
2023-10-12 01:34:19 Author: securityboulevard.com(查看原文) 阅读量:20 收藏

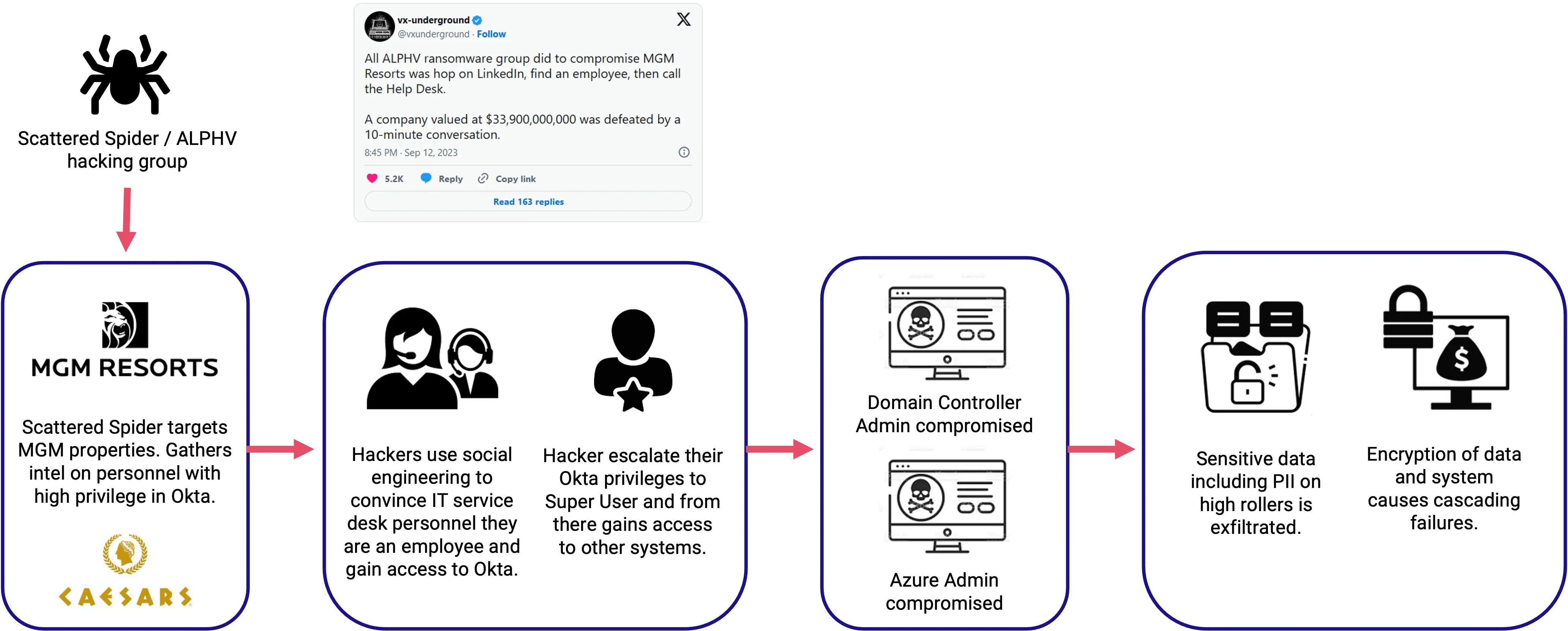
MGM Resorts recently found itself in the midst of a major cybersecurity incident that not only crippled its operations but also exposed sensitive customer data. The sophisticated attack orchestrated by a group known as Scattered Spider employed social engineering to the IT department to reset credentials. The attackers then gained access to the SSO, raised their identity credentials to super user level and then systematically got into other systems.
The cyberattack cost MGM over $100 million according to its FORM 8-K filing with the SEC.
While the attack chain involved multiple steps, exploiting several points of failure, the initial attack vector was low tech and all too common. We look at what happened and how organizations can protect themselves from these increasingly prevalent attacks.
Anatomy of the Attack: Unraveling Scattered Spider’s Web
On September 11, MGM Resorts announced a “cybersecurity issue” affecting its systems, prompting a shutdown to protect data integrity. Reports surfaced that essential services, from hotel room access to slot machines, were offline, leading to resort staff shifting to manual processes.
It wasn’t until October 5 that the true extent of the breach came to light. Personally identifiable information (PII), had been compromised. This same information was encrypted and a ransomware demand was made.
Scattered Spider, the group claiming responsibility (the same group involved in breaching Clorox), demonstrated a proficiency in social engineering, specializing in voice phishing, or “vishing” — exploiting human vulnerability through convincing phone calls. The hackers allegedly gained access to MGM’s systems by impersonating an employee. Utilizing publicly available information found on LinkedIn and other social platforms, they targeted the IT help desk, manipulating their way into obtaining credentials. The attackers utilized ransomware-as-a-service to encrypt MGM’s data.
Key Lessons
This incident underscores the vulnerability of even well-established organizations to social engineering and identity-related attacks. Most IT services desks/help desks are short-staffed, and dealing with large volumes of calls, many of which are related to password or MFA issues. In the case of MGM Resorts, the attackers exploited human nature and publicly available information to trick IT service desk personnel and gain the credentials necessary to simply login as a legitimate employee. From there they were able to breach multiple systems and gain command and control of the entire organization.
Identity Assurance for the Entire Identity Lifecycle
Human nature will always be the weakest point in any system — the 2023 Verizon DBIR found the human element to be a factor in 74% of all breaches. The MGM attack underscores the need for a comprehensive Identity Assurance approach that secures the modern user lifecycle and addresses the Achilles heel of current authentication and identity verification processes. Organizations need to ensure they can trust that somebody is who they claim to be at all times — when that call to the service desk comes through, the staff responding must be absolutely certain that the person they are speaking to is the legitimate holder of that identity. If, for example, they request access through a new device or credential reset, there must be a secure, efficient way to do so.
A complete Identity Assurance approach unites strong passkey-based authentication, continuous risk monitoring and intelligent identity verification into a comprehensive solution.
Passwordless Authentication
Deploying passwordless, phishing resistant multi-factor authentication (MFA) adds a crucial layer of security. Eliminating traditional passwords and adopting passwordless authentication methods, such as biometrics, security tokens, or mobile-based authentication, could have thwarted the MGM attackers. Passwords are often the weakest link, and removing them from the equation reduces the risk of unauthorized access.
Continuous Risk Monitoring
Threat vectors and risk levels change constantly. Risk signals and telemetry from a broad variety of sources must be continuously monitored and used to trigger appropriate authentication and verification actions. These should include various device and browser signals, user behavior anomalies and information from the broader security ecosystem.
Identity Verification
Simply put, identity verification helps ensure that someone is who they say they are at all times. It can eliminate many of the social engineering tactics currently being used. It should meet the unique needs of the population in question whether workforce or consumer. This requires a multi-verification approach that includes but is not limited to AI, chat, video, face recognition and other cutting-edge technologies to create a seamless and secure method of confirming the individuals’ identities — and re-verifying them at critical moments in time. This would eliminate the vishing attack vector which is based on implied and unreliable trust without a specific and comprehensive verification methodology.
Here’s an example of intelligent identity verification in action:
Protecting Against Helpdesk Social Engineering and Other Identity Attacks
The MGM Resorts cyber incident serves as a stark reminder that no organization is immune to cyber threats, regardless of its size or industry. As cybercriminals continue to evolve their tactics, it is imperative for businesses to stay ahead by implementing advanced security measures. Identity verification and passwordless authentication can stand as formidable defense against social engineering and other identity-related attacks, providing a robust protection for organizations, their systems, and their data. HYPR Identity Assurance protects the entire lifecycle and includes HYPR Affirm, the only identity verification solution designed specifically for the workforce. Affirm uses a multitude of signals including phone verification, document verification, a video chat, and face recognition to make help desk social engineering unviable for hackers. If you’d like to learn more, contact one of our identity security experts.
![]()
*** This is a Security Bloggers Network syndicated blog from HYPR Blog authored by Michael Rothschild, VP of Product Marketing, HYPR. Read the original post at: https://blog.hypr.com/lessons-from-the-mgm-attack
如有侵权请联系:admin#unsafe.sh
