
2023-11-1 23:42:6 Author: securityboulevard.com(查看原文) 阅读量:1 收藏
According to research done by ARMO, 100% of Kubernetes clusters that were tested contained at least one misconfiguration, while 65% had at least one high-severity misconfiguration. 50% of clusters had 14 or more failed security controls. According to Redhat research from 2023, 45% of respondents experienced security incidents or issues related to containers and/or Kubernetes due to misconfigurations.
Misconfigurations can lead to many security issues, including vulnerability to attacks and easy access to sensitive information. Thus, ensuring that your Kubernetes infrastructure is configured properly is crucial for system security.
A key feature of Kubernetes is the configuration of various resources. The choice of how to configure resources (.e.g. Helm, Kustomize, YAML, CRD etc) often depends on the specific use case. The commonality between them all is that they are all susceptible to misconfigurations. Misconfigurations that affect the stability and security of the cluster.
Common Kubernetes security misconfigurations
Before digging into the advantages of side-by-side remediation advice, let’s shed light on some typical Kubernetes security misconfigurations:
1. Excessive privileges: Granting unnecessary permissions to containers or pods can lead to unauthorized access and potentially devastating breaches.
2. Inadequate network policies: Failing to define proper network policies can result in unrestricted communication between pods, paving the way for the lateral movement of attackers.
3. Absence of resource limits: Resource-intensive applications can use up a significant portion of a cluster’s infrastructure, frequently resulting in issues like running out of memory (OOM).
4. Overly permissive RBAC Configurations: A permissive RBAC configuration becomes excessive when it grants users or groups more permissions than necessary for their intended tasks
5. Secret misconfiguration: refers to the improper management or configuration of Kubernetes secrets, which are used to store sensitive information such as API keys, passwords, and certificates. When secrets are misconfigured, it can lead to security risks, potentially exposing sensitive data to unauthorized users or applications. Common misconfigurations include inappropriate access permissions, accidental exposure in pod logs, or insecure storage practices.
The challenge of remediation
Identifying these misconfigurations is the first step towards a more secure Kubernetes environment. However, simply spotting them isn’t enough. Remediation is key, but it can be a complex process, especially for organizations lacking Kubernetes expertise. This is where advanced side-by-side remediation comes to the rescue.
In ARMO Platform we introduced advanced side-by-side remediation to always keep the user in context (this feature is available from Helm version v.1.16.0 onwards). Anyone who has ever used GitHub for code review and maintenance will find the interface inviting and easy to use.
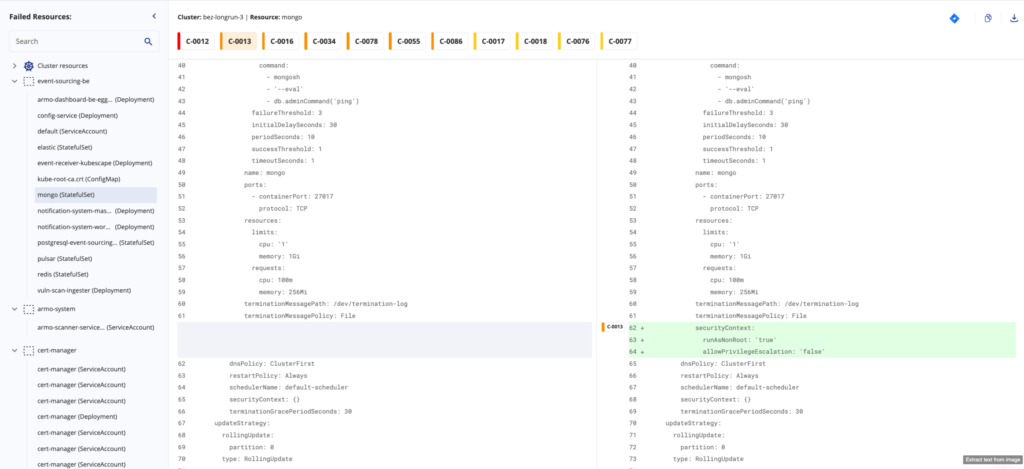
Benefits of advanced side-by-side remediation
1. GitHub style guidance: Side-by-side remediation advice offers you clear, step-by-step guidance on how to remedy misconfigurations. It’s like having an experienced Kubernetes security expert right by your side.
2. Time Savings: Your DevOps teams can efficiently assess remediation advice, leading to quick review cycles. This is particularly important for Agile and CI/CD development workflows.
3. Efficient misconfiguration detection: Developers can spot changes between the original code and the proposed changes quickly. Side-by-side comparison allows for the efficient identification of suggested fixes.
4. Immediate Action: With actionable advice, you can take immediate steps to address misconfigurations, reducing the window of exposure to potential threats.
5. Learning Opportunity: Not everyone in your organization may be well-versed in Kubernetes. Advanced side-by-side remediation doubles as an educational resource, helping your team understand the reasons behind the recommended changes.
6. Consistency: Consistency is crucial in maintaining a secure Kubernetes environment. Advanced side-by-side remediation ensures that best practices are followed consistently across your deployment.
Conclusion
Kubernetes security misconfigurations are a common challenge, but they don’t have to be a daunting one. Advanced side-by-side remediation advice simplifies the process of identifying and resolving these misconfigurations. Thus, enhancing the security of your Kubernetes environment. By following clear, actionable guidance, you can fortify your defenses, reduce risk, and maintain a resilient Kubernetes ecosystem.
As you navigate the dynamic world of container orchestration, remember that security is an ongoing process. Continuously monitor your environment, stay informed about best practices, and leverage the power of advanced side-by-side remediation to keep your Kubernetes ecosystem secure and resilient.
To turbo-charge your misconfiguration analysis and remediation, try ARMO Platform today. It’s free!

Kubernetes security platform
{powered by Kubescape}. Free forever.
Experience effective, end-to-end, from dev to production, Kubernetes protection:
Manage Kubernetes role-based-access control (RBAC) visually
Eliminate misconfigurations and vulnerabilities from your CICD pipeline – from YAML to cluster
Full Kubernetes security compliance in a single dashboard
The post The new standard of Kubernetes misconfiguration remediation appeared first on ARMO.
*** This is a Security Bloggers Network syndicated blog from ARMO authored by Yossi Ben Naim. Read the original post at: https://www.armosec.io/blog/kubernetes-misconfiguration-remediation-new-standard/
如有侵权请联系:admin#unsafe.sh
