Executive Summary
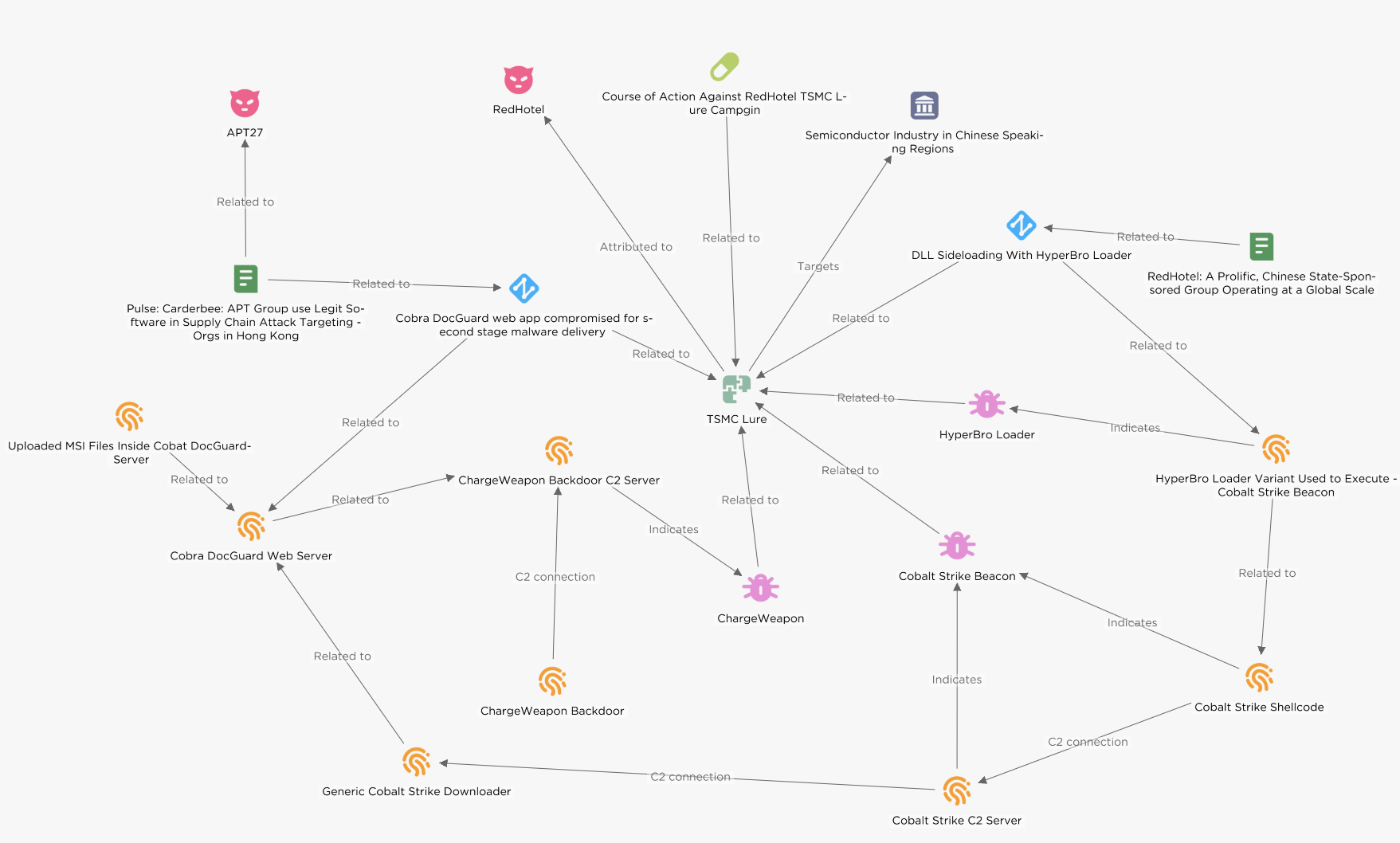
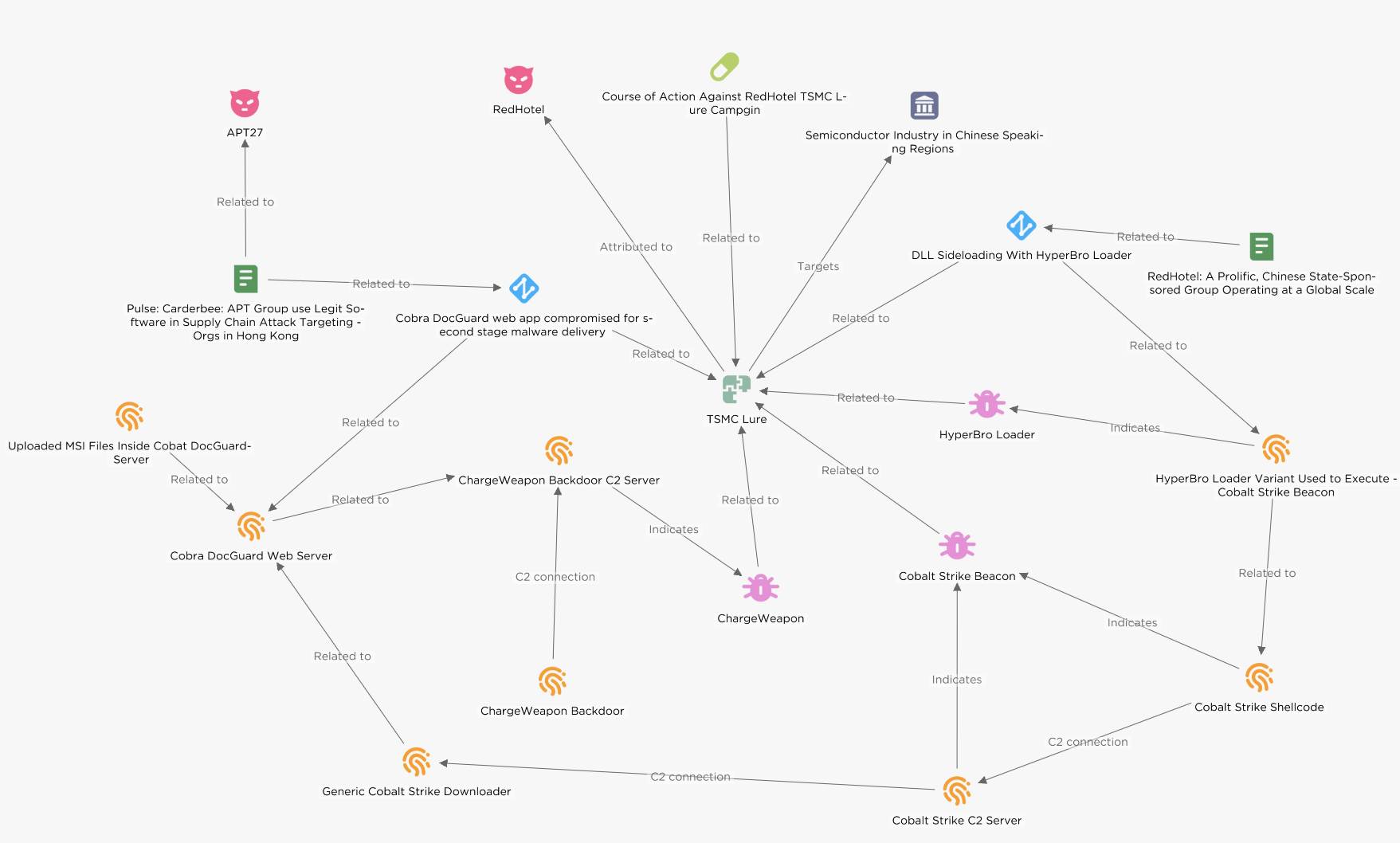
EclecticIQ analysts identified a cyber espionage campaign where threat actors used a variant of HyperBro loader with a Taiwan Semiconductor Manufacturing (TSMC) lure, likely to target the semiconductor industry in Mandarin/Chinese speaking East Asian regions (Taiwan, Hong Kong, Singapore). Operational tactics, techniques, and procedures (TTPs) overlap with previously reported activities attributed to People’s Republic of China (PRC) backed cyber espionage group.
The HyperBro loader variant leverages a digitally signed CyberArk binary for DLL-Side loading, resulting in in-memory execution of a Cobalt Strike beacon. [1] Pivoting the beacon, EclecticIQ analysts identified a previously undocumented malware downloader. This downloader utilizes the BitsTransfer module in PowerShell to fetch malicious binaries from a very likely compromised Cobra DocGuard server.
The malware downloader employs a DLL Side-Loading technique by using a signed McAfee binary, mcods.exe, to run the Cobalt Strike shellcode. Analysts identified that the shellcode used the same Cobalt Strike C2 server associated with the HyperBro loader variant.
The compromised Cobra DocGuard web server hosted a GO-based backdoor that EclecticIQ tracks as “ChargeWeapon”. The backdoor was very likely uploaded by the same threat actor on August 21, 2023 [2]. ChargeWeapon is designed to get remote access and send device and network information from an infected host to an attacker controlled C2 server.
Figure 1 – Graph view in EclecticIQ Intelligence Center
(click on image to open in separate tab).
![]()
*** This is a Security Bloggers Network syndicated blog from EclecticIQ Blog authored by Arda Büyükkaya. Read the original post at: https://blog.eclecticiq.com/chinese-state-sponsored-cyber-espionage-activity-targeting-semiconductor-industry-in-east-asia