One of the world’s largest online travel agencies, Booking.com, is being used by fraudsters to trick hotel guests into handing over their payment card details.
How do I know? The fraudsters tried it with me.
I’m speaking at an event in London in November, and needed to book a hotel room for the night before. I don’t normally use Booking.com for my travel arrangements, but on this occasion I did – and as a result I nearly fell for a scam that could have stolen my credit card details.
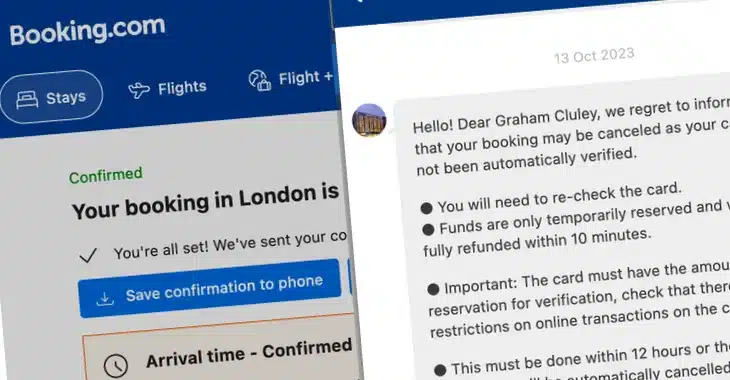
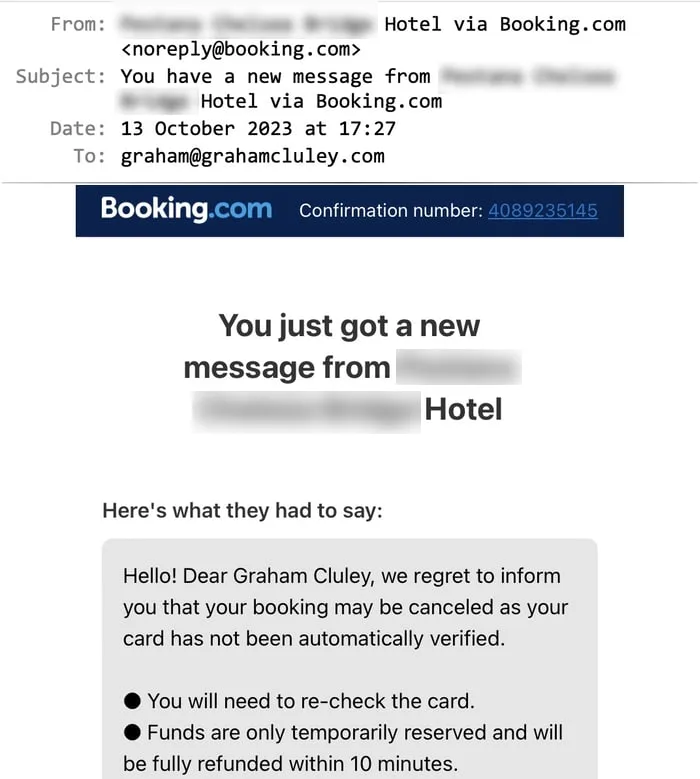
The online booking went smoothly as you would expect. But on Friday, two weeks after I made the original booking, I received a notification from the Booking.com smartphone app that I had a new message from the hotel I was planning to stay at.
I looked in the app, and sure enough I had a message from the “hotel”, straight after a legitimate message from the hotel. It also appears on the website version of Booking.com.
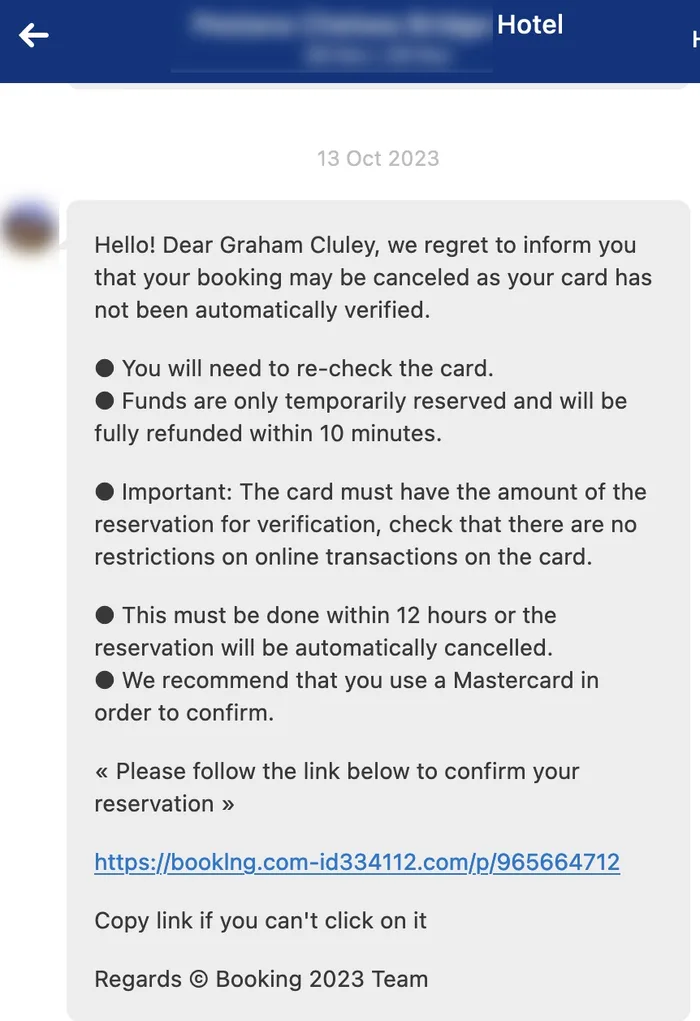
Hello! Dear Graham Cluley, we regret to inform you that your booking may be canceled as your card has not been automatically verified.
● You will need to re-check the card.
● Funds are only temporarily reserved and will be fully refunded within 10 minutes.● Important: The card must have the amount of the reservation for verification, check that there are no restrictions on online transactions on the card.
● This must be done within 12 hours or the reservation will be automatically cancelled.
● We recommend that you use a Mastercard in order to confirm.« Please follow the link below to confirm your reservation »
https://booklng.com-id334112.com/p/965664712
Copy link if you can’t click on it
Regards © Booking 2023 Team
Note that this wasn’t email spam. This was a message sent via the Booking.com website/app.
Here’s how it looked in the Booking.com smartphone app.
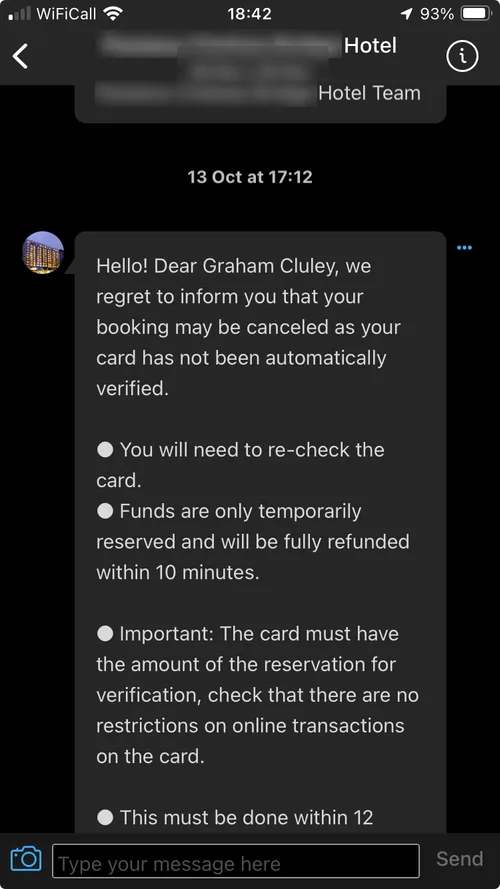
The message told me that my booking may be cancelled due to some credit card issue, and tells me to visit a URL to reconfirm my credit card details.
Clicking on the link took me to a webpage that contained my booking details, but was at a domain (com-id334112.com) that had been created just hours earlier. Sure enough, it asked me to enter my payment card data again.
After over 30 years of working in cybersecurity I like to think that I wouldn’t fall for a scam like this. But I received the notification when I was half-way down a supermarket aisle trying to find some aubergines. I could very easily have clicked on the link in my haste to ensure that I didn’t lose my hotel booking.
I can easily imagine how many Booking.com customers would fall for something like this, regardless of whether they were hunting for the ingredients for ratatouille or not.
I did the right thing. I went home, made a ratatouille, and then investigated how to contact Booking.com’s security team.
Unfortunately, Booking.com doesn’t have a “security.txt” file set up on its website listing how to contact it responsibly when a security issue has been found, which would have made things more straightforward.
Fortunately, colleagues in the security community on Mastodon, Twitter and other sites were able to point me in the right direction.
And so I sent the security team at Booking.com an email with all the details of what I had seen, in the hope that they would look into it and get back to me.
They haven’t responded to my email.
But this evening I (and I suspect other Booking.com customers) received the following email. Let’s take a look at what they say.
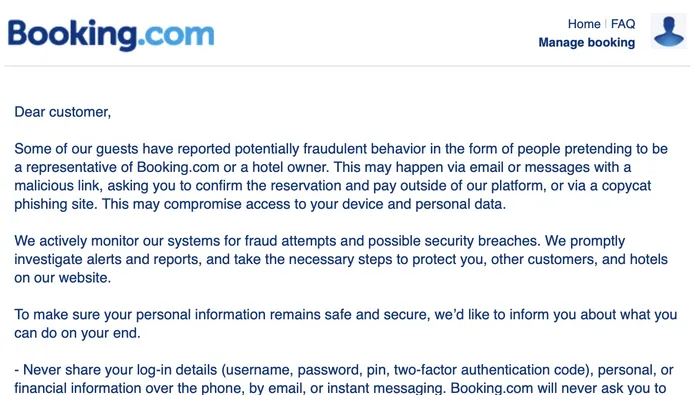
Some of our guests have reported potentially fraudulent behavior in the form of people pretending to be a representative of Booking.com or a hotel owner. This may happen via email or messages with a malicious link, asking you to confirm the reservation and pay outside of our platform, or via a copycat phishing site. This may compromise access to your device and personal data.
Okay, that sounds like what I’ve experienced.
We actively monitor our systems for fraud attempts and possible security breaches. We promptly investigate alerts and reports, and take the necessary steps to protect you, other customers, and hotels on our website.
Well, that’s good – although you didn’t manage to protect me on this occasion. I protected myself.
To make sure your personal information remains safe and secure, we’d like to inform you about what you can do on your end.
Great, let’s hear your suggestions.
– Never share your log-in details (username, password, pin, two-factor authentication code), personal, or financial information over the phone, by email, or instant messaging. Booking.com will never ask you to share this information with us. If someone – claiming to be a Booking.com employee – asks for your log-in details, personal, or financial information, or requests remote access to your devices, hang up and contact our Customer Service team. We strongly advise you to immediately change your password for your Booking.com account on our website.
I didn’t share my username, password, or any other information with anyone… other than with Booking.com when I log into Booking.com.
– If you used your Booking.com password to access other online services or accounts, we recommend you reset the passwords for those accounts as well.
I haven’t used my Booking.com password anywhere else. I used a unique, strong password.
It’s important to use a unique password for each account you have.
I agree.
– Always check email addresses thoroughly. We’ll only email you from an official Booking.com email address ending with “@booking.com” or “@partner.booking.com”.
Well, the message I received was via the Booking.com website itself (it’s still there by the way) and via the Booking.com app.
But now you mention it, if I look in my email I do see that I received the fraudulent message via email too…
Oh, this is embarrassing – it comes from a @booking.com email address.
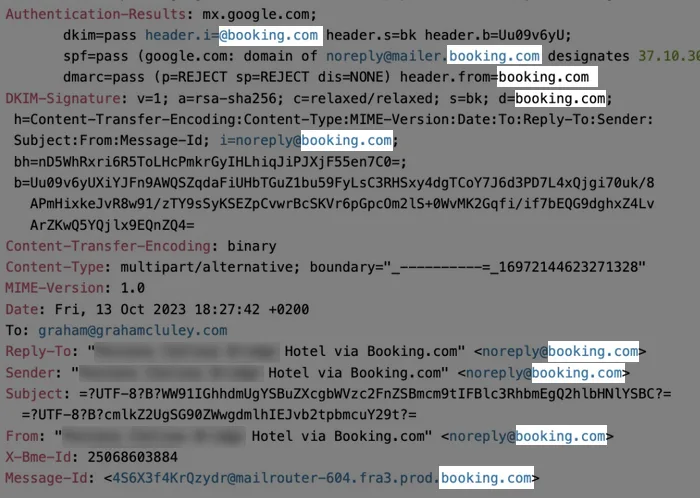
In fact, it even contained a Booking.com tracking pixel so the company could tell if I opened the message! (Fortunately my email client warns of such annoyances.)
![]()
Anyway, back to the warning email from Booking.com.
Any email addresses using other variations, such as “[email protected],” are not official Booking.com email addresses. To learn more about online security and awareness, check out the section ‘Safety resource center’ on our website, which you can find on the bottom of our homepage.
Good advice, but in my case the messages arrived via Booking.com’s app and website. And the email came from Booking.com.
– Only access your account via the official Booking.com website at www.booking.com
Yes, I did that.
or the mobile app.
And that.
When accessing your account, always check for a secure connection. Look for the security lock icon in the address bar or make sure the address starts with https://. This ensures the page is managed by Booking.com and is genuine.
Hmm.. Err. No, the presence of https and a padlock in your browser does NOT confirm “the page is managed by Booking.com and is genuine.”
If any email or message link directs you to a website that looks like Booking.com but doesn’t have a secure connection, leave the website, don’t enter any log-in details, and don’t click on other links. You can bookmark the official Booking.com page in your browser for quick and secure access.
If you have any other questions, please reply to this message.
I have some other questions.
How are fraudsters using Booking.com to send out fraudulent messages to guests? Your email doesn’t answer that. Is there a fraudster working at the hotel I’m going to be staying in in a few weeks’ time who has access to the hotel’s Booking.com account and can communicate with their customers? Or is there some other hijinks at play here?
Found this article interesting? Follow Graham Cluley on Twitter or Mastodon to read more of the exclusive content we post.
Graham Cluley is a veteran of the cybersecurity industry, having worked for a number of security companies since the early 1990s when he wrote the first ever version of Dr Solomon's Anti-Virus Toolkit for Windows. Now an independent analyst, he regularly makes media appearances and is an international public speaker on the topic of cybersecurity, hackers, and online privacy. Follow him on Twitter, Mastodon, Bluesky, or drop him an email.
