
2023-10-31 14:47:47 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Virtual programs are now an essential component of our daily lives. Web applications are now essential tools for both individuals and organizations. From online shopping to social media and banking, we depend on internet apps for convenience and accessibility. However, the very capabilities that make internet packages so critical additionally make them at risk of an extensive range of safety threats.
In this blog, we will explore the elements that render net packages maximum at risk of cyber attacks, exploring the key vulnerabilities and the ways to guard against them.
Vulnerabilities in Web Applications
Several vulnerabilities that can be exploited by hackers have also been made public by the growing reliance on web apps. These flaws have the potential to jeopardize entire systems along with sensitive data. For a safer online experience, everyone should be aware of these common vulnerabilities in web applications. We’ll look at a few of the most common vulnerabilities in web applications and the possible threats they present in the section:
Injection Attacks:
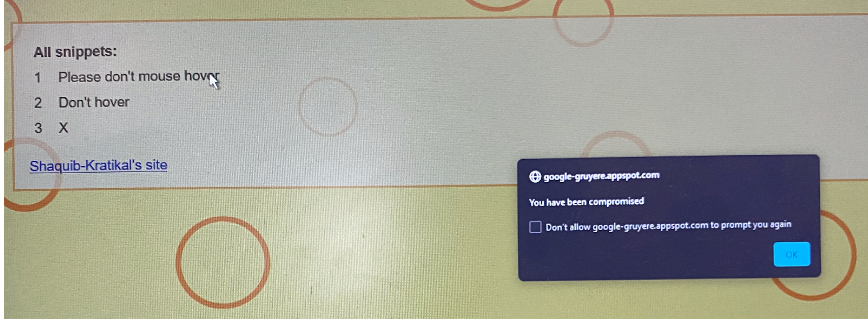
One of the maximum common-place vulnerabilities in net applications is injection attacks. These attacks arise whilst an attacker inputs malicious code into an input discipline, manipulating the utility’s conduct. Cross-site scripting (XSS) and SQL Injection are some of the most used attack techniques of injection attack.
Attackers use SQL injection to access and steal sensitive data from databases, including Personal Identifiable Information. To mitigate this attack, developers need to use parameterized queries and input validation to make sure that user input can not get as code to the server. To prevent XSS attacks, proper output encoding and entry validation are essential.
Authentication and Session Management
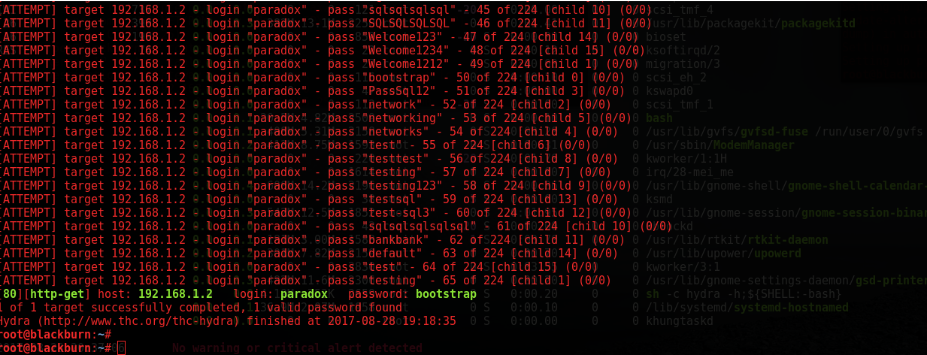
Weak authentication and session control are prime targets for attackers looking for unauthorized rights of entry to web applications. Inadequate password rules, terrible session management, and predictable session identifiers can open the door to breaches.
To beautify protection, builders must enforce strong password regulations, employ multi-component authentication (MFA), and regularly refresh session identifiers. Furthermore, securely storing passwords and the use of sturdy cryptographic techniques, inclusive of hashed passwords, is critical in safeguarding personal facts.
Cross-Site Request Forgery (CSRF):
Cross-website online request Forgery is an assault that hints the user into appearing unintentional movements on a distinctive web page. This can lead to actions being taken on behalf of the consumer without their consent. For instance, a CSRF attack should exchange the person’s email cope with or password without their expertise.
For example in the image below you can see how the Crss tie request forgery payload looks like
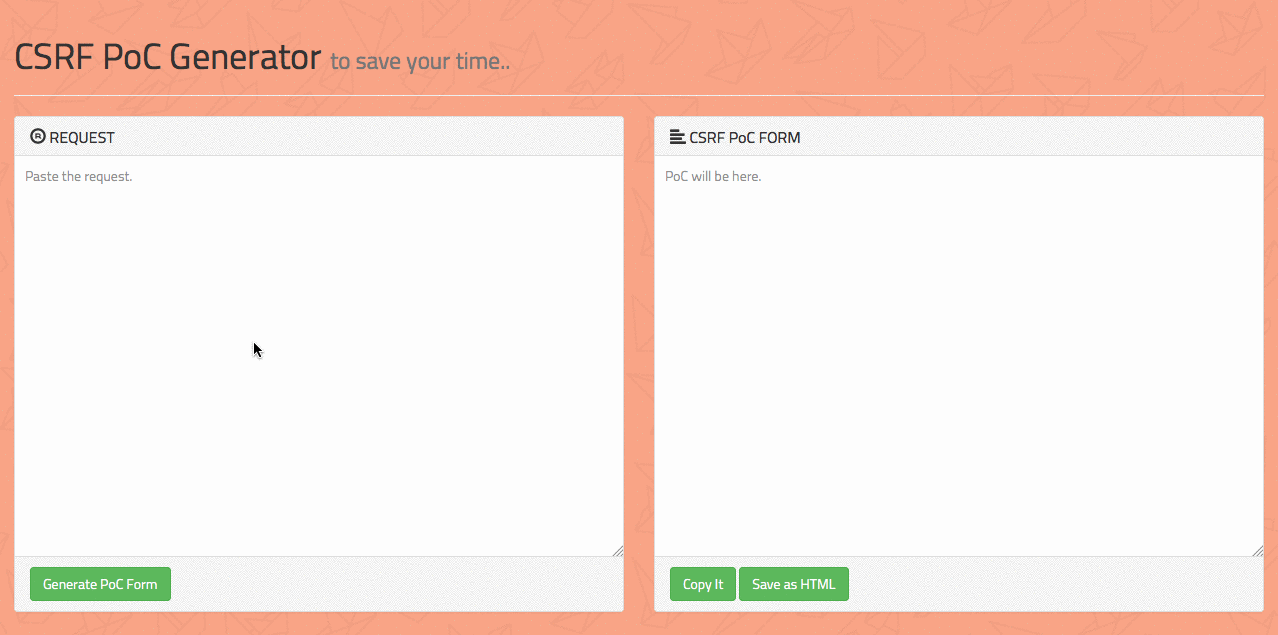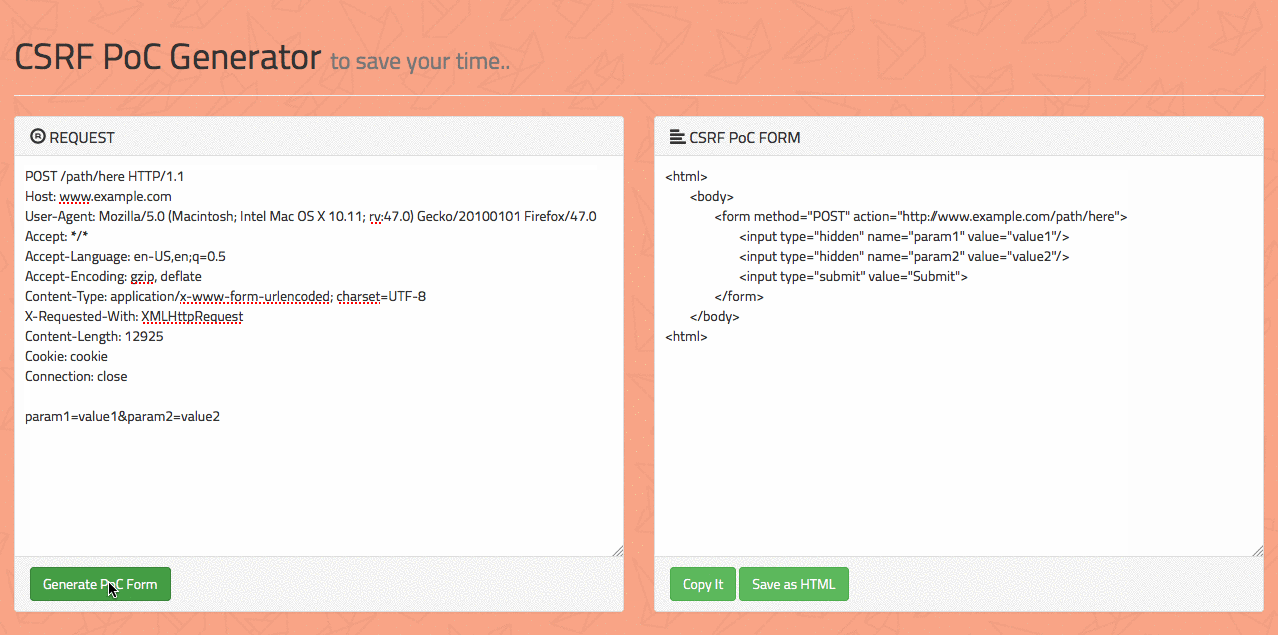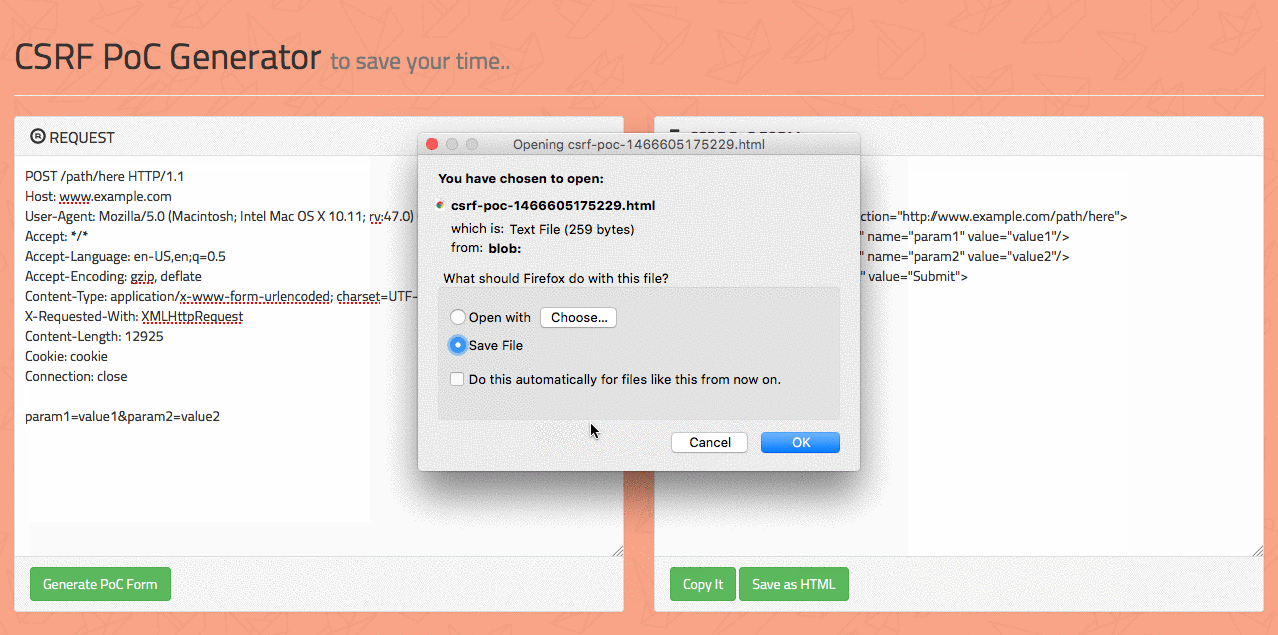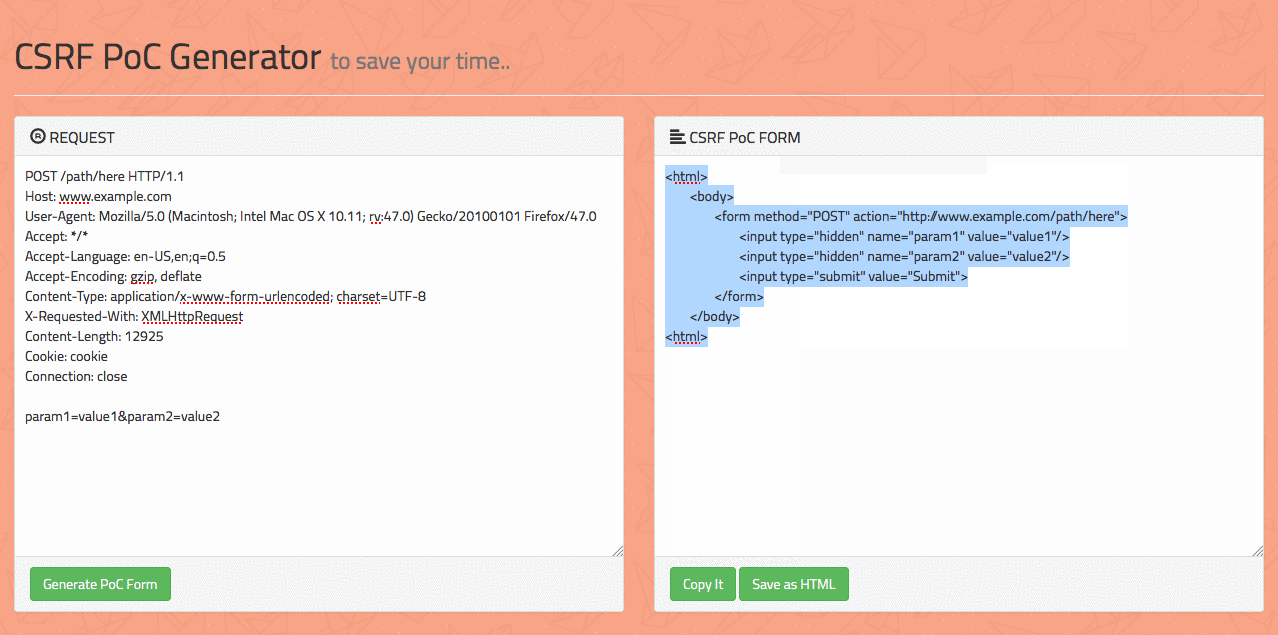
To mitigate this vulnerability, builders need to implement anti-CSRF tokens, which are precise tokens embedded in internet forms that confirm the authenticity of the request. Additionally, builders should keep away from executing vital actions through GET requests, as GET requests are greater liable to CSRF attacks.
Privilege Escalation Flaw
Privilege escalation enables attackers to change their user role through request interception and ID manipulation in a proxy tool. Such an attack is also called insecure Direct object reference and in short IDOR.
Let’s take a simple example, suppose an attacker checked his profile and found there’s a request with userid=9878 and isadmin=no what the attacker did is just change the value isadmin=no to Yes or change the value of his/her userid number the attacker can switch to another profile or can escalate his value to an admin role.
Book a Free Consultation with our Cyber Security Experts

How to mitigate IDOR Security Flaw?
Mitigating Insecure Direct Object Reference (IDOR) vulnerabilities in an internet utility is critical to guarding personal records and preserving the safety of your application. IDOR takes place while an attacker can control input to access gadgets or facts they may be not authorized to get the right of entry to. Here are steps to assist in mitigating IDOR bugs:
Implement Proper Access Control
Ensure that your software enforces get right of entry to manipulate guidelines for all resources. This consists of checking consumer permissions for each request to sensitive facts or functions.
Use Authentication and Authorization
Implement a robust consumer authentication and authorization mechanism. Only authenticated and licensed customers must be capable of getting the rights of entry to sensitive sources.
Session Management
Secure your consultation management to save you from consultation fixation and session hijacking attacks. Use secure, random consultation IDs and periodically re-authenticate users.
Conclusion
Web applications are the backbone of our digital interactions, so it’s crucial to understand and address their vulnerabilities. These applications have changed the way we shop, communicate, and work, offering unparalleled convenience. However, this convenience comes at a cost – a heightened vulnerability to cyber threats. The vulnerabilities we’ve discussed, from injection attacks to privilege escalation, highlight the need for proactive security measures.
Developers, organizations, and users must work collectively to protect web applications and safeguard sensitive data. Staying informed and applying best practices ensures secure navigation in the digital landscape, upholding the longevity and reliability of web applications amidst evolving cyber threats. We aimed to clarify what motivates unauthorized access and highlight the most risky web application bugs.
Kratikal a CERT-In empanelled auditor plays a crucial role in enhancing web application security. With vast VAPT experience, Kratikal audits decentralized software and smart contracts to find and fix potential vulnerabilities.
Kratikal’s proactive cybersecurity approach and its expertise in web application security position it as a significant player in ensuring the security of web applications. Dedication to staying ahead in the cybersecurity field positions us as the perfect choice for organizations seeking to protect their web application infrastructure. With Kratikal, businesses can confidently embrace the full potential of their web applications, ensuring user confidentiality and protecting valuable digital assets.
The post What makes Web Applications Vulnerable? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/what-makes-web-applications-most-vulnerable/
如有侵权请联系:admin#unsafe.sh
