
2023-10-12 22:41:57 Author: www.sentinelone.com(查看原文) 阅读量:23 收藏
In September 2023, automation and manufacturing company Johnson Controls was targeted in a ransomware attack where threat actors used Dark Angels ransomware to lock the company’s VMWare ESXi servers. SentinelOne has analyzed the binary related to this attack and found that it has considerable overlap with RagnarLocker’s ESXi version.
In this post, we present technical details of the Dark Angels ransomware, offer a comparative analysis of Dark Angels and RagnarLocker samples, and provide recommendations for security teams safeguarding ESXi servers.

Overview
RagnarLocker is a ransomware group that was active throughout 2020 to 2022, drawing attention from the United States Federal Bureau of Investigation (FBI) for targeting entities in the critical manufacturing sector.
Dark Angels is a relative newcomer first reported in 2022 for its Windows version, which was very closely linked to the leaked Babuk Windows source code. Interestingly, our analysis finds the ESXi version of Dark Angels shares no significant overlap with the leaked Babuk ESXi locker source code, which many Linux ransomware families are based on or adapted from.
Technical Details
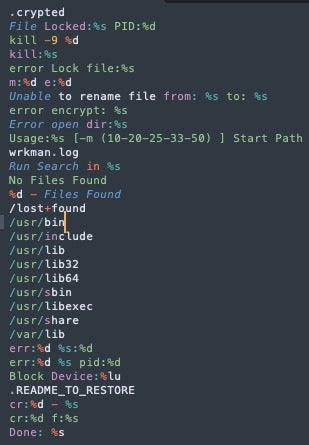
Dark Angels (06187023d399f3f57ca16a3a8fb9bb1bdb721603) is a 64-bit Executable & Linkable Format (ELF) binary designed for Intel-based Linux systems. On execution, the program logs the encryption progress to the hardcoded log file name, wrkman.log, which is saved to the directory that the Dark Angels binary is run from.
The program requires the operator to specify a root directory for file encryption to start, which will then process any subdirectories. Dark Angels takes optional arguments, which are documented internally as dl:m:s:v.
The -m argument lets the operator specify how many encryption threads to run concurrently, which can be 10, 20, 25, 33, or 50. The -v argument enables verbose logging mode to the command line. The -l argument lets the actor specify a log file name for the progress log.
During analysis, we observed that Dark Angels wrote a ransom note for each file encrypted; normally, ransomware writes one ransom note per directory where files are processed for encryption. The ransom note naming convention is <encrypted_file_name>.crypted.README_TO_RESTORE.
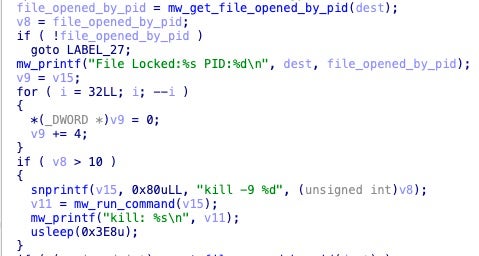
Dark Angels uses AES with a 256-bit key to encrypt files. The encryption routine can override a locked file by obtaining the PID of the locking process, then running the kill -9 command against that PID to terminate the process. This code will only execute if the PID value is greater than 10, which prevents the binary from attempting to kill files locked by crucial, kernel-interfacing processes.
Dark Angels vs. RagnarLocker
We identified considerable similarities between the Linux version of Dark Angels and a RagnarLocker binary circa 2021, 5411d7905bef69cb16d44f52fc46aa32fd922c80. From the file metadata perspective, both binaries are roughly 150 KB in size and designed for Intel x86-64 architectures. They also share the same compiler string compilation artifact: GCC: (GNU) 4.8.5 20150623 (Red Hat 4.8.5-44).
Dark Angels and RagnarLocker use the same encryption mechanism (AES-256) and the same file extension, .crypted. This is notable because the Windows version of RagnarLocker uses a bespoke file extension, RGNR_<victim_id>. The Dark Angels Windows version uses the .crypt extension.
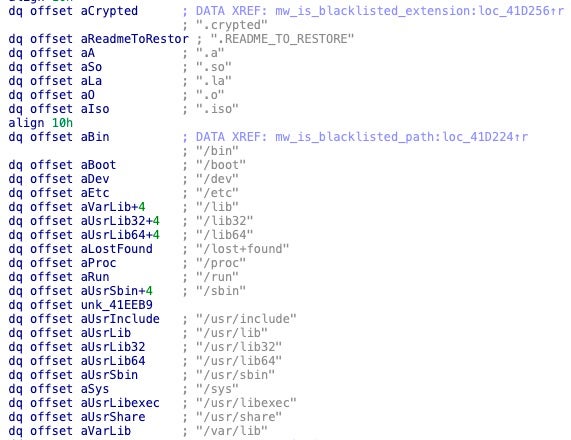
Both ransomware families share the same file path exclusion list, which ensures critical system files are not encrypted. Dark Angels’ extension exclusion list also includes the ransom note name, .README_TO_RESTORE, which is not present in RagnarLocker.
RagnarLocker also writes the same log file, wrkman.log. The RagnarLocker binary only takes the threading argument with the same -m flag, as outlined in its usage message.
Usage:%s [-m (10-20-25-33-50) ] Start Path
Other optional arguments seen in Dark Angels are not present in RagnarLocker.
The overlap between the two families is further solidified with analysis of a sample of Dark Angels ransomware observed in September 2022. Sample 7c2e9232127385989ba4d7847de2968595024e83 is highly similar to the 2023 Dark Angels sample 06187023d399f3f57ca16a3a8fb9bb1bdb721603 described above.
At the surface level, we see the same wrkman.log file being used and the same -m parameter supported, but that is the only argument available, other than supplying a starting path.
The .crypted extension is also used along with the previously observed README_TO_RESTORE filename.
However, the 2022 sample directs victims to a different .ONION address, qspjx67hi3heumrubqotn26cwimb6vjegiwgvrnpa6zefae2nqs6xqad[.]onion.
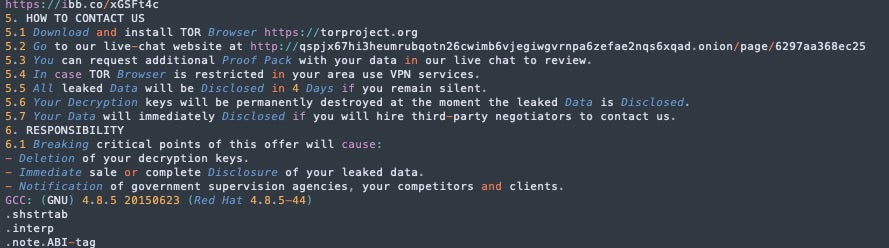
When this payload was first reported that address was inactive and remains so at the time of writing. In contrast, the 2023 variant directs victims to lyoevnzm3ewiq6jeyyuob2wfou7gh47yotuucsrwlf6ju3xrw43wacad[.]onion for live-chat/support and uses p66slxmtum2ox4jpayco6ai3qfehd5urgrs4oximjzklxcol264driqd[.]onion as the victim leak site. p66slxmtum2ox4jpayco6ai3qfehd5urgrs4oximjzklxcol264driqd is the historic Dark Angels Team-hosted “Dunghill Leak” site.

Also of note, the 2023 variant changed the hosting method for proof-packs (proof or evidence of leakage), using the victim(s) password-protected ufile[.]io links.
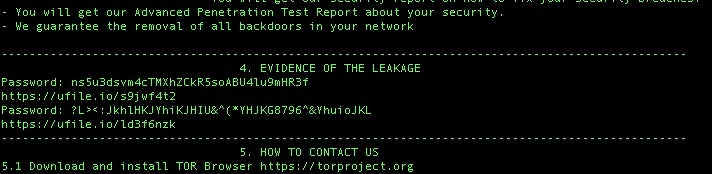
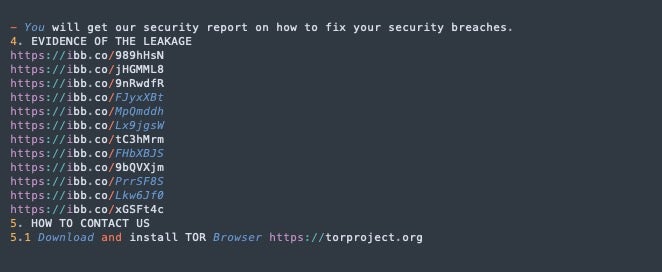
The 2022 variation uses simple, unsecured image links to image sharing service ibb[.]co.
Recommendations
Endpoints running the SentinelOne agent are protected against the Dark Angels and RagnarLocker Linux variants. Organizations can prepare for attacks from groups like Dark Angels by implementing a robust vulnerability & patch management program, as previous reports indicate the group leverages vulnerabilities to achieve initial access before pivoting deeper into the environment.
Given the lack of security software on ESXi hypervisors, consider enhanced network monitoring for unusual access to these systems, including internal system traffic. When possible, focus on large or abnormal data transfers off of the ESXi server as well as other file storage services within the network.
Conclusion
ESXi lockers continue to prove successful for the ransomware groups who use them, yet the overall pool of unique Linux ransomware families remains narrow. We assess with high confidence that these two samples are related and that the Linux version of Dark Angels is a very lightly modified, more recent version of the analyzed RagnarLocker binary.
There is a potential caveat to attributing Dark Angels as the next iteration of RagnarLocker when vendors miscategorize information or fail to thoroughly explain connections made through their analysis. For example, the RagnarLocker binary was classified as RagnarLocker by Fortinet, but listed as a Vice Society file by another vendor, Quorum Cyber.
Based on the volume of VirusTotal community comments for the RagnarLocker binary, our assessment aligns with contributions from earlier researchers.
Indicators of Compromise
| 06187023d399f3f57ca16a3a8fb9bb1bdb721603 | Dark Angels ELF binary (2023) |
| 5411d7905bef69cb16d44f52fc46aa32fd922c80 | RagnarLocker ELF binary (2021) |
| 7c2e9232127385989ba4d7847de2968595024e83 | Dark Angels ELF (2022) |
如有侵权请联系:admin#unsafe.sh