2023-10-13 21:0:0 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
By: Robert O’Callaghan
A method of communication that remains important in our modern world is that of the voice message. The PDC recently observed a phishing campaign where threat actors included an access key in the body as a way to entice the user to access the voice message that had been left for them to review.
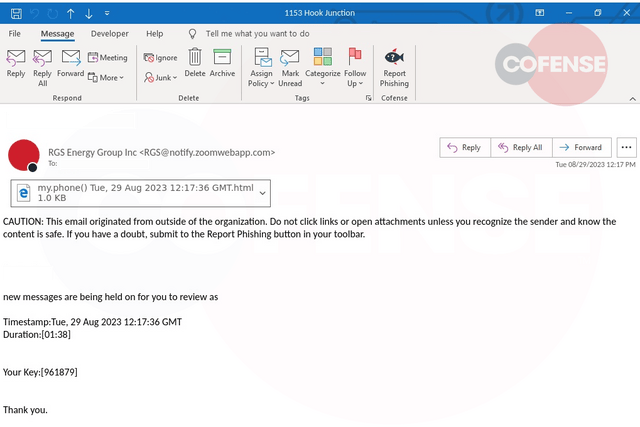
In Figure 1, we can see the email notifying the user of the messages available.
We note the use of a Zoom-esque domain. The attachment, which includes the date in the name, is an HTML file that will act as the first stage of the attack. The convincing aspect of this stage of the attack is the use of the access key. It is an attempt by the threat actors to personalize the email for the user.
Techniques like this are used to convince victims of the safety of the message and to access the message waiting for them securely.

Figure 1
Opening the attachment displays a page which requests the user to view a message as seen in Figure 2. It displays the same Access Key mentioned in the email as a way to confirm the legitimacy of the message to the user.

Figure 2
Once the link is clicked a prompt appears asking for the access key previously mentioned, as seen in Figure 3. The actual purpose of this input is to engage the user to allow for another download to occur.

Figure 3
Having provided the access key and following a few standard captcha checks a file is finally downloaded. One thing to watch out for also is the URL used to host the download here. It is an AWS URL disguised as though it were a legitimate Zoom URL.
This is not dissimilar to using Zoom as a novice user. If a meeting URL for Zoom is interacted with it can result in a fresh installation of Zoom. The download confirmation is displayed through Figure 4.

Figure 4
Following the download, the page redirects to the legitimate Zoom page to help the campaign seem more legitimate. When the downloaded file is opened, the user is presented with a badly rendered Microsoft-themed login page as seen on Figure 5.
However, it seems to indicate Outlook and Teams are the platforms being spoofed. The lack of consistency, where the threat actor began by impersonating Zoom but now attempts to gather credentials via an Outlook/Teams login page should raise a red flag with the user.

Figure 5
The user email address is pre-populated so the malicious actor is only looking for the password entry. This input is asked for twice as per a usual technique to help the malicious actor to confirm the password has been typed correctly. From here the page redirects to a looping animation of the outlook symbol.
Voice Phishing Conclusion
There are enough red flags within this campaign to raise suspicion early on, but there are some elements here that may fool unsuspecting users.
Be wary of the use of suggested access keys to access any messages, although not a common approach they can appear convincing.
如有侵权请联系:admin#unsafe.sh
