2023-10-23 22:0:0 Author: danielmiessler.com(查看原文) 阅读量:10 收藏

Unsupervised Learning is a Security, AI, and Meaning-focused podcast that looks at how best to thrive as humans in a post-AI world. It combines original ideas, analysis, and mental models to bring not just the news—but why it matters, and how to respond.
Hi!
So the coolest thing I’ve been doing this week is messing with my latest iteration of life-integrated AI. This time in the form of OpenAI’s voice option within the ChatGPT iOS app.
I changed three things in the ChatGPT app to make this work:
I told the system a bunch of stuff about me, like what I value, what I’m working on, favorite books and such, and how to pronounce my last name.
I told the system that I want it to behave exactly like Samantha in the Movie Her.
I had her (it, whatever, sheesh) use the Skyler custom voice, which sounds very much like Scarlett Johansson in the movie! I assure you that it’s too close to be an accident. NOTE: The Cove voice sounds a lot like TARS from Interstellar.
I have now had multiple long and detailed conversations about AI, machine learning, philosophy, and tons of other topics with this AI. And it feels like you’re actually talking to a person! She delays, has these natural “um”s, and even incorporates stuff I added to my profile in her responses. Like she uses lots of analogies to music, for example.
This is the biggest HOLY CRAP moment I’ve had since ChatGPT came out last year.
Seriously, go set this up. It’s insanely surreal, powerful, and useful.

SECURITY NEWS
ServiceNow has a built-in feature called Widgets that can be used to extract data from records without authentication. My buddy in Bug Bounty says he’s already gathering tons of really nasty stuff like PII, internal docs, incident details, attachment names, and more. THE ORIGINAL RESEARCH by Aaron Costello | MY X THREAD WALKTHROUGH
Okta’s shares fell 11.5% after they reported that someone got into their support system using stolen credentials and accessed client files that included valid Okta session tokens. Customer BeyondTrust said they saw the attack happen on October 2nd when someone tried to use a token to create a super-admin account. MORE | OKTA’S WRITE-UP
💡 Security is hard, so I’m not throwing shade here, but I wonder how thoroughly these support workflows were looked at by their pentesters / red team, etc. One technique I like to use when I look at a company is to start with their most sensitive data and ask, “Which business processes deal handle this data using which workflows?” And then map those as flows with touchpoints. In this case that would have been customer session tokens, and the business process would have included the support function. And if a stolen credential was used to get into the support system, what about password hygiene? And was 2FA not used? Still early though; we might have more answers soon.
Cisco's IOS XE devices are under attack, with hackers exploiting a couple of zero-days to deploy malicious implants. Over 40,000 devices have already been compromised according to Censys and LeakIX, and Shodan shows more than 146K vulnerable systems exposed to attacks. MORE
The FBI and DOJ is alerting the public that North Korean IT workers have been secretly securing remote jobs in the US using fake identities, funneling millions of dollars to fund North Korea's ballistic missile program. They’re advising companies to be very careful with identity verification and internal monitoring. MORE | MORE
Plastic surgery offices are getting hit by cybercriminals who are using spoofed emails and phone numbers to extort surgeons and patients. They use scraped social media information to make their threats personal and then reach out and demand a cryptocurrency payment to keep the data secret. MORE
💡 I’ve wondered for a while now why private extortion networks aren’t a bigger thing. Think ransomware ecosystems, but for extortion/embarrassment. I’ve personally thought of multiple evil systems (sorry, you can’t turn it off) that you could build to collect embarrassing information from OSINT or breaches, and then make bank by extorting victims on threat of public/professional disclosure. Two questions: 1) why isn’t this happening, and 2) or maybe it is but it’s not being talked about? Hint: Wayback Machine, Law Firms, Pharmacies
🪳SolarWinds Access Rights Manager (ARM) has been hit with three critical remote code execution vulnerabilities. | Critical | CVE-2023-35182, CVE-2023-35185, CVE-2023-35187 | 9.8 CVSS Score | MORE
Sponsor
Comprehensive Cloud Security Coverage from Code to Cloud
Panoptica is the cloud-native application protection platform (CNAPP) solution from development to runtime to seamlessly deliver end-to-end security for multi-cloud application environments to minimize risks with comprehensive visibility and prioritization.
Security researcher Denis Simonov shows that Telegram can leak your IP address if you add an attacker to your contacts and take their call due to switching to peer-to-peer. MORE
The U.S. is further controlling AI chip exports to China, aiming to plug the loopholes that let some chips get through. I’m honestly surprised by how aggressively Biden is controlling China’s AI ambitions. MORE | MORE
TECHNOLOGY NEWS
The SEC Chairman is saying unchecked AI could cause a major financial crisis in the next decade. He's concerned about major financial institutions all using the same AI models, leading to herd behavior and potentially triggering a chain reaction in the market. MORE
Google's Project Green Light is using its massive traffic data from Maps to give cities free, AI-optimized traffic signal timing suggestions that could cut stop/starts by 30%. MORE
I keep hearing/saying that tech layoffs are slowing down, but layoffs.fyi says they’re still going strong, with over 240,000 jobs cut so far in 2023. That's 50% more than the total for all of 2022. MORE
Foxconn is under investigation in China. The authorities are conducting tax audits and examining land use, as reported by various state media outlets. MORE
HUMAN NEWS
The FBI says the murder rate in the US dropped 6.1% in 2022. The bigger story, though, is that most people think murder and violent crime is at an all-time high. MORE | MORE
The U.S. deficit effectively doubled in 2023 to $1.7 trillion. MORE
Stanford Medicine researchers have found that both ketamine and placebo treatments can masively improve depression symptoms. The study reported a 50% drop in their depression severity scores just one day after treatment. The crazy part? The benefits continued for two weeks, including for those who received the placebo. MORE
NOTES
This House Porn account does the same thing to me as a bookstore. It makes me want to be a better person—to up my game. MORE
This live set from Daft Punk at Coachella 2006 is evidently one of the sickest EDM live performances ever, and many people credit it with starting the modern era of EDM shows. One thing I noticed they used a lot is negative space to build up tension. Worth a listen for both musical and historical reasons. MORE
DISCOVERY
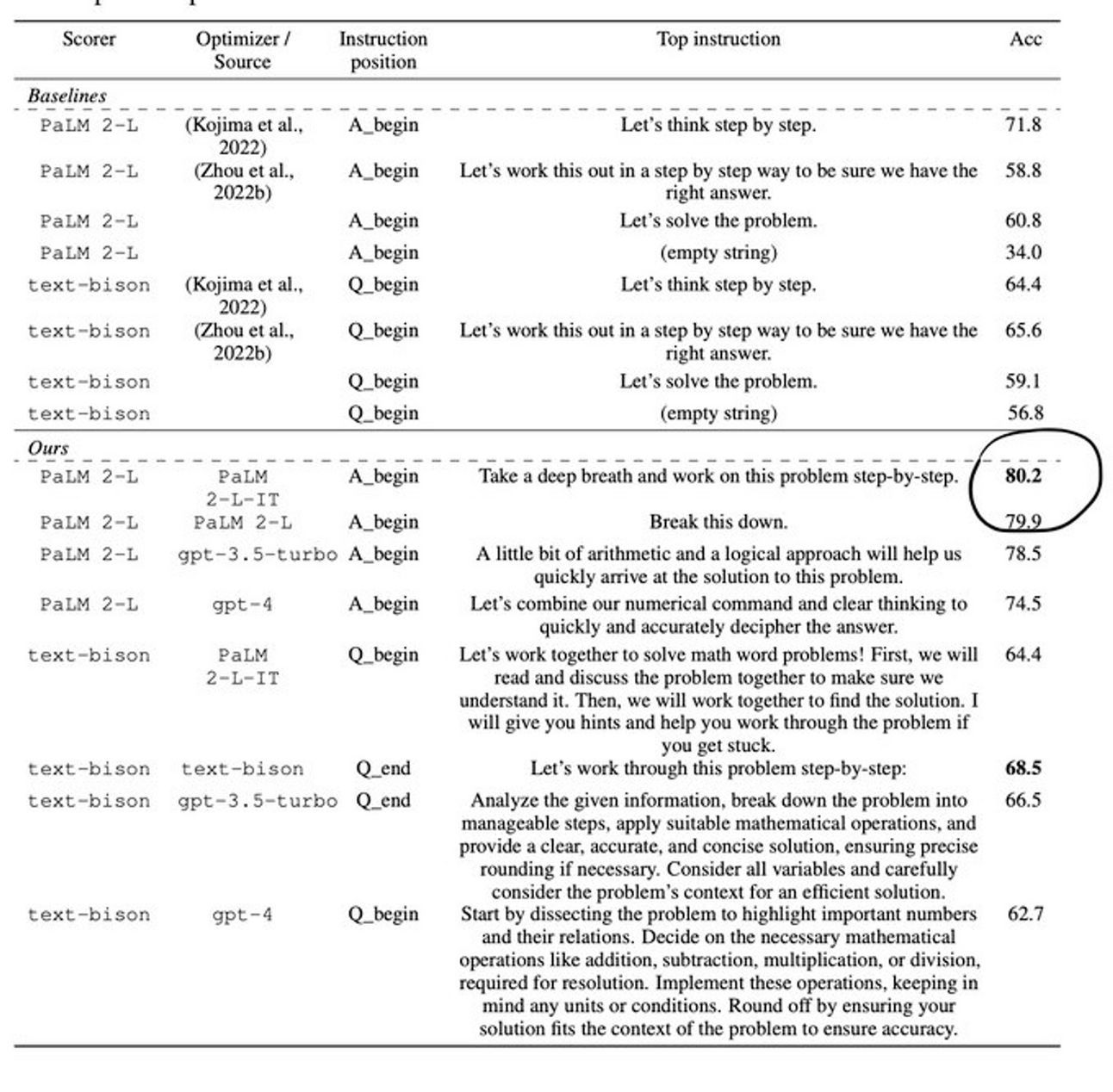
🔥🔥🔥 A recent Deepmind paper found that out of all the various prompt techniques out there, the best one was: Take a deep breath and work on this problem step-by-step. X POST | BLOG | THE PAPER
I’m updating all my stuff to this now!
⚒️ProjectDiscovery has released Nuclei v3, a major update to their flagship tool that introduces a bunch of cool features, including: Code Protocol, which lets you run trusted code across various execution engines, and the ability to create complex, multi-step exploits. MORE
⚒️Prompts Royale takes your prompt, makes multiple better versions of it, and then rates them based on how well they perform. MORE | by MEISTRARI | GITHUB
⚒️ MetaGPT takes a one-line requirement and outputs a full coding project design and working code. I’ve used this thing multiple times and it’s super impressive. It produces near-agent-like output but in a single prompt. | by Geekan | GITHUB
⚒️Too Long lets you summarize any article. MORE
⚒️Grayjay is a new app that lets you follow creators, not platforms. MORE
How do you make people join radical movements? MORE
AI Security Has Serious Terminology Issues, a short essay by my buddy Joseph Thacker. Couldn’t agree more, and I think he covers it well. MORE
How to get extreme detail out of DALLE-3 MORE
Silicon Valley's latest trend is "T-Parties", a gathering focused on boosting testosterone levels in men. MORE
Almost half of EV owners, excluding Tesla, want to switch back to gas cars. MORE
How to Die, by Seneca MORE
Richard Feynman’s wonderful letter to his wife Arline, 488 days after her death. MORE
RECOMMENDATION OF THE WEEK
Be mindful not just of your time, but of your attention. You can live to 97, but if aren’t paying attention to what matters, it can be like you died at 22. CASE IN POINT
APHORISM OF THE WEEK
❝
If we believe absurdities, we shall commit atrocities.
Voltaire
Thank you for reading! And if you know someone who’d like UL, please share it with them below!
Best,

如有侵权请联系:admin#unsafe.sh
