2023-10-3 11:30:0 Author: securityboulevard.com(查看原文) 阅读量:13 收藏
I. Abstract
In September 2023, NSFOCUS global threat hunting system monitored several new botnet variant families developed based on Mirai, among which hailBot, kiraiBot and catDDoS are the most active, are accelerating their spread, and are widely deployed, which has constituted a considerable threat. Through this article, we will disclose the technical details of these three new Mirai variants and the data monitored by the global threat hunting system.
More and more botnet Trojan horses have been developed based on Mirai in recent years. A large number of attackers carry out secondary development based on Mirai source code. These newly developed Trojan horses either introduce new encryption algorithms to hide critical information or better hide themselves by modifying the go-live process and designing more covert communication methods. Although the open source code has gradually lowered the threshold for building a botnet, the attacker’s attempt to enhance invisibility has not been weakened.
II. Mirai’s New Variants Are Coming
(1) hailBot
The hailBot is developed based on Mirai source code, and its name is derived from the string information “hail china mainland” output after running. This unusual expression cannot escape the suspicion of being planted and framed.
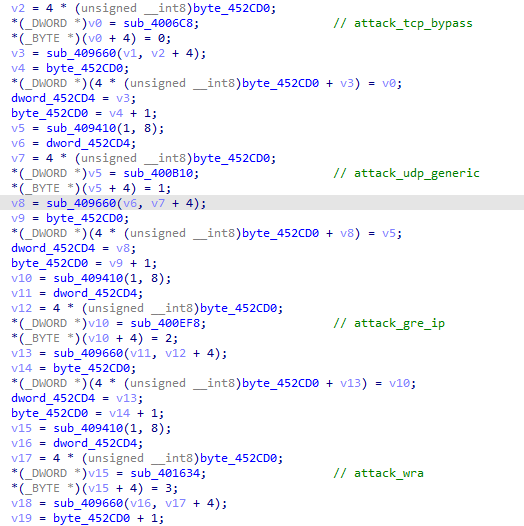
Regarding hailBot traffic, the go-live data packet of the original Mirai has been modified.
The flow generated is as follows:
The current version of hailBot attack mode supports four DDoS attack methods based on TCP and UDP protocols.
The hailBot spreads through vulnerability exploitation and weak password scanning & brute force. The current version has only one built-in vulnerability, CVE-2017-17215 , but it does not exclude the possibility of separating the vulnerability propagation module from the sample.

In historical activities, the controller of hailBot was highly active. As early as the end of last year, it began to build its own botnet based on Mirai source code. The Mirai Trojan horse, which was developed earlier, will return the string information “WHO THE HELL ARE YOU? TELL ME YOUR NAME!” on the server side after going live.
Monitoring data shows that hailBot has not issued too many commands recently. It still focuses on exploratory test attacks, but its active C&C number continues to increase, indicating that it is in a large-scale layout, which deserves our vigilance.

After further investigation into the asset information of the hailBot controller, we discovered that their C&C infrastructure, with IP addresses 5.181.80.120 and 5.181.80.115, had previously disseminated multiple bait documents carrying the CVE-2017-11882 vulnerability. These bait documents bore file names such as ‘INVOICE.xlsx’, ‘Product_requetslist.xlsx’, ‘CIF WMS REF NO 451RFQ ARN-DT-2021-06-29.xlsx’, and others, intending to lure victims into opening the documents to trigger the vulnerability. As a result, they downloaded and executed various commercial espionage-oriented banking trojans, including Lokibot and Formbook.
Based on this, we believe that the hailBot controller is a systematically organized multi-faceted attacker. Initially, their primary targets were financial and trade institutions. However, in the latter half of 2022, they shifted their focus to IoT platforms.
(2) kiraiBot
The kiraiBot is a recent addition to the Mirai botnet variant family, which draws inspiration from the Mirai source code but incorporates numerous unique personal design elements. Its name comes from the string information “kirai” in the sample.
The kiraiBot implements persistence by setting the self-starting script under/etc/init.d/init.d/.

The known propagation mode of kiraiBot is to breach port 23 through weak password scanning.
The “kirai” string will also appear in the scan traffic of the kiraiBot, and the report server is set by referring to Mirai to receive the breach results.
The site where kiraiBot propagation scripts are stored is not consistent with C&C.
Its go-live data packet is composed of the string information “BUILD” concatenated file running path, with the following characteristics:
The current version supports six DDoS attack modes.
Compared with the traditional Mirai class, the kiraiBot has a large change in code structure. The instruction parsing module has also been adjusted on the basis of the original Mirai. Its activities are concentrated in August and September 2023. The version change frequency is low. The number of instructions issued by the family recently is not large, but the propagation volume is extremely large, and its threat cannot be ignored.
(3) catDDoS
The catDDoS family introduces the ChaCha20 algorithm on the basis of Mirai source code to encrypt and store some key information. The key and nonce of the latest version are as follows:
This variant has adjusted the go-live process of the original Mirai, and the go-live data is sent to the server in multiple rounds.
The go-live data packets sent to the server end are composed of plaintext and ciphertext encrypted by the ChaCha20 algorithm. After “00 00 00 04” is sent, the bytes and actual contents of the subsequent data will be sent alternately. The generated traffic is as follows:
The monitoring data shows that the catDDoS family has entered the combat phase, and the frequency of command issuance is relatively frequent. The choice of attack time is mostly from 8 a.m. to 9 p.m. Recent monitoring data shows that 58% of its attack targets are located in China, followed by the United States, accounting for 25%. In addition, Japan, Singapore, France and other countries have also been affected.
The catDDoS has a variety of built-in DDoS attack methods, and attackers tend to use ack_flood and grip_flood in actual attack activities, accounting for 63% and 29%, respectively.
Although the controller of the catDDoS did not build a complete botnet Trojan horse from zero, it attached great importance to the concealment of the Trojan horse. It not only introduced the ChaCha20 algorithm but also introduced the OpenNIC domain name, which is quite similar to the Fodcha family.
III. Conclusion
In recent years, we have observed the emergence of numerous new families of botnets, with most of them appearing briefly and then disappearing. Most of these botnets are derived from integrating Mirai and Gafgyt codes. Some attackers only slightly modified the go-live process of the open source Trojan horse and publicized the establishment of a new botnet family to attract buyers. However, some attackers insist on the “pursuit” of technology. Although they also reuse open-source code, they spend some time and energy on this basis.
Attackers’ redesign of open-source botnet trojans primarily focuses on two dimensions. First, they aim to enhance the stealthiness on the file side, such as introducing new encryption algorithms to conceal critical information or employing anti-analysis techniques. Second, they manipulate the communication aspect, employing tactics like binding malicious IPs to benign domains using ClouDNS or incorporating OpenNIC domains to evade detection. However, it’s noteworthy that the efforts on the communication side tend to be more intricate and intriguing.
IOCs
hailBot
3f30a468b56c5761e346f3e709fd098e
34.147.16.24
34.165.70.211
34.176.112.249
34.64.52.239
34.69.75.60
34.92.28.223
35.188.240.127
5.181.80.115
5.181.80.120
5.181.80.70
5.181.80.71
kiraiBot
33ea03c6fdb4bcd826f99ca7ae8b5907
179.43.155.231
catDDoS
12fe77575c11b698501e2068810823a4
139.177.197.168
212.118.43.167
77.105.138.202
84.54.47.93
88.218.62.22 88.218.62.221
The post Mirai Botnet’s New Wave: hailBot,kiraiBot, catDDoS, and Their Fierce Onslaught appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks..
*** This is a Security Bloggers Network syndicated blog from NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks. authored by NSFOCUS. Read the original post at: https://nsfocusglobal.com/mirai-botnets-new-wave-hailbot-kiraibot-catddos-and-their-fierce-onslaught/
如有侵权请联系:admin#unsafe.sh


















