
read file error: read notes: is a directory 2023-10-14 07:0:10 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:137 收藏

Executive Summary
We present a study on why and how domain name system (DNS) tunneling techniques are used in the wild. Motivated by our findings, we present a system to automatically attribute tunneling domains to tools and campaigns.
Attackers adopt DNS tunneling techniques to bypass security policies in enterprise networks because most enterprises implement relatively permissive policies for DNS traffic. Previous research has shown that malware campaigns such as SUNBURST and OilRig use DNS tunneling for command and control (C2).
However, many aspects of how attackers use DNS tunneling in the wild remain unknown. For example, do they use DNS tunneling techniques exclusively for C2? How do they implement and host these techniques? Can we further analyze and provide actionable insights on DNS tunneling traffic?
We answer the above questions through over four years of experience in DNS tunneling traffic investigations and in-the-wild tunneling domain detections. We find that apart from threat actors using DNS tunneling techniques for C2 communication, enterprise employees are using them for censorship circumvention and vehicle passengers are using them to bypass network service charges.
Different tunneling domains share characteristics that can reveal the tools used to embed data onto DNS queries and responses – and the associated malware campaign name.
Therefore, we have built an attribution system called DNS Security System, which can gather information about the DNS tunneling traffic and provide details about the tools and the associated campaigns in real time.
Palo Alto Networks Next-Generation Firewall customers can access the tunneling tool and campaign information with DNS Security subscriptions.
Palo Alto Networks Next-Generation Firewall customers receive protections against malicious indicators (domain, IP) mentioned in this article via Advanced URL Filtering and our DNS Security subscription services.
Palo Alto Networks Cortex XDR analytics customers receive protection against DNS tunneling techniques mentioned in this article via the DNS tunneling analytics detector.
| Related Unit 42 Topics | DNS Tunneling, Cobalt Strike |
Table of Contents
DNS Tunneling Basics
Case Studies
DNS Tunneling as C2
DNS Tunneling as VPN Service
Attribution of Tools and Campaigns
Conclusion
Indicators of Compromise
Domains
IPs
Additional Resources
DNS Tunneling Basics
What is DNS tunneling? DNS tunneling is a technique to encode data of non-DNS programs and protocols within DNS queries and responses. This enables various types of communication over the DNS protocol, including file transfer, C2 and web browsing.
Why perform DNS tunneling? DNS normally uses UDP port 53, which is usually open on clients, systems, servers and firewalls to transmit DNS queries. DNS is a fundamental component of the internet. It serves many applications, from well-known services like web browsing and email, to lesser-known services like auto-discover, load balancing, censorship and security monitoring.
Due to its criticality, most enterprises implement relatively permissive policies for DNS traffic. Therefore, attackers are abusing the DNS protocol to tunnel C2 communications and retrieve malware payloads.
Well-known attack campaigns such as SUNBURST, OilRig, xHunt and DarkHydrus have employed DNS tunneling techniques. Permissive policies on DNS traffic allow attackers to reach the internet. The large amount of benign DNS traffic becomes a natural disguise for attackers to hide their footprint.
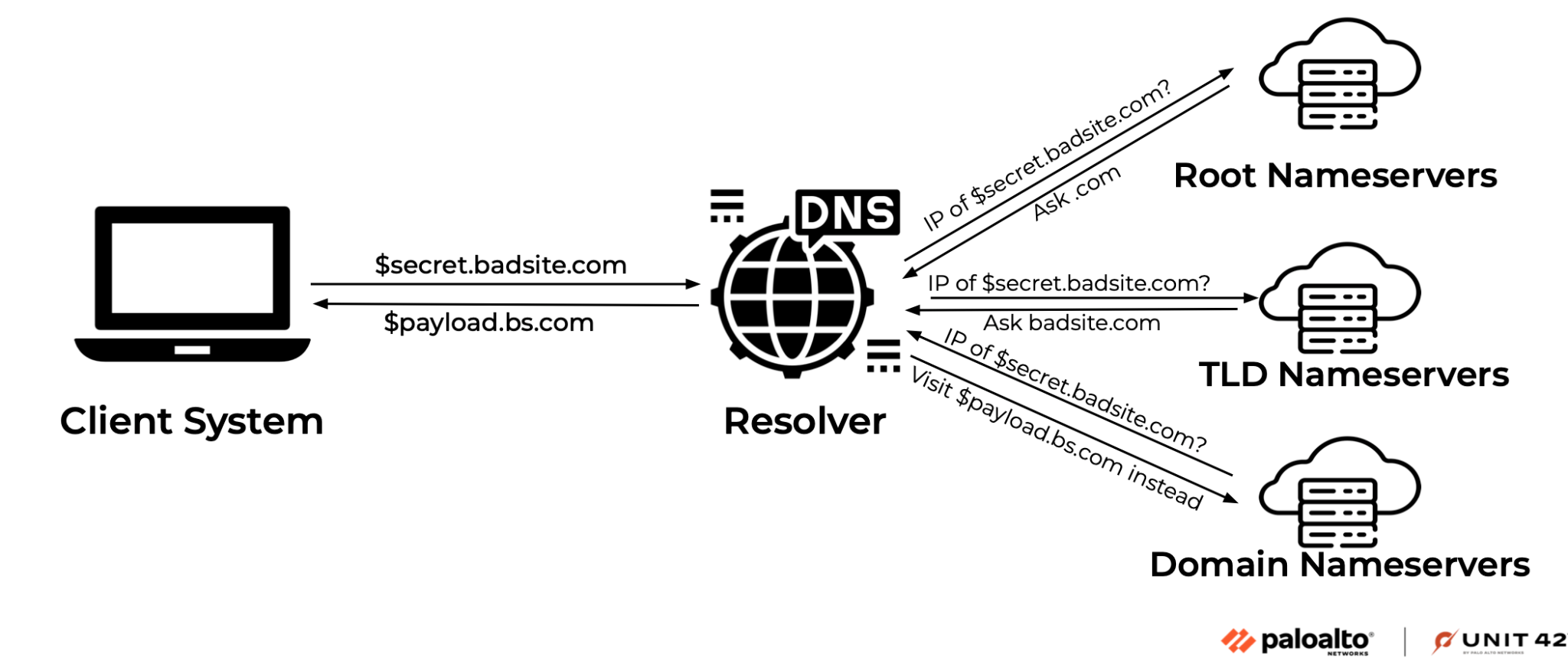
How DNS tunneling is performed: Two main components are needed to perform DNS tunneling: a client and a server. The client sends DNS packets to the internet, encodes content through DNS queries and decodes content from DNS responses. The server receives DNS queries from recursive resolvers, decodes content from DNS queries and encodes content as DNS responses.
Figure 1 illustrates this process at a high level. In this example, the client first encodes a secret value as the subdomain $secret and sends out the DNS query $secret.badsite[.]com. The resolver then iteratively queries nameservers of different domain levels until it gets a valid response. Figure 1 shows the server receiving and decoding the encoded value $secret. Optionally, the server component (domain nameservers) encodes a malicious payload as the subdomain $payload and sends out the DNS response: $secret.badsite[.]com CNAME $payload.bs[.]com.
The client component receives and decodes the encoded message $payload. If the secret value or the malicious payload exceeds the size of a single DNS packet, the client and server break them down and send them as multiple queries and responses.
Instead of sending raw data, an encoding algorithm is often used to encode and fragment the data. Virtually anyone can come up with an algorithm to perform the fragmentation.
Meanwhile, there are ready-to-use DNS tunneling tools, including open-source applications such as iodine, DNSStager, dnscat2 and sliver, as well as proprietary ones such as Cobalt Strike. These tools support encoding generic messages as subdomains of DNS queries and as various types of DNS responses, such as A (IPv4 address), AAAA (IPv6 address), TXT, CNAME and MX. Please see our previous post for a more detailed description of DNS tunneling.
Case Studies
The Palo Alto Networks DNS Security service has supported detecting DNS tunneling traffic since 2019. DNS tunneling detection uses machine learning to analyze the behavioral qualities of DNS queries, DNS responses and how domains are hosted.
We have accumulated four years of data in our efforts to detect in-the-wild DNS tunneling traffic. Our previous research shows that malware campaigns like SUNBURST, OilRig, xHunt and DarkHydrus have used DNS tunneling for C2 communications.
Our data also reveals other uses for DNS tunneling. To circumvent censorship measures in an enterprise environment, employees have employed virtual private network (VPN) services that utilize DNS tunneling techniques.
Individuals have also used DNS tunneling to bypass charges by internet providers for commercial transportation services like airplanes or cruise ships. Our research indicates that different tunneling domains share characteristics that can reveal the tools used to embed data onto DNS queries and responses and the associated malware campaign name.
Note that people can also use DNS tunneling for legitimate purposes – such as security monitoring. Cybersecurity vendors can leverage the permissive policies of DNS traffic and use DNS tunneling techniques to build easy-to-deploy communication channels. We can use these communication channels to perform real-time checks for files and domains, as well as monitoring honeypots residing in internal networks.
The following anonymized record is an example of such communications:
gqwtqmzxhaydimbvgyys2mrnmq6t2pj5.ovqs45lemuxhiy3bfz2gk3ttnrxw62ddomyt2pj5.con[...]per.io TXT "bsu1oaukzzdbehhbsrhaoebqsxvhrdukqavfrfafhbqlncvvdcs15hwawuebfccwuys0npurcnhbtox0wvfv0sfbtcauzpdbuqabdkehjm" |
Because enterprises usually approve such use cases, and because they can be identified and allowed on a per-case basis, we will not discuss them in detail. Meanwhile, it’s important to note that we obtained all the DNS queries and responses described in this article from third-party, passive DNS rather than from customers.
DNS Tunneling as C2
C2 is the most well-known use case for DNS tunneling. The same campaign can share characteristics such as common nameservers as C2 for communication or a common tunneling tool for encoding and decoding. We introduce examples from three campaigns: two we have identified, and one identified by the community.
Our first example is a campaign that has targeted one of our customers from the financial industry. We observed communications between 22 tunneling domains and the same customer.
These domains share seven nameserver IPs and use the same underlying encoding tool. The attackers also used domain names that imitate popular security or cloud vendors, hoping to evade detection.
A subset of these domains are as follows:
- panos[.]ltd
- ciscocloud[.]space
- ubrella[.]online
- msft[.]center
- mscd[.]store
- awsl[.]site
We list these domains together with their sample queries, nameserver domains and nameserver IPs in Table 1. Since this campaign targets a customer from the financial industry and uses the same underlying encoding tool that uses queries starting with a counter, we named this campaign FinCounter.
| Domain | Sample Query | Nameserver Domain | Nameserver IP |
| panos[.]ltd | 10.eff89fcf44a13186ad3765f35860ce19c722c4bcda6bbbae6b7bab6025b36d0.d036b5a3fd8b67e55ee35feff7d014fdb8d32afe93d5d6f05f1dda3a096e8fa.2e10d53e935549b3a081982724c3e6f806.oak.panos[.]ltd | bur.panos[.]ltd | 34.92.43[.]140 |
| ciscocloud[.]space | 10.a6674ae5d37cab7263074adef14925ef28698896b8491276097a470beca325a.669f12d4b31e9a6707ce2ee5b595cb723f40ea6d8e5f406b8fba874c8bec632.3299de58f43c3e4be80a7d7db2a2ed5aee9e13bac9cb.habit.ciscocloud[.]space | bram.ciscocloud[.]space | 34.92.43[.]140 |
| ubrella[.]online | 8.d4fee8aa63e4ee6435452f86e84464168e96e314eb1a19c45e0e76f3ca71b2a.e9476062765ba0aeaeea97333805f09470ff3bd103e3ce8bd3ffefa3dfea90f.369cd352a204e9662db180407f1d1b8fa87be97c81d1.feign.ubrella[.]online | rumor.ubrella[.]online | 34.92.43[.]140 |
| mscd[.]store | 4.a6gpmbnqbjewgwnqnlivwhleux4vnnyiuduyqgjkyn9jcihsttpdbdenf7lx8jx.jqhdulrejthsyipzvoleyvhv5s99nydtj5um8bzdmdms9gwdqnq46yis5hvbryo.dernuvjw7a6p6ndq4c8lwomsl7zq5lncgsutndxfpaufefhr7xxeuhfpk8hs.sny7htmpdpqdcumtgrmeptytbe9p78skry64.17328.fish.mscd[.]store | rug.mscd[.]store | 35.194.255[.]111 |
| awsl[.]site | 1.758fcd0ac2301084ef82efb047050ff5e7d45b4cd636b46e4292b67acac5ab0.a1644dfde400b8d41e7b6ec37338c45d34a8e9ed81173e8dffdf57ebb3c9e30.9fc12877d608dfca610d50a121acbd30b2450391c13a.mud.awsl[.]site | lkas.awsl[.]site | 35.194.255[.]111 |
| msft[.]center | 10.c5f310abb43603a3af324ee92bea16c8132ec2909fbca8d1036fe409d33af9b.c8c30e936bffb9f93bcba2c27682dcca1ab79aced6d1cf015a11d56a9c2f9f5.c49d8757a19b693d78d1772977cbf164e2748b57bb9f.ud.msft[.]center | 08e099da.msft[.]center | 34.81.65[.]4 |
Table 1. A subset of the domains used in the FinCounter campaign.
Our second example is a campaign targeting another financial industry customer. We have observed three tunneling domains targeting the same customer and using the same underlying tunneling-capable tool, Cobalt Strike. Representative characteristics of Cobalt Strike include using common prefixes such as www, post and api.
We have listed the three domains, identity-mgmt[.]com, internalsupport[.]info, cloud-enrollment[.]com, along with sample queries, nameserver domains and IPs in Table 2. Since the attackers try to evade detection by adopting domain names that look like supporting services, we named this campaign FinSupport.
| Domain | Sample Query | Nameserver Domain | Nameserver IP |
| cloud-enrollment[.]com | api.12abc2cb5.446f35fa.dns.cloud-enrollment[.]com | ns1.cloud-enrollment[.]com | 3.238.113[.]212 |
| identity-mgmt[.]com | intact.md.180.02d8f18d2.7e8986be.int.identity-mgmt[.]com | ns1.cloud-enrollment[.]com | 3.238.113[.]212 |
| internalsupport[.]info | icr.0325e18d8.16ae9fb2.pl.internalsupport[.]info | dn.internalsupport[.]info | 3.238.244[.]129 |
Table 2. The list of the domains used in the FinSupport campaign.
Our third example is the Decoy Dog campaign, which was reported by Infoblox in April 2023. We have detected tunneling activities using the same publicly reported domains, including the following:
- claudfront[.]net
- allowlisted[.]net
- hsdps[.]cc
These Decoy Dog domains share the same underlying tunneling tool Pupy, which uses the character 9 as padding when encoding data. Table 3 provides a subset of the domains used by the Decoy Dog campaign, along with sample queries, nameserver domains and nameserver IPs.
| Domain | Sample Query | Nameserver Domain | Nameserver IP |
| claudfront[.]net | fstz1yibfqnaw6mxpen3nknghh2q9999.1112umplhvbbzf2udr2rpuq9.claudfront[.]net | ns1.claudfront[.]net, ns2.claudfront[.]net | 5.252.176[.]63 |
| allowlisted[.]net | hs1t4lt2lb2ispy5ho4vmr5okvua9999.111b52v2e3ktuuyrn6j4xrq9.allowlisted[.]net | ns1.allowlisted[.]net, ns2.allowlisted[.]net | 83.166.240[.]52,
5.252.176[.]22 |
| hsdps[.]cc | gc2qagfacoq1zutfr61dko5mdjqa9999.1111suhsamuohkj4o4wn5qa9.hsdps[.]cc | ns1.hsdps.ns1[.]name, ns2.hsdps.ns1[.]name | 194.31.55[.]85 |
Table 3. A subset of the domains used in the Decoy Dog campaign.
DNS Tunneling as VPN Service
VPN service is a previously under-studied use case for DNS tunneling. Some VPN services utilize DNS tunneling to bypass firewall restrictions against VPNs in an enterprise environment. This type of DNS tunneling can also help users bypass service charges for internet access provided by commercial transportation services like airlines, buses or cruise ships.
These types of VPN services share characteristics with DNS tunneling for malicious C2 communications. These characteristics include a common nameserver for communication, or a common tunneling tool for encoding and decoding. To illustrate this, let's examine two popular VPN services and one tunneling tool adopted by multiple VPN services.
Astrill VPN is a popular VPN service that tunnels traffic using IPv6 (AAAA) queries and responses, and it uses a corpus of 49 tunneling domains to avoid being blocked. These domains are registered under different TLDs, including the following
- .com
- .net
- .pw
- .tech
- .top
- .space
Still, they all share the same nameserver IP addresses: 209.133.209[.]197 and 104.156.49[.]110. These are also pointed to by in01.astrill[.]com and in02.astrill[.]com, the official nameservers for Astrill VPN.
We have listed a subset of the domains used by Astrill VPN in Table 4, along with sample records, nameserver domains and nameserver IPs. The sample record is different from the sample query. A sample query only contains one field (i.e., the query), whereas a sample record contains three fields (the query, the response type and the response).
We frequently observe tunneling traffic from Astrill VPN in customers’ networks, indicating its wide adoption and potential abuse by employees to bypass corporate firewall restrictions on using VPN services. However, the real intentions of users can vary from unawareness of the underlying technology to active adoption of a DNS tunneling-based VPN service. An IT department can only identify and handle this on a per-case basis.
| Domain | Sample Record | Nameserver Domain | Nameserver IP |
| nanogardens[.]tech | 0g87sbvrbb8f79ee.s2bbv747ck53wp7k.s.nanogardens[.]tech AAAA 1327:fb85:793c:bda6:d571:841f:b240[:]1cb2 | s01.nanogardens[.]tech, s02.nanogardens[.]tech | 209.133.209[.]197, 104.156.49[.]110 |
| openair[.]pw | nq482xfw1zyq0vg5.ehadgy6qeq015w47.s.openair[.]pw AAAA aca9:8998:5018:1b61:fa26:b64f:77fb[:]a325 | s01.openair[.]pw, s02.openair[.]pw | 209.133.209[.]197, 104.156.49[.]110 |
| radiantsands[.]com | nq482xfw1zyq0vg5.ehadgy6qeq015w47.s.radiantsands[.]com AAAA a646:622:d647:539b:a780:21c9:eabe[:]1162 | s01.radiantsands[.]com, s02.radiantsands[.]com | 209.133.209[.]197, 104.156.49[.]110 |
Table 4. A subset of the domains used by Astrill VPN.
Similarly, HA Tunnel Plus is a popular VPN service that tunnels traffic using TXT queries and responses, and it uses only one tunneling domain (hat53[.]com). We frequently observe tunneling traffic under this domain from customers’ networks, including cruise lines, which indicates that passengers use VPN services to bypass network service charges.
The following is a sample TXT tunneling record:
t3f43builrjoxy5olfgijiryoi3vcabaabtq4byag2cqaad3emaaa3aaaaacsnn.5rhm62glydte5esgax5p57dwyygwfnszyvpc4s2euahvqeceqb6crq64lbq5fr6.4lwcok3fmou2bobxyv2v27u67oez35kt5suc7eek26ykoob32vizswowherp2vj.bv2cnzu3luktz7aplh2whj63kmd2tb5kse4rky3ag4r.ns-ca1.hat53[.]com TXT \\000\\024\\1628r7r\\000@\\000\\140\\014\\007\\0009\\133\\000\\000u\\133\\000\\000\\000\\000\\000\\000 |
To optimize its performance, HA Tunnel Plus uses multiple nameservers to serve tunneling traffic from different regions. For example, tunneling queries that are subdomains of ns-ca1.hat53[.]com are redirected to a Canadian nameserver a-ca1.hat53[.]com with IP 138.197.156[.]58. Tunneling queries that are subdomains of ns-de1.hat53[.]com are redirected to a German nameserver a-de1.hat53[.]com with IP 104.248.27[.]88.
We list more service countries in Table 5.
| Service Country | Subdomain | Nameserver Domain | Nameserver IP |
| Canada | ns-ca1.hat53[.]com | a-ca1.hat53[.]com | 138.197.156[.]58 |
| Germany | ns-de1.hat53[.]com | a-de1.hat53[.]com | 104.248.27[.]88 |
| Singapore | ns-sg1.hat53[.]com | a-sg1.hat53[.]com | 159.223.37[.]124 |
| United States | ns-us1.hat53[.]com | a-us1.hat53[.]com | 147.182.186[.]204 |
Table 5. A subset of the service countries of HA Tunnel Plus.
While VPN services can be individually identified and verified, different services can use the same underlying tunneling encoding and decoding tool. An example is dnstt, an open-source DNS tunneling tool used by several VPN services, such as the following:
Dnstt implements a protocol on top of DNS queries and responses, and it has security features such as encryption and authentication. Dnstt uses TXT record exclusively to encode data into DNS responses. In addition to the standard UDP, dnstt can also use DoH (DNS-over-HTTPS) and DoT (DNS-over-TLS) to provide privacy and evade detection.
Note that DNS Security Service can identify DoH and DoT resolvers and use the decryption feature to decrypt the payloads, allowing DNS tunneling detection to work seamlessly.
Table 6 includes example VPN services using the dnstt tool and their sample domain setups. Similar to HA Tunnel Plus, the listed services use multiple nameservers to serve tunneling traffic from different regions to optimize performance.
| VPN Service | Sample Domain | Sample Record | Nameserver Domains | Nameserver IPs |
| MinaProNet VPN | minapronetvpn[.]com | 6rpaviehgxyvpyy4ocbbxkiyv2zvcacaad4iw3qaxa3acahhuyaaaayaaaabo3z.2.dnstt-server.minapronetvpn[.]com TXT \\000\\024\\169\\024\\174\\179r\\000@\\000\\248\\139n\\000\\1866\\001\\000\\1846\\001\\000\\000\\000\\000\\000 | nl-server.minapronetvpn[.]com | 146.190.20[.]243 |
| ajph3r4dpholdyywl7fbxrsv4cofcacaab62iayaeynqaac2e4aaaayaaaahx6a.2.dnstt2-server.minapronetvpn[.]com TXT \\000\\024\\198u\\224\\156r\\000@\\000u\\164\\003\\000\\022\\027\\000\\000\\020\\027\\000\\000\\000\\000\\000\\000 | ws2-server.minapronetvpn[.]com | 104.248.142[.]17 | ||
| Edoztunnel VPN | dozapp[.]xyz | khvsoyur5pwo5yyz6wzeikuydeivcacaabgxiaaa74bqaad4amaaalaaaaagi4s.idfsuez5dmik2iuoywuf57fozubc2vw2e7jd4ioufzyvaumnhuceo5gznotvueq.ez4u.newca.dozapp[.]xyz TXT \\000\\024*\\152\\025\\017r\\000@\\000dt\\000\\000\\251\\003\\000\\000\\253\\003\\000\\000\\000\\000\\000\\000 | newcan.dozapp[.]xyz | 144.217.81[.]86 |
| 2no7jtyrhvomd2b6qdao4fkdb7ra.dnsau.dozapp[.]xyz TXT \\000\\024\\017a\\163\\209r\\000@\\000\\005\\000\\000\\000\\000\\000\\000\\000\\002\\000\\000\\000\\000\\000\\000\\000 | au.dozapp[.]xyz | 104.21.69[.]17 | ||
| TunnelCat VPN | tcat[.]site | n6s7qzzxy43m5y6qu6tibfphtc3vcabaacvfsaia2ibqaabcaaaaa2aaaaaoimg.e2w6epiijkqs73eyxui3w4vxxpvemn5zy5ikh5med7gisk35c6lnwgjjcoquoer.igvoe2ysqytgj4jfonfbkteyrkowecqtkoskugqgomq56vxvpsmmdm4j4fk2tuo.223tigunynencz4ak6743i5z7jyyrxgazv7m4.dns.de3-dnstt.tcat[.]site TXT \\000\\024\\149\\231\\152\\183r\\000@\\000\\169y\\001\\000\\208\\003\\000\\000\\209\\003\\000\\000\\000\\000\\000\\000 | de3-dnstt.tcat[.]site | 64.225.106[.]232 |
| hknjypabcykw3yznc4sb7ehanbufcabaactvsaaatebaaaheaaaaabyaaaaoo4n.22vtyimy.dns.dnstt-fast-de.tcat[.]site TXT \\000\\024\\144\\224hhr\\000@\\000\\167y\\000\\000\\152\\002\\000\\000\\153\\002\\000\\000\\000\\000\\000\\000 | dnstt-fast-de.tcat[.]site | 3.67.83[.]152 |
Table 6. Example VPN services using the dnstt tool.
Attribution of Tools and Campaigns
Since various tools use tunneling domains for different purposes, IT departments need more information on these domains to decide if they need to block them. For example, if an IT department encounters tunneling traffic from TunnelCat VPN in its enterprise network, this could be caused by an employee trying to circumvent firewall restrictions. They can warn the employee, or leadership can reinforce the organization's policy on best security practices.
If the VPN traffic is found within a cruise ship’s network, this is potentially because a passenger is trying to bypass service access charges, and the traffic should be blocked. However, if tunneling traffic matches the FinCounter campaign, enterprise IT departments can choose to isolate the compromised hosts and conduct a thorough investigation to understand the impact of the attack.
Tunneling traffic toward VPN services and C2 domains is different not only because of the implied intentions, but also because of the implied capabilities. First, VPN services require users to install an app that is vetted by marketplace maintainers, and which will authenticate that they’re using the right VPN server. While it’s possible to proxy malicious traffic through VPN servers, it does incur a higher engineering and financial overhead. Second, C2 domains don’t have such overhead and are highly customizable.
To this end, based on our insights into tunneling domains, we have implemented an attribution system that analyzes tunneling domains in real time to detect corresponding tools and campaigns.
The key idea is to extract characteristics unique to different tools and campaigns from tunneling domains including the following:
- How tunneling domains are hosted
- How data is encoded into queries and responses
- How and when data is transmitted
- Auxiliary information, such as who is being targeted and third-party verdicts about these domains
We have created a labeled dataset containing over 50 tunneling tools and campaigns and over 1,000 tunneling domains. Our system compares newly detected tunneling domains against the labeled ones using the aforementioned characteristics to automatically predict if a newly encountered domain belongs to an existing campaign or uses a known tunneling tool.
Table 7 lists examples of attributed tunneling tools and campaigns by the system. Rcsmf100[.]net is attributed to the Decoy Dog campaign mainly because it uses the same nameserver IP 83.166.240[.]52 as the domain allowlisted[.]net. On the other hand, hammercdntech[.]com and todoreal[.]cf are attributed to Cobalt Strike and dnstt respectively, because they reused the encoding tool.
| Domain | Sample Query | Nameserver Domain | Nameserver IP | Attribution |
| rcsmf100[.]net | tjkrwmhdoj5ctmtatfsvfnnwfeva9999.1125de632ujq9999.rcsmf100[.]net | ns1.rcsmf100[.]net, ns2.rcsmf100[.]net | 83.166.240[.]52 | Decoy Dog |
| hammercdntech[.]com | d-1ox.2cd649aed1f5ab311b08dce2066589388e395e9f0c0e85c940b37f209.b24afc9b030682dac90e4f83acc913711b68b056601e00e8778c4040.17f1d6e11.370935f6.ns1.hammercdntech[.]com | cdn7ad6a01b.hammercdntech[.]com | 65.20.73[.]176 | Cobalt Strike |
| todoreal[.]cf | bcm74mohxicvfy77u2zte2whzjjveacaadnj5nb6hubaaaceaiaaaaaaaaagvr6.kkniqaqaa2nlqeahpaiaaaracaaaaeaaaaaazy.slowdns.todoreal[.]cf TXT \\000\\024j\\199\\202sr\\000 \\000\\211w\\002\\000\\239\\002\\000\\000d\\004\\000\\000\\000\\000\\000\\000 | dns.todoreal[.]cf | 172.67.136[.]96 | dnstt |
Table 7. Examples of attributed tunneling tools and campaigns.
Conclusion
People are actively using DNS tunneling for various purposes, including well-known C2 servers and less-known VPN services. Detecting and understanding DNS tunneling can help protect Palo Alto Networks customers. Therefore, we have built a real-time attribution system to identify the underlying tools and associated campaigns for tunneling domains to provide more insights, allow fine-grained analysis and fast incident response.
Palo Alto Networks Next-Generation Firewall customers receive protections against malicious indicators (domain, IP) mentioned in this article via Advanced URL Filtering and our DNS Security subscription services.
Palo Alto Networks Cortex XDR analytics customers receive protection against DNS tunneling techniques mentioned in this article via the DNS tunneling analytics detector.
Palo Alto Networks has shared our findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Domains
- panos[.]ltd
- ciscocloud[.]space
- ubrella[.]online
- mscd[.]store
- awsl[.]site
- msft[.]center
- cloud-enrollment[.]com
- identity-mgmt[.]com
- internalsupport[.]info
- claudfront[.]net
- allowlisted[.]net
- hsdps[.]cc
- rcsmf100[.]net
- hammercdntech[.]com
IPs
- 34.92.43[.]140
- 35.194.255[.]111
- 34.81.65[.]4
- 3.238.113[.]212
- 3.238.244[.]129
- 5.252.176[.]63
- 83.166.240[.]52
- 5.252.176[.]22
- 194.31.55[.]85
- 65.20.73[.]176
Additional Resources
- DNS Tunneling Archives — Unit 42, Palo Alto Networks
- SolarStorm Timeline: Details of the Software Supply-Chain Attack — Unit 42, Palo Alto Networks
- DNS Tunneling: how DNS can be (ab)used by malicious actors — Unit 42, Palo Alto Networks
- xHunt Campaign: Newly Discovered Backdoors Using Deleted Email Drafts and DNS Tunneling for Command and Control — Unit 42, Palo Alto Networks
- xHunt Campaign: New PowerShell Backdoor Blocked Through DNS Tunnel Detection — Unit 42, Palo Alto Networks
- OilRig Targets Middle Eastern Telecommunications Organization and Adds Novel C2 Channel with Steganography to Its Inventory — Unit 42, Palo Alto Networks
- DNS Tunneling in the Wild: Overview of OilRig’s DNS Tunneling — Unit 42, Palo Alto Networks
- DarkHydrus delivers new Trojan that can use Google Drive for C2 communications — Unit 42, Palo Alto Networks
- Cobalt Strike Analysis and Tutorial: Identifying Beacon Team Servers in the Wild — Unit 42, Palo Alto Networks
- Dog Hunt: Finding Decoy Dog Toolkit via Anomalous DNS Traffic — Infoblox
- dnstt – DoH- and DoT-capable DNS tunnel — Bam Software
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh