2023-10-12 03:8:12 Author: securityboulevard.com(查看原文) 阅读量:2 收藏

Introduction
Welcome to 2023, a year that promises to be pivotal in the realm of cybersecurity. As we navigate an increasingly digital world, the need for robust cybersecurity frameworks has never been more urgent. One such framework that stands out is the NIST Cybersecurity Framework, a comprehensive guide designed to help organizations manage and mitigate cybersecurity risks. In this guide, we’ll delve into why these elements are essential and implementing them in your cybersecurity framework.
Our timeline graphic above walks you through the evolution of this framework, from its inception in 2014 to its latest updates in 2023, including the much-anticipated NIST CSF 2.0.
Why Implementing the NIST Cybersecurity Framework is Crucial in 2023
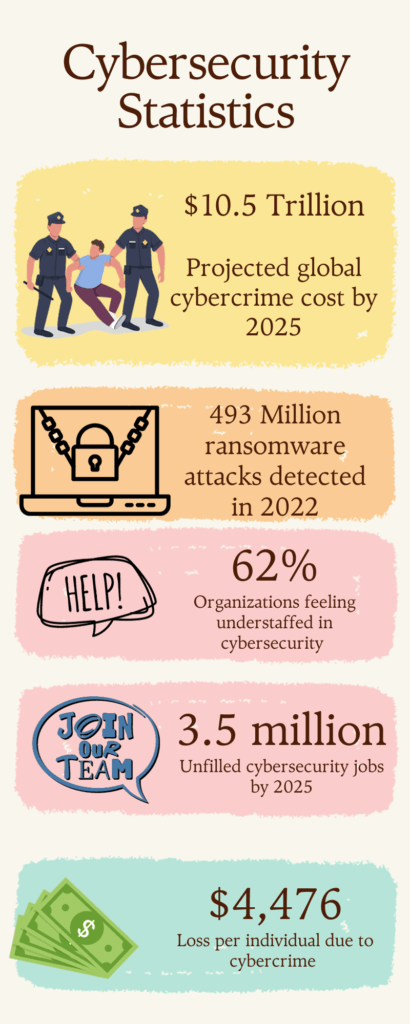
In 2023, the cybersecurity landscape is more treacherous than ever. As our infographic illustrates, global cybercrime costs are projected to reach $10.5 trillion annually by 2025. Ransomware attacks alone accounted for 493.33 million incidents in 2022. These alarming statistics underscore the urgent need for robust cybersecurity measures.
Enter the NIST Cybersecurity Framework. This framework is not just a set of guidelines but a comprehensive strategy for organizations to defend critical infrastructure, disrupt threat actors, and invest in resilience.
- Identify Risks: The NIST Framework helps organizations identify cybersecurity risks to systems, assets, and data.
- Protect Assets: It provides a systematic methodology for protecting sensitive data and systems.
- Adaptability: The latest version, CSF 2.0, is designed to be adaptable, allowing organizations to leverage other technology frameworks and standards.
In a world where 62% of organizations feel understaffed in cybersecurity, implementing the NIST Framework is not just advisable; it’s crucial.
Understanding the Core Components of the NIST Framework
The Core
The Core of the NIST Framework serves as the foundation and is divided into three parts: Functions, Categories, and Subcategories. It provides a set of desired cybersecurity activities and outcomes.
Implementation Tiers
Implementation Tiers help organizations understand their current cybersecurity posture. These tiers are broken down into three main components: Risk Management Processes, Risk Management Program, and External Participation.
Profiles
Profiles are unique to each organization and serve as a roadmap for reducing cybersecurity risks. They align the Framework’s Core functions with the organization’s specific requirements, risk tolerance, and resources.
Core Functions: Identify, Protect, Detect, Respond, Recover
The NIST Cybersecurity Framework is a pivotal guide for organizations aiming to bolster their cybersecurity measures. It is structured around five core functions: Identify, Protect, Detect, Respond, and Recover. These functions serve as the backbone for effective cybersecurity management. The functions are designed to help organizations spot, manage, and counter cybersecurity events promptly.
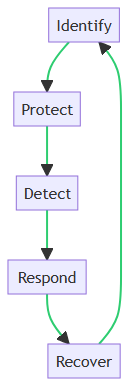
Identify
The “Identify” function serves as the foundation of the framework. It involves recognizing the assets, systems, and data that need protection. This is crucial for laying the groundwork for effective risk management and cybersecurity planning.
Protect
The “Protect” function aims to safeguard the identified assets. It involves implementing security measures to ensure that essential services are secure. Doing so can reduce the impact of potential cybersecurity events.
Detect
The “Detect” function focuses on monitoring and timely identification of cybersecurity events. It enables organizations to quickly detect anomalies and take immediate action, thereby minimizing potential damage.
Respond
The “Respond” function outlines the actions to be taken once a cybersecurity event is detected. This includes steps for containment, eradication, and recovery, aiming to minimize the impact and prevent further damage.
Recover
The “Recover” function is the final step in the framework. It focuses on restoring and validating system functionality for business operations to resume. It also involves learning from the incident to prevent future events.
Implementation Tiers: What Are They?
The NIST Cybersecurity Framework employs a tiered approach to help organizations manage cybersecurity risks effectively. These tiers are not maturity levels but rather represent different degrees of framework adoption. Let’s delve into the four implementation tiers and how they differ.
Tier 1: Partial
In Tier 1, organizations operate without a formal plan for cybersecurity. Their approach to risk management is reactive and case-by-case. There’s no overarching strategy, making their cybersecurity posture weak.
Tier 2: Risk-Informed
Organizations in Tier 2 are aware of cybersecurity risks but lack standardized procedures. While they recognize the need for managing risks, the awareness is not company-wide, leading to inconsistent practices.
Tier 3: Repeatable
Tier 3 organizations adopt a more structured approach, complete with developed and implemented procedures for managing cybersecurity risks. These include incident response plans and regular security assessments. This tier represents a more organized and repeatable strategy for tackling cybersecurity challenges.
Tier 4: Adaptive
Moving on to Tier 4, it is distinguished by an adaptive and continuously improving approach to cybersecurity risk management. Organizations in this elite tier proactively adapt their strategies in response to new incidents, emerging threats, and evolving business needs.
In summary, each tier serves as a roadmap, guiding organizations to pinpoint their current standing. Further, each tier set targets for bolstering their cybersecurity posture.
Profiles: Tailoring the Framework to Your Needs
In the context of the NIST Cybersecurity Framework, Profiles serve as a valuable tool for customizing the framework according to an organization’s specific needs, risk appetite, and objectives. Unlike the one-size-fits-all approach, Profiles allow for a more nuanced application of the framework’s core functions—Identify, Protect, Detect, Respond, and Recover.
Customization and Alignment
Profiles enable organizations to align their cybersecurity activities with their business requirements, risk tolerances, and resources. By doing so, they can prioritize actions based on their unique circumstances.
Gap Analysis
Using Profiles, organizations can perform a gap analysis between their “Current” and “Target” profiles. This helps in identifying areas that require improvement and allocating resources more effectively.
Communication
Profiles also facilitate better communication among different stakeholders within an organization. They serve as a common language that can be understood by both technical and non-technical personnel, thereby fostering a more cohesive approach to cybersecurity.
Regulatory Compliance
For organizations that need to adhere to specific regulations or standards, Profiles can be tailored to include those requirements. This ensures that compliance is integrated into the cybersecurity strategy, rather than being an afterthought.
In summary, Profiles offer a flexible way to adopt the NIST Cybersecurity Framework, making it easier for organizations to manage cybersecurity risks in a manner that is most relevant to them.
Step-by-Step Guide to Implementing the NIST Cybersecurity Framework
This section is designed to provide you with a structured approach to enhance your organization’s cybersecurity posture. We’ll walk you through each phase of the NIST Framework, from understanding its components to practical implementation steps. Whether you’re a small business or a large enterprise, this guide aims to offer actionable insights for improving your cybersecurity risk management. A visual roadmap may be useful here to outline the steps involved.
Step 1: Goal Setting
Setting clear objectives is the cornerstone of implementing the NIST Cybersecurity Framework effectively. Goals serve as the roadmap, guiding your organization through the complex landscape of cybersecurity. They help in prioritizing tasks, allocating resources, and measuring success.
Without well-defined objectives, your cybersecurity efforts can become disjointed, leading to vulnerabilities. Goals should align with your organization’s overall business strategy and cybersecurity risk management strategy, ensuring that you’re not just checking boxes but making meaningful improvements to your security posture.
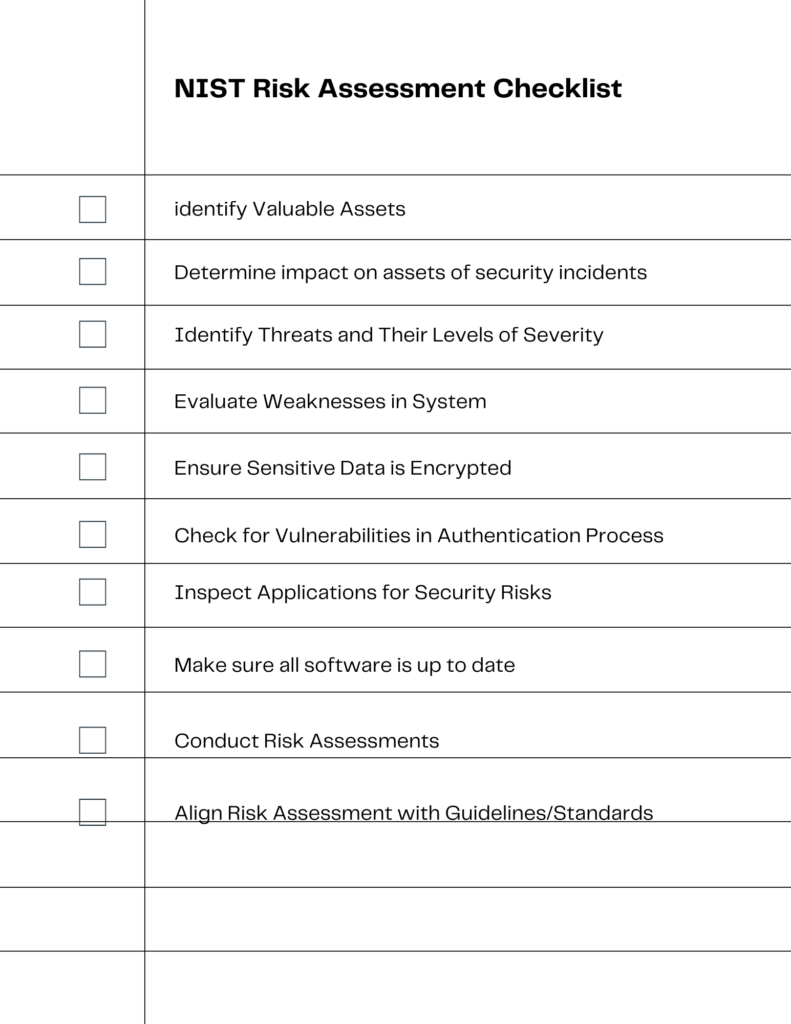
Step 2: Risk Assessment
In this step, prioritizing and scoping are crucial for effective risk assessment. Utilize the checklist visual as a roadmap to guide you through this process.
Tools for Risk Assessment
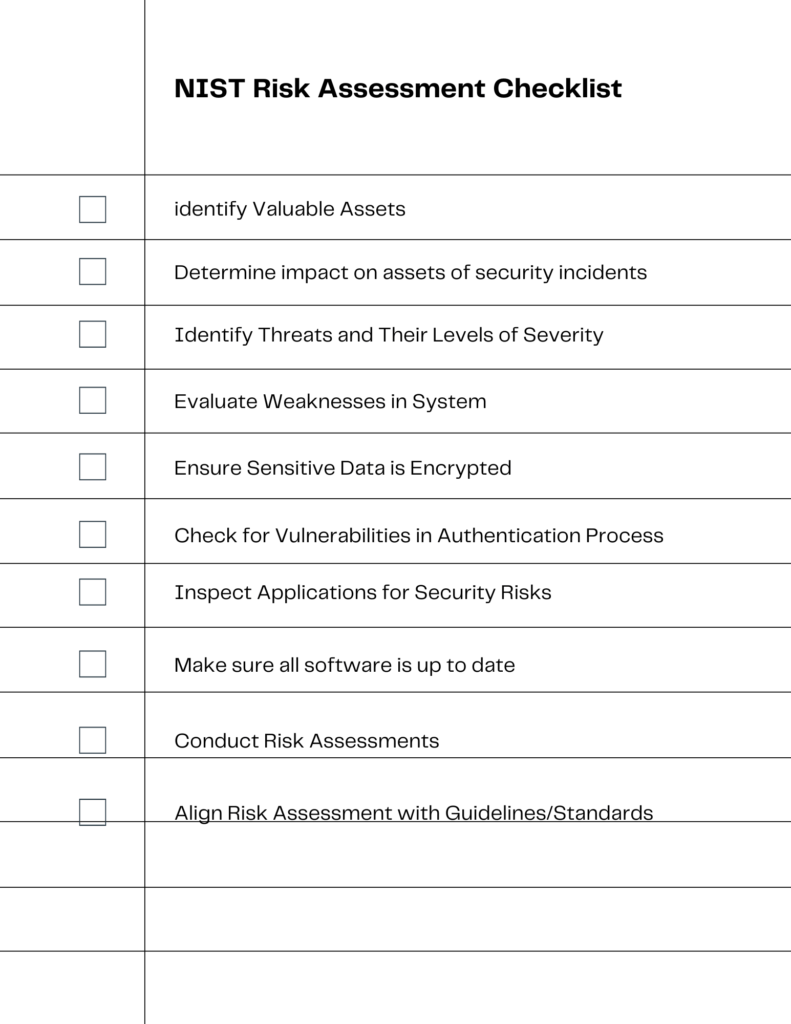
- Risk Assessment Software: Automated tools can streamline the assessment process by identifying vulnerabilities and calculating risks.
- Templates and Checklists: Use standardized forms like the one in the visual to ensure you don’t miss any critical areas.
- Hazard Identification Checklists: These lists help in recognizing all potential hazards during the assessment.
Methods for Risk Assessment
- Qualitative Analysis: This involves categorizing risks into levels such as low, medium, and high.
- Quantitative Analysis: Here, numerical values are assigned to risks for a more precise evaluation.
- Hybrid Analysis: A combination of both qualitative and quantitative methods for a comprehensive view.
The visual checklist serves as a foundational guide, ensuring that you cover all the bases from identifying valuable assets to using industry best practices.
Step 3: Creating Your Profile
In Step 3, crafting a profile that’s tailored to your needs becomes crucial for executing a targeted cybersecurity strategy. Initially, you should conduct a comprehensive inventory of your existing cybersecurity measures.
Then, seamlessly align these measures with the NIST Framework’s core functions, which are: Identify, Protect, Detect, Respond, and Recover. Doing so will effectively help you pinpoint gaps and highlight areas that need improvement. Importantly, remember that your profile isn’t merely a one-time setup; rather, it serves as a dynamic tool that evolves with your needs.
As your organization evolves, so should your profile. Regularly update it to reflect new technologies, threats, and business objectives. By maintaining an up-to-date profile, you ensure that your cybersecurity measures are always in sync with your organizational needs and compliance requirements.
Step 4: Gap Analysis
Step 4, Gap Analysis, is a critical phase in implementing the NIST Cybersecurity Framework. This step involves comparing your current profile with your target profile to identify “gaps” or areas where your cybersecurity measures fall short. The objective is to pinpoint vulnerabilities and weaknesses that need to be addressed.
Start by listing the controls and measures you currently have in place and compare them against industry best practices or regulatory requirements. This will give you a clear picture of where you stand. Once the gaps are identified, the next step is to prioritize them. Not all gaps are created equal; some may pose a higher risk to your organization than others.
Use a risk assessment matrix to rank these gaps based on factors like potential impact and likelihood of occurrence. Prioritizing helps you allocate resources more effectively and tackle the most critical issues first. Remember, gap analysis is not a one-off activity but should be revisited periodically to adapt to changing cybersecurity landscapes.
Step 5: Actual Implementation
Step 5, Actual Implementation, is the stage where planning meets execution. You’ve identified your goals, created your profile, conducted gap analysis, and now it’s time to put those plans into action.
Begin by revisiting your prioritized list of gaps and start implementing the necessary controls and measures. This could range from updating software and hardware to training staff on new security protocols. It’s crucial to have a detailed action plan that outlines the steps, responsibilities, and timelines for each task.
Monitoring is equally important; use metrics and key performance indicators (KPIs) to gauge the effectiveness of your implementations. Regular audits and reviews should be part of this phase to ensure that the controls are working as intended and to make adjustments as needed.
Finally, documentation is key. Keep records of all actions taken, changes made, and lessons learned. This not only aids in compliance but also sets the groundwork for continuous improvement in your cybersecurity posture.
Step 6: Continuous Improvement
In the final stage of your NIST Cybersecurity Framework journey, Continuous Improvement takes center stage. Given that cybersecurity is a constantly evolving landscape, your approach must also be dynamic. This step zeroes in on iterative learning and adaptation. Make it a habit to regularly review and update your cybersecurity measures, keeping pace with emerging threats, new technologies, and shifting business requirements.
To gauge the effectiveness of your cybersecurity controls, employ metrics and make data-driven decisions. Periodically conduct audits and actively seek feedback from all stakeholders. This ongoing cycle of assessment and improvement not only keeps your cybersecurity posture robust and current but also aligns seamlessly with NIST’s guidelines for managing cybersecurity-related risks.
Real-World Examples of Successfully Implementing the NIST Cybersecurity Framework

Lower Colorado River Authority’s (LCRA)
The Lower Colorado River Authority (LCRA) is a diverse organization with a wide range of businesses, including electric generation and transmission, water and wastewater services, and recreation. This diversity created a challenge for the LCRA in developing a cybersecurity program that would meet the needs of all of its businesses.
The LCRA found that the CSF was a good fit for its needs because it is a flexible framework that can be adapted to meet the specific needs of any organization. The LCRA implemented the CSF in a tailored way to meet the needs of each business unit.
The CSF helped the LCRA to identify gaps in its security posture and develop a plan to address them. For example, the LCRA used the CSF to identify the need to improve its risk management process. The LCRA also used the CSF to develop a plan to improve its incident response capabilities.
LCRA Implementing the NIST Cybersecurity Framework
The LCRA’s implementation of the CSF can be summarized in the following steps:
- Assess current cybersecurity capabilities. The LCRA used the CSF to assess its current cybersecurity capabilities and identify areas for improvement. This assessment included identifying its cybersecurity goals, assets, and risks.
- Develop a Target State Profile. The Target State Profile is a document that describes the organization’s desired cybersecurity posture. The LCRA used the CSF to develop a Target State Profile that identified the specific cybersecurity controls that it needed to implement in order to achieve its cybersecurity goals.
- Implement cybersecurity controls. The LCRA used the CSF Profiles to implement a variety of cybersecurity controls, such as access control, incident response, and risk management.
- Monitor and improve the cybersecurity program. The LCRA regularly monitors its cybersecurity program and makes adjustments as needed to ensure that it is aligned with its cybersecurity goals and Target State Profile.
The LCRA’s success with the CSF is a testament to the flexibility and adaptability of the framework. The CSF can be used by organizations of all sizes and industries to improve their cybersecurity posture.
How the CSF Improved LCRA’s Security Posture
Here are some of the specific ways that the LCRA used the CSF to improve its security posture:
- The LCRA used the CSF to identify its top cybersecurity priorities. The LCRA used the CSF to identify its top cybersecurity priorities, such as protecting customer data and ensuring compliance with regulations.
- The LCRA used the CSF to develop a cybersecurity program that meets the needs of all of its businesses. The LCRA tailored the CSF to meet the specific needs of each business unit.
- The LCRA used the CSF to improve its risk management process. The LCRA used the CSF to develop a risk management process that helps it to identify, assess, and manage cybersecurity risks.
- The LCRA used the CSF to improve its incident response capabilities. The LCRA used the CSF to develop an incident response plan that helps it to respond to and recover from cybersecurity incidents.
The LCRA’s implementation of the CSF is a good example of how a large organization can use the CSF to improve its security posture. The CSF is a flexible framework that can be adapted to meet the needs of organizations of all sizes and industries.
Optic Cyber Solutions
Optic Cyber Solutions is a small cybersecurity company that used the NIST Cybersecurity Framework (CSF) to improve its security posture. They chose the CSF because it is a widely recognized and comprehensive framework that provides flexibility for organizations to adapt it to their specific needs.
Optic Cyber Solutions Implementing the NIST Cybersecurity Framework
Optic used the CSF Core and Profiles to facilitate collaboration and define its cybersecurity program. The CSF Core provides a high-level view of cybersecurity and the Profiles provide more specific guidance on how to implement cybersecurity controls. They evaluated its current cybersecurity capabilities and identified areas for improvement.
Then, Optic documented its risk and created a Target State Profile to clarify cybersecurity expectations. Optic formalized an Information Security Policy based on the CSF. Optic is now using the CSF to continuously improve its cybersecurity posture.
How Optic Cyber Solutions Improved Their Security Posture
Here are some of the specific ways that Optic used the CSF to improve its security posture:
- Optic used the CSF Core to identify and prioritize its cybersecurity goals. The CSF Core provides a high-level view of cybersecurity and helps organizations to identify the most important cybersecurity goals. Optic used the CSF Core to identify its top cybersecurity priorities, such as protecting client data and ensuring compliance with regulations.
- Optic used the CSF Profiles to implement cybersecurity controls. The CSF Profiles provide more specific guidance on how to implement cybersecurity controls. Optic used the CSF Profiles to implement a variety of cybersecurity controls, such as access control, incident response, and risk management.
- Optic used the CSF to create a Target State Profile. The Target State Profile is a document that describes the organization’s desired cybersecurity posture. Optic used the CSF to create a Target State Profile that identified the specific cybersecurity controls that it needed to implement in order to achieve its cybersecurity goals.
- Optic used the CSF to formalize its Information Security Policy. The Information Security Policy is a document that describes the organization’s cybersecurity policies and procedures. Optic used the CSF to formalize its Information Security Policy and ensure that it was aligned with its cybersecurity goals and Target State Profile.
Optic Cyber Solutions is a good example of how a small organization can use the CSF to improve its security posture. The CSF is a flexible framework that can be adapted to meet the needs of organizations of all sizes and industries.
Graphic: Case study snapshots with key takeaways.
How to Keep Your Implementation Up-to-Date
Keeping your NIST Cybersecurity Framework implementation up-to-date is crucial for maintaining a robust security posture. Regular updates ensure that you’re equipped to handle emerging threats and vulnerabilities. Monitoring plays a vital role in identifying unusual activities, thereby enabling timely interventions.
- Regular Updates: Cyber threats evolve rapidly. Staying current with the latest security patches and updates is essential for closing vulnerabilities that could be exploited.
- Monitoring: Continuous monitoring of network activities helps in early detection of anomalies. This proactive approach minimizes potential damage.
- Compliance Checks: Regular audits ensure that your implementation aligns with updated regulations and standards, reducing legal risks.
- Feedback Loop: Regular reviews and feedback from internal and external audits can offer insights for improvement.
- Employee Training: As the framework updates, so should your staff’s knowledge. Regular training sessions can equip them to better manage new types of threats.
By integrating these practices, you create a dynamic security environment that adapts to new challenges, ensuring long-term resilience.
Conclusion and Next Steps
In conclusion, maintaining an up to date NIST Cybersecurity Framework is non-negotiable for robust security. Regular updates and vigilant monitoring are pivotal for safeguarding your organization’s digital assets. Don’t overlook these aspects; take action today to fortify your cybersecurity measures. We encourage you to share your experiences and pose any questions in the comments section below. Your insights could be invaluable to others on a similar journey.
The post Unlock 2023’s Best Practices: How to Implement the NIST Cybersecurity Framework appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/nist-csf-implementation/?utm_source=rss&utm_medium=rss&utm_campaign=nist-csf-implementation
如有侵权请联系:admin#unsafe.sh
