
2023-10-27 21:0:0 Author: www.tenable.com(查看原文) 阅读量:13 收藏

Check out how organizations’ enthusiasm over generative AI is fueling artificial intelligence adoption for cybersecurity. Plus, how CISA plans to revamp the U.S. government’s cyber incident response plan. In addition, learn about a new set of best practices for protecting cloud backups. Also, why boards of directors feel more comfortable with cybersecurity. And much more!
Dive into six things that are top of mind for the week ending October 27.
1 - Survey: GenAI to boost overall AI use for cybersecurity
Business and technology leaders’ fascination with the potential benefits of generative AI tools is accelerating the adoption of artificial intelligence in general for cybersecurity.
That’s one key finding of the “State of Cybersecurity 2024” report from the Computing Technology Industry Association (CompTIA), which polled 511 U.S. business and IT pros involved in cybersecurity.
Specifically, 36% of respondents said they haven’t yet used AI and machine learning for cybersecurity, but that they’re currently “seriously exploring” generative AI tools. Fifty-six percent are already working with AI and ML.
When respondents were asked about potential uses of AI in cybersecurity in the next two to three years, networking traffic monitoring / malware detection ranked first, followed by analysis of user behavior patterns, and automated responses to cyber incidents.
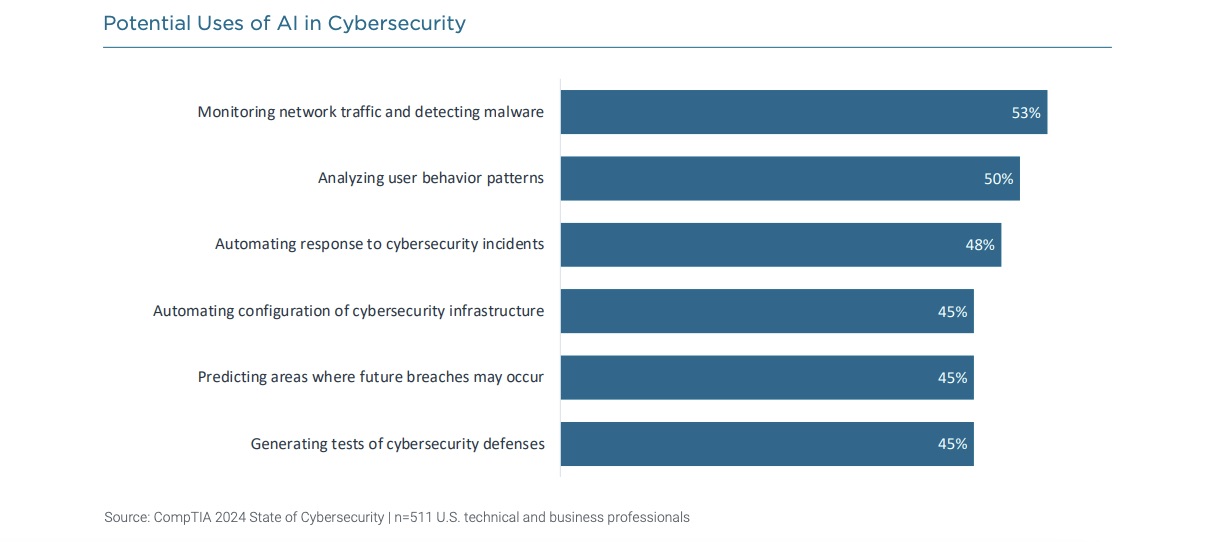 Other findings from the study include:
Other findings from the study include:
- Organizations’ greatest cybersecurity challenge is the skills gap, which they’re addressing partly by hiring more candidates without college degrees but with solid cybersecurity knowledge.
- Respondents’ top concerns are the growing number of hackers; data privacy; generative AI use by cybercriminals; and the scale and variety of attacks.
- The top risk analysis areas were IT procurement / shadow IT; cloud computing use; and classification / prioritization of data.
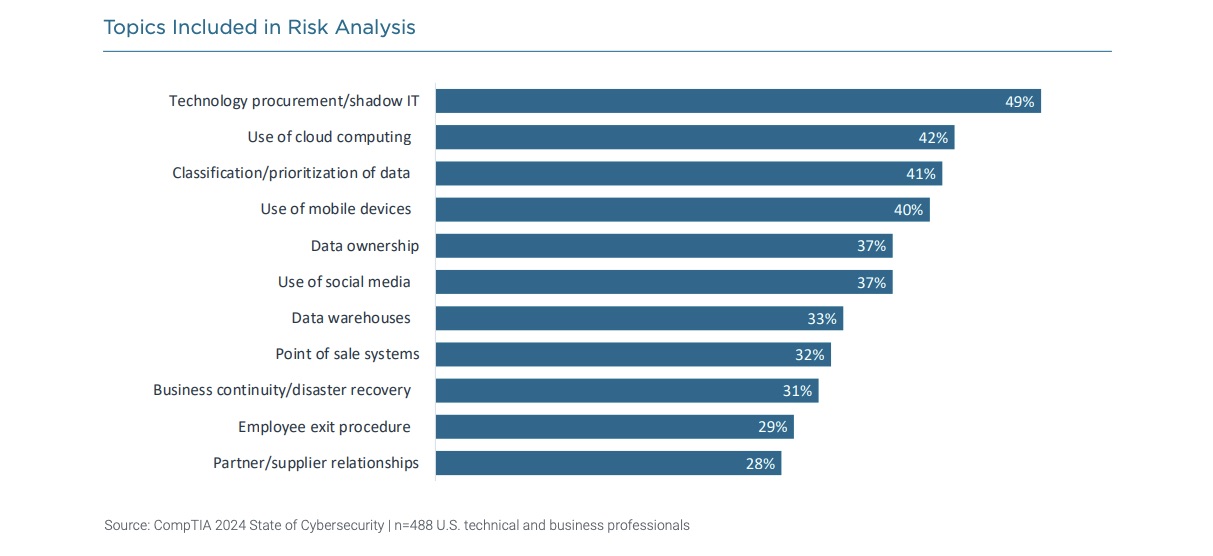 To get more details, check out:
To get more details, check out:
- The “State of Cybersecurity 2024” report’s home page
- The report’s announcement “New CompTIA report finds steady progress on the cybersecurity front, but balancing act gets tougher for organizations”
- The full report
For more information about the impact of AI on cybersecurity:
- “Evaluate the risks and benefits of AI in cybersecurity” (TechTarget)
- “The role for AI in cybersecurity” (Cybersecurity Dive)
- “AI Is About To Take Cybersecurity By Storm” (Tenable)
- “Assessing the pros and cons of AI for cybersecurity” (Security Magazine)
- “New Generative AI Tools Aim to Improve Security” (Dark Reading)
VIDEO
Tenable CEO Amit Yoran discusses AI and preventive security on CNBC
2 - CISA to update National Cyber Incident Response Plan
Interested in incident response tactics and strategies? If so, you can now track how an incident response plan with a massive scope gets a top-to-bottom makeover.
We’re talking about the U.S. National Cyber Incident Response Plan (NCIRP), which the U.S. government adopted back in 2016. Obviously, much has changed in cybersecurity since then.
That’s why the U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced this week that it’s time to update the NCIRP. In a two-page factsheet, CISA has outlined how it plans to modernize the way the U.S. government coordinates its responses to major cyber incidents.

Here are some details about the new NCIRP, which is expected to be finalized by the end of 2024:
- Its core goal is to provide a national response framework that’s coherent, repeatable, modern, agile and flexible.
- The update process won’t be limited to the U.S. federal government. State and local governments, the private sector, international partners and others will also be involved.
- The plan will reflect the contributions of all stakeholders, and maximize their expertise, while incorporating lessons learned and anticipating changes in the cyber landscape.
- In broad strokes, this is the project’s timetable:
- It’s now at the initial planning stage, in which CISA is engaging with federal agencies and will soon reach out to non-federal stakeholders.
- Once the formal planning team is created, the process will move to the “planning and development” phase in December.
- The planning team will publish a draft of the new NCIRP in 2024 and open it to public comment, before finalizing it before the end of the year.
To get more details, you can write to [email protected] and check out:
- The current National Cyber Incident Response Plan (PDF) and FAQ
- The NCIRP 2024 fact sheet
- The NCIRP home page
- CISA’s announcement about the plan to update the NCIRP
3 - Board directors get more cyber confident
Board directors feel less burdened by their cybersecurity oversight duties, as they take proactive steps to boost their security knowledge and their communication with cyber leaders.
That’s according to PwC’s “2023 Annual Corporate Directors Survey,” which polled more than 600 directors from publicly traded companies.
Specifically, 49% of directors surveyed see cybersecurity as a significant oversight challenge, down from 59% last year.

Actions taken by boards in the past year related to cybersecurity include:
- Devoted more time to cybersecurity during board meetings
- Sought to broaden their cybersecurity knowledge and skills
- Brought in external experts to assist the board with cybersecurity oversight
- Increased the number of meetings with their company’s CISO
However, the survey also found that there is room for improvement, especially in light of stricter cybersecurity requirements placed on boards, such as the new rules adopted by the U.S. Securities and Exchange Commission (SEC) in July.
“For several topics, only roughly half of directors noted they were receiving information related to the area — indicating a gap and an opportunity for management,” reads the report, highlighting areas like third-party cybersecurity risk considerations and cyber program maturity assessments.
To get more details, check out:
- Highlights from the report
- The full “2023 Annual Corporate Directors Survey” report
For more information about board of directors’ growing cybersecurity responsibilities:
- “How much cybersecurity expertise does a board need?” (CSO)
- “A Tool to Help Boards Measure Cyber Resilience” (Harvard Business Review)
- “How to prepare company boards for new cybersecurity rules” (World Economic Forum)
- “Want a board-level cybersecurity expert? They're hard to find” (TechTarget)
- “Cybersecurity experts have become targets for board seats” (CNBC)
4 - Report: Ransomware attacks almost double in Q3
Ransomware gangs apparently didn’t take much of a summer break.
That’s according to a global ransomware frequency report from cyber insurance provider Corvus, based on the number of victims whose stolen data ransomware attackers posted on “leak” sites.
Specifically, Corvus observed a 95.4% jump in this number in the third quarter, compared with the same quarter last year. “While we usually see ransomware decline in the summer months, this year’s decrease was later and shorter than normal,” reads the report.
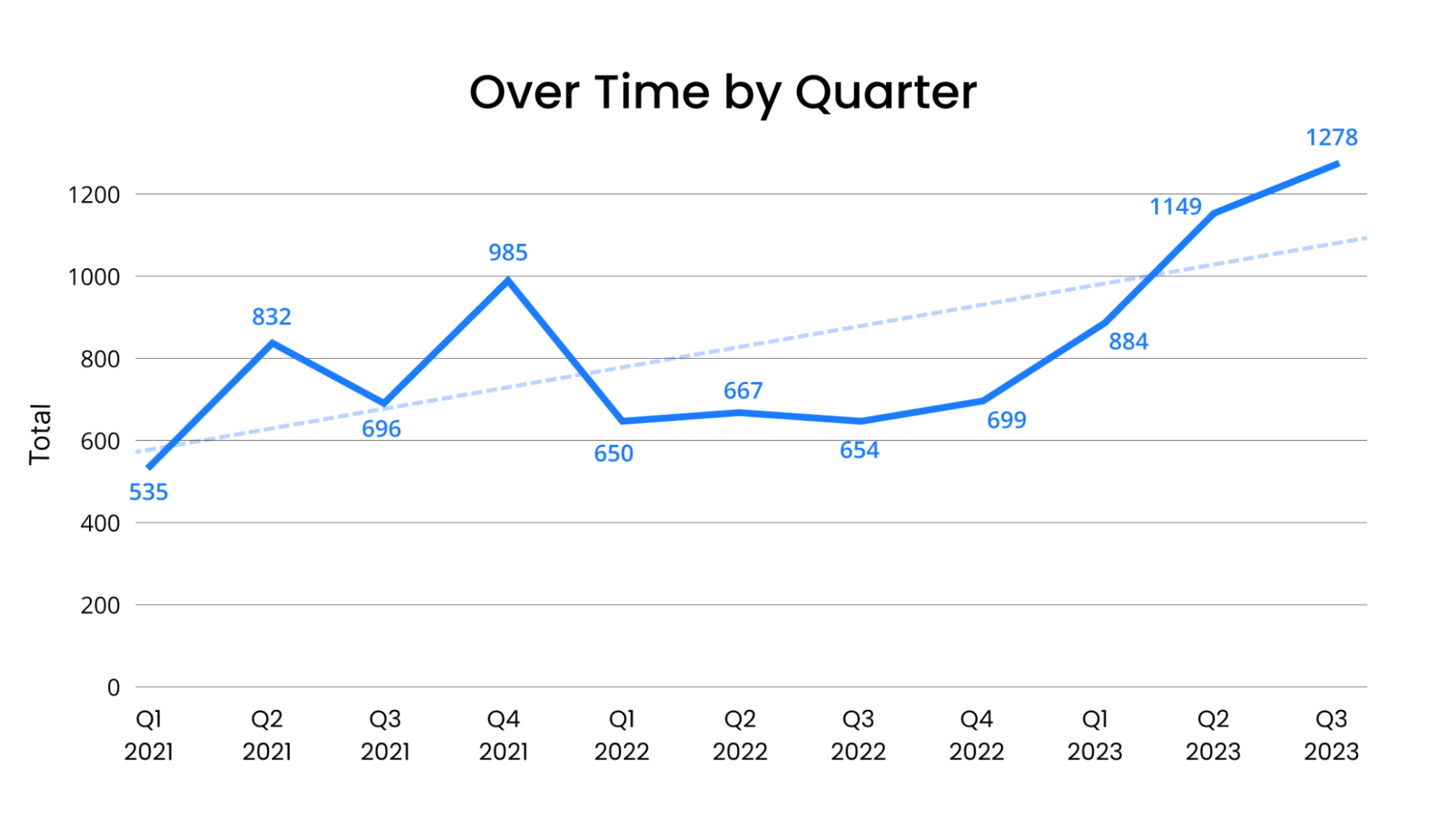
(Source: Corvus, October 2023)
In addition to the shorter-than-usual summer slump, activity from the CL0P ransomware gang also helped drive up the number of attacks during the quarter. Industry segments that were especially hard hit during the third quarter included law practices; government; oil and gas; and manufacturing.
To get more details, read the Corvus report “Q3 Ransomware Report: Global Ransomware Attacks Up More Than 95% Over 2022”.
For more information about recent ransomware incidents and trends, check out these Tenable resources:
- “CVE-2023-20269: Zero-Day Vulnerability in Cisco Adaptive Security Appliance and Firepower Threat Defense Reportedly Exploited by Ransomware Groups” (blog)
- “FAQ for MOVEit Transfer Vulnerabilities and CL0P Ransomware Gang” (blog)
- “FBI and CISA Release Cybersecurity Advisory on Royal Ransomware Group” (blog)
- “The Ransomware Ecosystem” (report)
- “Tenable’s Ransomware Ecosystem Report” (on-demand webinar)
5 - NCSC: How to protect cloud backups as part of ransomware preparedness
As ransomware continues to plague organizations, it’s key for them to continuously back up their critical data, in case attackers encrypt it and threaten to erase or destroy it.
Noticing that cloud backups have become a popular option, the U.K. National Cyber Security Centre (NCSC) has published a set of best practices to better protect this data-backup method.

Here’s a sampling of what the NCSC recommends to cloud backup vendors and their customers in its new “Principles for ransomware-resistant cloud backups” guidance:
- Options to make cloud backups more resilient to destructive actions:
- Once a backup is created, deny all data deletion, alteration and destruction requests
- Offer “soft-delete” capability by default, which makes deleted data available for a period of time
- Delay data deletion, destruction or alteration requests
- Option to prevent an attacker from locking out all users of a cloud backup system:
- Set up an “out of band” mechanism for customers to access a compromised backup service, such as a separate authorized account or device
- Options to allow a customer to restore data from a specific backup version if attackers corrupt other versions:
- Allow backups to be stored at fixed time intervals, so that attackers can’t overwrite the system with a quick succession of corrupted backups
- Create and retain a backup version history from which system owners can choose which version to restore data from
To get more details, read the NCSC blog “Our new principles to help make cloud backups more resilient” and the full guidance “Principles for ransomware-resistant cloud backups”.
6 - U.S. government spotlights OSS security in OT environments
Is your organization using open source software (OSS) in its operational technology (OT) environments? You might want to check out a new fact sheet from the U.S. government that aims to create awareness about OSS security risks among OT users.
Jointly published by CISA, the FBI, the National Security Agency and the Treasury Department, the fact sheet also offers best practices to securely use OSS in OT systems, especially in those used by critical infrastructure providers.
“This fact sheet will assist with better management of risk from OSS use in OT products and increase resilience using available resources,” reads the document.
Titled “Improving Security of Open Source Software (OSS) in Operational Technology (OT) and Industrial Control Systems (ICS),” the fact sheet addresses areas such as vulnerability management, patch deployment, supply chain security, asset inventory, and identity and access management.
To get more details, check out:
- The joint announcement “CISA, FBI, NSA, and Treasury Release Guidance on OSS in IT/ICS Environments”
- The CISA page “Securing Open Source Software in Operational Technology”
- The fact sheet “Improving Security of Open Source Software (OSS) in Operational Technology (OT) and Industrial Control Systems (ICS)”
- Commentary from the Open Source Security Foundation (OpenSSF)

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
Related Articles
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- OT Security
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
65 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
BUY
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
65 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Try Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Formerly Tenable.sc
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Formerly Tenable.ot
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Formerly Tenable.ad
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Formerly Tenable.asm
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Try Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
如有侵权请联系:admin#unsafe.sh