libwebp exploit timeline
CVE-2023-41064; CVE-2023-4863; CVE-2023-5129
- On September 7th 2023, researchers at Citizen Lab reported a zero-click exploit that was actively used by NSOs to infect iOS devices with the Pegasus malware – this was disclosed as CVE-2023-41064.
- A zero-click exploit means that a user is not required to click anything or take any action to trigger the exploit. Simply viewing a maliciously crafted WebP image is enough to be infected.
- Citizen Lab researchers together with Apple’s Security Engineering & Architecture promptly disclosed the exploit to Google due to the potential damage to Google Chrome users.
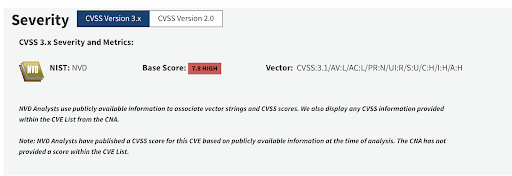
- On or around September 12 2023, Google reported the vulnerability to NVD as a Chrome vulnerability with a different id – CVE-2023-4863.
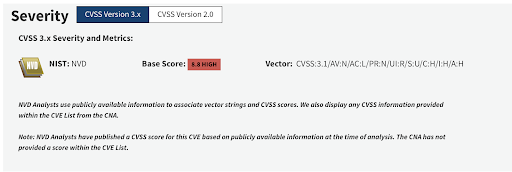
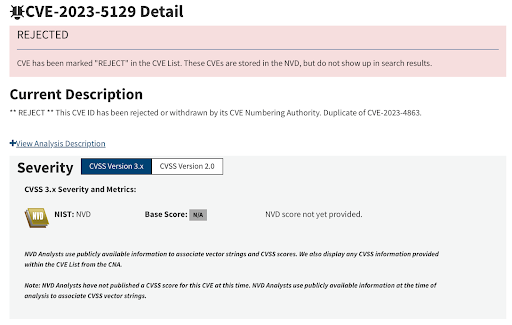
- On September 25, 2023 Google understood that the potential impact went beyond Chromium and submitted another CVE with the id CVE-2023-5129, giving it the maximum CVSS score of 10.0. The scope was not limited to a specific software product or framework, rather it applied to the libwebp library which is used by nearly all modern operating systems. NVD marked this CVE as a duplicate of CVE--2023-4863.
What is libwebp?
Libwebp is a popular library used to render webp images. This library is part of almost all modern operating systems and software platforms, including Apple iOS and Chromium based products like Google Chrome browser, Electron Software Framework, Debian (Ubuntu, Alpine), CentOS, Gentoo, SUSE and MacOS.
And products like Google Chrome browser and the Electron Software Framework are used in some of the most popular applications including Slack,1Password, Visual Studio Code, Discord and Microsoft Edge. You can see a more complete list of applications using Chromium and applications using Electron by clicking on these links.
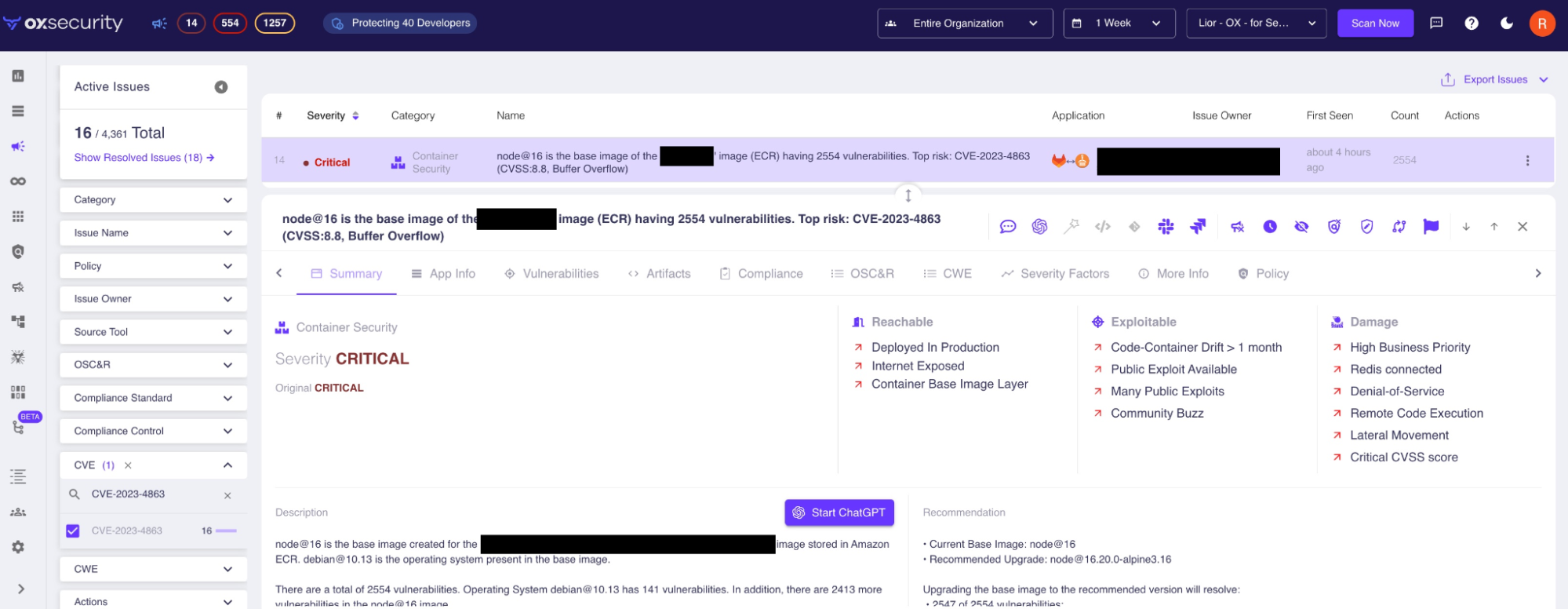
How to detect libwebp with OX Security
The libwebp vulnerability can be found in code, but it is most commonly detected in operating systems. This makes it particularly difficult to detect because it requires security teams to scan all operating systems in use, including container base images. Traditional scanners typically do not scan the latter.
For OX Security users, scanning Dockerfile definitions and container images happens automatically.
What you should do now
Step 1: Test your applications with OX Security. Sign up for a free OX Security account.
OX Security automates the rest. Our solution:
- Scans all your applications from cloud to code.
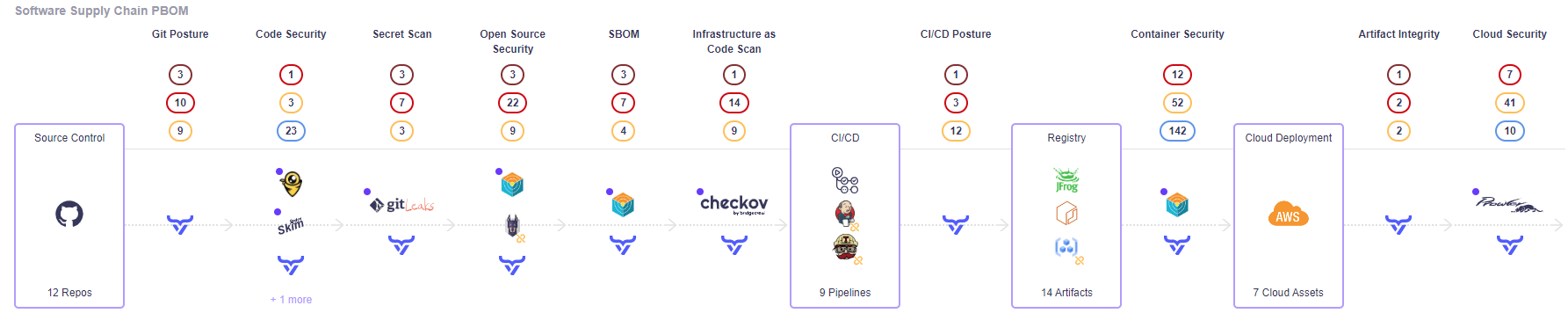
- Detects direct uses of libwebp, as well as the more difficult challenge of identifying libraries, frameworks and base images that contain libwebp.
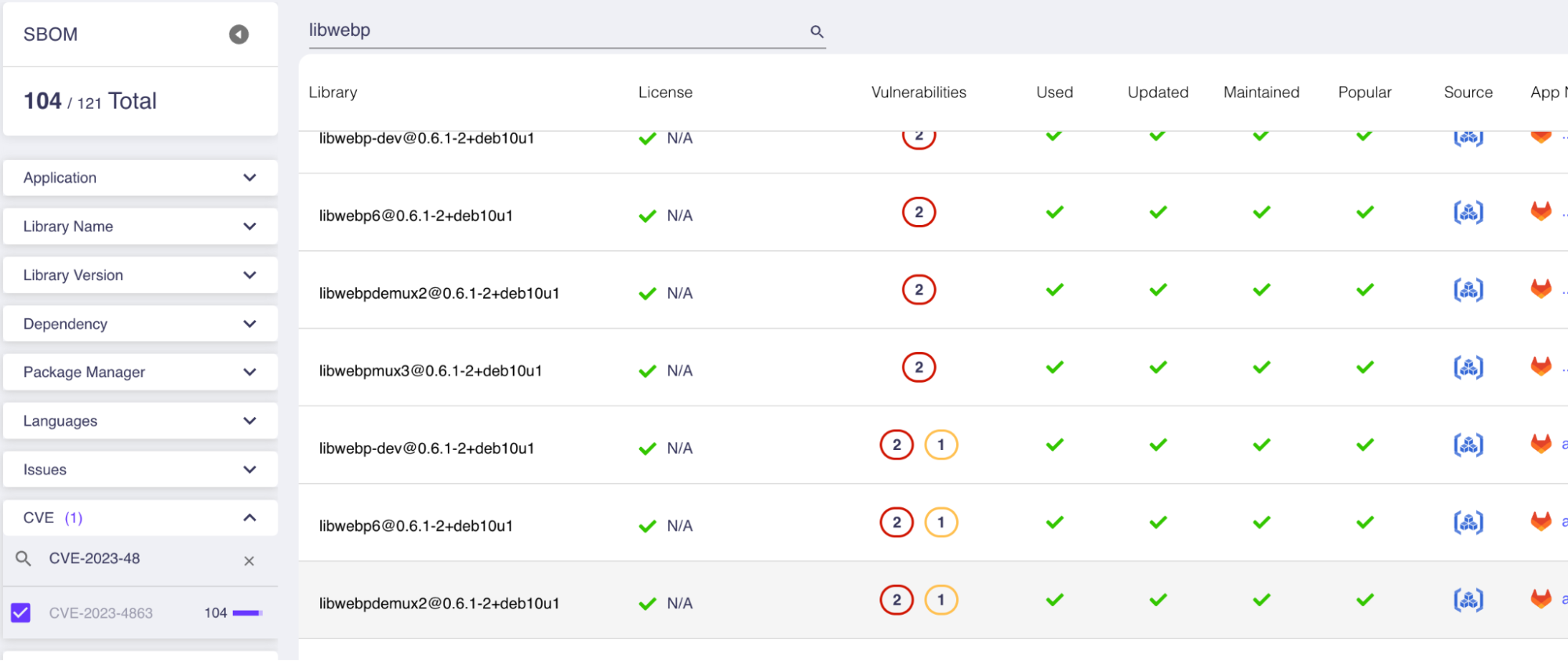
- Figures out the safe versions you should be using.

- Prioritizes risks where libwebp is exposed in production and deprioritizes risks where libwebp is not deployed or used.
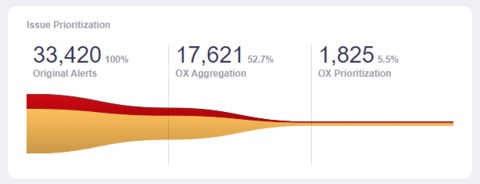
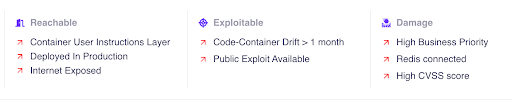
- Triggers your organization’s response plan.
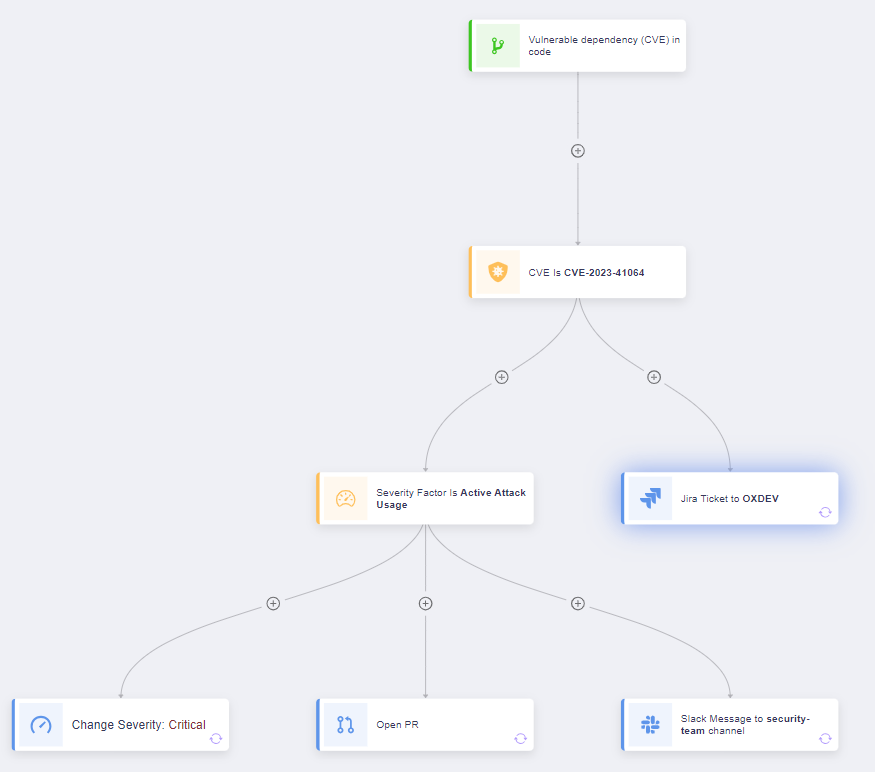
OX Security will continue to monitor this situation and continue to provide updates as events unfold. Make sure you follow us on Linkedin and check back on the OX Security Blog for any developments as they occur. If you have any questions please feel free to send an email out to one of our product specialists at [email protected].
The post What You Need to Know About the libwebp Exploit appeared first on OX Security.
*** This is a Security Bloggers Network syndicated blog from OX Security authored by Yael Citro. Read the original post at: https://www.ox.security/what-you-need-to-know-about-the-libwebp-exploit/

