that paid ransom
Knight (Cyclops)
Since early August 2023, the threat actors behind the Qakbot malware have been distributing the Knight (Cyclops) ransomware and the Remcos backdoor via phishing emails. The campaign began before the infrastructure takedown in the same month, but then continued despite the law enforcement’s efforts. This could suggest that the action may not have affected the Qakbot operators’ spam delivery infrastructure but rather only their command and control (C2) servers. The campaign was attributed to Qakbot based on the metadata found in LNK files used in this campaign. In September, Knight was also seen to be distributed by the threat actors behind RedLine and Vidar malware families.
Knight (formerly known as Cyclops) is a group which appeared on cybercrime forums in May 2023, offering ransomware-as-a-service (RaaS) for affiliates. The operation launched its public blog in June. In August, the gang announced a 2.0 version of its RaaS operation changing the name from Cyclops to Knight. The recent update is their launch of their 3.0 version in late October. The cybercriminals claimed their ransomware is able to compromise Windows, Linux, MacOS and ESXi, and the encryption speed was improved. The operators also added additional features related to negotiations between victims and affiliates. Since June 2023, Cyclops/Knight claimed to have compromised 34 victims, growing its pace in October.
Knight representatives are highly active on cybercrime forums, looking for affiliates and claiming that all negotiations and payment will be handled by them. Interestingly, from May till mid-August 2023 the group has been looking for phishing and spear phishing attack specialists, publishing several announcements about it. Their further cooperation with Qakbot, Redline and Vidar hints that they succeeded in finding such partners.
As this blog has illustrated, the QakBot botnet served as a crucial tool for various ransomware gangs. Despite the setbacks, Black Basta appears to have regrouped, while other actors, such as Knight ransomware operation, continued to collaborate with threat actors behind QakBot. Their ability to thrive in the aftermath of the QakBot takedown highlights the challenges faced by cybersecurity professionals in an evolving landscape of cyber threats.
Get notified about threats targeting your organization in real-time. Try KELA’s Cyber Threat Intelligence Platform for Free.