
2023-9-11 21:46:46 Author: www.sentinelone.com(查看原文) 阅读量:43 收藏
This year has seen an explosion of infostealers targeting the macOS platform. Throughout 2023, we have observed a number of new infostealer families including MacStealer, Pureland, Atomic Stealer and RealStealer (aka Realst). Over the last few months, we have also been tracking a family of infostealers we call ‘MetaStealer’. Last week, Apple dropped a new signature for XProtect that detects some (but not all) variants of the MetaStealer family.
In this post, we describe how MetaStealer differs from other recent stealers, as well as indicate some intriguing overlaps with other malware. We highlight how threat actors are proactively targeting macOS businesses by posing as fake clients in order to socially engineer victims into launching malicious payloads, and we provide a comprehensive list of indicators to help threat hunters and security teams identify MetaStealer in their environments. All SentinelOne customers are automatically protected from macOS MetaStealer.

MetaStealer Droppers Targeting Businesses
Many of the samples of MetaStealer we have observed are distributed in malicious application bundles contained in disk image format (.dmg) with names indicating that the targets were business users of Mac devices.
MetaStealer disk images contain names such as
- “Advertising terms of reference (MacOS presentation).dmg”
- “CONCEPT A3 full menu with dishes and translations to English.dmg”
- “AnimatedPoster.dmg”
- “Brief_Presentation-Task_Overview-(SOW)-PlayersClub.dmg”
Many of the disk image droppers contain the names including the words “Official Brief Description” such as “(Cover references,tasks,logos,brief)\YoungSUG_Official_Brief_Description_LucasProd.dmg”, suggesting that these were lures aimed at business users of macOS.
In one case, a malicious version of MetaStellar with the name “Conract for paymen & confidentiality agreement Lucasprod.dmg” was uploaded to VirusTotal with a comment from the victim describing how they were lured.
“I was targeted by someone posing as a design client, and didn’t realize anything was out of the ordinary. The man I’d been negotiating with on the job this past week sent me a password protected zip file containing this DMG file, which I thought was a bit odd.
Against my better judgement I mounted the image to my computer to see its contents. It contained an app that was disguised as a PDF, which I did not open and is when I realized he was a scammer.”
Other versions of MetaStealer we have seen use names masquerading as Adobe files or software such as “AdobeOfficialBriefDescription.dmg” and “Adobe Photoshop 2023 (with AI) installer.dmg”.
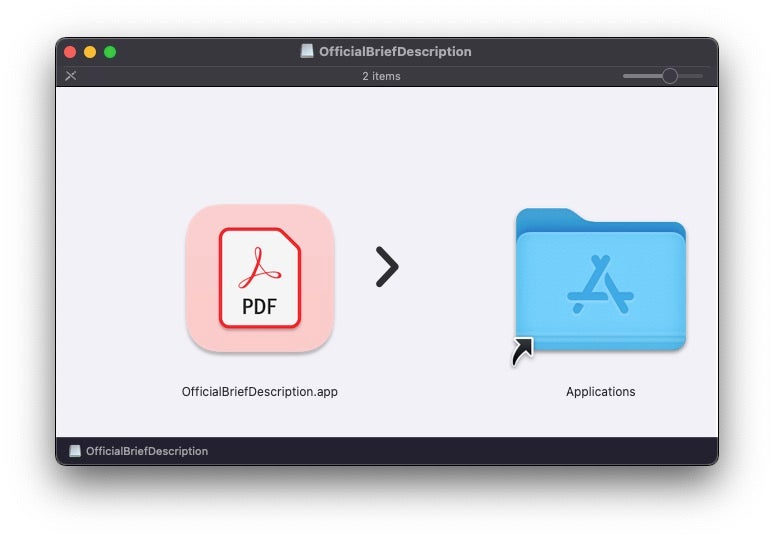
This specific targeting of business users is somewhat unusual for macOS malware, which is more commonly found being distributed via torrent sites or suspicious third-party software distributors as cracked versions of business, productivity or other popular software.
MetaStealer Malicious Application Bundles
The applications inside the MetaStealer disk images contain the minimum required to form a valid macOS bundle, namely an Info.plist file, a Resources folder containing an icon image and a MacOS folder containing the malicious executable.
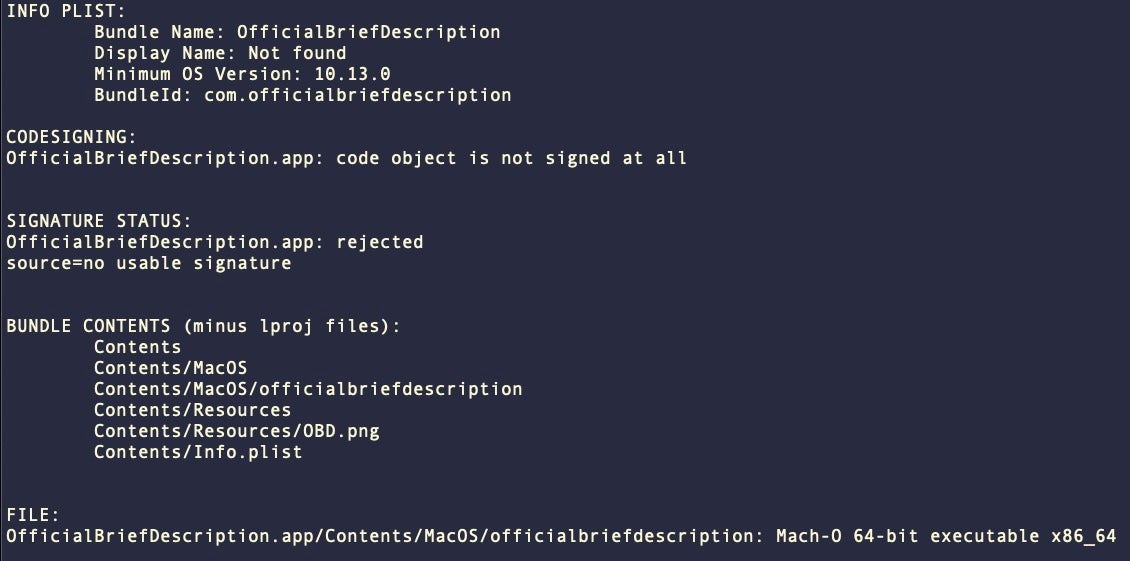
Although we have seen some versions carrying an Apple Developer code signature embedded in the executable (Bourigaultn Nathan (U5F3ZXR58U), none of the samples we observed attached a code signature or used ad hoc signing. This means that to gain execution, the threat actor would likely need to be guided or persuaded to override protections such as Gatekeeper and OCSP.
Interestingly, all the samples we have collected are single architecture x86_64 binaries, meaning that they will only run on Apple’s Apple silicon M1 and M2 machines with the help of Rosetta.
Early samples of MetaStealer began appearing on VirusTotal around March 2023 and increased throughout the summer. The most recent sample we are aware of was uploaded to VirusTotal on 27 August. Apple updated its malware blocking tool XProtect to version 2170 in the week commencing 4 September.
However, some of the samples in our collection that appeared in June and July remain undetected by XProtect after this update; these include the following malicious Mach-O executables:
1df8ff1fe464a0d9baaeead3c7158563a60199d4 1e5319969d6a53efc0ec1345414c62c810f95fce 2c567a37c49af5bce4a236be5e060c33835132cf 57c2302c30955527293ed90bfaf627a4132386fb b51d7482d38dd19b2cb1cd303e39f8bddf5452ac c37751372bb6c970ab5c447a1043c58ce49e10a5 c5429b9b4d1a8e147f5918667732049f3bd55676 fce7a0c00bfed23d6d70b57395e2ec072c456cba
MetaStealer Obfuscated Go Executable
The main executable in MetaStealer bundles is an Intel x86 Mach-O containing compiled and heavily obfuscated Go source code. The Go Build ID has been stripped and function names obfuscated. The obfuscation method bears similarity to that used in obfuscated Sliver and Poseidon malware binaries, and may be a product of the garble obfuscator or similar.
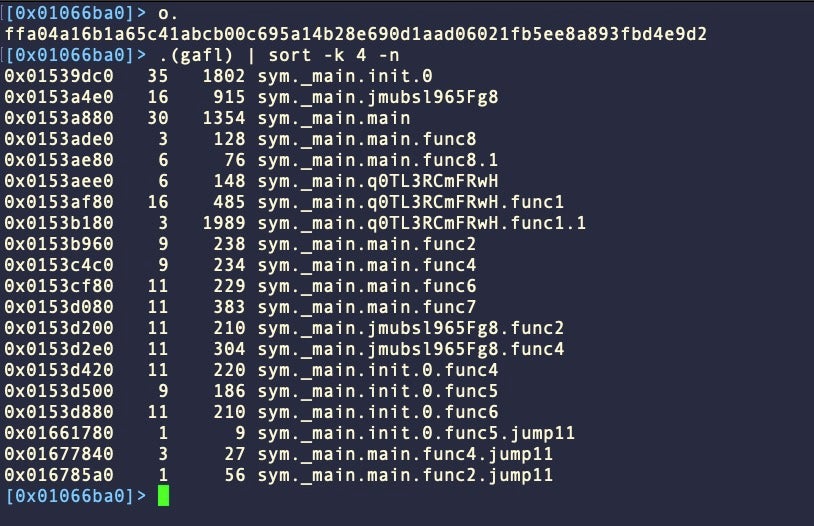
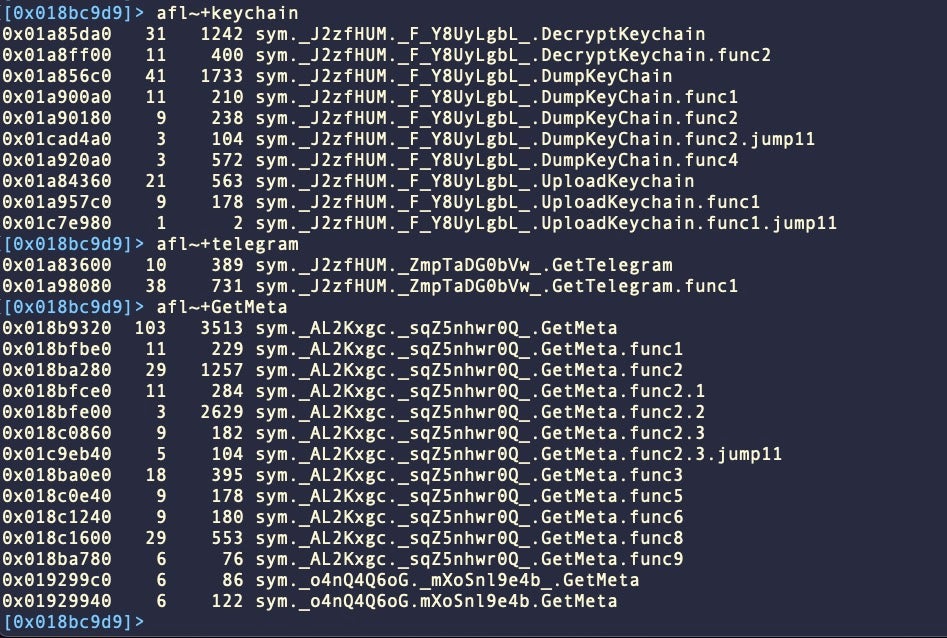
Despite the obfuscation, some tell-tale signs of the binary’s tasking remain as artifacts. In particular, we can identify functions for exfiltrating the keychain, extracting saved passwords, and grabbing files.
Some, but not all, versions contain methods seemingly targeting Telegram and Meta services.
Samples of MetaStealer have been observed reaching out to one of the following domains:
api.osx-mac[.]com builder.osx-mac[.]com db.osx-mac[.]com
MetaStealer has also been observed attempting to open an outgoing TCP connection to either host 13[.]125.88[.]10 or 13[.]114.196[.]60 over port 3000.
Is MetaStealer Related to Atomic Stealer?
Earlier this year we documented how another macOS infostealer, Atomic Stealer, was being offered for rent to threat actors via a Telegram channel. Last week, other researchers noted that a version of Atomic Stealer was being distributed via malvertising through Google Ads using a typosquatting technique to deliver a fake TradingView application. Interestingly, some versions of MetaStealer are also masquerading as TradingView.
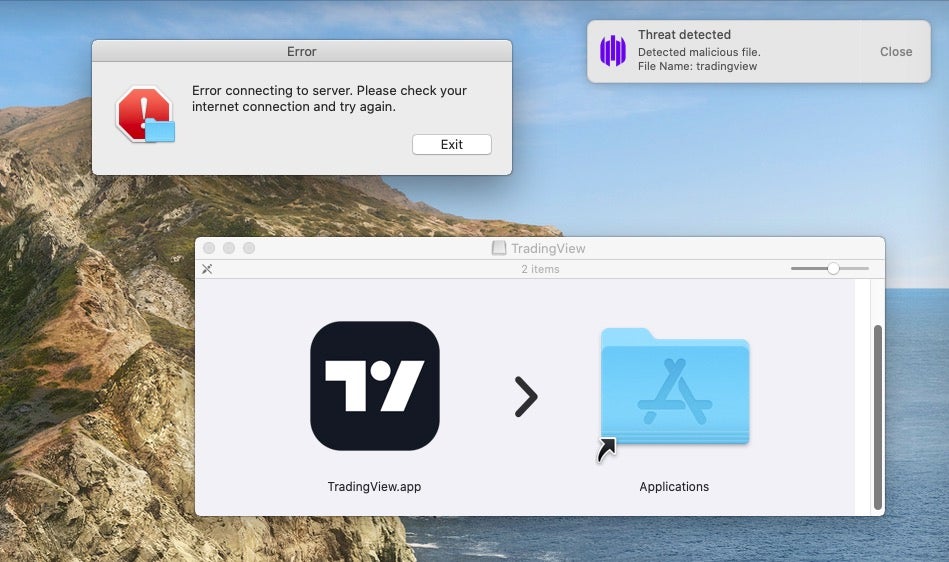
However, despite both being Go-based infostealers that also use osascript to display error messages to the user on execution, we see little actual code overlap between MetaStealer and Atomic Stealer. We also note that the network infrastructure and observed method of delivery in MetaStealer campaigns is rather different to that seen in Atomic Stealer.
At this point, we cannot rule out that the same team of malware developers could be behind both stealers, but it is also equally possible that an entirely different individual or team is simply using similar techniques to achieve the same objectives.
How to Stay Safe from MetaStealer Malware
The SentinelOne Singularity platform detects these and all other samples of MetaStealer malware both on-write and on execution.
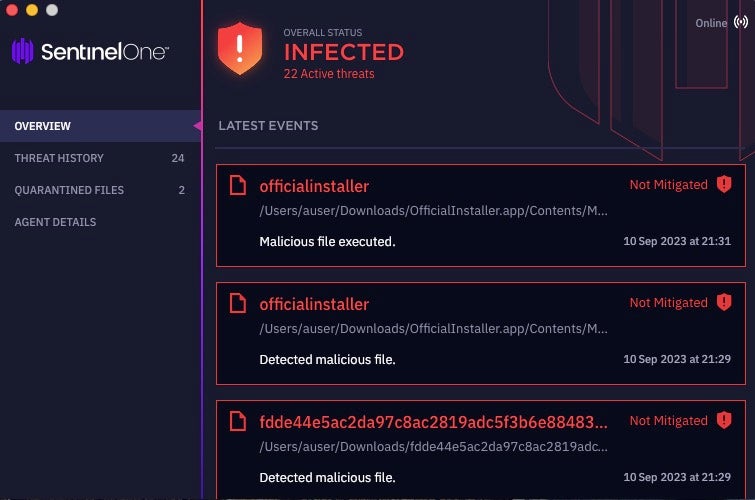
As noted above, Apple’s XProtect update v2170 contains a detection signature for some versions of MetaStealer but not all, so organizations without SentinelOne or other capable security solution are advised to review the indicators below for threat hunting and mitigation.
Conclusion
The appearance of yet another macOS infostealer this year shows the trend towards targeting Mac users for their data continues to rise in popularity among threat actors. What makes MetaStealer notable among this crop of recent malware is the clear targeting of business users and the objective of exfiltrating valuable keychain and other information from these targets. Such high-value data can be used to pursue further cybercriminal activity or gain a foothold in a larger business network.
All Mac users are advised to ensure they have an adequate security solution in place and IT and security teams are encouraged to review the comprehensive list of IoCs below.
Indicators of Compromise
MetaStealer Droppers
AdobeOfficialBriefDescription.dmg
00b92534af61a61923210bfc688c1b2a4fecb1bb
Adobe Photoshop 2023 (with AI) installer.dmg
51e8eaf98b77105b448f4a0649d8f7c98ac8fc66
Advertising terms of reference (MacOS presentation).dmg
14da5241119bf64d9a7ffc2710b3607817c8df2f
AnimatedPoster.dmg
c2cd344fbcd2d356ab8231d4c0a994df20760e3e
CardGame.dmg
5ba3181df053e35011e9ebcc5330034e9e895bfe
Conract for paymen & confidentiality agreement Lucasprod.dmg
dec16514cd256613128b93d340467117faca1534
FreyaVR 1.6.102.dmg
d3fd59bd92ac03bccc11919d25d6bbfc85b440d3
Matrix.dmg
3033c05eec7c7b98d175df2badd3378e5233b5a2
OfficialBriefDescription.app.zip
345d6077bfb9c55e3d89b32c16e409c508626986
P7yersOfficialBriefDescription 1.0.dmg
35bfdb4ad20908ac85d00dcd7389a820f460db51
PDF.app.zip
aa40f3f71039096830f2931ac5df2724b2c628ab
YoungClass brief presentation Mac 20OS.zip
3161e6c88a4da5e09193b7aac9aa211a032526b9
TradingView.dmg
e49c078b3c3f696d004f1a85d731cb9ef8c662f1
YoungSUG(Cover references,tasks,logos,brief)\YoungSUG_Official_Brief_Description_LucasProd.dmg
61c3f2f3a7521920ce2db9c9de31d7ce1df9dd44
Mach-O Binaries – Intel x86_64
0edd4b81fa931604040d4c13f9571e01618a4c9c
13249e30a9918168e79cdb0f097e4b34fbbd891f
13bcebdb4721746671e0cbffbeed1d6d92a0cf6c
1424f9245a3325c513a09231168d548337ffd698
148bc97ff873276666e0c114d22011ec042fb9b9
15c377eb5a69f93fa833e845d793691a623f928c
166ff1cd47a45e47721bb497b83cc84d8269b308
1b3ce71fa42f4c0c16af1b8436fa43ac57d74ce9
1cc66e194401f2164ff1cbc8c07121475a570d9f
1df31db0f3e5c381ad73488b4b5ac5552326baac
1df8ff1fe464a0d9baaeead3c7158563a60199d4
1e5319969d6a53efc0ec1345414c62c810f95fce
291011119bc2a777b33cc2b8de3d1509ed31b3da
2c567a37c49af5bce4a236be5e060c33835132cf
33a5043f8894a8525eeb2ba5d80aef80b2a85be8
34c7977e20acc8e64139087bd16f0b0a881b044f
3589dd0d01527ca4e8a2ec55159649083b0c50a8
35c3b735949151aae28ebf16d24fb32c8bcd7e6b
35e14d8375f625b04be43019ccb8be57656b15cf
394501f410bd9cb4f4432a32b17348cdde3d4157
47620d2242dfaf14b7766562e812b7778a342a48
57c2302c30955527293ed90bfaf627a4132386fb
65de53298958b4f137c4bd64f31f550dd2199c36
70625f621f91fd6b1a433a52e57474316e0df662
78e8f9a93b56adc8e030403ba5f10f527941f6ae
80c83e659c63c963f55c8add4bf62f9bec73d44e
816fdf1fd9cf9aff2121d1b59c9cca38b5e4eb9d
86eb7c6a4d4bec5abeb6b44e0506ab0d5a96235d
8dfeda030bd3b38592b29d633c40e041d5f3331d
8ec57c1b1b5409cadb99b050c3c41460d4c7fea8
8f211c0ef570382685d024cc8e6e8acd4a137545
90d7f8acf3524fcb58c7d7874a5b6e8194689b1a
92b178817a6c9ad22f10b52e9a35a925a3dc751b
a54c9906d41b04b9daf89c2e6eb4fdd54d0eae39
a8724eb5f9f8f4607b384154f0c398fce207259e
b51d7482d38dd19b2cb1cd303e39f8bddf5452ac
bd6b87c6f4f256fb2553627003e8bce58689d1d8
bdd4ce8c2622ddcf0888e05690c8b3d1a8c83dae
be1ac5ed5dfd295be15ba5ed9fbb69f10c8ec872
c37751372bb6c970ab5c447a1043c58ce49e10a5
c4d9272ef906c7bf4ccc2a11a7107d6b7071537b
c5429b9b4d1a8e147f5918667732049f3bd55676
caf4fb1077cea9d75c8ae9d88817e66c870383b5
cf467ca23bdb81e008e7333456dfceb1e69e9b8a
cfa56e10c8185792f8a9d1e6d9a7512177044a8b
d7de135a03a2124c6e0dfa831476e4069ebfba24
dbf0983b29a175ebbcf7132089e69b3999adeca7
dfd5adb749cbc5608ca915afed826650fcb0ff05
e5cfc40d04ea5b1dac2d67f8279c1fd5ecf053f6
f6f09ecc920eb694ed91e4ec158a15f1fb09f5dd
f93dd5e3504fe79f7fcd64b55145a6197c84caa2
f97e22bad439d14c053966193fdfdec60b68b786
fce7a0c00bfed23d6d70b57395e2ec072c456cba
Network Communications
IPs
13[.]114.196.60
13.125.88.10
Domains
api.osx-mac[.]com
builder.osx-mac[.]com
db.osx-mac[.]com
URLs
hXXps[:]//api.osx-mac[.]com/api/collections/victims/records
returns:
{"page":1,"perPage":30,"totalItems":0,"totalPages":0,"items":[]}
hXXp[:]//api.osx-mac[.]com/chainbreaker
returns:
{"code":404,"message":"Not Found.","data":{}}
Developer ID
Bourigaultn Nathan (U5F3ZXR58U)
如有侵权请联系:admin#unsafe.sh