The internship season is back at Quarkslab! Our internship topics cover a wide range of our e 2023-10-16 06:0:0 Author: blog.quarkslab.com(查看原文) 阅读量:29 收藏
The internship season is back at Quarkslab! Our internship topics cover a wide range of our expertise and aim at tackling new challenges, namely:
- 🟢 Automation of Cryptographic Software Vulnerability Research
- 🟢 Exploring the gVisor Sandboxing Technology
- 🟢 Map your firmware with Pyrrha
- 🟢 Offensive RFID/NFC open-source tools development
We are also welcoming people with wide but realistic creativity, so if you have an idea and want to join the team, don't hesitate to reach out to discuss it with our experts!
Our goal is to publish most of the results of our internships. Here are some examples of publications from previous internships:
- A blogpost on Starlink's User Terminal internals;
- A Hardwear.io talk on breaking Secure Boot on the Silicon Labs Gecko platform;
- A Kubernetes penetration testing tool, named kdigger;
- A Black Hat EU talk on the Google Titan M chip;
- A blogpost on defeating eBPF uprobe monitoring.
Quarkslab's team is always pleased to welcome new talents who want to work on complex security research subjects. If you want to face new challenges and work in a dynamic environment where curiosity and teamwork are at the heart of our way to do R&D, please apply!
In particular, we would be more than happy to welcome more applications from female candidates, and under-represented minorities.
Quarkslab is dedicated to making the cybersecurity world more welcoming and inclusive for all, and that starts with our internships.
With that in mind, and because we know impostor's syndrome is a big obstacle for women in particular -- we've been there -- don't hesitate to reach out to us at icandoit-AT-quarkslab-DOT-com to discuss your skills, and we will help you navigate our offers.
To apply for an internship position, you must be a student, able to communicate effectively technical matters in written and spoken English, and willing to present the results of your internship to a large group of curious Quarkslab colleagues. Beforehand, you need to prepare the following elements:
- A resume;
- A cover letter: avoid the generic letter saying that you are so motivated and that we are so interesting. We welcome a more personal letter which explains why the topic is of particular interest to you, why you, and why us;
- Your proposed solution to the assignment attached to the offer you are interested in;
- Your preference between
pain au chocolatorchocolatine.
Package these elements and send them via email to internship-AT-quarkslab-DOT-com, with the subject field containing the internship name mentioned in the respective offer.
Do not forget that the key aspect of a good application is being curious and motivated, not meeting all requirements should not prevent you from sending us your application, and we can discuss your skills. Keep in mind that internships are done to learn. Let's go!
Each internship offer comes with a little assignment that should not require too much time to be completed. The result will show us not only the type of skills and knowledge you already possess, but also how ingenious you are and how well you can present your reasoning. It will serve as the basis for the interview you will have in the selection process. The assignment works both ways and is also intended to make sure that you like the topic as well as the technical aspects of the internship. If unsure about a specific aspect of a challenge, do not hesitate to drop us an email. We want to discuss not frustrate you!
The first applications usually reach us by November, and we start reviewing them right away. Every year, the filling is alike: half of the internships are filled by Christmas, while the others remain open until March.
Did you notice the colored circles next to the title of the offers at the top of this blogpost? They reflect the state of internships:
- 🟢 Waiting for applications;
- 🟠 Reviewing applications, we are still accepting internship assignments but hurry up;
- 🔴 Internship is filled.
We consider internships as opportunities to spot profiles that match how we work. They are intended to guide students to enter the professional world as potential future colleagues if they feel like it. We love interns because they bring fresh air to the company and because we see them grow, not only during the internship but also after, when they are hired and can get to work on so many other topics. There are two goals in every internship we offer:
- Exploring a topic we don't necessarily know very well, hence training the new expert on the topic;
- Hiring you after the internship to keep and share your new expertise with colleagues.
Training and growing people in the security industry is part of the company's DNA. That is why we provide in-depth blogposts, tools, trainings, weekly internal conferences (called Fridaycon, guess when they are), we teach in universities and schools, write articles in tech magazines and send our less experienced hires to a 6-month intensive training program (BADGE-RE or BADGE-SO). Sharing is caring, but sharing is also learning. We provide the environment for that the rest relies on you.
Intern package in France:
- Salary: €1800 gross per month (approximately €1550 net);
- "Tickets restaurant" (restaurant coupons);
- In-depth and challenging topics.
Automation of Cryptographic Software Vulnerability Research
Description
At Quarkslab, audits of cryptographic designs and implementations are a common practice. In order to facilitate the evaluation of the conformity of a crypto-system, we developed a tool to perform automatic conformity checks by the means of test vectors on the most common primitives. The goal of this internship is to enhance this tools with advanced features for deeper conformity checks and to build up internal corpus of test vectors for resiliency checks (as it is done is some other tools).
What you will do
The first step of the internship will consist in appropriating the ways of the tool by adding new primitives. Then, the candidate will start enhancing the tool with different features such as the following ones:
- Differential fuzzing of cryptographic implementations;
- Crafting of homemade test vectors for common primitives for resiliency checks;
- Detection of cryptographic primitives in native code;
- Different test on real-world examples;
- Other topics to be discussed.
Required Skills
- Knowledge of basic cryptography (e.g. asymmetric and symmetric crypto, and examples of such primitives);
- Somewhat proficient in at least one programming language (C, C++, Rust, Python...);
- Preferably capable of understanding academic articles and/or technical blogposts;
- Good communication skills.
Assignment
The assignment contains a C reference implementation of the AES with some mistakes. The goal is to perform a small review of the implementation and list different misbehavior compared to the original design. The focus of the candidate should be on the report more than on the technical solutions, as we are more interested in reviewing the thought process than the current technical skills.
File to download:
Location
- Paris
Duration
- 6 months
Exploring the gVisor Sandboxing Technology
Description
gVisor is an open-source Linux-compatible sandbox used to run user applications in container-like fashion. Similar to a container, it isolates the user applications from the host environment. However, the isolation mechanisms it uses are quite different. To some extent, they can be seen as similar to the ones used by virtual machines. In detail, gVisor is an application kernel, written in Go, which implements a substantial portion of the Linux system call interface. This way, it provides an additional layer of isolation between running applications and the host operating system compared to other common container technologies. gVisor includes an Open Container Initiative (OCI) runtime called "runsc" that makes it easy to work with existing container tooling such as Docker, Containerd and Kubernetes. gVisor’s approach is said similar to how User Mode Linux works but with a lower footprint on resource consumption.
What you will do
- Study gVisor’s architecture — a general overview of its different components (Sentry, Gofer, runsc), their software architecture and roles, how they interact with user applications and which each other;
- Understand how gVisor can be used in Kubernetes and by other container technologies;
- Study the advantages and disadvantages of gVisor compared to traditional container technologies;
- Define and implement an attack model suitable for gVisor;
- The results of you research will be shared among our peers.
Required Skills
- Desire to learn and dive into deep technical topics;
- Ability to explain, work in a team and share the knowledge with others;
- Good knowledge on container technologies (e.g.: Docker, Containerd, Runc, Podman, LXC, Kubernetes);
- A decent understanding of Go would be considered a plus.
Assignment
The assignment for this year’s internship involves four separate and independent challenges. Each one of them is validated with a separate proof of compromise (flag). You are provided with two Linux x86_64 virtual machines. On the VMs are installed the following services:
- A vulnerable Python Web application running inside a Docker container (VM1);
- A program written in Go running inside a Docker container. You’ll also be provided with the compiled binary which you’ll have to reverse engineer to get the flag (VM1);
- A badly configured Docker container which misconfiguration you’ll have to exploit (VM1);
- A Docker container running as a non-privileged user (user namespace) on a Linux VM. Your objective will be to escalate your privileges on the system and escape from the container (VM2).
With each challenge will be provided hints and external resources which will help you solve them. You don’t need to solve each one of them (however, the more, the better). Don't panic if you don't manage to solve all the challenges! What is important for us is how you reason and the way you tackle problems, hence we’re not interested in the flags that you’ve obtained. Don't hesitate to send us the solutions of the challenges that you did manage or tried to solve! In your solution, try to give as much detail as possible and provide us with clear explanations. Please include also the time that you've spent resolving the challenges.
Hint: Imagine that you’re sending it to people who are not experts in the challenge domains but have a decent understanding in security.
Location
- Paris
Duration
- 6 months
Map your firmware with Pyrrha
Description
Nowadays, structured firmwares can be a complete OS with thousands of files. It usually requires several hours to find the links between some components, and it is easy to get lost in this mass of information. At Quarkslab, we have combined and extended open-source solutions to solve this issue and help reversers in their daily tasks. The resulting tool, Pyrrha, allows users to visualize the different binaries and libraries of the firmware and their interactions in the form of several dependency graphs.
Pyrrha is an extension of Sourcetrail, an open-source code source explorer (for c/cpp, Python, and Java). This extension uses LIEF to analyze imports and exports of each library and binary of the firmware and create links between them. The result is exported as a sourcetrail database. Thanks to the Sourcetrail UI, the user will be able to navigate and search in the resulting firmware mapping.
What you will do
This internship's goal is to enhance Pyrrha's capabilities. As Pyrrha uses Sourcetrail, the first task will be to patch this tool to keep it working and to extend its functionality as it is an archived project. Then, you will improve the Pyrrha filesystem parser by adding new features. Finally, you will create a new parser to explore the code source of an already compiled binary.
Required Skills
- Good Python skills;
- C++ basics.
Assignment
This challenge goal is to create an unpacker for Android OTA update files as a Python package. The provided script challenge.py describes the required features of your module and provides hints on how OTA files can be unpacked. Your package should be able to extract at least the provided OTA file.
If you have any question regarding the understanding of the file format to extract do not hesitate to contact us, this challenge is done to evaluate your level in Python development not your ability to understand complex file formats.
Files to download:
- challenge.py
- OTA file (750 MB)
Location
- Paris
Duration
- 3 to 4 months
Offensive RFID/NFC open-source tools development
Description
For more than 15 years, the Proxmark3 has been the unbeatable Swiss army knife of 125 kHz and 13.56 MHz RFID hacking. Over these years, its software has accumulated a considerable amount of R&D and offensive features. But by today standards, its hardware (AT91SAM and xc2s30 FPGA) is aging and quite limited. A new open-source device based on a nRF52840, the Chameleon Ultra, has a great potential to cover the 125 kHz and the ISO14443A spectrums in a modern, fast-paced environment.
The goals of this internship are to develop a number of offensive features needed to be able to use the Chameleon Ultra as an effective Red Team tool. This involves getting intimately familiar both with the nRF firmware written in C and with the Python client.
This is your chance to experience the satisfaction of developing open-source tools beneficial for the entire infosec community, in close proximity with skilled colleagues having contributed to both projects since years, but also with external contributors.
What you will do
- Get familiar with various NFC/RFID security analysis techniques;
- Improve and add offensive functionalities in the firmware and in the client.
Required Skills
- Proficient in C and Python3;
- Preferably knowledgeable with embedded devices specificities;
- Capable of collaborating with other open-source contributors;
- Good communication skills;
- Prior interest/knowledge into RFID/NFC is highly recommended.
Assignment
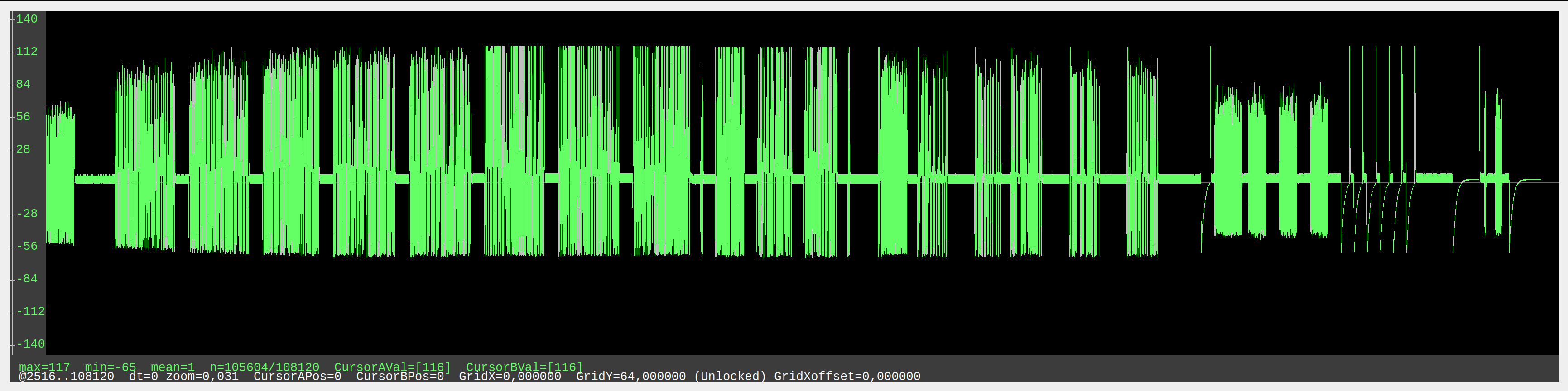
Write a Python script to decode as much as you can the RFID analog trace recorded in https://github.com/RfidResearchGroup/proxmark3/tree/master/traces/lf_sniff_blue_cloner_em4100.pm3, created by sniffing a "blue cloner" when it is writing an EM4100 ID on a T5577 tag and a EM4305 tag. You can use existing DSP/SDR libraries if it makes sense, but avoid huge frameworks. The expected modulations are the ones used to write to T5577 and EM4305 tags and their response, read the datasheets!
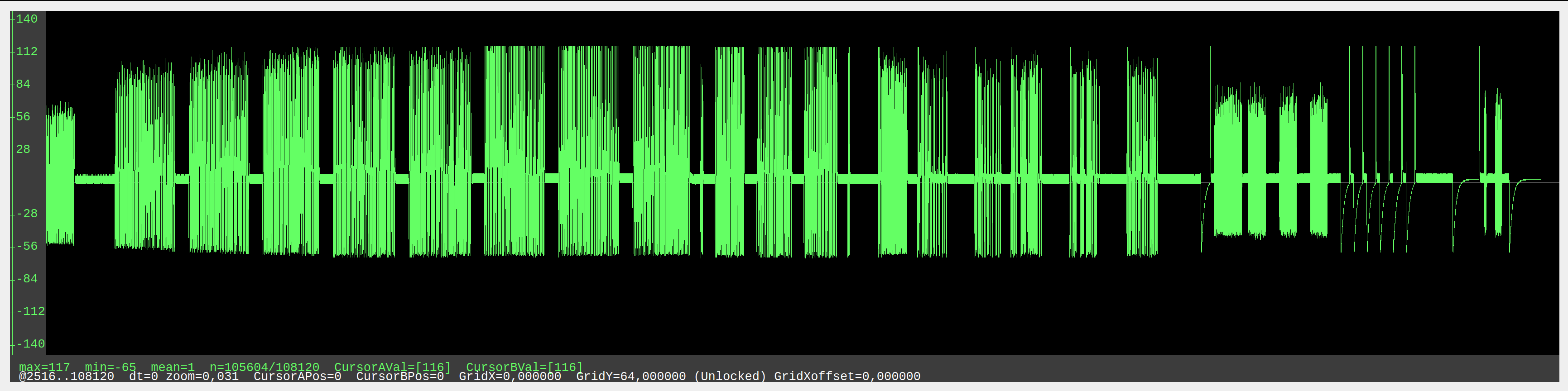
The trace visualization was obtained with the Proxmark client.
pm3 --offline -c 'data load -f lf_sniff_blue_cloner_em4100.pm3; data plot' -i
Location
- Paris
Duration
- 6 months
If you would like to learn more about our security audits and explore how we can help you, get in touch with us!
如有侵权请联系:admin#unsafe.sh