When you run cloud-native workloads, vulnerabilities are always found, whether a certain vulnerable package or a known exploit. You could have thousands or even hundreds of thousands of vulnerabilities at any time. Multiply that by the number of container assets and images, and you have a big challenge of figuring out where to start. In my previous blog, I dove deep into how one could operationalize valuable guides such as the Kubernetes NSA Hardening Guide by leveraging Uptycs' unified CNAPP and XDR platform for visibility across your cluster fleet, continuous monitoring and scanning, and detailed evidence and remediation steps. Now, we’ll dive into vulnerability management and how to implement shift left controls to prevent any vulnerabilities, malware, or secrets from entering your SDLC and supply chain. Here are some of the challenges we see when it comes to vulnerability management for Kubernetes and containers today: Let’s see how Uptycs unified CNAPP and XDR security platform enables you to solve these challenges while providing a single solution for all your Kubernetes/containers vulnerability management from code to cloud. The Uptycs platform gives you a single place to start for anything and everything on your Kubernetes and containers vulnerability management! Specifically, the dashboard empowers SecOps admins to do the following: By starting here you can instantly cut the noise down and start with what is most important! Operationalize daily/weekly triages: Through metrics such as what are your new daily vulnerabilities or net new this week - SecOps admins now have an easy way to see what is most relevant now and assign a JIRA ticket or add to an exception list with one single click. Next, in order to be more proactive in fixing your vulnerabilities earlier in the SDLC, Uptycs offers CI and Registry scanning capabilities that are extremely easy to onboard, allowing you to secure your innovation pipeline from code to cloud. Capability Supported Platforms CI Scanning Jenkins, GitHub, GitLab, Travis CI, AWS CodeBuild Registry Scanning JFrog Artifactory, Private Docker, Amazon ECR, Azure ACR, Google GCR We can uniquely scan images across CI and Registry for vulnerabilities, malware, and secrets - ensuring your code is always at its safest. Ready to elevate your Kubernetes and container security? Explore how Uptycs can empower your strategy at Uptycs Containers & Kubernetes. When you start with CI Scanning, the Uptycs platform shows you the security results and passed and failed image builds so that you can correlate your security findings to your SDLC. You also get the same view with registry scanning, allowing admins to filter by a given CVE vulnerability and check on what parts of their SDLC, CI Registry, and Runtime that vulnerability is present. As you start to prioritize fixes of images across your SDLC or look at your most vulnerable images, you get a single pane of glass view of your image security across the SDLC to answer key questions such as: These insights can be key to ensuring your development teams and business units follow the right process while ensuring you have end-to-end security controls across your developer pipeline. While you may want to enable guardrails in runtime, a delicate balance must be achieved in the SDLC to ensure you have security controls in place while not hindering developer velocity. In order to facilitate this, Uptycs offers key capabilities as part of the CI Scanning capabilities, such as the following: Grace Periods: Users may configure a vulnerability "Grace Period," which allows a vulnerability, once first detected, to remain within an image for a set amount of time. If the vulnerability remains within an image once the Grace Period has elapsed, then builds will fail until the vulnerability is no longer detected. This grants developers time to remediate the newly detected vulnerabilities without immediately interrupting their task when the vulnerability was first discovered. Policy Configurations: What if you wanted to ignore vulnerabilities with no fixes as part of your CI Scanning? Or only fail based on a set of critical CVEs or even ignore certain vulnerabilities? As part of your Uptycs CI Scanning configuration, you can enable certain policy configurations and flags to tailor your vulnerability management to your business needs. # Configure vulnerability scanning. vulnerabilities: fatal_cvss_score: 7 # Configure the maximum allowable CVSS score. ignore_no_fix: true # Ignore any detected vulnerabilities for which there are no known fixes. Image Admission Controller: With the image admission controller (Fig. 6), you can implement secure guardrails by blocking images coming from registries scanning in Uptycs and with critical or high vulnerabilities from being used in runtime. This gives SecOps admins confidence that critical or high vulnerabilities will never make it into their container and Kubernetes runtime environments while allowing developers the necessary time to fix the image vulnerabilities earlier in the SDLC. Navigating vulnerabilities in Kubernetes and container environments is complex. As these vulnerabilities mount, challenges arise in prioritization, securing the SDLC, and ensuring developer flexibility. Uptycs unified CNAPP and XDR is designed to meet these challenges head-on. By offering intelligent vulnerability prioritization, seamless integration with the SDLC through CI and Registry scanning, and developer-centric guardrails, Uptycs ensures businesses can effectively manage risks while fostering innovation. Mastering Kubernetes Security - Part 1: Uptycs Guide for NSA Hardening & ComplianceTop vulnerability management challenges for Kubernetes and containers
Step 1: Vulnerability prioritization and KPI measurement
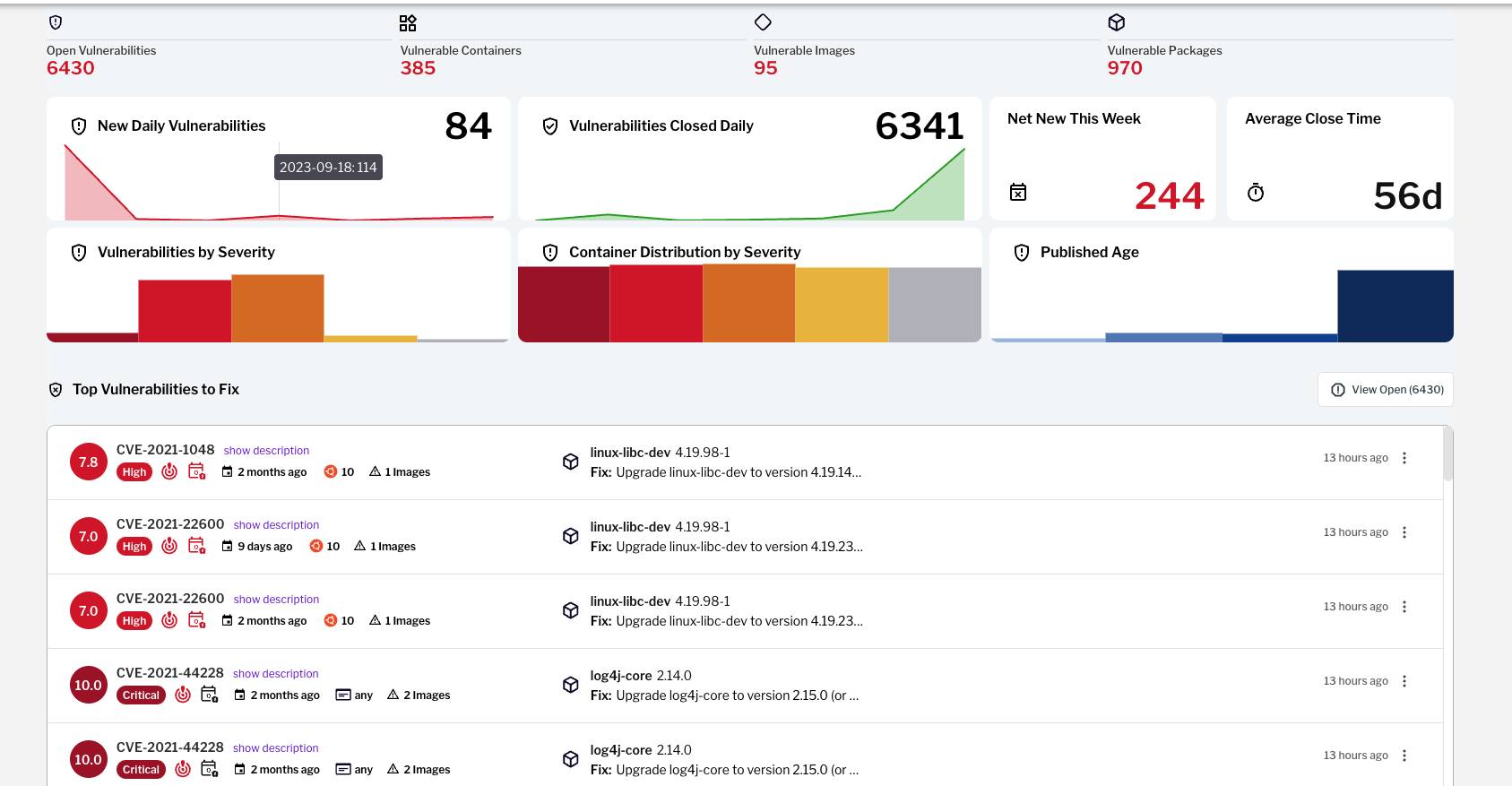 Figure 1 – Container vulnerabilities dashboard in the Uptycs platform
Figure 1 – Container vulnerabilities dashboard in the Uptycs platform
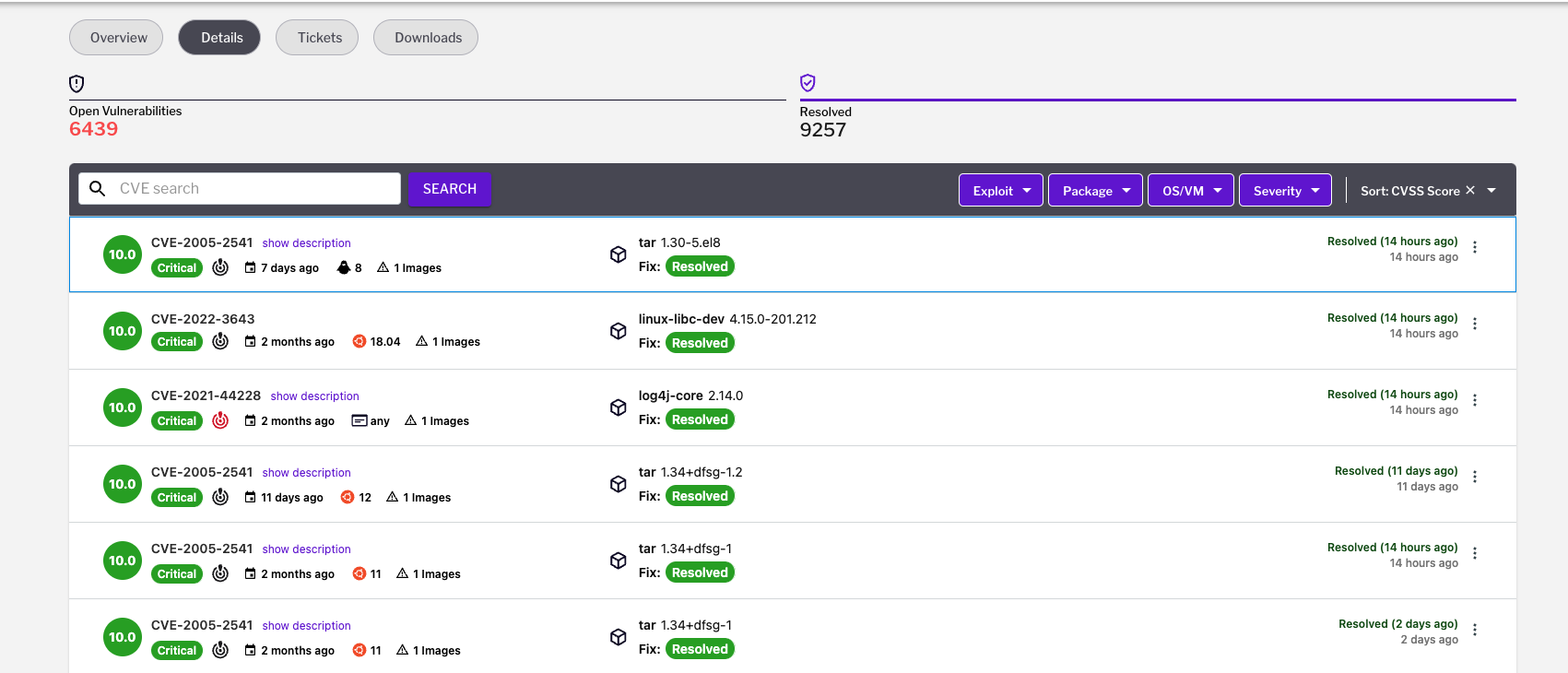 Figure 2 – Resolved vulnerabilities shown in the Uptycs platform
Figure 2 – Resolved vulnerabilities shown in the Uptycs platformStep 2: Implementing shift left controls across your SDLC
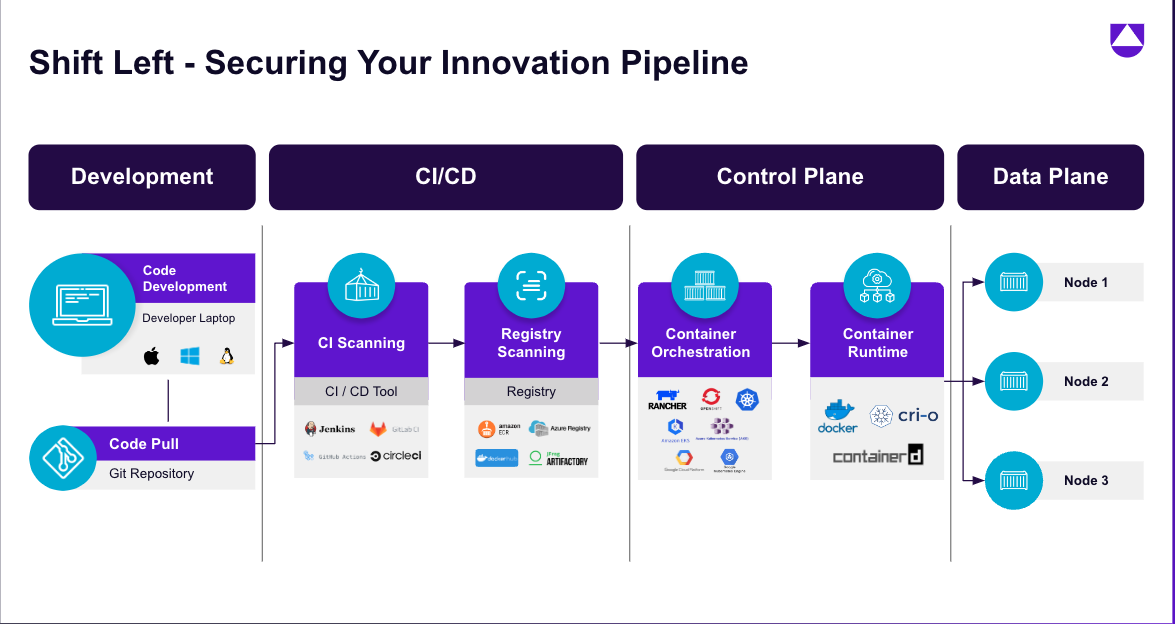 Figure 3 - Secure your innovation pipeline from code to cloud
Figure 3 - Secure your innovation pipeline from code to cloud
What sets Uptycs apart?
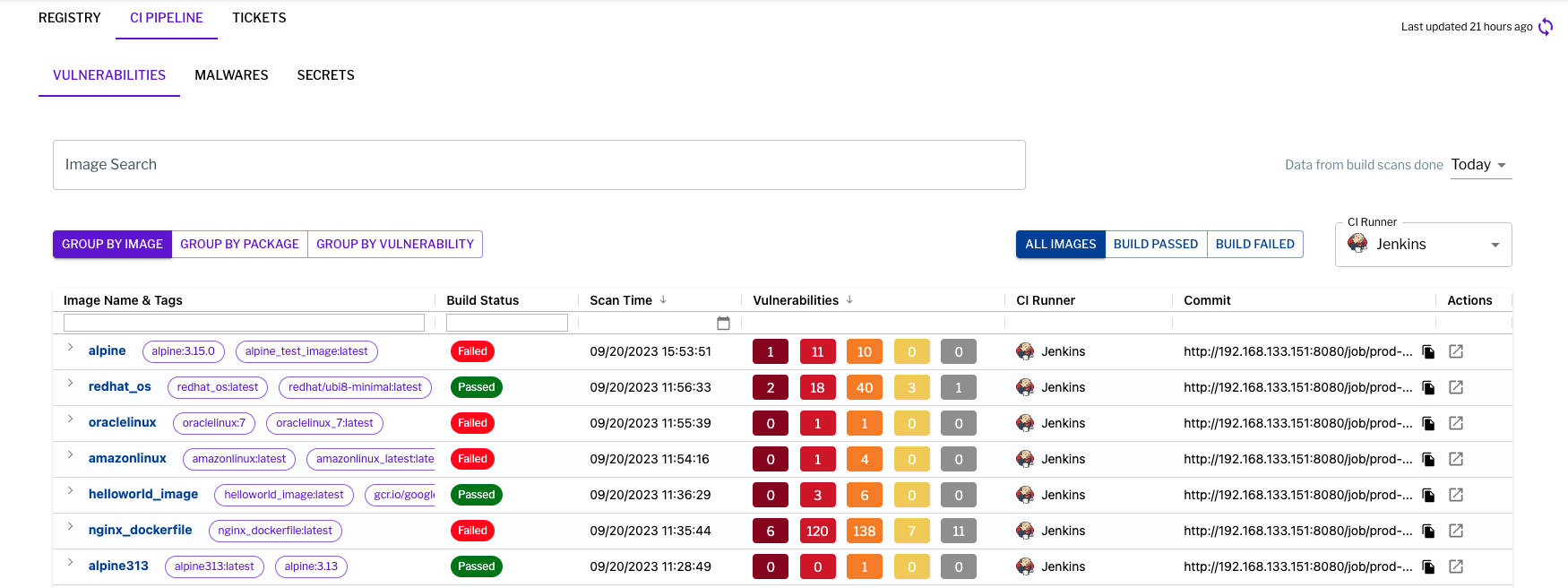 Figure 4 – CI Image scanning in the Uptycs platform
Figure 4 – CI Image scanning in the Uptycs platform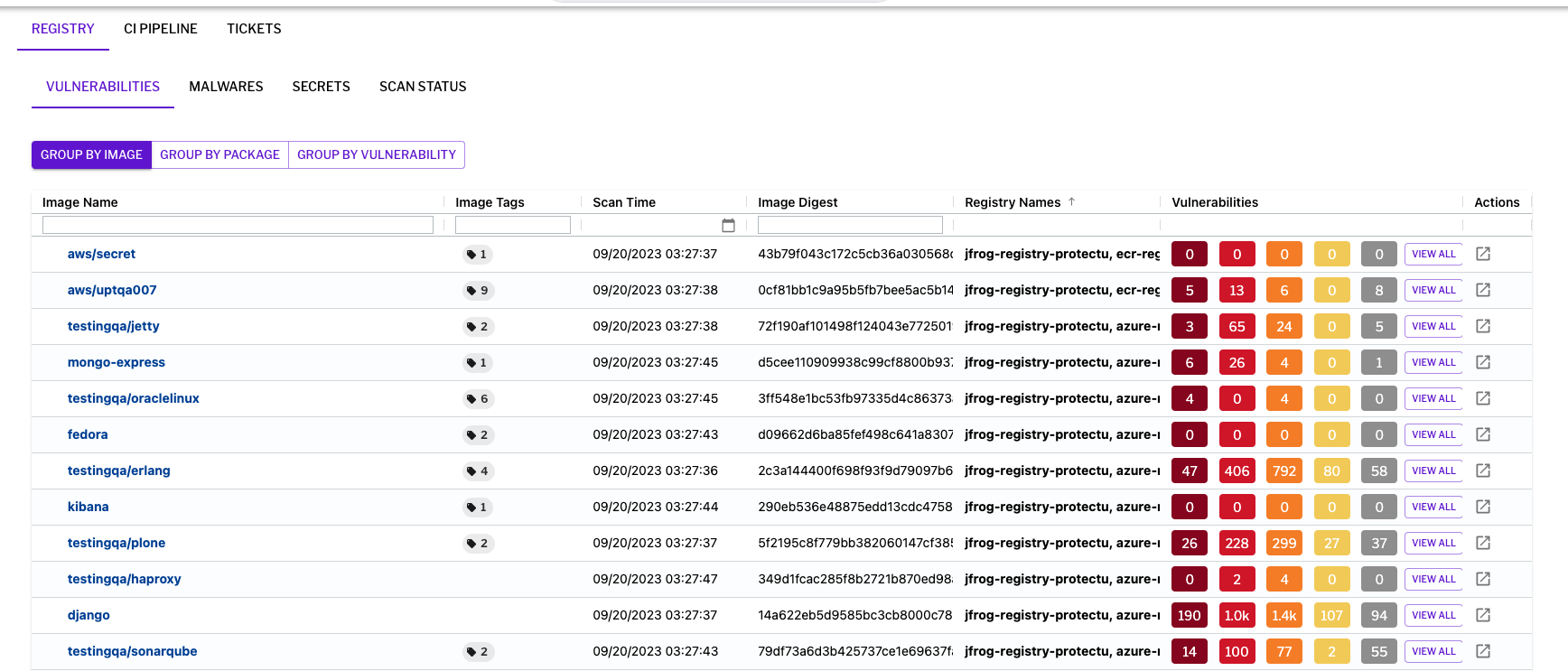 Figure 5 – Registry scanning in the Uptycs platform
Figure 5 – Registry scanning in the Uptycs platform
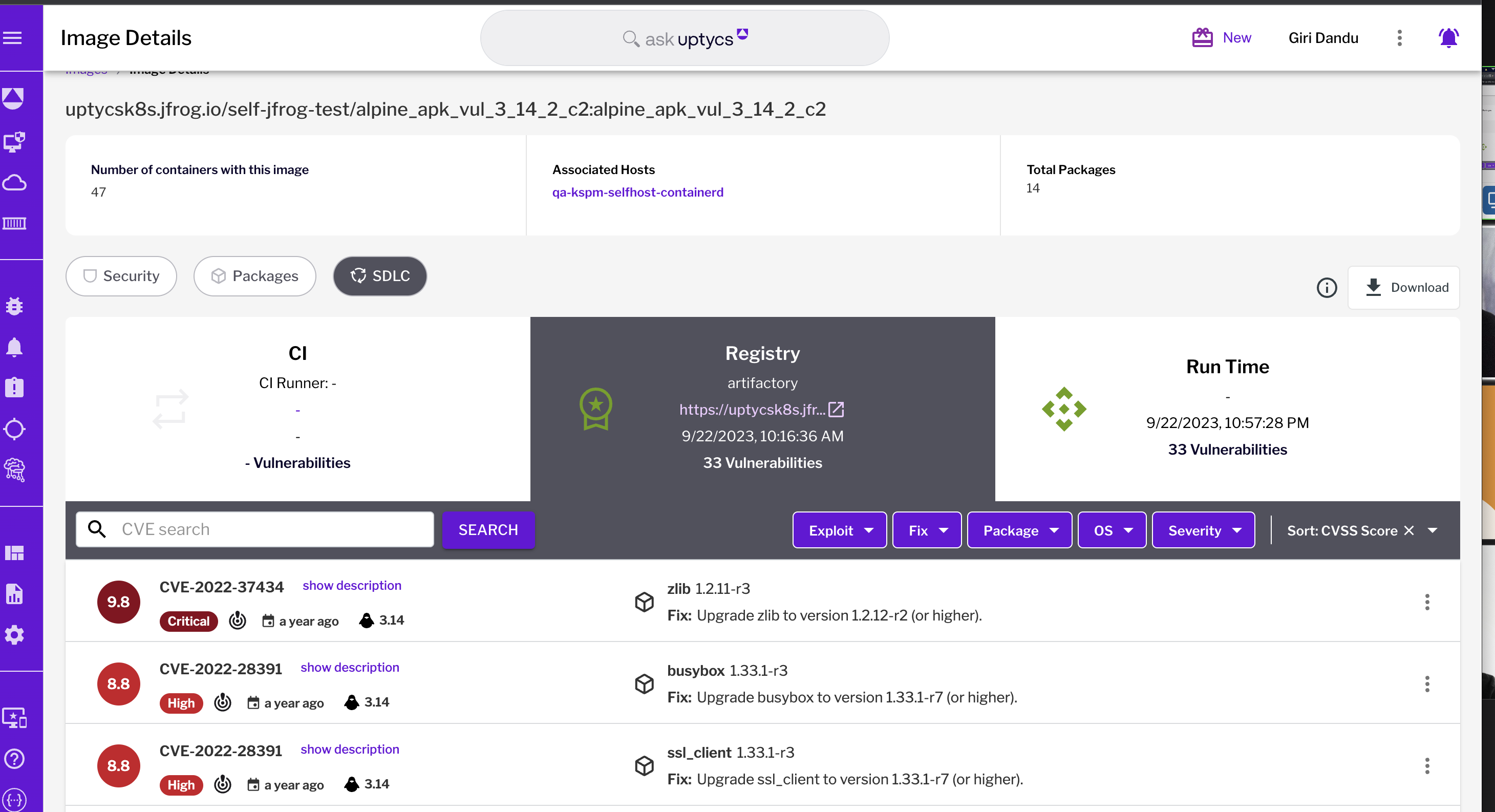 Figure 6 – Image traceability through the SDLC
Figure 6 – Image traceability through the SDLCStep 3: Enabling developer-friendly guardrails
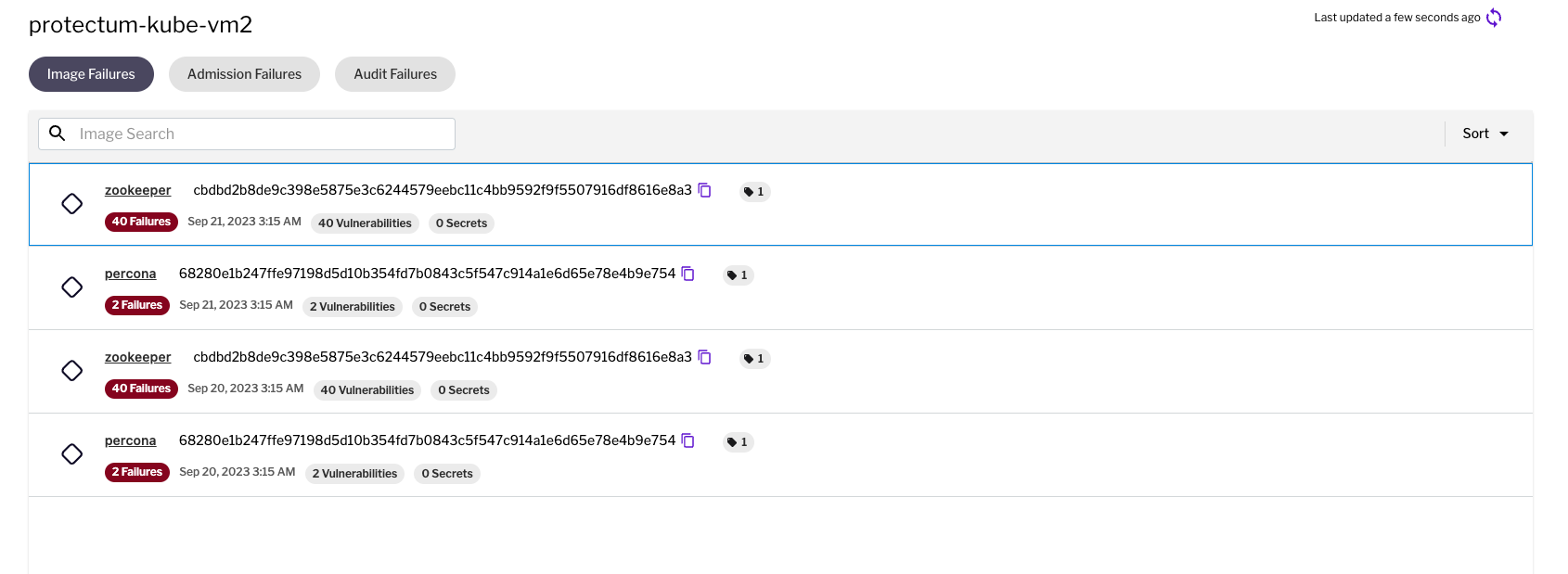 Figure 7 – Image admission controller in Uptycs platform
Figure 7 – Image admission controller in Uptycs platformConclusion
More from this series:
Vulnerability Management Shift Left Controls: Kubernetes Security #2
2023-9-26 22:54:34 Author: www.uptycs.com(查看原文) 阅读量:17 收藏
2023-9-26 22:54:34 Author: www.uptycs.com(查看原文) 阅读量:17 收藏
文章来源: https://www.uptycs.com/blog/mastering-kubernetes-and-container-security-2
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh