2023-10-20 03:0:47 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
By Cofense Intelligence
A series of campaigns delivering the newly christened “Complaint Stealer” malware began in mid-October and escalated within the last 2 days. The Complaint Stealer malware is an Information Stealer that targets cryptocurrency wallets and programs as well as credentials stored in browsers. Complaint Stealer shows unusual interest in the graphics card and other information associated with cryptocurrency mining so cryptocurrency mining may be a later addition. Complaint Stealer also often makes use of legitimate software such as AutoIT or PKWARE. All samples seen to date use the same C2 location. This campaign uses social engineering tactics also recently seen during the MGM, Caesars and other luxury hotel resort breaches.
Phishing Campaign Characteristics
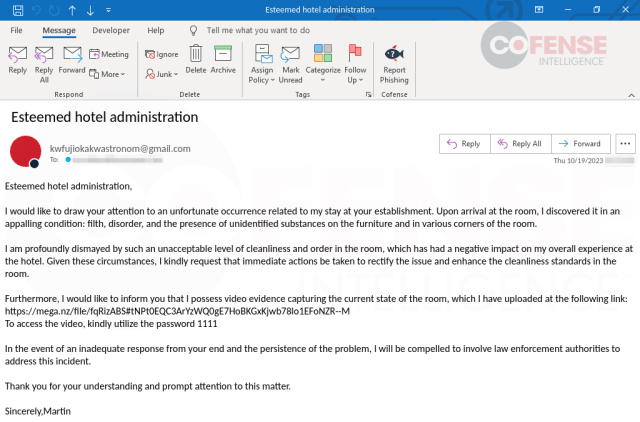
These campaigns all targeted hospitality customers and were themed around complaints about the accommodations, staff behavior, etc. The campaigns bypassed multiple Secure Email Gateways (SEGs) including Cisco Ironport and Microsoft ATP. The phishing campaigns delivering Complaint Stealer all used password protected archives downloaded from embedded mega[.]nz URLs to deliver the malware.

Figure 1: Email from campaign delivering Complaint Stealer.
如有侵权请联系:admin#unsafe.sh
