2023-10-16 21:28:15 Author: www.bitdefender.com(查看原文) 阅读量:12 收藏
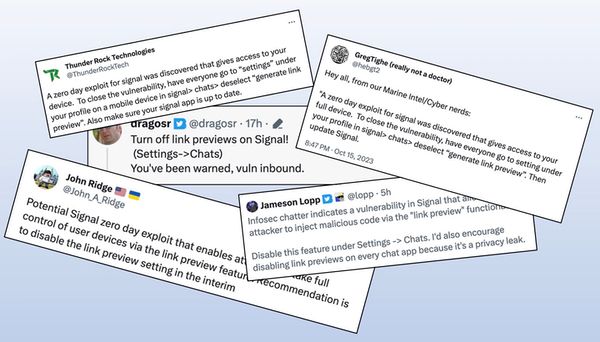
Over the weekend rumours circulated on social networks of an unpatched security hole in the Signal messaging app that could allow a remote hacker to seize control of your smartphone.
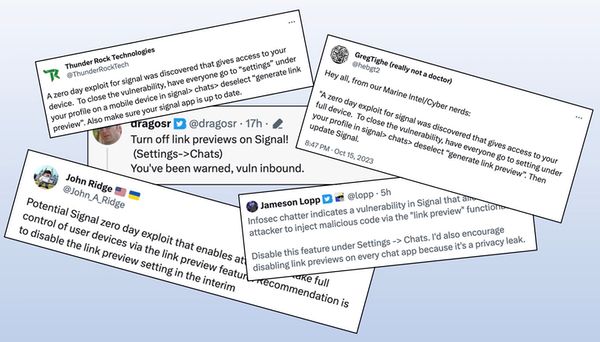
The rumours, which rapidly spread further than the cybersecurity community into the wider public, claimed that the Signal encrypted messaging app contained a flaw related to its "Generate Link Previews" feature that could be exploited by hackers.
As someone once said, a lie can travel halfway around the world before the truth has got its boots on. And the situation is even worse in the 21st century, where anyone has the power to post a claim on Twitter, and watch it be retweeted and reshared thousands and thousands of times before anyone takes the time to ask a difficult question.
Some people did bother to respond to the rumours, asking for more details or a source that would confirm there was an issue. Which seems quite reasonable. After all, an encrypted messaging app like Signal is used by privacy-conscious folks who want to keep their communications secret.
However, in the threads I saw online, anyone asking for more details of the so-called vulnerability were fobbed off with "I heard it from a trusted source" or vague references to unnamed individuals within the US government.
In short, there were no real details of a zero-day vulnerability having been found in Signal at all.
And the idea that the link preview feature of Signal might be linked to the alleged vulnerability seemed unlikely.
Although it's true that in the past other messaging apps have been found to reveal a user's location through preview links, it isn't the case with Signal.
Signal generates link previews (when the feature is enabled) before the link is sent to the other Signal user - not after.
In other words, disabling "link previews" in Signal (the advice being given in the erroneous warnings posted on social media) only prevents creation of link previews on your device, you are still able to receive them from others.
Earlier today, Signal posted a message on Twitter stating that it had seen no evidence that the vulnerability was real.
It went on to say that it had "checked with people across US Government, since the copy-paste report claimed USG as a source. Those we spoke to have no info suggesting this is a valid claim."
Signal's President, Meredith Whittaker, commented that "the vague and viral form of the report has the hallmarks of a disinfo campaign."
I don't know if the seemingly baseless rumours of a Signal flaw were begun maliciously or not, but it certainly is the case that Signal has plenty of enemies who would love to see its reputation tarnished.
Even if there isn't a zero-day vulnerability in Signal as the online rumours described, it still makes sense to practice safe computing, ensure that your privacy settings are configured as you expect them to be, and that you are ensuring that your apps are properly updated.
如有侵权请联系:admin#unsafe.sh