
2023-10-17 08:4:35 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
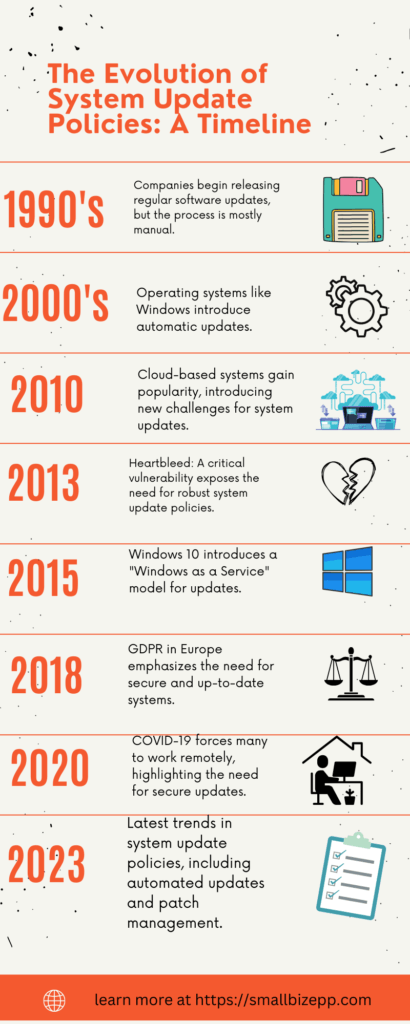
Introduction
In 2023, a robust system update policy is more crucial than ever. Cyber threats are evolving, and outdated systems are easy targets. Our infographic below charts this vital evolution. From the late ’90s to today, you’ll see why staying updated is non-negotiable. So, let’s dive in and uncover what you might be overlooking in your system update policy.
Why System Update Policies are Crucial in 2023
In 2023, the stakes for system update policies have skyrocketed. Cybersecurity threats are not only increasing but also becoming more sophisticated. For instance, ransomware attacks have surged, targeting vulnerabilities in outdated systems. Additionally, the rise of IoT devices in the workplace has expanded the attack surface. These challenges make 2023 a critical year for reevaluating and fortifying your system update policy.
Asset Prioritization in System Updates
Asset prioritization is a cornerstone of an effective system update policy, especially in 2023. Not all assets are created equal; some are more critical to your business operations than others. Our matrix above serves as a guide to help you categorize assets based on priority level, vulnerability risk, and business impact. Knowing which assets are crucial and when they’re available for updates helps in crafting a policy that’s both secure and practical.
| Asset Type | Priority Level | Update Frequency | Vulnerability Risk | Business Impact |
|---|---|---|---|---|
| Desktop Computers | High | Weekly | Moderate | High |
| Cloud Servers | Critical | Daily | High | Critical |
| IoT Devices | Medium | Monthly | Low | Medium |
| Mobile Devices | Low | Bi-weekly | Low | Low |
| Network Routers | High | Weekly | High | High |
Mapping Vulnerabilities to Assets
Mapping vulnerabilities to assets is a critical step in fine-tuning your system update policy. This process allows you to identify which assets are most at risk and require immediate attention. By assessing the severity of vulnerabilities, you can allocate resources more effectively. For example, a high-severity vulnerability in a critical cloud server warrants urgent action. This targeted approach not only enhances security but also optimizes the use of IT resources.
The Role of Vulnerability Scanners
Understanding what to patch requires knowing your system’s vulnerabilities. That’s where vulnerability scanners come into play. These tools scan your network and systems, identifying potential security risks. They provide a comprehensive list of vulnerabilities, often ranked by severity, enabling you to prioritize your patching strategy effectively. Investing in a reliable vulnerability scanner is a crucial step in proactive cybersecurity, making it an indispensable part of your system update policy.
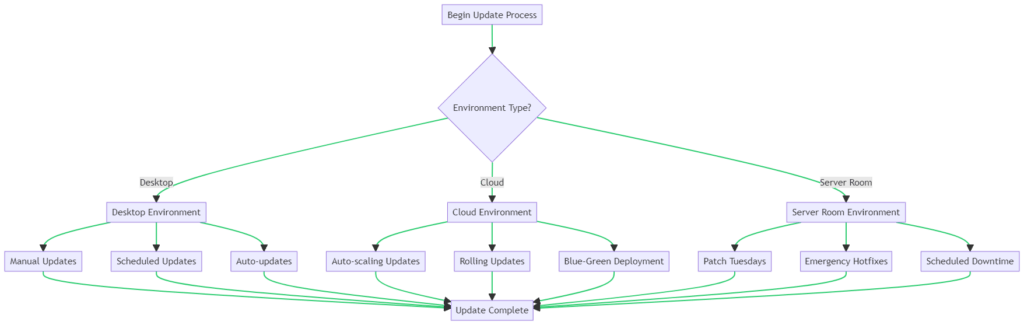
Understanding System Update Environments
In the complex landscape of system updates, understanding the environment in which your assets operate is crucial. The flowchart above provides a comprehensive guide to navigate this terrain.
Desktop Environment
As seen in the flowchart, desktop environments offer various update options. These range from manual updates to scheduled or auto-updates. Knowing which to use can significantly impact your endpoint security.
Cloud Environment
Cloud environments introduce unique challenges and opportunities. Options like auto-scaling updates and blue-green deployments offer flexibility but require careful planning.
Server Room Environment
Server rooms often house critical business assets. As the flowchart indicates, updates here may follow a strict schedule, like Patch Tuesdays, or require emergency hotfixes.
By tailoring your system update policy to the specific environment, you can optimize both security and resource allocation.
Update Policy for Windows Systems
Microsoft provides a comprehensive guide on managing updates for Windows operating systems, known as “Windows as a Service.” The guide outlines various servicing channels, tools, and strategies for deploying and maintaining Windows 10 and Windows 11. It emphasizes the importance of a structured approach to updates, including the use of different servicing channels and tools to manage feature and quality updates.
Key Points from Microsoft’s Guide:
- Servicing Channels: Microsoft offers three main channels—General Availability, Long-Term Servicing, and Windows Insider. Each has its own update frequency and target audience.
- Servicing Tools: Tools like Windows Update for Business, WSUS, and Microsoft Configuration Manager offer varying levels of control over updates.
- Feature and Quality Updates: Microsoft distinguishes between feature updates that add new functionalities and quality updates that provide security and reliability fixes.
Thought-Provoking Questions:
- How does your organization’s current update policy align with Microsoft’s recommendations?
- Which servicing channel is most appropriate for your organization’s needs?
- Are you utilizing the right servicing tools to manage updates effectively?
For more details, you can refer to Microsoft’s Overview of Windows as a service.
Update Policy for Mac OSX Systems
Apple emphasizes the importance of keeping your Mac updated for optimal performance and security. Here’s a rundown of their key recommendations:
- Automatic Updates: Apple advises enabling automatic updates to ensure you’re always running the latest software.
- Security Patches: Apple releases security updates separately, so you can install them without affecting your current setup.
- Compatibility Checks: Before updating, Apple’s system checks for compatibility issues and informs you beforehand.
- Backup: Always back up your data before initiating an update.
- User Approval: For major updates, user approval is required, ensuring you have control over the update process.
By adhering to Apple’s guidelines, you can maintain a robust and secure Mac OSX environment.
Update Policy for Linux Systems
Linux-based systems are a cornerstone in many enterprise environments, particularly Ubuntu and CentOS. While both are Linux distributions, their approaches to system updates differ. Understanding these nuances is crucial for effective update management.
Update Policy for Ubuntu Systems
Ubuntu uses the APT package management system, offering a range of options from automatic security updates to full manual control. The unattended-upgrades package is commonly used for automated security patches.
Update Policy for CentOS Systems
CentOS employs the YUM package manager. It provides options like yum-cron for automated updates and allows fine-grained control over package versions. Security updates can be selectively applied using yum-security.
By tailoring your update policies to the specific Linux distribution, you can optimize both security and system performance.
Update Policy for Cloud Environments
In cloud environments like AWS, Azure, and Google Cloud, the approach to system updates often includes unique features tailored for cloud computing. One such feature is the ability to backup entire instances before applying patches, a best practice that minimizes risks associated with updates.
AWS Update Policy
AWS offers AMI (Amazon Machine Images) backups, allowing you to revert to a previous state if an update causes issues. Even so, it is a good idea to have multiple instances running the same software so you could patch one, test it, then revert back to the original state if it isn’t working right.
Azure Update Policy
Azure provides snapshot capabilities, enabling you to capture the VM state and data at a specific point in time.
Google Cloud Update Policy
Google Cloud offers persistent disk snapshots, which can be used for backup, restore, or VM creation.
Leveraging these cloud-specific features can significantly enhance your system update policy, providing an extra layer of security and flexibility.
Automated vs Manual Updates: What’s Best for Your Business?
Automated updates excel in efficiency and security, requiring minimal human intervention and ensuring immediate patching of vulnerabilities. However, they offer less control over what gets updated and when, and they lack the flexibility to customize or delay updates. On the flip side, manual updates give you complete control over the update process and the flexibility to customize based on specific needs. But this comes at the cost of efficiency, as manual updates are time-consuming and require more resources. Additionally, the risk of delayed patching could lead to potential security vulnerabilities. Ultimately, the choice between automated and manual updates should align with your business needs and risk tolerance.
| Criteria | Automated Updates | Manual Updates |
|---|---|---|
| Efficiency | High | Low |
| Control | Low | High |
| Security | High (Immediate Patching) | Variable (Depends on Timeliness) |
| Resource Usage | Low | High |
| Flexibility | Low | High |
| Cost | Low | High (Labor Costs) |
The Role of Patch Management in System Update Policy
Patch management is the linchpin that holds your entire system update policy together. It’s not just about applying patches; it’s about strategically managing vulnerabilities across your IT landscape. Patch management involves identifying, acquiring, installing, and verifying patches for various software applications and systems. It’s a continuous cycle that aligns closely with your overall update policy to ensure system integrity, compliance, and security.
In essence, patch management serves as the operational backbone of your update policy. It provides the structure and governance needed to implement updates effectively. Whether you opt for automated or manual updates, a robust patch management strategy ensures that you’re applying the right fixes, at the right time, in the right environments. By integrating patch management into your system update policy, you’re taking a holistic approach to endpoint security, thereby elevating the resilience and reliability of your IT systems.
Testing Patches: QA First, Production Later
In the realm of system updates, patch management plays a pivotal role. One of the most crucial aspects is testing patches on QA (Quality Assurance) systems before rolling them out to production. This practice is not just a safety net; it’s a necessity.
Testing in a QA environment allows you to identify any issues or conflicts that could disrupt your production systems. It’s a proactive measure that safeguards against potential downtime and security risks. By adhering to this best practice, you’re not just preventing problems; you’re fortifying your entire update policy.
Compliance and Legal Considerations
Neglecting system updates isn’t just a technical oversight; it can also have legal repercussions. Outdated systems are vulnerable to security breaches, and if sensitive data is compromised, your organization could face hefty fines and legal actions. Laws like GDPR in Europe and CCPA in California mandate strict data protection measures, including timely system updates.
Moreover, industry-specific regulations like HIPAA for healthcare and PCI DSS for payment card information also require up-to-date security measures. Non-compliance not only results in financial penalties but can also damage your brand’s reputation and customer trust.
In summary, integrating compliance and legal considerations into your system update policy is not optional; it’s a necessity. By staying compliant, you’re not just avoiding penalties but also fortifying your system’s security and integrity.

How to Create an Effective System Update Policy
Creating an effective system update policy is a multi-step process that requires careful planning and execution. Here’s a step-by-step guide to help you navigate this crucial task:
- Identify Stakeholders: Determine who will be involved in the update process, such as IT personnel, management, and compliance officers.
- Asset Inventory: Catalog all hardware and software assets that will be subject to updates.
- Risk Assessment: Evaluate the potential risks associated with each asset. This will inform your asset prioritization strategy.
- Define Update Types: Classify updates as security patches, feature updates, or bug fixes. Each type may have different urgency levels.
- Set Update Frequency: Decide how often updates will be conducted. This could be influenced by compliance requirements or asset criticality.
- Choose Update Method: Decide between automated and manual updates based on your business needs and risk tolerance.
- Testing Protocol: Establish a QA environment for testing patches before they’re applied to production systems.
- Rollout Strategy: Plan the sequence and timing for rolling out updates to minimize disruption.
- Compliance Checks: Ensure that your policy aligns with legal and industry-specific regulations.
- Documentation: Keep detailed records of all updates, including what was updated, why, and the outcomes.
- Review and Revise: Regularly review the policy to adapt to new risks, technologies, and compliance requirements.
By following these steps, you’ll create a system update policy that is not only effective but also compliant and adaptable to the ever-changing landscape of cybersecurity.
Eye-Opening Statistics on the Consequences of Neglecting System Updates
Did you know that up to 60% of data breaches are tied to unpatched vulnerabilities? This alarming figure underscores the dire need for robust system update policies. Moreover, 25% of organizations admit to not being compliant with data security legislation, often delaying patches to avoid business interruptions.
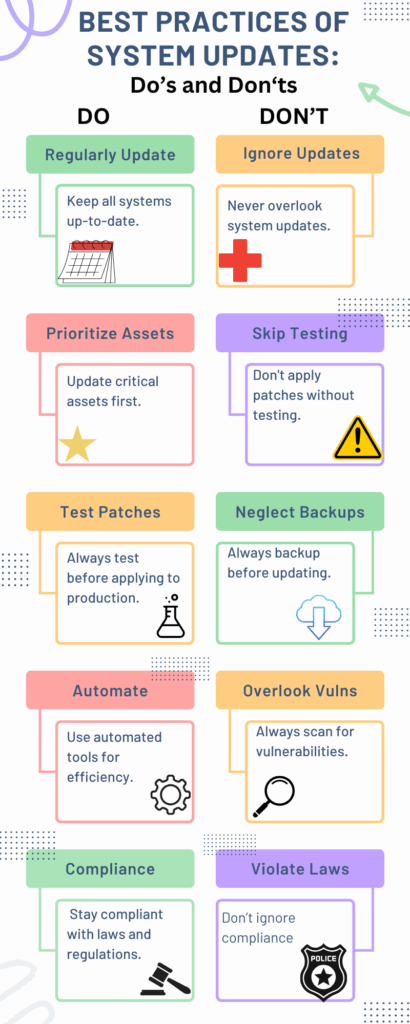
Best Practices for 2023: Do’s and Don’ts
Navigating system updates can be complex, but adhering to some best practices can simplify the process. Our infographic outlines the essential do’s and don’ts for 2023.
Do’s
- Regularly Update: Consistency is key. Make sure all systems are up-to-date to minimize security risks.
- Prioritize Assets: Not all assets are created equal. Focus on updating critical systems first.
- Test Patches: A patch is only as good as its test. Always test in a QA environment before rolling out.
- Automate: Time is money. Utilize automated tools to streamline the update process.
- Compliance: Ignorance is not bliss. Stay compliant with relevant laws and regulations to avoid legal repercussions.
Don’ts
- Ignore Updates: Neglecting updates can lead to severe security breaches.
- Skip Testing: A failed patch can be catastrophic. Never skip the testing phase.
- Neglect Backups: Always have a backup plan. Literally.
- Overlook Vulnerabilities: Know your weaknesses by regularly scanning for vulnerabilities.
- Violate Laws: Non-compliance can result in hefty fines and a tarnished reputation.
By following these best practices, you’re well on your way to fortifying your system update policy for 2023.
Conclusion
In 2023, a well-defined system update policy isn’t just a good idea—it’s a necessity. With evolving cybersecurity threats and stringent compliance requirements, staying updated is your first line of defense. Don’t overlook this crucial aspect of endpoint security; the stakes are too high.
We’d love to hear your thoughts. Have questions or insights about system update policies? Feel free to comment below. Take this opportunity to review your own update policy and ensure it’s up to par for the challenges of 2023.
The post Unlocking the Best Practices for System Update Policy in 2023 appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/system-update-policy/?utm_source=rss&utm_medium=rss&utm_campaign=system-update-policy
如有侵权请联系:admin#unsafe.sh
