
2023-11-2 22:24:7 Author: www.sentinelone.com(查看原文) 阅读量:11 收藏
Earlier this week, Apple notified a number of individuals that their iPhones had apparently been targeted by state-sponsored attackers. Around a dozen iPhone users, including journalists and politicians in India’s opposition parties, are said to have received the alerts. Apple began warning its users that they could be being targeted by sophisticated, nation-state hackers in 2021, after the discovery that Pegasus spyware was widely being used by governments and other entities to compromise mobile devices. Since then, individuals in over 150 countries have been notified of potential nation-state hacks against their Apple devices.
Receiving an alert, however, leaves users with little to no indication of how they are being targeted or by whom. The wording of the alert even suggests it might be a mistake, raising questions about how alarmed users should be and what they ought to do. In this post, we explain how threat notifications work, discuss the security threat to mobile devices, and offer guidelines for concerned users.

What Are Apple Threat Notifications?
In the wake of rising incidents of spyware attacks from private sector greyware vendors such as the now-sanctioned NSO, developers of Pegasus, Positive Technologies, Candiru and the Computer Security Initiative Consultancy, Apple began sending alerts to users whenever it discovers activity “consistent with a state-sponsored attack”.
The alerts contain only generic information about such attacks and give no indication of precisely what Apple found, nor who might be behind the attack. Recipients are warned that attackers may be able to remotely access the device’s camera, microphone, data and applications such as messaging software. Somewhat confusingly, Apple’s alert also tells users that this could be a false alarm, but that the recipient should “take this warning seriously”.
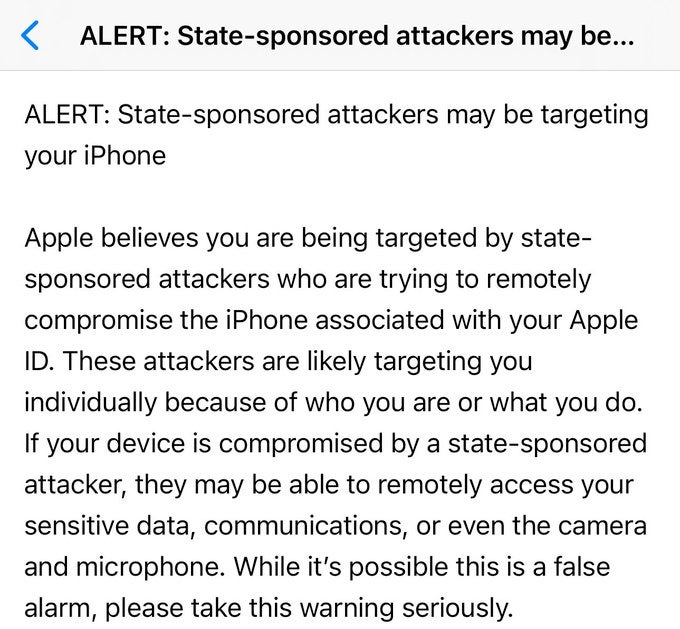
The alerts are sent to the email addresses and phone numbers associated with a targeted Apple ID via email and iMessage notifications. Apple also displays a banner notification on the users AppleID login page.
Who Is Behind the Attacks?
While there is plenty of speculation about who might be behind the activity Apple has warned users about this week, the information provided to users means it is impossible to attribute specific state-sponsored attackers to a batch of threat notifications.
Apple says its alerts are based on “threat intelligence signals” that may be imperfect and incomplete, and the company says it withholds making those details public “as that may help state-sponsored attackers adapt their behavior to evade detection in the future”.
However, there are a number of well-known Private-Sector-Offensive-Actors (PSOAs) that specialize in developing and selling mobile device exploits to governments and other “security” agencies. PSOAs may be contracted by nation-states to help them avoid attribution, or they may provide “software as a service” that nation-state actors deploy in their campaigns.
The most commonly observed PSOA actor in this space is NSO and its Pegasus software, recently used in an iPhone zero-click zero day to compromise the mobile device of a Washington DC-based civil society organization. Following this recent attack, Apple has in recent weeks issued three separate security updates for iOS to patch a number of bugs it says may have been “actively exploited in the wild”.
What Are the Threats to Mobile Devices?
Although mobile malware is most widely associated with spyware for surveillance and data theft, it can and has been used to serve a broader range of sinister capabilities. There are known cases where it has been employed to fabricate evidence of a crime, a disturbing trend that has gained prominence in the digital age. Cybercriminals with malicious intent have deployed malware to plant false data or tamper with existing records, creating a virtual trail of incriminating information against unsuspecting victims.
Such deceptive tactics can be used to frame individuals or organizations for illicit activities, thereby tarnishing their reputation or even leading to legal consequences. One example of an attacker who repeatedly and consistently planted evidence is the ModifiedElephant APT, which we reported on early last year.
What Should You Do If You Receive an Apple Threat Notification?
Threat actors evolve quickly, and as long as they are able to avoid attribution and repercussions of their actions, we can expect their activity to recur. For those who receive a threat notification, or who operate in high-profile political, religious, business, or civil society communities, the following recommendations can help:
- Enable auto updates for your devices, including iPhones, Macs, and Windows PCs.
- Ensure multi-factor authentication is enabled on iCloud accounts, and all email accounts you own. We strongly recommend hardware-based tokens and not text-message (SMS) codes.
- Turn on iOS Lockdown Mode.
- Enable Advanced Data Protection for iCloud.
- Remove all unnecessary apps from your devices, and perform a Safety Check.
- Reboot / Force Restart mobile devices at least once a day.
- Backup your mobile device at least once per week.
- If applicable, avoid iOS jailbreaking. In general, jailbreaking may increase the risk of your device.
- For work devices, request your organization to provide a trusted mobile security solution.
And What About Android Devices?
Although threat notifications are an Apple-only service, users may possess other kinds of mobile and computing devices. Android devices, for example, can be hardened with the following measures:
- Enable automatic updates.
- Never install apps from a third-party app store.
- Understand the risks of rooting a device. Like jailbreaking, this generally introduces more security weaknesses.
- Consider enabling Android Lockdown Mode. Unlike iOS Lockdown Mode, the Android version disables all forms of biometric authentication to prevent non-consensual phone access.
- Enable device encryption.
- If your organization uses Android for Work, consider using a work profile to separate work and leisure activity and requesting a trusted mobile security solution.
- Consider a reputable Android security solution for non-work devices.
Personal computers, whether Windows, Mac or Linux, should also be protected by trusted security software. Note that OS vendor supplied security software is also regularly targeted by threat actors looking for exploitable bugs. Both Windows and macOS have received multiple patches this year alone for vulnerabilities “actively exploited in the wild”.
Conclusion
In a world where state-sponsored attackers are increasingly targeting mobile devices, vigilance is essential. The recent widespread notifications from Apple serve as a stark reminder that no one is immune to such threats. As we’ve discussed, the potential for mobile devices to be weaponized against individuals and organizations is not limited to surveillance; it extends to the disturbing use of malware to fabricate evidence of crimes.
In this rapidly evolving landscape, it’s crucial to take proactive steps to protect your digital life. Enabling automatic updates, implementing multi-factor authentication, and regularly backing up your devices are some fundamental measures.
While different devices have their unique security considerations, the overarching principle remains the same: prioritize your digital security and be prepared for evolving threats. As threat actors continue to adapt and evade attribution, these precautions become our best defense against their relentless activities.
Singularity Mobile
Combat the Rising Tide of Mobile Threats with On-Device, Adaptive, Real-Time Mobile Defense
如有侵权请联系:admin#unsafe.sh