
2023-10-20 00:55:36 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
40,000 devices compromised and counting: That’s what we’re facing with the zero-day vulnerability in Cisco’s IOS XE software used in its routers, switches, and access points, both physical and virtual.
This is still a developing story, but here are the important points:
What to know
- The current activity is likely coming from a single threat actor, with the first observed threat activity on September 28.
- Cisco announced a zero-day vulnerability on October 16 (CVE-2023-20198) with no patch available as of this writing. The current guidance is to disable the HTTP Server feature on all internet-facing systems (or set access control lists) and check for indicators of compromise.
- As of October 18th, the internet scanning firm Censys has found more than 40,000 devices showing indicators of compromise. One Shodan search found more than 140,000 Cisco IOS XE Web UIs exposed to the internet (potentially making them vulnerable).
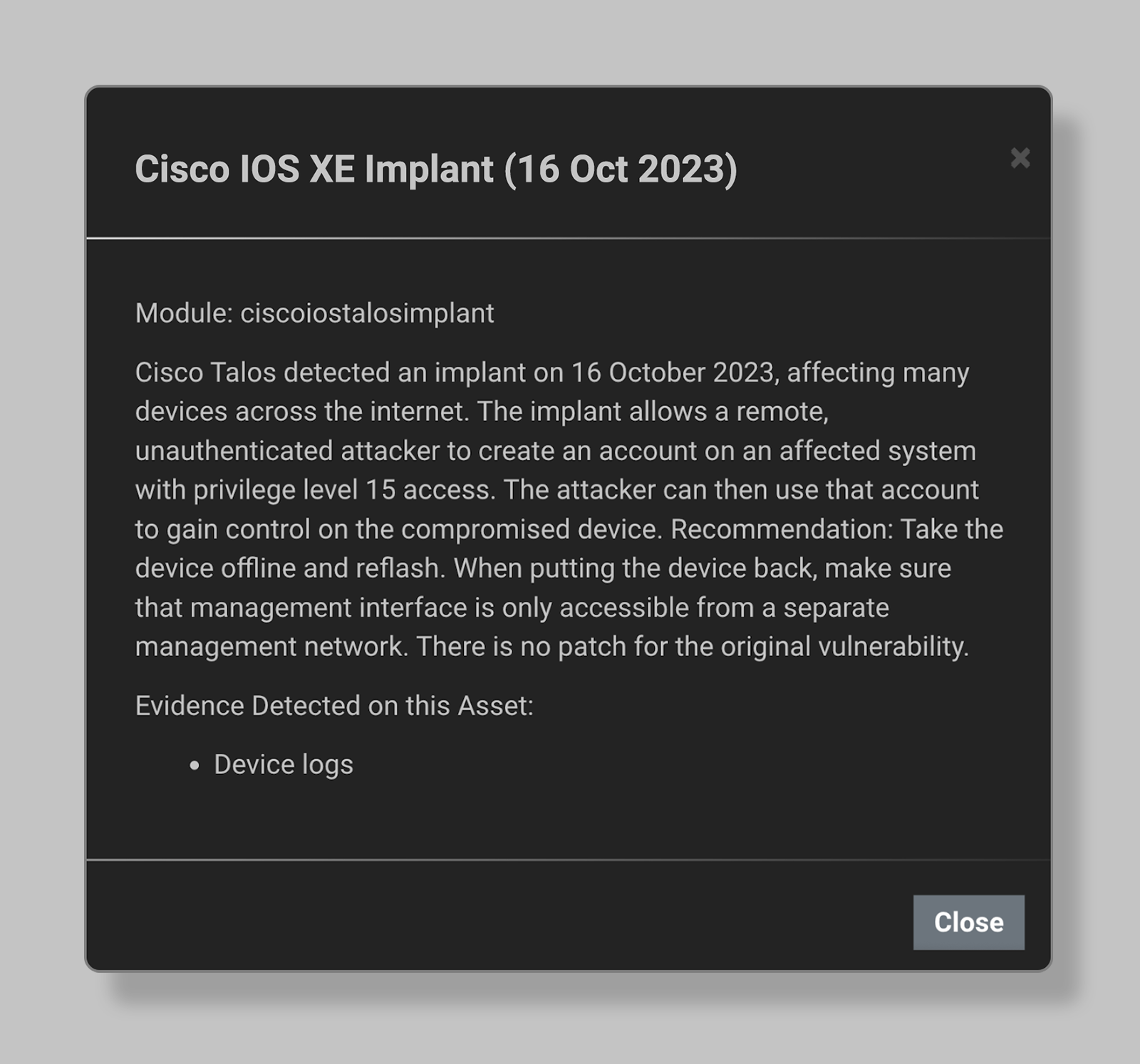
- Eclypsium detects the implant that is part of the ongoing mass exploitation campaign, along with other threats.
Key takeaways
- In this case, the speed at which the threat actors have compromised vulnerable devices is astounding—compromising tens of thousands of infrastructure devices before the vendor has released a patch. Updating network infrastructure can affect the availability of business-critical applications, so even when a patch is available it will require careful attention on the part of network operations teams. Unlike modern server environments, the patching process for network infrastructure vulnerabilities is complex due to downtime involved.
- The wide scope of the discovered exploits shows that many, many organizations are still not following best practices of either removing management interfaces from the internet or implementing zero-trust network access controls. This is why CISA issued Binding Operational Directive 23-02 in June, requiring federal agencies to mitigate these risks. Even if you’re not in the federal government, CISA’s note is worth a read. We all need to reflect on why many attacks on important IT infrastructure are successful because of poor security hygiene.
- One reason attackers target network devices is because they are by their nature connected to internal networks—perhaps thought to be unexposed to the internet. Many vulnerabilities are deprioritized because they are mistakenly thought to be unreachable by attackers, such as the baseboard management controller vulnerabilities that Eclypsium research discovered earlier this year.
Eclypsium customers can detect Cisco IOS XE exploits
Based on analysis details of the exploit provided by Cisco Talos, Eclypsium has added detection capabilities for the implant used in the CVE-2023-20198 mass exploitation campaign.

Network infrastructure is under attack!
So far in 2023, there have been a number of attacks against network devices of which this is the latest. We’ve had Volt Typhoon, JaguarTooth, and BlackTech campaigns from APTs. But we’ve also seen ransomware groups Akira, CACTUS, FIN8, and LockBit 3.0 targeting network appliances.
Eclypsium is on a mission to secure the supply chain for your IT infrastructure, part of the broader digital supply chain. What we do addresses a critical gap in cybersecurity programs: Eclypsium provides security teams the ability to inventory assets and their low-level components, harden their hardware and firmware attack surface, and detect below-the-surface threats that evade EDR. CVE-2023-20198 and the mass exploitation campaign that we’re seeing for this zero-day vulnerability is just an example of why a new approach is needed to protect network infrastructure.
Finally, threat detection for network devices
As you know, EDR is not supported on network infrastructure. That’s one reason Eclypsium has expanded our firmware OS integrity and threat detection capabilities for network devices, and last month announced new features that monitor for changes in firmware and OS binaries, modified configuration and backup files, reverse shells, persistence modules, and more. Eclypsium brings EDR-like capabilities to network infrastructure and helps organizations to detect and respond to events like the mass exploitation of CVE-2023-20198.
This is a supply chain security problem
While we wait for all enterprise technology products to be shipped secure by design, organizations need to have a “trust but verify” approach to the digital supply chain, including for network devices. Defenders need to anticipate and manage supply chain risk, including zero-day vulnerabilities in components such as IOS XE firmware. Simply scanning for known vulnerabilities alone is insufficient. Additional device integrity checks and continuous monitoring can add important compensating controls to detect compromise.
If you are ready for a new approach to protecting network infrastructure, please schedule a demo. You can also walk through the key capabilities of our platform in this product tour (no form fill required).
The post Cisco IOS XE Zero-Day: Network Supply Chain Vulnerabilities Underscore Lack of Threat Detection appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.
*** This is a Security Bloggers Network syndicated blog from Eclypsium | Supply Chain Security for the Modern Enterprise authored by Chris Garland. Read the original post at: https://eclypsium.com/blog/cisco-ios-xe-zero-day-network-supply-chain-vulnerabilities-underscore-lack-of-threat-detection/
如有侵权请联系:admin#unsafe.sh
