
2023-9-29 02:25:22 Author: securityboulevard.com(查看原文) 阅读量:7 收藏

Introduction
In the evolving landscape of cyber threats, small businesses find themselves in the crosshairs, necessitating robust and dynamic security solutions. Endpoint Security and Cyber Security as a Service (SECaaS) emerge as pivotal components in fortifying the digital frontiers of organizations.
Endpoint Security was explored in a previous post. It is the practice of safeguarding the individual devices that connect to your network from cyber threats. It is the frontline defense against malware, phishing, and other malicious attacks. Endpoint Security ensures that each access point to the network is secure, thus preventing unauthorized access and protecting sensitive data.
On the other hand, Cyber Security as a Service is a comprehensive solution that outsources cybersecurity to experts. SECaaS ensures continuous monitoring, management, and response to security threats. It provides small businesses with access to top-tier security technologies and expertise, alleviating the burden of managing cybersecurity in-house.
How Endpoint Security Works with Security As A Service
The synergy between Endpoint Security and Cyber Security as a Service is a game-changer for small businesses. Endpoint Security ensures that each device connecting to the network is secure, while SECaaS provides overarching protection and response mechanisms. This combination allows for a multi-layered defense strategy. Endpoint Security acts as the shield against incoming threats. SECaaS is the vigilant guardian, monitoring, and responding to any anomalies or breaches in real-time.
This synergy is particularly crucial for small businesses, where resources are often limited. By leveraging Endpoint Security as a Service, organizations can ensure comprehensive protection. This works from individual devices to the entire network without the need for extensive in-house cybersecurity teams or infrastructure. It enables businesses to focus on their core competencies, with the assurance that their cyber frontiers are well-guarded.
In this article, we will delve deeper into how combining Endpoint Security with Cyber Security as a Service can unlock unparalleled protection for small businesses. We will explore the features, benefits, and implementation strategies of this integrated approach to cybersecurity.
The Rising Threat Landscape
In 2023, the cyber threat landscape has escalated, posing unprecedented challenges, especially for small businesses. The frequency and sophistication of cyber-attacks have surged. Statista reports 1,802 data compromises impacting over 422 million individuals in 2022 alone.
Why Small Businesses are Prime Targets
Small businesses often become prime targets for cybercriminals due to typically having less robust security infrastructures compared to larger enterprises. Limited resources and a lack of specialized cybersecurity knowledge make them more susceptible to breaches. The perceived ease of penetration coupled with potentially lower risk of prosecution makes small businesses attractive to attackers seeking quick gains.
The Vulnerable Sectors
Particularly, sectors like healthcare, financial services, and manufacturing have witnessed significant increases in data compromises. These sectors often handle sensitive information. Thus, making them lucrative targets for cybercriminals aiming to exploit vulnerabilities for financial gain or data theft.
The Need for Proactive Measures
Given this rising threat, it’s imperative for small businesses to adopt proactive security measures. They need to embrace a comprehensive protection strategy to safeguard against the evolving cyber risks. Implementing robust endpoint security as a service can be a pivotal step in fortifying defenses. Doing so ensures the integrity of sensitive data and mitigates the risk of unauthorized access.
Endpoint Security: More Than Just a Buzzword
In today’s interconnected world, endpoint security is not merely a buzzword. Endpoint Security is a critical component in safeguarding individual devices (both in-network and user devices) connected to a network. Every device is a potential entry point for cyber threats, making their protection paramount.
The Necessity of Protecting Individual Devices
Protecting individual devices is crucial as they often have access to sensitive business information. A compromised device can lead to unauthorized access, data breaches, and severe business disruptions. Implementing robust endpoint security measures ensures that each device adheres to security policies, reducing the risk of cyber-attacks and safeguarding business assets.
Consequences of Ignoring Endpoint Security
Ignoring endpoint security can have devastating consequences. Below is a table illustrating various threats and their potential impacts:
| Threat Type | Consequence | Potential Impact |
|---|---|---|
| Ransomware | Encryption of Data | Financial Loss, Operational Disruption |
| Phishing | Unauthorized Access to Sensitive Information | Data Theft, Financial Loss |
| Data Breach | Exposure of Confidential Data | Reputation Damage, Legal Penalties |
| Malware | Corruption of System Files | System Downtime, Productivity Loss |
| DDoS Attack | Overloading of Network Resources | Service Unavailability, Loss of Business |
Ignoring endpoint security can lead to severe financial losses, operational disruptions, and irreversible damage to a company’s reputation. The exposure of sensitive information can also result in legal penalties, further emphasizing the importance of proactive endpoint security measures.
A Proactive Approach is Key
To mitigate these risks, adopting a proactive approach to endpoint security is essential. Employing comprehensive protection strategies, continuous monitoring, and regular updates can fortify defenses, detect threats early, and ensure the integrity and confidentiality of business data.
Cyber Security as a Service: A Proactive Approach
Cyber Security as a Service (SECaaS) is not just a solution; it’s a proactive approach to ensuring the security of your business. It empowers small businesses by providing them with the necessary tools and services to protect against cyber threats, allowing them to focus on their core business functions.
SECaaS Empowers Small Businesses

As depicted in the flowchart above, SECaaS operates systematically from threat detection to continuous monitoring. It begins with identifying potential threats, analyzing their risk levels, responding with immediate actions, mitigating by deploying preventive measures, and finally, ensuring continuous monitoring for any future threats.
Small businesses, often lacking in-house security expertise and resources, can greatly benefit from SECaaS. It provides access to advanced security technologies and expert knowledge, leveling the playing field with larger organizations and enhancing overall security posture.
Role of SECaaS in Continuous Protection and Monitoring
SECaaS plays a pivotal role in offering continuous protection and monitoring. It ensures that security measures are always up-to-date and effective against the latest threats, providing peace of mind to businesses. The service’s proactive nature allows for the early detection of threats, minimizing potential damages and disruptions.
By employing SECaaS, small businesses can ensure the integrity and confidentiality of their data while maintaining compliance with industry regulations. The continuous monitoring and protection offered by SECaaS are crucial in today’s ever-evolving threat landscape, where new cyber threats emerge daily.
Endpoint Security Solutions: Shielding Your Business
Endpoint Protection Platforms (EPP) are a comprehensive security solution designed to safeguard businesses from a myriad of cyber threats. They combine multiple security technologies to provide robust protection to endpoint devices.
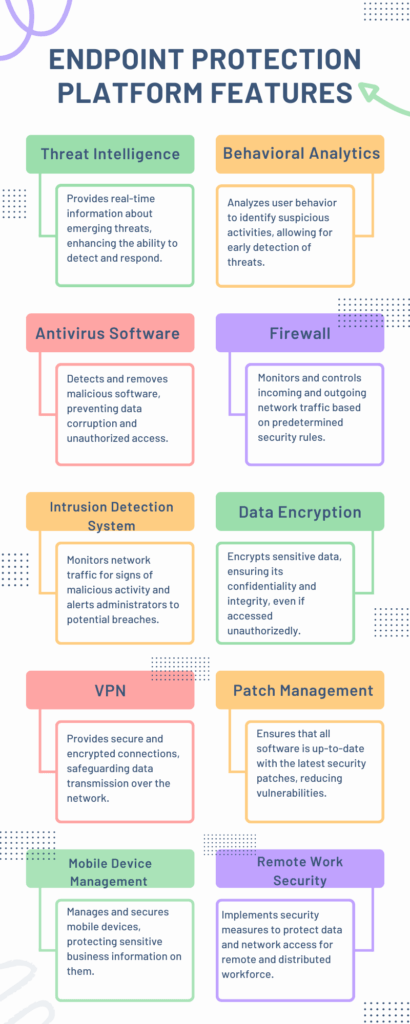
Explore the Endpoint Protection Platforms (EPP)
As illustrated in the infographic, EPPs are equipped with a variety of features, each serving a unique protective role, ensuring the security of business data and networks.
- Threat Intelligence: Empowers businesses with real-time information on emerging threats, enhancing detection and response capabilities.
- Behavioral Analytics: Analyzes user behavior to identify and counteract suspicious activities swiftly.
- Antivirus Software: Offers foundational protection by detecting and removing malicious software.
- Firewall: Controls network traffic based on security rules, preventing unauthorized access and attacks.
- Intrusion Detection System (IDS): Monitors for signs of malicious activity, providing alerts to potential security breaches.
- Data Encryption: Secures sensitive data, maintaining its integrity and confidentiality.
- VPN: Ensures secure and encrypted connections, protecting data during transmission.
- Patch Management: Keeps software updated, mitigating vulnerabilities and reducing the risk of exploitation.
- Mobile Device Management (MDM): Secures and manages mobile devices, safeguarding business information.
- Remote Work Security: Implements measures to secure data and network access for remote employees.
Benefits of EPPs
EPPs are not just about protection; they offer numerous benefits to businesses. They reduce the complexity of managing multiple security solutions, providing a unified approach to endpoint security. By leveraging EPPs, businesses can enhance their security posture, ensure compliance, and protect against evolving cyber threats, all while optimizing operational efficiency.
Navigating the Challenges of Remote Work & BYOD
The Rise of Remote Work and its Security Implications
The digital age has ushered in a new era of work flexibility. Remote work, once a luxury, has become a staple for many businesses. This shift, while beneficial, brings forth a myriad of security challenges. Cyber threats don’t discriminate based on location. Whether in an office or a coffee shop, your data can be at risk.
It’s evident that remote work and BYOD (Bring Your Own Device) policies are intertwined. As more employees work from different locations, many use their personal devices for work tasks. This mix of personal and professional data on a single device can be a goldmine for cybercriminals. This article on BYOD policy highlights the importance of setting clear guidelines for employees using personal devices for work.
The infographic below visually delineates how endpoint security software fortifies data transmission between diverse remote devices and company servers. It illustrates the seamless flow of secured data, showcasing the initial user access, followed by the protective layer of the endpoint security software, and finally, the secure arrival of data at the company servers. This depiction underscores the vital role of endpoint security in maintaining the integrity and confidentiality of data during remote transmissions, ensuring that every piece of information is meticulously shielded from potential threats.
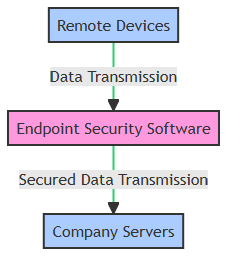
How Endpoint Security Software Mitigates Risks in Remote Work
Endpoint security plays a pivotal role in safeguarding data in a remote work environment. It acts as a shield, protecting endpoints from potential threats. As mentioned in the article on endpoint security for remote work, this software detects, prevents, and responds to threats. It ensures that only authorized devices access your network.
Moreover, endpoint security software offers key features like real-time monitoring and threat intelligence. These tools provide insights into potential vulnerabilities and offer solutions before they escalate. Transitioning to remote work doesn’t mean compromising on security. With the right tools and policies in place, businesses can enjoy the benefits of flexibility without the looming threat of cyberattacks.
In conclusion, the rise of remote work has changed the way businesses operate. While it offers numerous advantages, it also presents security challenges. However, with robust endpoint security software and clear BYOD policies, businesses can mitigate these risks and ensure a safe working environment for their employees.
Implementing Robust Security Technologies
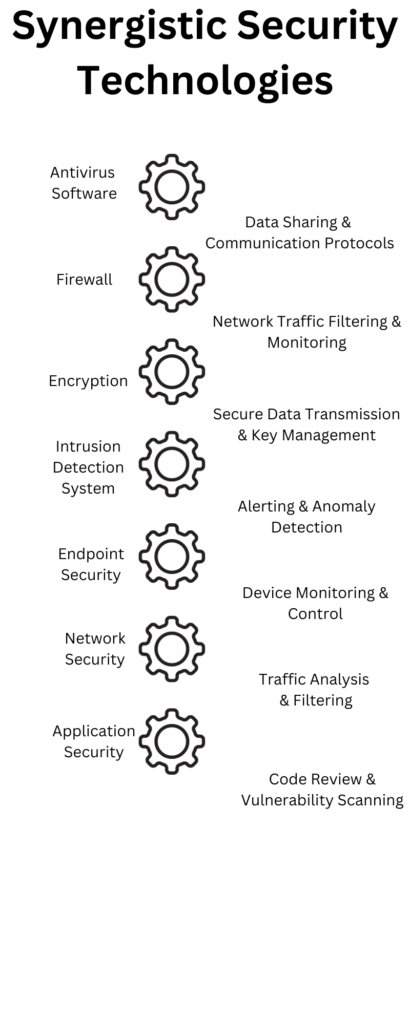
In today’s digital landscape, implementing robust security technologies is not just a need but a necessity. The infographic below meticulously illustrates how diverse security technologies interconnect to form a fortified defense against cyber threats, each layer contributing to a comprehensive security ecosystem.
The infographic presents a layered structure, depicting the interconnectedness of various security technologies. It starts with Antivirus Software as the foundational layer, scanning and removing malicious software and files. This layer is interconnected through data sharing and communication protocols to the Firewall layer, which monitors and controls network traffic based on predetermined security rules. The Firewall is connected to Encryption, ensuring data integrity and confidentiality through secure data transmission and key management. The subsequent layer is the Intrusion Detection System, monitoring for malicious exploits and security policy violations, connected to Endpoint Security, which protects network endpoints from being exploited. Network Security is the next layer, focusing on protecting computer networks from intruders, connected to the final layer, Application Security, which keeps software and devices free of threats and vulnerabilities.
Importance of Encryption and Multifactor Authentication
Encryption is crucial, acting as a secure envelope, safeguarding data from unauthorized access during transmission. It ensures that even if data is intercepted, it remains unreadable to unauthorized entities. Multifactor Authentication (MFA), on the other hand, adds an extra layer of security, requiring users to verify their identity using multiple verification methods before granting access. This dual shield is pivotal, especially when securing sensitive information, making unauthorized access exceedingly challenging.
Securing Mobile Devices with Advanced Technologies
Mobile devices, being portable and often used on unsecured networks, are susceptible to threats. The integration of advanced security technologies is vital to shield them. Endpoint security plays a significant role here, monitoring and controlling endpoint devices, ensuring secure data transmission between the devices and company servers. It’s like having a vigilant guard, constantly overseeing the safety of mobile devices, ensuring no unauthorized access occurs, and swiftly responding to any potential threats.
By employing a combination of these advanced security technologies, businesses can ensure a secure environment, mitigating risks and safeguarding their assets against the ever-evolving cyber threats.
Strategizing Endpoint Security Implementation
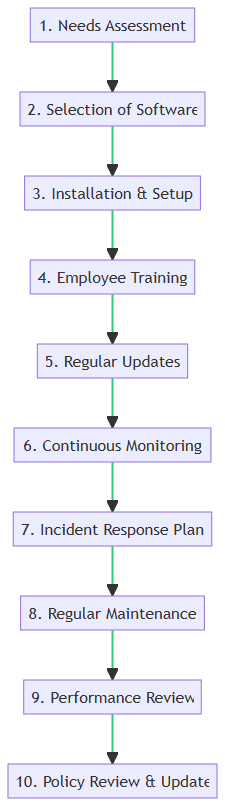
Strategizing Endpoint Security Implementation is a meticulous process, crucial for fortifying your business against cyber threats. The infographic and the table below provide a succinct guide to implementing endpoint security software effectively, from assessing needs to regular updates and maintenance.
| Step Name | Description | Associated Feature |
|---|---|---|
| 1. Needs Assessment | Evaluate specific security needs and requirements, focusing on identifying vulnerabilities. | Network Security |
| 2. Selection of Software | Choose appropriate endpoint security software based on assessed needs and business goals. | Application Security |
| 3. Installation & Setup | Install and configure the software on all endpoint devices according to security policies. | Endpoint Security |
| 4. Employee Training | Educate employees on security best practices and effective use of the new software. | Intrusion Detection |
| 5. Regular Updates | Update the software and security policies regularly to protect against the latest threats. | Antivirus Software |
| 6. Continuous Monitoring | Monitor the network and endpoint devices continuously for any suspicious activities. | Firewall |
| 7. Incident Response Plan | Address any security incidents promptly and efficiently with a robust response plan. | Encryption Methods |
| 8. Regular Maintenance | Perform regular checks and maintenance to ensure optimal functioning of the security software. | Endpoint Security |
| 9. Performance Review | Conduct regular reviews to ensure the software meets the evolving security needs of the business. | Application Security |
| 10. Policy Review & Update | Adapt to the changing threat landscape and business environment by updating policies regularly. | Network Security |
Starting with Needs Assessment, it’s vital to understand your business’s unique security needs and potential risks. This step is foundational, focusing on the identification of vulnerabilities and potential threats, ensuring the maintenance of network security.
Choosing the right Endpoint Security Software is pivotal. It’s not just about selecting a solution. It is also about choosing one that aligns perfectly with your business goals and the specific needs identified during the assessment, optimizing application security.
Follow this structured and strategic approach and reference the provided visual guide. By doing so, you can ensure the implementation of robust and effective endpoint security, safeguarding your business against the ever-evolving landscape of cyber threats.
Conclusion: Safeguarding the Future of Small Businesses
In the dynamic realm of cybersecurity, Endpoint Security is not a one-time task but an ongoing commitment. It’s crucial to stay vigilant, constantly updating and adapting to the latest security technologies and threats. Endpoint Security as a Service emerges as a beacon. It offers continuous monitoring and comprehensive protection, ensuring the safety of your business in the ever-evolving digital landscape.
Embracing Endpoint Security as a Service is not just a strategic move; it’s an imperative. Endpoint Security as a Service empowers businesses, especially small ones, to fortify their defenses. Thus, safeguarding their assets and data against the myriad of cyber threats lurking in the digital shadows.
We encourage you to delve deeper. Embrace the proactive and robust protection offered by Endpoint Security as a Service.Make it an integral part of your business strategy. It’s about fostering a culture of security. Become proactive rather than reactive. Thus, ensuring the longevity and success of your business in this digital age.
We invite you to share your thoughts, experiences, and insights on implementing Endpoint Security. Let’s create a dialogue, learn from each other, and together, build a safer, more secure digital world for our businesses.
The post Unlocking Endpoint Security as a Service: 2023 Insights! appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/endpoint-security-as-a-service/?utm_source=rss&utm_medium=rss&utm_campaign=endpoint-security-as-a-service
如有侵权请联系:admin#unsafe.sh
